SOC 2 has two report types: Type 1 is a “snapshot in time” showing control design on a specific date, while Type 2 demonstrates those controls actually operated effectively over 6–12 months.
Key Takeaways
- SOC 2 has two report types: Type 1 is a “snapshot in time” showing control design on a specific date, while Type 2 demonstrates those controls actually operated effectively over 6–12 months.
- Enterprise and mid-market buyers almost always prefer or require SOC 2 Type 2, but many startups sensibly start with Type 1 to unblock deals faster and build their compliance foundation.
- Your decision should balance four key factors: sales urgency, control maturity, regulatory pressure, and the time you have to collect evidence before customer deadlines.
- Typical timelines run 4–8 weeks for Type 1 at $5k–$30k, while Type 2 requires 6–12 months of evidence collection plus $8k+ in audit costs, depending on organizational size and complexity.
- Most organizations benefit from a staged approach: achieve Type 1 first to validate control design, then transition to Type 2 within 6–18 months to demonstrate operational effectiveness and meet growing customer demands.
What Is SOC 2 and Why Do Type 1 vs Type 2 Reports Matter?
If you’re selling software or cloud services, you’ve likely encountered security questionnaires asking about your SOC 2 status. SOC 2 is a framework developed by the American Institute of Certified Public Accountants (AICPA) for assessing how service organizations protect customer data across five trust services criteria: security, availability, processing integrity, confidentiality, and privacy.

Unlike certifications with a simple pass/fail outcome, SOC 2 produces an attestation report where an independent CPA firm issues an opinion on your organization’s controls. The auditor examines your service organization’s system, evaluates the controls you’ve implemented, and provides their professional judgment on whether those controls meet the relevant trust services criteria.
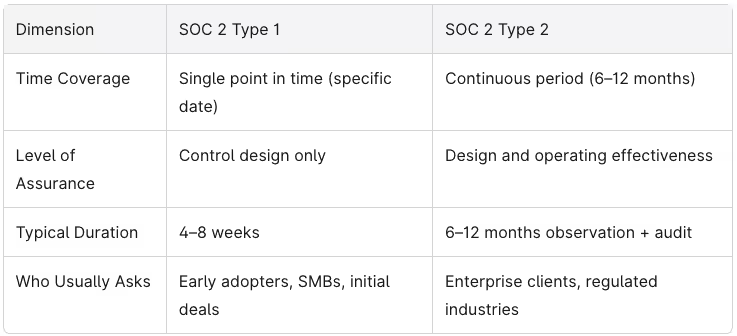
Here’s where the decision gets important: there’s one SOC 2 standard but two report types. Choosing between Type 1 and Type 2 directly affects your sales timelines, audit costs, and the level of assurance your potential customers receive. Understanding this distinction is critical for cloud computing organizations, IT managed service providers, and any service provider handling sensitive customer data.
SOC 2 primarily applies to SaaS companies, cloud providers, fintech platforms, healthtech vendors, and other organizations that store or process client data in cloud environments.
Quick Definitions: SOC 2 Type 1 vs SOC 2 Type 2
Let’s cut to the core distinction for readers who need a fast answer.
SOC 2 Type 1 is an attestation of whether controls were suitably designed and implemented as of a specific date. For example, “as of June 30, 2026.” The auditor confirms your policies, procedures, and systems are appropriately structured to meet control objectives—but they don’t test whether those controls actually worked over time.
SOC 2 Type 2 covers both design and operating effectiveness of controls over a defined audit period, typically 6–12 months. For example, “for the period July 1, 2025 through June 30, 2026.” The auditor examines evidence showing that your organization’s controls operated consistently throughout that monitoring period.
Key dimensions that differ between the two:
- Time horizon: Point-in-time snapshot vs. extended observation window
- Evidence required: Policy documentation vs. months of logs, tickets, and records
- Auditor testing depth: Design review vs. sample-based testing of actual performance
- Customer assurance level: “Controls exist” vs. “Controls work consistently”
When a prospect asks “Do you have a SOC 2?” they almost always mean “Do you have a recent SOC 2 Type 2 report?” unless otherwise specified.
Trust Services Criteria (TSC) – What Both Types Have in Common
Both Type 1 and Type 2 audits are based on exactly the same five trust services criteria published by the AICPA. The report type doesn’t change which criteria can be included—it only changes how deeply and over what time period those controls are tested.
