Picture this: You’re sitting in a meeting room, and your auditor just dropped a bomb. “We’ll need to examine all your cloud accounts, every subsidiary, and each product that touches customer data.” Your heart sinks as you watch dollar signs multiply faster than rabbits in spring.
Sound familiar? If you’re a CTO preparing for your first SOC 2 audit—or trying to optimize your current one—you’ve probably wrestled with the age-old question: “What exactly needs to be included in our audit scope?” System requirements play a crucial role here, as they determine which specific services, systems, and controls must be included in the SOC 2 audit scope.
The good news? You don’t have to audit everything under the sun. The challenging news? Making smart scoping decisions requires strategy, not guesswork.
Why Getting Your Scope Right Matters More Than You Think
Before we dive into the how-to, let’s talk about why this matters. Getting your SOC 2 scope wrong is like ordering pizza for a party—get it wrong, and you’re either paying for way too much or leaving your guests hungry (and in this case, your customers questioning your security posture).
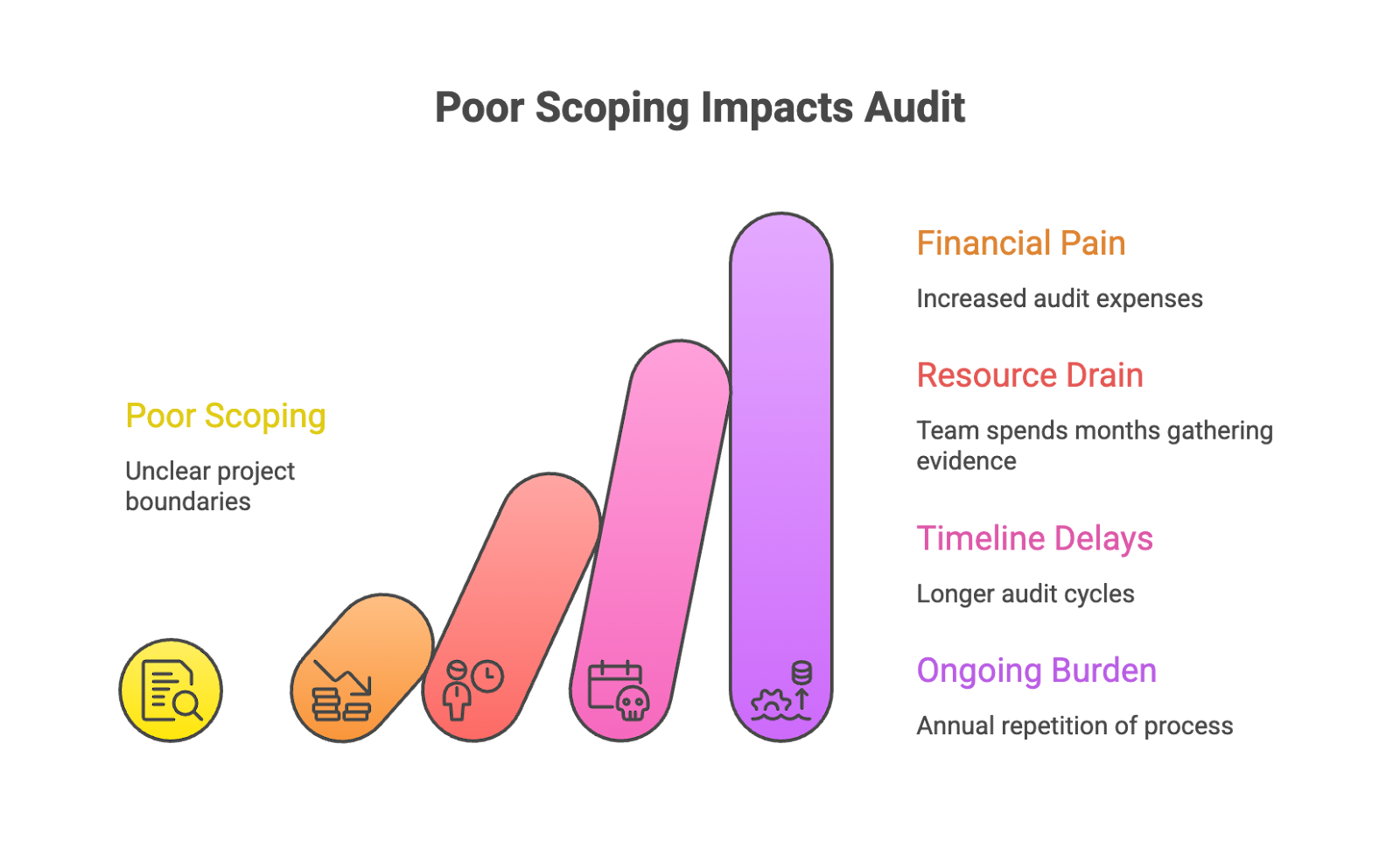
The Real Impact of Poor Scoping:
- Financial Pain: Every additional system, subsidiary, or cloud account can add thousands to your audit bill
- Resource Drain: Your team spends months gathering evidence for systems that don’t actually need to be audited
- Timeline Delays: Broader scope means longer audit cycles and delayed certifications
- Ongoing Burden: Remember, this isn’t a one-time thing—you’ll repeat this process annually
The scope of a SOC audit determines which systems, processes, and controls are evaluated, directly impacting the cost, audit complexity, and the overall effort required for certification.
