Author: Marçal Santos, vCISO | +20 Years Cybersecurity Experience
Key takeaways about SOC auditors
- Only CPAs Can Issue Reports: A SOC auditor must be a licensed SOC 2 CPA firm (or a CPA-led practice) authorized by the AICPA. While they may partner with cybersecurity experts for testing, only the CPA firm can issue valid SOC 2 audit reports.
- Match the Firm to Your Size: When searching for the best SOC 2 auditors, align your choice with your company's stage. SOC 2 compliance companies are generally categorized into Big Four (for enterprise), Mid-Market leaders (for scale-ups), and Boutique specialists (for startups seeking a personalized approach).
- Understanding the Audit Phases: A standard SOC 2 audit progresses through four distinct phases: scoping evidence requirements (IRL), collecting and sampling evidence, testing the operating effectiveness of controls, and finally issuing the report.
- Type 2 Focuses on Operations: A SOC 2 Type 2 audit goes beyond design; it requires providing evidence that your security, availability, and confidentiality controls functioned effectively over a specific period of time (typically 3-12 months).
Quick answer: what is a SOC auditor and why do you need one?
A SOC auditor is an independent CPA firm or qualified assessor that performs SOC 1, SOC 2, and SOC 3 examinations under standards set by the American Institute of Certified Public Accountants (AICPA). These certified public accountants specialize in evaluating whether a service organization’s controls actually work as intended—not just on paper, but in daily operations. SOC audits are primarily categorized as SOC 1 (focused on financial reporting controls), SOC 2 (focused on data security, availability, processing integrity, confidentiality, and privacy), and SOC 3 (a public version of the SOC 2 report intended for general distribution).
Only licensed CPA firms (or CPA-led practices under AICPA rules) can issue official SOC reports, even if they partner with cybersecurity specialists for technical testing.
The SOC 2 framework is designed for all types of service organizations, particularly those that store customer data or handle sensitive data for US-based clients. SOC 2 reports focus on controls at service organizations relevant to security, availability, processing integrity, confidentiality, or privacy, as defined by the AICPA. SOC 2 compliance is not mandatory but is often required by clients seeking assurance that their sensitive data will be protected.

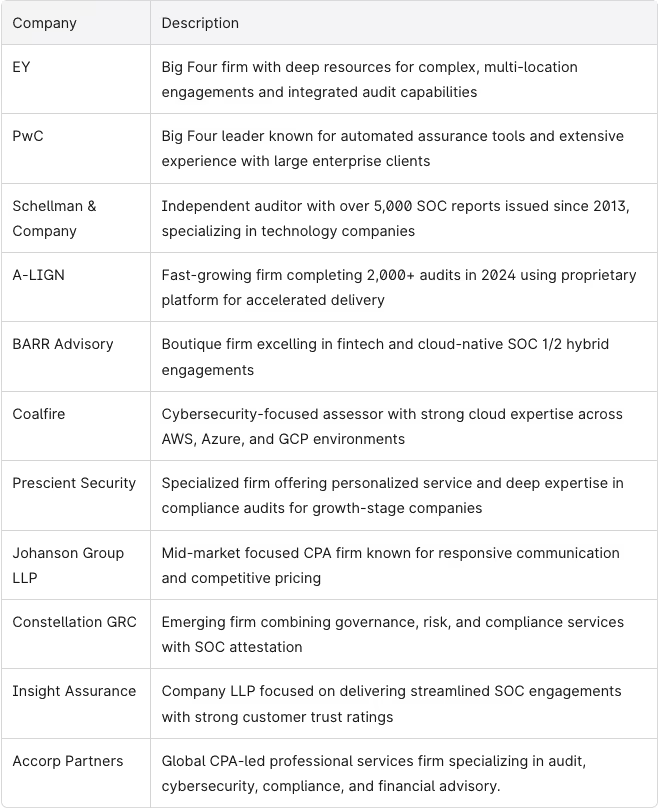
SOC auditors: leading firms to consider in 2026
Choosing the right SOC auditor depends on your company size, industry, budget, timeline, and—crucially—how well the auditor aligns with your organization's specific business needs and objectives. Below you’ll find a mix of established firms and specialized boutique practices that have a proven track record in delivering SOC audits for cloud-native and SaaS companies. Leading firms are recognized for their expertise in security assessments and control logics, which are foundational for robust SOC audits.