Here’s what each TSC covers:
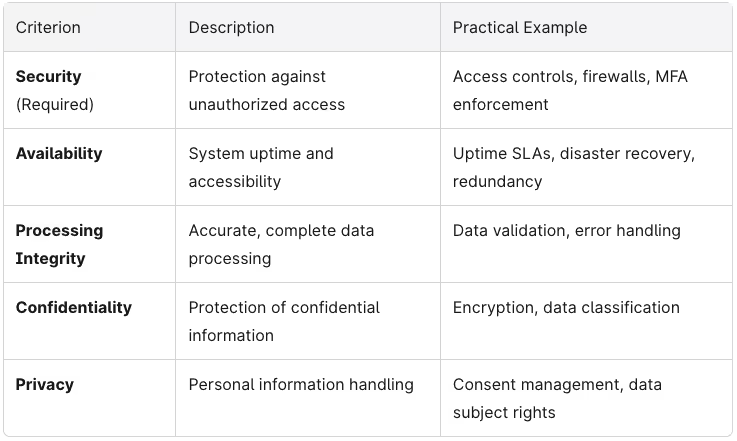
Most technology and SaaS vendors at minimum include security and often add availability and confidentiality to their audit scope. Organizations with heavy data processing requirements or those in regulated industries may also include processing integrity and privacy.
Both report types follow the same underlying COSO 2013 internal control framework, so investing in controls for Type 1 lays the groundwork for Type 2. The same controls are evaluated—the difference is whether the auditor checks if they existed on a date or if they operated effectively over months.
What Is SOC 2 Type 1? (Snapshot of Control Design)
A SOC 2 Type 1 report is a “point-in-time” assessment focused on control design and implementation. The auditor evaluates your policies, systems, and procedures as they existed on the examination date—essentially asking, “Are the right controls in place, and are they designed properly?”
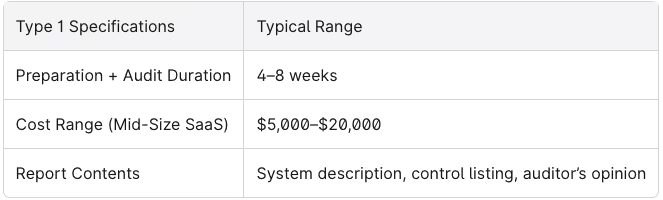
The typical audit scope for Type 1 includes:
- Documented policies (access control, change management, incident response)
- System diagrams and architecture documentation
- Onboarding and offboarding procedures
- Configuration screenshots and security settings
- Vendor management and risk assessment processes
Auditors verify that controls are in place and logically capable of meeting the selected trust services criteria. However, they don’t test months of operational evidence like recurring access reviews, quarterly vulnerability scans, or monthly backup verifications. It’s a design review, not a validation of consistent execution.
Type 1 is especially attractive when you’ve just implemented or overhauled your security program and cannot yet show 6–12 months of history but need something concrete for customer conversations.

Advantages of SOC 2 Type 1
- Faster to achieve: Often just a few weeks of preparation plus a short audit window, making it ideal under tight sales deadlines or funding milestones.
- Lower cost: Generally 30–50% less expensive than Type 2 because there’s no extended audit period and less sampling of historical evidence.
- Strong signal for early deals: Provides credible proof of serious security work for early adopters, angels, or Series A investors without requiring full operational history.
- Low-risk pilot: A practical way to test your system description, audit scope, and evidence collection processes before committing to a longer Type 2 period.
- Foundation for Type 2: Everything you document and implement for Type 1 carries directly into your future Type 2 efforts.
Real-world scenario: A 15-person B2B SaaS company lands a meeting with their first enterprise prospect. The security team requires a SOC 2 report before contract signing, but the deal needs to close within 90 days. A Type 1 report can be completed in time to unblock the deal, while the company continues building toward Type 2.
Limitations and When Type 1 Is Not Enough
Many mid-market and enterprise security teams treat Type 1 as a stepping stone, not an endpoint. They may accept it for initial vendor onboarding but require a Type 2 report within 6–12 months.
Type 1 doesn’t prove that recurring activities actually happen over time:
- Monthly log reviews and access certifications
- Quarterly disaster recovery tests
- Annual penetration testing and security awareness training
- Continuous vulnerability scanning and patching
Heavily regulated sectors—financial institutions, healthcare organizations, and payments processors—often explicitly require a recent SOC 2 Type 2 report as part of their vendor risk management programs. A Type 1 simply won’t satisfy their compliance requirements.
Type 1 reports also become “stale” relatively quickly, often within 6–12 months or after major system changes. If your organization’s security posture has evolved significantly since the report date, customers may question its relevance.
If you’re already operating at scale with thousands of customers, skipping directly to Type 2 is usually more aligned with market expectations.