The Foundation: Understanding What SOC 2 Actually Cares About
Here’s where many CTOs get tripped up. SOC 2 isn’t about auditing your entire technology stack—it’s about auditing the systems that process, store, or transmit customer data that’s covered by your service commitments.
SOC 2 is based on the AICPA's Trust Services Criteria, which define audit scope and evaluate controls. The five categories are Security (mandatory), Availability, Processing Integrity, Confidentiality, and Privacy (optional). Organizations must justify excluding any criteria. These criteria guide auditors and organizations in designing effective, flexible controls tailored to their environment and risks.
Think of it this way: If a system doesn’t touch customer data or isn’t part of delivering your core service, it probably doesn’t need to be in scope. Your HR system, employee expense platform, or that random marketing tool your team uses? Likely out of scope.
The Three Golden Questions for Any System:
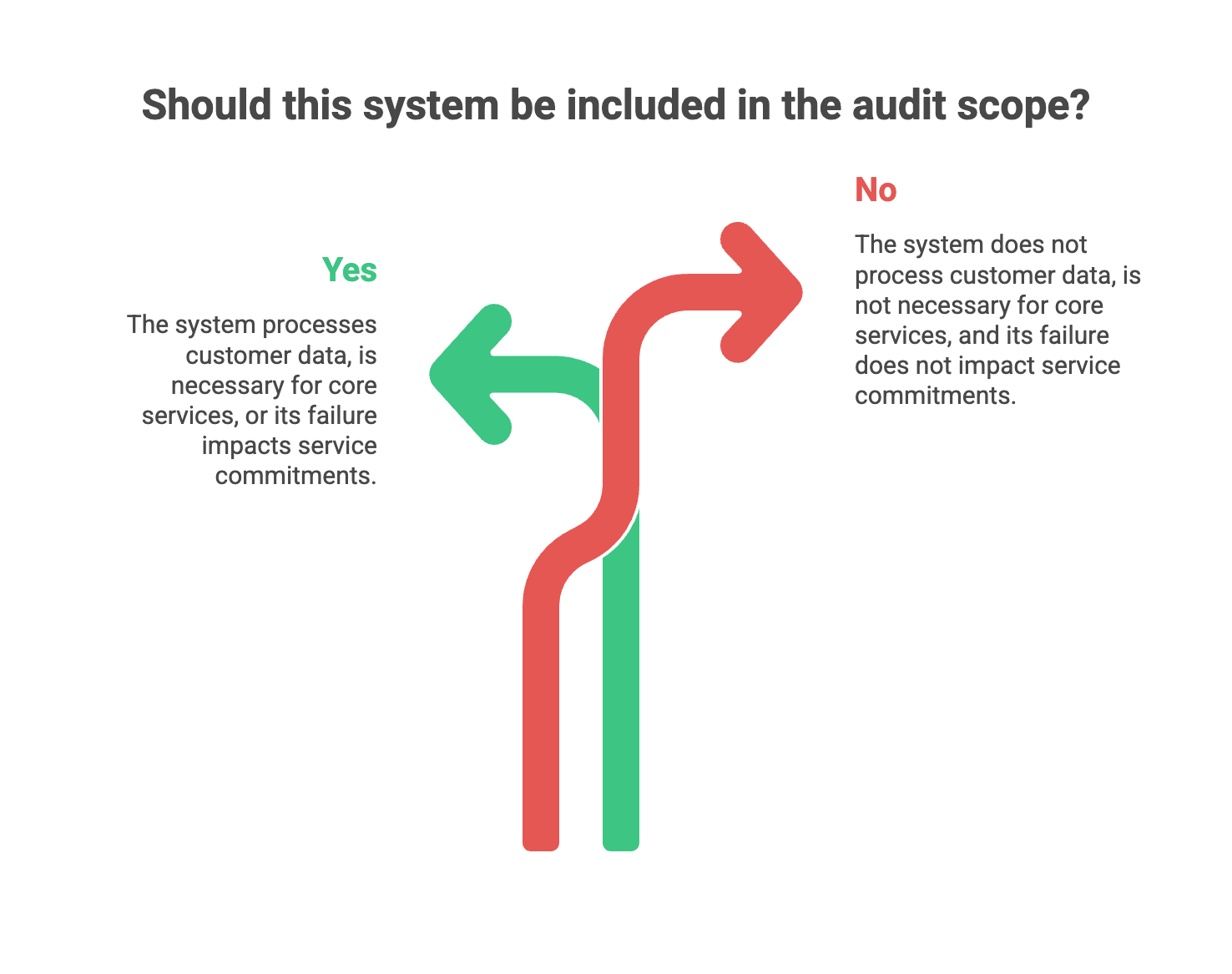
- Does this system process, store, or transmit customer data?