How to Choose the Best SOC Auditor: Key Considerations
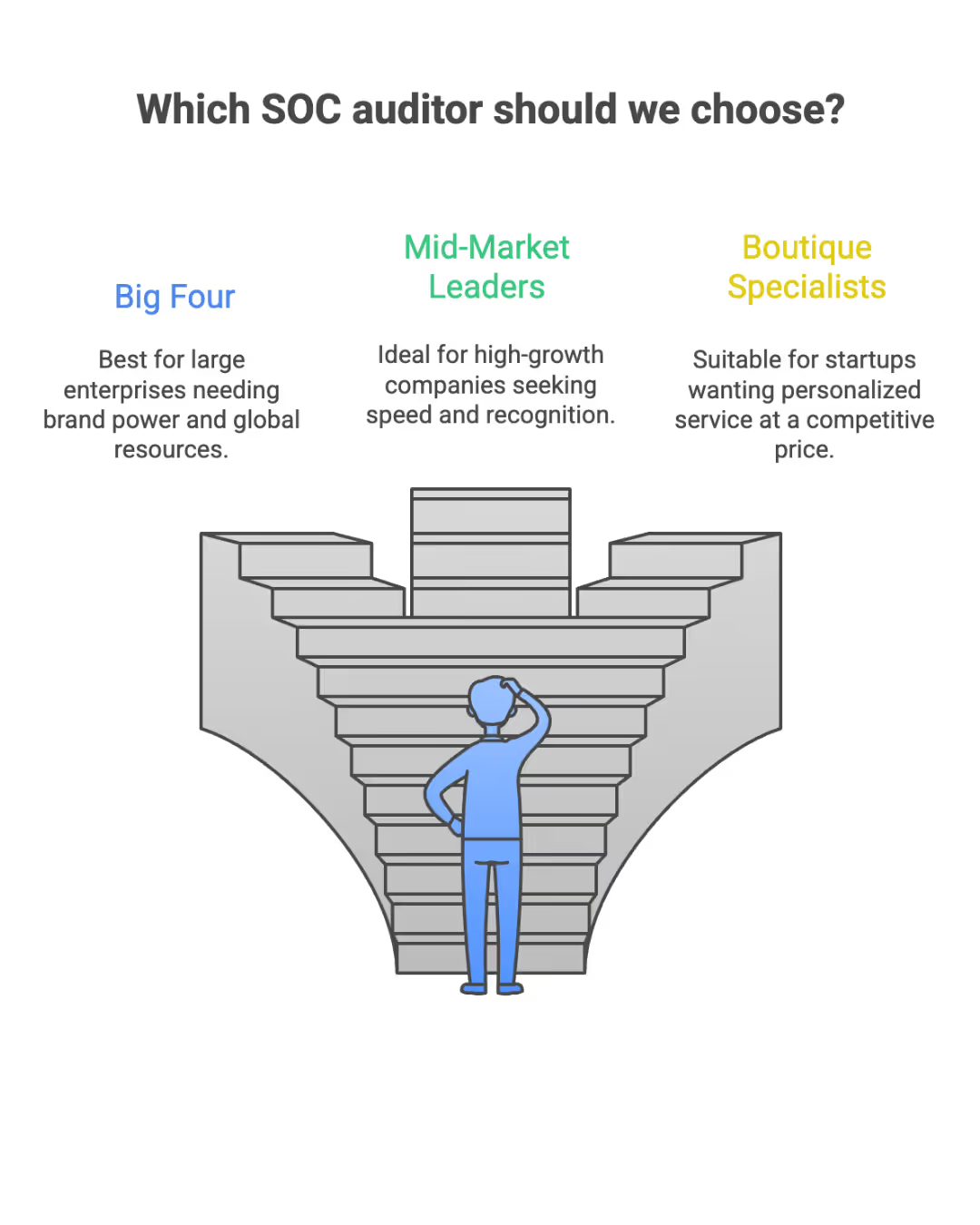
Not all audit firms are created equal. The best SOC auditor is one who understands your organization's system and can effectively evaluate your organization's controls. To save time and money, match your auditor to your company size:
Below is Secureleap's suggested list of companies aligned according to company size / need:
- The Big Four (Best for Enterprise): Massive organizations with global footprints often require the brand power and resources of firms like PwC and EY. Ensure their expertise aligns with your business needs and that they are capable of assessing your service organization's controls.