What Is SOC 2 Type 2? (Evidence of Controls Working Over Time)

A SOC 2 Type 2 report covers both the design and the operating effectiveness of controls over a continuous period—commonly 6, 9, or 12 months. The auditor doesn’t just confirm controls exist; they test samples from the entire audit period to verify consistent execution.
During a Type 2 audit, auditors examine:
- Access logs and user provisioning/deprovisioning records
- Change management tickets and approval workflows
- Backup logs and restoration test results
- Vulnerability scan reports and remediation evidence
- Incident response records and resolution timelines
- Security awareness training completion records
For example, controls around logical access might be tested by reviewing 40–60 access logs from across the period to ensure no unauthorized disclosure occurred and that access reviews happened on schedule.
First-time SOC 2 Type 2 reports often cover a shorter initial period (e.g., 6 months) before moving to a standard 12-month cadence for subsequent reports. This allows organizations to demonstrate operational effectiveness without waiting a full year for their first Type 2.
Example Timeline:
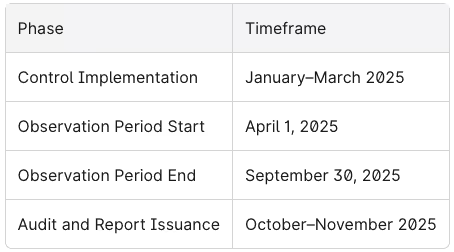
Type 2 is commonly viewed as the “gold standard” by procurement and security teams because it demonstrates not just intent but sustained execution of security measures.
Advantages of SOC 2 Type 2
- Higher customer assurance: Demonstrates that controls were not only present but consistently followed for the entire audit period, providing robust assurance about your current security posture.
- Meets enterprise requirements: Many RFPs, especially from financial institutions and healthcare organizations, explicitly list a “current SOC 2 Type 2 report” as mandatory.
- Faster security reviews: Vendors with recent Type 2 reports frequently move through procurement faster and face fewer follow-up questionnaires.
- Institutionalizes security: Maintaining annual Type 2 reports makes data security part of day-to-day operations rather than one-off projects.
- Benchmarking capability: Type 2 reports help leadership and boards track security maturity year over year and demonstrate continuous improvement.
Type 2 says “we’ve been using our controls correctly every day” versus Type 1’s mere “we’ve designed the right systems.”

Challenges and Trade-offs of Type 2
Type 2 demands more organizational maturity. You must have recurring processes running reliably—monthly access reviews, regular vulnerability scans, quarterly DR tests, ongoing security training—and the ability to prove them with timestamps and records.
Key challenges include:
- Extended timeline: The full observation period must elapse before the auditor can finalize the report, so it’s not a quick fix for a near-term RFP deadline.
- Higher costs: Audit costs increase due to extended scope and sampling, especially for larger environments with multiple products, regions, or data centers.
- Operational overhead: Teams must maintain evidence collection and continuous monitoring throughout the year, not just before the audit date.
- Risk of exceptions: If controls aren’t consistently executed, the audit process may uncover significant findings that require remediation before report issuance.
Going straight to Type 2 with immature security processes can be risky. Control failures during the observation period become documented exceptions in your report, potentially raising more concerns than a clean Type 1 would have.
Side-by-Side Comparison: SOC 2 Type 1 vs SOC 2 Type 2
Both report types use the same trust service principles, require an independent CPA firm, and contain similar sections: system description, management assertion, and auditor’s opinion. The fundamental difference is depth and time.
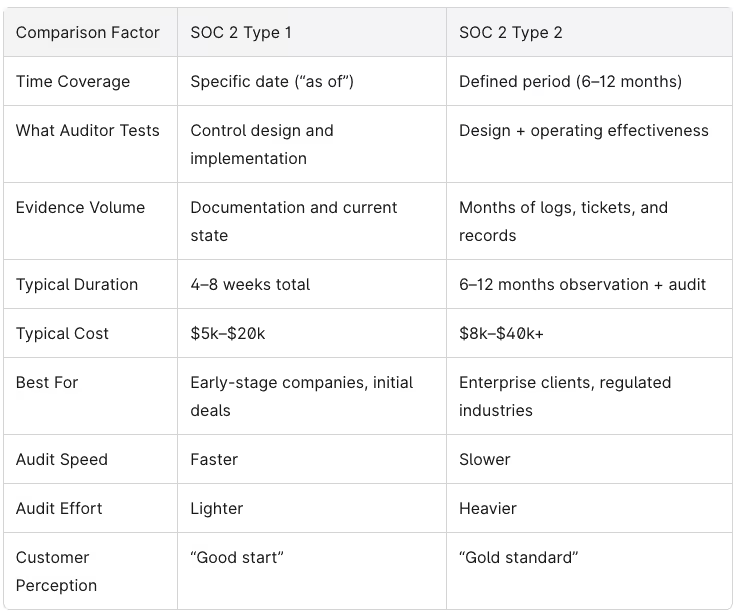
Type 1 answers: “Are your controls designed properly today?” Type 2 answers: “Have you actually followed those controls consistently for months?”