- Is this system necessary for delivering our core service to customers?
- Would a failure of this system directly impact our ability to meet our service commitments?
If you answer “no” to all three, you can probably leave it out.
Readiness Assessment: Laying the Groundwork for a Successful Audit
Before you even think about inviting an auditor in, a readiness assessment is your secret weapon for a smooth and successful SOC 2 audit. Think of it as a dress rehearsal: it’s your chance to spot any gaps in your security controls, shore up your defenses, and make sure your organization is truly ready to protect sensitive data in line with the Trust Services Criteria.
A thorough readiness assessment evaluates how well your current controls stack up against the SOC 2 requirements—covering everything from access controls and security awareness training to incident response and data security practices. This process helps you identify areas where your controls might not be operating effectively, giving you time to address weaknesses before the official audit begins.
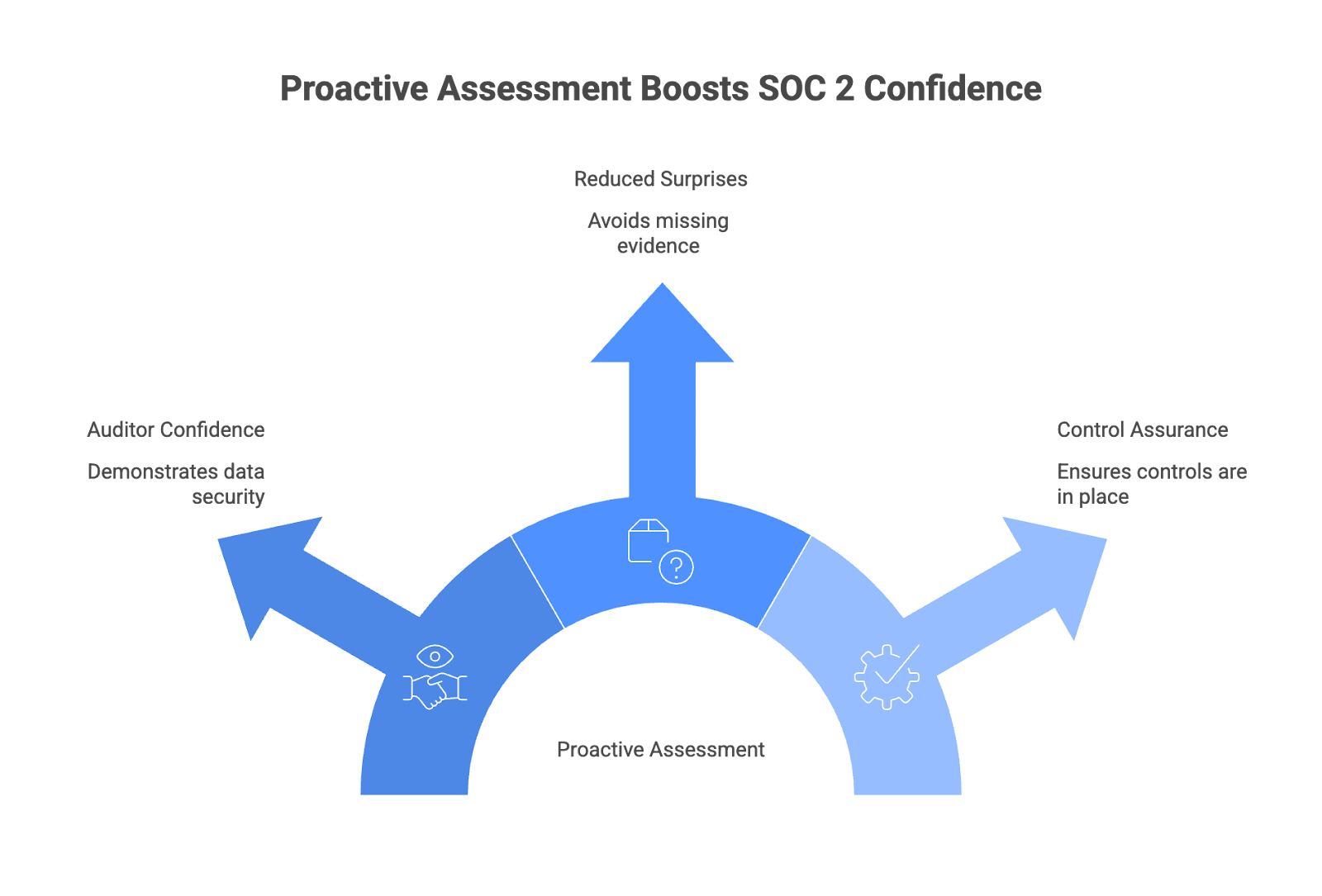
By proactively assessing your environment, you can demonstrate to auditors (and customers) that you take data security seriously. You’ll also reduce the risk of unpleasant surprises during the audit, such as missing evidence or overlooked vulnerabilities. The readiness assessment is your opportunity to ensure that all controls relevant to the Trust Services Criteria are in place and functioning as intended, so you can walk into your SOC 2 audit with confidence.