- Mid-Market Leaders (Best for Scale-ups): High-growth companies usually look for a blend of speed and market recognition. Top choices include Schellman, A-LIGN, BARR Advisory, and Coalfire. Choose a firm whose experience matches your business needs and who understands your service organization's controls.
- Boutique Specialists (Best for Startups): Companies looking for a personalized, “white-glove” experience at a competitive price point often choose Prescient Security, Johanson Group LLP, Constellation GRC, Insight Assurance, or Accorp Partners. Make sure the auditor’s expertise fits your business needs and that they can effectively evaluate your service organization's controls.
When choosing a SOC 2 auditor, it is essential to consider their experience within your specific industry to understand unique needs and challenges. Select an auditor with a strong industry background, positive client reviews, and relevant accreditations.
Note: For valuable insights on audit pricing and how to optimize your SOC 2 budget, be sure to check out Secureleap’s audit pricing calculator.

How the SOC 2 audit process works with an auditor
Once you engage an auditor, the process shifts entirely to data gathering, evidence verification, and reporting. The workflow focuses on proving that your controls operated as designed during the audit period.
Phase 1: Defining the Evidence Requirements (Scoping & IRL)
The process begins with the auditor defining exactly what data is required. They generate a Provided by Client (PBC) list or Information Request List (IRL) based on your specific technology stack and the Trust Services Criteria you selected. The audit process is service organization relevant, focusing on controls that impact five Trust Services Criteria (TSC): security, availability, processing integrity, confidentiality, or privacy (note: only security criteria is mandatory).
- Defining Populations: The auditor requests full lists of activities that occurred during the audit period—such as a list of all new hires, all terminated employees, and all code changes deployed to production.
- System Boundaries: Determining which specific cloud environments (e.g., AWS, Azure), databases, and tools are in scope for evidence collection.
Phase 2: Evidence Collection & Sampling
This is the data-intensive phase where your team submits proof that controls are working. Auditors review evidence to ensure the organization's controls are operating as intended.
- Population Sampling: From the full lists (populations) you provided in Phase 1, the auditor selects a random sample (typically 25–40 items) for detailed inspection.
- Submission: You upload specific evidence for those samples. For example, if the auditor selects “Change Request #102,” you must upload the Jira ticket showing the approval timestamp, the pull request, and the deployment log.
- Automated Collection: If you use a GRC automation platform (like Drata or Vanta), the auditor may simply review the automated data feed rather than asking for manual screenshots.
Phase 3: Testing & Review
Once evidence is submitted, the auditor reviews the data to validate its accuracy and completeness. The auditor evaluates the organization's system and controls to ensure alignment with the Trust Service Principles.
- Design & Operating Effectiveness: The auditor checks if the evidence proves the control is well-designed and was operating effectively at the time. They look for specific details: Was the access approved before it was granted? Was the background check cleared before the start date?
- Walkthroughs: The auditor meets with your process owners to observe controls in real-time. This might involve screen-sharing to show how an admin creates a user or how a backup is restored.
- Inquiry & Clarification: If submitted evidence is unclear (e.g., a screenshot is blurry or a timestamp doesn’t match), the auditor flags it for clarification before marking it as a “pass.”
Phase 4: Reporting
After all evidence is reviewed and testing is complete, the auditor compiles the data into the final SOC 2 report. The SOC report is the formal output of the audit, providing assurance to customers and stakeholders.
- Test of Controls: The auditor lists every control tested, the specific method used to test it (Inspection, Observation, or Inquiry), and the result.
- Management Assertion: They review your description of the system to ensure it accurately matches the evidence they observed.
- Opinion & Exceptions: The auditor writes their formal opinion. If any evidence failed testing (e.g., a missing approval), it is noted as an “exception” in the report. You will have a chance to review the draft and add management responses to any exceptions before the final report.