The choice comes down to whether speed or depth of assurance matters more for your current situation.
How to Decide: SOC 2 Type 1 vs Type 2 for Your Organization

There’s no universally “better” report. The right choice depends on customer expectations, company stage, control maturity, and how fast you need a report in hand. Here’s how to think through the decision:
Key Decision Factors:
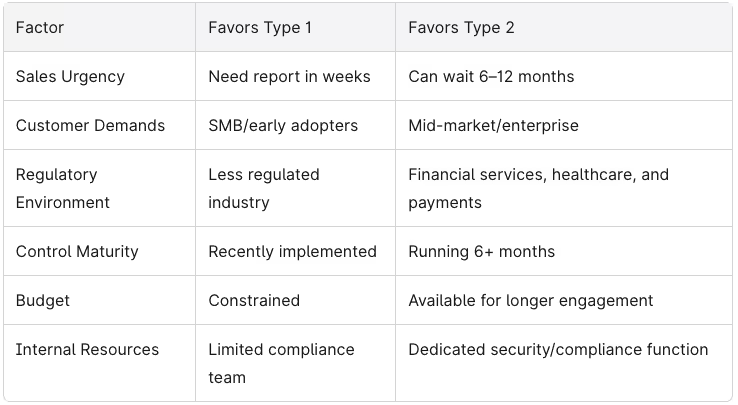
Typical Paths by Company Stage:
- Early-stage startups (pre-Series A): Start with Type 1 to demonstrate security commitment and unblock initial deals. Plan for Type 2 within 12–18 months.
- Growth-stage SaaS (Series A/B): Complete Type 1, then transition to Type 2 within 6–12 months as enterprise clients enter the pipeline.
- Mature or regulated providers: Often go straight to Type 2, especially if pursuing financial institutions or healthcare organizations from day one.
When a SOC 2 Type 1 Report Makes the Most Sense
Type 1 is the right choice when:
- You’ve just implemented your first formal security program and lack 6–12 months of operational history
- A single anchor customer needs evidence quickly to proceed with contract signing
- Internal resources are limited for ongoing evidence collection
- You’re primarily selling to early adopters or mid-market customers with flexible security requirements
- You’re planning to raise capital or enter partnerships within 3–6 months and need credible attestation for due diligence
Organizations in the 10–100 employee range often find Type 1 provides the right balance of speed, cost, and assurance for their current stage.
Strategic positioning: Frame Type 1 internally as “Phase 1” of a multi-year SOC compliance journey, not the final destination. Use the Type 1 project to refine your audit scope, documentation, and control ownership so the transition to Type 2 is smoother.
When You Should Go Directly to SOC 2 Type 2
Skip Type 1 and start with Type 2 when:
- Enterprise customers or regulated institutions have explicitly stated they require a Type 2 report before signing
- Your organization already follows established security frameworks (like ISO 27001) with mature, documented processes
- You manage highly sensitive or regulated data—PHI, payment card data, or large financial transaction volumes
- You can tolerate the upfront time and cost investment for long-term sales and reputational benefits
- Competitors in your space already have Type 2 reports, making it table stakes for your market
Some organizations run a short internal “mock Type 2” period before the official audit. This helps verify that recurring processes are reliable and evidence collection is consistent before committing to the formal observation window.
From Type 1 to Type 2: Building a Practical Roadmap
For teams intentionally planning to start with Type 1 and advance to Type 2 over the next 6–18 months, here’s a high-level roadmap:
Step 1: Conduct a Readiness Assessment Evaluate current controls against the required trust services criteria. Identify gaps in policies, procedures, and technical controls before engaging an auditor.
Step 2: Complete Type 1 Audit Document your control environment, implement missing controls, and complete the Type 1 examination. Use auditor feedback to identify areas needing strengthening.
Step 3: Close Identified Gaps Address any observations or recommendations from the Type 1 report. Strengthen processes that may struggle with sustained execution.
Step 4: Run Controls Consistently Operate your control environment for 6–12 months while collecting evidence. Assign clear owners for recurring controls:
- HR: Onboarding, offboarding, training
- IT: Access reviews, patch management
- DevOps: Backups, infrastructure monitoring
- Security: Vulnerability scanning, incident response
Step 5: Begin Type 2 Observation Period Start the formal audit period with your CPA firm. Maintain compliance efforts and evidence collection throughout.