In short: a readiness assessment isn’t just a checkbox—it’s your roadmap to a successful audit, helping you protect sensitive data, avoid costly delays, and show your commitment to operating effectively under the SOC 2 framework.
Risk Assessment and Audit Planning
Defining the SOC 2 scope is a critical first step for any organization seeking compliance. The scope determines which systems, processes, and data are included in the audit, and directly impacts the resources required and the overall success of the engagement. Conducting a gap analysis can help identify areas where controls may be lacking before the audit begins.
A structured risk assessment is essential to determine which Trust Services Criteria (TSC) are relevant to your business and which systems and processes should be included. This process should involve identifying key data flows, third-party vendors, and business-critical applications. An internal audit can help evaluate the effectiveness of existing controls and readiness for the SOC 2 audit. It is also important to identify specific controls tailored to your organization's unique risks and systems, ensuring that your SOC 2 scope addresses all relevant compliance requirements. Prioritizing controls based on risk and business impact will help ensure that your SOC 2 program is both effective and efficient.
The Decision Tree: Your Roadmap to Smart SOC 2 Scope Scoping
Effective scoping for a SOC 2 audit requires clearly defining the boundaries for your services, technical environments, and compliance objectives. The primary goal of defining the scope is to identify the key data and systems to focus on and to establish appropriate controls that address the Trust Services Criteria—security, availability, processing integrity, confidentiality, and privacy. Implementing strong internal controls is essential for ensuring compliance and building trust with customers and auditors. To ensure your controls are effective, a structured risk assessment should be performed to prioritize appropriate controls for critical threats relevant to your organization.
Let’s walk through a practical decision tree that’ll help you make scoping decisions without second-guessing yourself every step of the way.
Step 1: Start With Your Core Service
Question: What is the primary service you’re providing to customers?
This sounds obvious, but it’s worth spelling out clearly. Are you a SaaS platform? A cloud hosting provider? A data analytics service? As a service provider, your specific role and responsibilities are central to defining your SOC 2 scope, as the audit will focus on the systems and processes you manage for your clients. Your core service definition will guide everything else.
Example: If you’re a project management SaaS tool, your core service is providing project management capabilities to your customers through your web application.

Step 2: Map Your Service Delivery Chain and Customer Data
Question: What systems are absolutely essential for delivering this core service?
Work backwards from your customer’s experience. What happens when they log in? What systems are involved in processing their data? Which databases store their information? Identify all relevant systems that are part of the service delivery chain, ensuring that system processing is complete, valid, accurate, and timely to maintain data integrity and compliance. As part of this process, it is crucial to validate and control data inputs to ensure data accuracy, completeness, and authorization throughout data processing. Additionally, understanding the service organization's environment—including its services, systems, people, processes, and policies—is essential for effective SOC 2 scoping, as it helps identify potential weaknesses and define the audit scope appropriately. It is also important to document the personnel involved—including IT staff, management, and other employees responsible for system governance and security—as well as data processors who handle customer data throughout its collection, processing, storage, and transmission.
Include
- Web application servers
- Customer databases
- Authentication systems
- API gateways
- Load balancers
- Customer-facing applications
Probably Exclude:
- Internal HR systems
- Financial planning tools
- Marketing automation platforms
- Development/testing environments (unless they use real customer data)
Step 3: Apply the Cloud Account Filter
Question: Does this cloud account contain systems that are part of your service delivery chain?
Here’s where many organizations go overboard. Just because you have five AWS accounts doesn’t mean all five need to be in scope.
Cloud computing services are typically included in the SOC 2 scope due to their role in data storage, processing, and transmission. If your organization offers cloud computing services, these accounts should be considered in scope because of their access to sensitive data and the need for strong security controls. It is also important to consider the security of the data centers that host your cloud infrastructure, including physical access controls and environmental safeguards. Additionally, implementing intrusion detection systems is essential for monitoring network traffic and protecting cloud environments from unauthorized access.