A typical SOC 2 audit duration can vary from a few weeks to a few months depending on the organization's complexity and readiness.
A SOC 2 report can signal to customers a level of sophistication and demonstrates a commitment to security.
What to look for when hiring SOC auditors
Choosing the right SOC auditor affects the credibility of your report with potential clients, how smoothly the audit runs, and your long-term compliance program costs. Not all auditors deliver the same experience. The right SOC auditor should be able to address your organization's specific business needs and evaluate your security controls to ensure they align with compliance requirements.
Verify licensing and credentials
Confirm the firm is a licensed CPA practice authorized to perform SOC examinations under AICPA guidelines. This isn’t optional—only properly licensed firms can issue valid SOC reports. Ask about:
- Individual credentials: CPA, CISA, CISSP
- Cloud platform experience: AWS, Azure, Google Cloud certifications
- Familiarity with your technology stack
Evaluate communication and pricing
The best audit experience comes from auditors who:
- Provide clear, transparent pricing upfront (avoid firms that nickel-and-dime for every question)
- Assign a consistent engagement team rather than rotating junior staff each year
- Communicate proactively about milestones and deadlines
- Offer reasonable response times during evidence collection
Switching auditors frequently costs more than maintaining a relationship with a trusted partner who knows your systems.
Consider tooling and continuous compliance
Modern auditors often provide:
- Secure evidence portals with organized request tracking
- Integrations with ticketing systems, cloud providers, and identity platforms
- Support for continuous compliance rather than just annual interactions
- Automated control monitoring between audit periods
These capabilities can reduce your team’s workload and help you demonstrate compliance year-round rather than scrambling before each audit period.

FAQ: common questions about SOC auditors
Who is authorized to issue a valid SOC 2 report?
Only licensed CPA firms or CPA-led practices authorized by the AICPA can issue valid SOC 2 audit reports. While they may partner with cybersecurity experts for testing, the final issuance must come from the CPA firm
How should I choose the right SOC 2 auditor for my company?
Match the auditor to your company size, choosing Big Four firms for enterprise needs or boutique specialists for startups. You should also verify their industry experience, pricing transparency, and familiarity with your technology stack.
What are the four phases of a SOC 2 audit?
he audit progresses through defining evidence requirements, collecting and sampling evidence, testing operating effectiveness, and issuing the report. This workflow focuses on proving that your controls operated as designed during the audit period.
Which SOC 2 auditors are best for startups?
Startups often benefit from boutique specialists like Prescient Security, Johanson Group LLP, ConstellationGRC or Insight Assurance. These firms generally offer a personalized 'white-glove' experience and competitive pricing compared to global enterprise firms.
Can organizations outside the US use SOC auditors?
Yes. Many global SaaS providers pursue SOC 2 compliance in addition to ISO 27001 because US enterprise customers specifically request SOC reports.
How often should you engage SOC auditors?
For Type II reports, annual audits are standard. Your customers expect a current report covering the past 12 months. Whether to switch firms periodically or maintain continuity depends on your experience. Continuing with the same auditor offers benefits: they know your systems, reducing preparation time and avoiding repeated explanations. However, switching can bring fresh perspectives and sometimes better pricing through competitive pressure.
How Secureleap Can Help with Your SOC 2 Audit
Secureleap is a trusted partner for organizations seeking expert guidance and support throughout their SOC 2 audit journey. We specialize in assisting companies of all sizes—from startups to enterprises—in preparing for and successfully completing their SOC 2 compliance assessments. Our team works closely with you to streamline the audit process, helping you understand the key steps such as readiness assessment, evidence collection, and control activities testing.
By leveraging our deep knowledge of the SOC 2 framework and experience with various security frameworks, Secureleap ensures your organization meets regulatory requirements and industry standards. We provide tailored recommendations to protect customer data, address potential vulnerabilities, and demonstrate compliance to your stakeholders. Whether you are aiming for a SOC 2 Type I or Type II report, Secureleap offers personalized service to make your audit efficient, thorough, and aligned with your business needs.
Partner with Secureleap to navigate the complexities of SOC 2 audits confidently and unlock new business opportunities with a strong commitment to information security and customer trust.