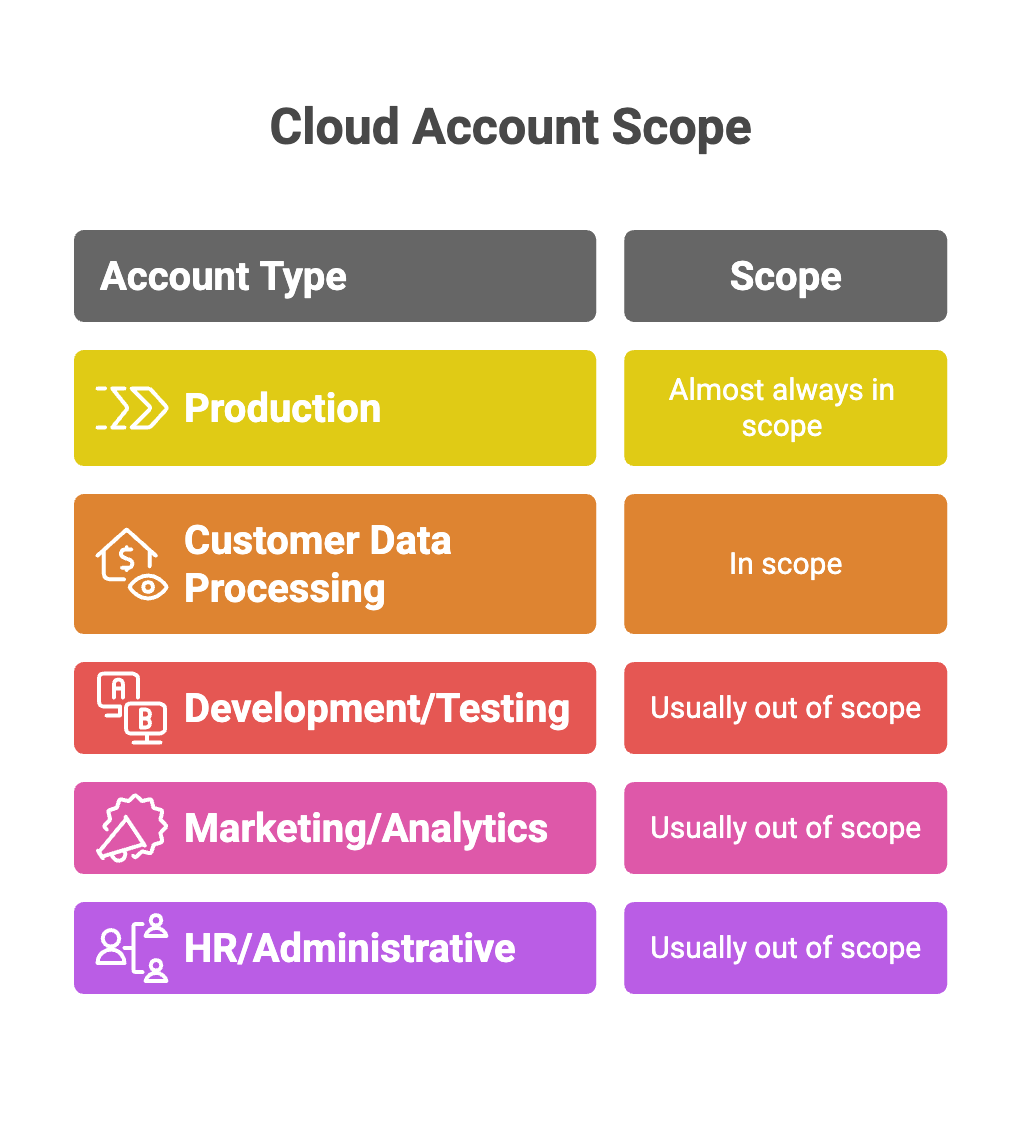
Decision Logic for Cloud Accounts:
- Production Account: Almost always in scope
- Customer Data Processing Account: In scope
- Development/Testing Account: Usually out of scope (unless using real customer data)
- Marketing/Analytics Account: Usually out of scope
- HR/Administrative Account: Usually out of scope
Step 4: Navigate the Subsidiary Maze
Question: Does this subsidiary process customer data or deliver part of your core service?
This is where it gets tricky. Having multiple legal entities doesn’t automatically mean multiple audit scopes.
Include Subsidiaries If:
- They process customer data on behalf of the parent company
- They deliver a component of your core service
- They have access to production systems
- They handle customer support or billing
Including subsidiaries in your SOC 2 scope provides assurance to user entities who rely on the SOC 2 report to understand how the service organization's controls protect their data and interests.
You should also consider sub-service organizations, such as third-party vendors, in your SOC 2 scope if they have access to sensitive data or systems. The SOC 2 scope should include details about these sub-service organizations, as auditors will evaluate the effectiveness of the service organization's controls over third-party vendors and subsidiaries. Companies can choose to include third-party vendors in their SOC 2 audit using the carve-out or inclusive method.
Exclude Subsidiaries If:
- They operate completely independently
- They don’t touch customer data
- They provide purely internal services (like facilities management)
Step 5: Product Portfolio Decisions
Question: Is this product included in the service commitments you’re making to customers?
If you offer multiple products, you don’t necessarily need to include all of them in a single SOC 2 report.
Strategic Considerations:
- Can you create separate SOC 2 reports for different product lines?
- Do your customers specifically require SOC 2 for this particular product?
- Do different products share infrastructure or data stores?
- Which products handle sensitive data or critical data, such as PII or protected health information (PHI)? Products that collect, store, transmit, or process sensitive or critical data, including PHI, should be prioritized for inclusion in your SOC 2 scope.
The primary goal of defining the scope of your SOC 2 audit is to identify the key data to focus on, the associated risks, and to establish appropriate SOC 2 controls and operational controls for products that process sensitive data, ensuring their security and compliance.
Scope Change Control Process
Before Adding Anything to Scope:
- Justification Required: Why does this need to be included?
- Cost Impact: What’s the estimated additional audit cost?
- Effort Estimate: How many additional hours of preparation?
- Stakeholder Approval: Who needs to sign off on this addition?
The audit scope can be refined based on findings and changes in the service organization’s environment as the audit progresses. Changes in scope may impact the audit period and require a reassessment of the design and operating effectiveness of controls to ensure they meet SOC 2 Type 2 requirements.
Annually Scope Review Questions:
- Have we added new systems that process customer data?
- Have we launched new products or services?
- Have we acquired companies or spun off subsidiaries?
- Have our service commitments to customers changed?
Regulatory Compliance Considerations: Aligning SOC 2 With Broader Requirements
SOC 2 compliance doesn’t exist in a vacuum. For most organizations, especially those in SaaS, fintech, or healthtech, aligning your SOC 2 efforts with broader regulatory requirements—like HIPAA, GDPR, or CCPA—is essential for building a truly robust compliance program.
The Trust Services Criteria (TSC) at the heart of SOC 2 are designed to evaluate your organization’s controls around security, availability, processing integrity, confidentiality, and privacy. By mapping these criteria to other regulatory frameworks, you can streamline your compliance efforts and ensure that your controls are not only SOC 2-ready but also meet the expectations of regulators and enterprise customers alike.
Certified public accountants (CPAs) who perform SOC 2 audits will look for evidence that your controls are operating effectively—not just on paper, but in practice. This means your policies and procedures should address all relevant requirements, from protecting sensitive data to ensuring processing integrity and maintaining a strong control environment.
Regular audits and internal assessments help you stay ahead of evolving regulations and demonstrate ongoing compliance. By taking a holistic approach, you can reduce audit fatigue, avoid duplication of effort, and provide assurance to customers that your organization is committed to availability, processing integrity, confidentiality, and privacy—no matter which regulatory acronym comes knocking.

Vendor and Third-Party Management: Scoping Beyond Your Walls
Your SOC 2 audit scope shouldn’t stop at your organization’s front door. In today’s interconnected world, vendors and third-party providers often play a critical role in processing or storing your sensitive data. That’s why effective vendor management is a must-have for any SOC 2 compliance program.
When defining your audit scope, be sure to include an assessment of the security controls your vendors and third-party providers have in place. This means reviewing their service level agreements (SLAs), contracts, and security posture to ensure they meet your standards for protecting sensitive data. If a third party has access to your production systems or customer data, their controls become part of your risk landscape—and auditors will expect you to demonstrate how you manage those risks.
Regularly monitoring and reassessing your vendors’ security controls helps you identify potential vulnerabilities before they become problems. By scoping beyond your own environment, you can ensure that your entire data supply chain is secure, compliant, and ready to withstand scrutiny during your SOC 2 audit.
In short: don’t let a weak link in your vendor chain put your compliance (or your customers’ trust) at risk. Make vendor management a core part of your SOC 2 audit scope, and you’ll be better positioned to protect sensitive data—no matter where it lives.
Common Scoping Mistakes (And How to Avoid Them)
Unlike SOC 1, which is intended for financial auditors and focuses on financial reporting and internal controls relevant to the accuracy and reliability of financial statements, SOC 2 is designed to address broader security and compliance concerns. Poor scoping in SOC 2 can increase the risk of data breaches and security incidents by overlooking critical systems or controls, leading to both financial and reputational impacts. Properly defining your SOC 2 scope is essential to mitigate these risks and ensure comprehensive protection.
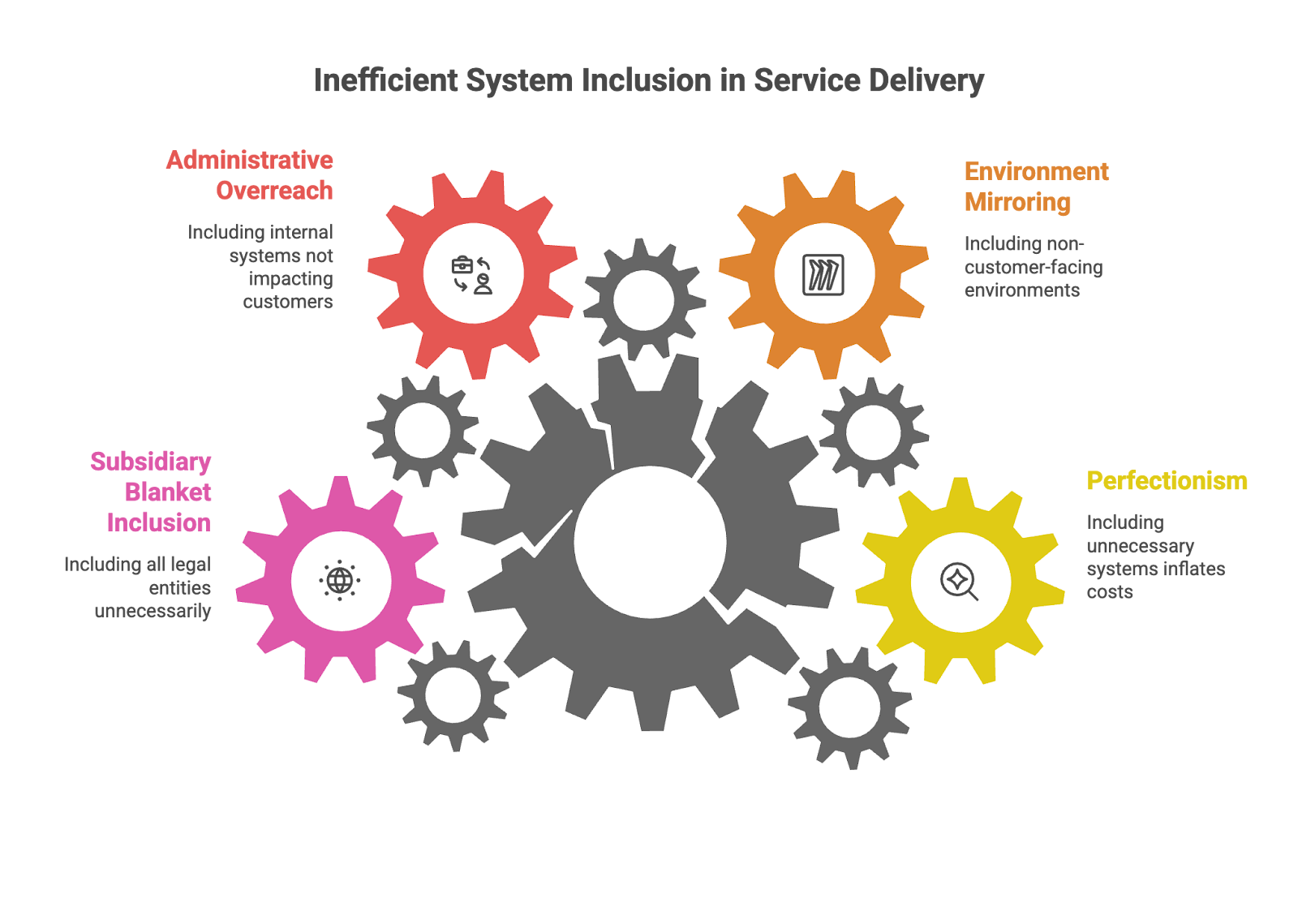
Mistake #1: The "Everything Must Be Perfect" Trap
What Happens: Including every system "just to be safe"
Why It's Problematic: Massively inflates costs and timeline
Better Approach: Use the three golden questions religiously
Mistake #2: The Development Environment Inclusion
What Happens: Including dev/test environments because they "mirror production"
Why It's Problematic: These don't process customer data or deliver services
Better Approach: Only include if they contain real customer data (which they shouldn't)
Mistake #3: The Administrative System Overreach
What Happens: Including HR, finance, and other internal systems
Why It's Problematic: These don't impact your service commitments to customers
Better Approach: Focus only on customer-facing service delivery
Mistake #4: The Subsidiary Blanket Inclusion
What Happens: Assuming all legal entities must be included
Why It's Problematic: Creates unnecessary complexity and cost
Better Approach: Only include entities that touch customer data or service delivery
Working With Your Auditor: Setting Expectations Early
Your auditor is your partner in this process, not your adversary. A SOC 2 audit is an independent audit conducted by a third party to objectively assess your controls and provide assurance to your customers. Understanding the audit process—including how the soc audit is conducted, what evidence is required, and how scope is determined—is essential for a successful SOC 2 engagement. Consulting an auditor early can help you refine your SOC 2 scope based on your organization’s specific needs and risks. You will also need to provide justification to SOC 2 auditors for any Trust Services Criteria you believe do not apply to your services, and document your systems and controls thoroughly to provide sufficient evidence during the SOC 2 external audit. Regularly evaluating and documenting your controls is critical to ensure compliance with SOC 2 requirements and to be fully prepared for the audit. Here’s how to have productive scoping conversations:
Before the First Meeting:
- Prepare a simple architecture diagram
- List out your key service commitments to customers
- Identify any areas where you’re genuinely unsure
Questions to Ask Your Auditor:
- “Based on our service description, what would you typically see in scope?”
- “Are there any systems you’d question excluding?”
- “How do you typically handle [specific scenario relevant to your business]?”
- “What’s the cost impact of including/excluding this particular system?”
Red Flags in Auditor Conversations:
- Insisting on including systems without clear justification
- Being unable to explain why something needs to be in scope
- Pushing for broader scope without considering your actual service commitments
The Business Case for Smart Scoping
Let’s talk numbers. Smart scoping isn’t just about saving money—it’s about strategic resource allocation.
Typical Cost Differences:
- Over-scoped SOC 2: $25K-$150K+ annually
- Right-sized SOC 2: $10K-$50K annually
- Internal effort over-scoped: 500+ hours annually
- Internal effort right-sized: 100-300 hours annually
Beyond Cost Savings:
- Faster audit completion
- Clearer focus on systems that actually matter to customers
- Easier ongoing compliance maintenance
- More strategic use of your security team’s time
Achieving SOC 2 compliance can also streamline vendor management and due diligence processes. By providing a recognized SOC 2 report, your organization can simplify third-party assessments and strengthen oversight of vendors, reducing the need for repetitive audits. SOC 2 certification is a way organizations demonstrate compliance with regulatory requirements and validate their commitment to data protection and privacy. Additionally, developing a robust information security program is essential for ongoing compliance and effective risk management. SOC 2 compliance also helps demonstrate adherence to regulatory requirements such as GDPR, CCPA, and HIPAA, lowering the risk of fines and penalties while ensuring your controls meet industry-specific standards.
The Bottom Line
Scoping your SOC 2 audit doesn't have to feel like navigating a minefield. With the right framework and a clear understanding of what SOC 2 actually requires, you can make confident decisions that protect your budget while still meeting your compliance needs.
SOC 2 (System and Organization Controls 2) is a voluntary compliance framework developed by the AICPA to evaluate how service organizations manage and protect customer data. Achieving SOC 2 compliance builds trust and credibility with customers and stakeholders, and can provide a competitive advantage by demonstrating a strong commitment to data protection and security. The SOC report is essential for organizations to demonstrate compliance to customers and stakeholders, providing assurance that your controls meet the Trust Services Criteria.
Remember: SOC 2 is about demonstrating that you can securely deliver your service to customers. It's not about proving that every single system in your organization is perfect. Focus on what matters, be strategic about what you include, and don't let scope creep turn your audit into an expensive fishing expedition.
Your customers want to know they can trust you with their data. Your SOC 2 report should give them that confidence without breaking your bank or consuming your entire engineering team's bandwidth.
The key is finding that sweet spot where you're comprehensively covering what matters while strategically excluding what doesn't. Get this right, and your SOC 2 audit becomes a manageable, predictable part of your compliance program rather than an annual crisis.
Need help right-sizing your SOC 2 scope? At SecureLeap, we help small businesses navigate SOC 2 and ISO 27001 certification with practical, cost-effective approaches.
FAQ for SOC2 Scope
What is included in the SOC 2 scope?
The SOC 2 scope defines which systems, processes, and data are covered by the audit. The audit scope should include controls related to security, availability, processing integrity, confidentiality, and privacy, as these are the Trust Services Criteria evaluated in a SOC 2 report. The security category is mandatory for all SOC 2 audits and serves as the baseline focus for security assessments. Organizations can choose to include additional categories (availability, processing integrity, confidentiality, privacy) based on their business needs and customer requirements.
What is the confidentiality principle in SOC 2?
The confidentiality principle focuses on protecting sensitive information from unauthorized access or exposure. It is designed to ensure that confidential data is only accessible to authorized individuals and is not disclosed to unauthorized parties. Preventing unauthorized disclosure of sensitive information is a critical aspect of the confidentiality principle, helping organizations maintain privacy and security.
What is the privacy principle in SOC 2?
The privacy principle addresses how personal information is collected, used, retained, disclosed, and disposed of. It ensures that organizations handle personal data in accordance with their privacy policies and regulatory requirements.
What is the difference between a SOC 2 Type I and Type II report?
A SOC 2 Type I report evaluates the design and implementation of controls at a specific point in time. A SOC 2 Type II report, on the other hand, assesses the operating effectiveness of controls over a defined period (typically 3-12 months), demonstrating how well the controls function in practice. Type II reports are generally preferred by customers and partners because they provide assurance that controls are not only designed properly but are also operating effectively over time.
What systems should be included in a SOC 2 audit scope?
Include systems that process, store, or transmit customer data or are strictly necessary for delivering your core service. If a system failure would directly impact your ability to meet service commitments, it belongs in the audit scope.
Do development environments need to be included in SOC 2?
Development and testing environments are usually out of scope provided they do not contain real customer data. They should only be included if they mirror production with actual sensitive information.
Should all company subsidiaries be included in a SOC 2 audit?
You only need to include subsidiaries that process customer data, deliver a component of the core service, or have access to production systems. Independent entities that do not touch customer data can be excluded to reduce complexity.
How does proper scoping affect SOC 2 audit costs?
A right-sized SOC 2 audit typically costs between $15,000 to $75,000 annually, whereas an over-scoped audit can range from $25,000 to over $150,000. Strategic scoping also saves hundreds of hours of internal team effort.
Are internal tools like HR or marketing software in scope for SOC 2?
Internal tools like HR systems, financial planning software, or marketing platforms are generally out of scope. These systems usually do not process customer data or impact the delivery of your core service.
About SecureLeap
Your Trusted Partner in Security Compliance
SecureLeap is a specialized security and compliance consultancy providing virtual CISO (vCISO) services tailored for growing startups and SMBs. Our team of experts helps organizations navigate the complex landscape of security certifications, including SOC 2, ISO 27001, and GDPR compliance, without the overhead of a full-time security executive.
Whether you're preparing for your first SOC 2 audit, looking to optimize your audit scope, or aiming to enhance your existing compliance program, SecureLeap offers comprehensive support to guide you through every step of the process. From readiness assessments and gap analysis to audit preparation and ongoing compliance management, we help ensure your organization meets the SOC 2 Trust Services Criteria effectively and efficiently.
📍 Visit secureleap.tech to learn how we can support your security compliance journey.