Step 6: Complete Type 2 Audit The auditor samples evidence from across the period to verify control effectiveness. Receive your Type 2 report.
Plan your Type 2 audit period to align with business cycles. A July–June period works well for many North American SaaS companies, ensuring reports are ready ahead of peak selling seasons.
Track metrics like on-time completion of recurring tasks, incident response SLAs, and security awareness training completion rates to demonstrate readiness.
The Role of Automation and Tools in SOC 2 Type 1 and Type 2
While SOC 2 is a standard, many organizations rely on compliance platforms and automation to handle evidence collection, control monitoring, and auditor collaboration.
Automation is especially valuable for Type 2 because of the need to consistently gather logs, screenshots, tickets, and sign-offs across 6–12 months without overwhelming your team. Current trends show platforms like Vanta, Drata, and Secureframe can reduce Type 2 timelines from 12 to 8 months and cut costs by 20–30% through automated evidence collection.
Typical Automated Connections:
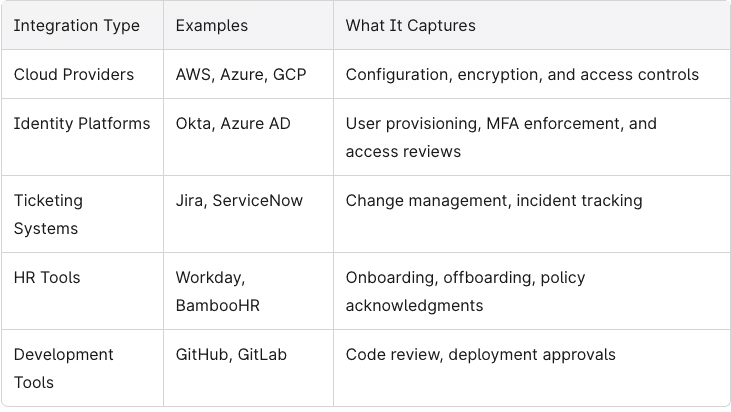
Even for Type 1, automation can shorten prep time by mapping existing controls to SOC 2 requirements and continuously flagging gaps before the audit date.
When evaluating tools, consider not just “getting the first report” but supporting a multi-year SOC 2 program, including renewals, additional frameworks (like ISO 27001 or HIPAA), and evolving client demands.
Conclusion: Choosing the SOC 2 Path That Supports Your Growth
SOC 2 Type 1 and Type 2 serve different but complementary purposes. Type 1 validates that your internal controls are properly designed at a specific point in time. Type 2 proves those same controls work in practice over months of actual operation.
The core decision guidance is straightforward: choose Type 1 when speed and foundational assurance are the priority. Choose Type 2 when enterprise clients, regulators, or organizational scale demand stronger, ongoing validation. Most growing companies will travel both paths—starting with Type 1 to unblock immediate opportunities, then advancing to Type 2 as customer expectations mature.
Treat SOC 2 as a continuous program. Review controls regularly, plan audit periods around your business calendar, and iterate from one reporting cycle to the next. Maintain compliance by building security into your daily operations rather than treating it as an annual project.
Create a simple internal decision document outlining why you chose Type 1, Type 2, or a staged approach. This helps you clearly explain your strategy to auditors, investors, and user entities during security reviews.
A well-chosen SOC 2 path doesn’t just satisfy compliance requests—it strengthens your organization’s security posture and builds the long-term customer trust that enables sustainable growth.
Frequently Asked Questions (FAQ)
What is the main difference between SOC 2 Type 1 and Type 2?
SOC 2 Type 1 is a point-in-time snapshot showing control design on a specific date. Type 2 demonstrates that those controls operated effectively over a continuous period, typically 6-12 months.
How long does a SOC 2 audit take?
Typical timelines run 4-8 weeks for Type 1. A SOC 2 Type 2 report requires a 6-12 month evidence collection period plus additional time for the audit.
How much does a SOC 2 audit cost?
Type 1 audits generally range from $5,000 to $30,000. Type 2 reports are typically 30-50% more expensive due to extended audit periods. More Info.
Should a startup choose SOC 2 Type 1 or Type 2?
Many startups start with Type 1 to unblock deals faster. However, enterprise buyers almost always prefer or require SOC 2 Type 2.
Is SOC 2 mandatory, and who typically asks for it?
SOC 2 is not required by law in most jurisdictions, but it has become a de facto requirement for cloud and SaaS vendors. Procurement teams, security teams, and sometimes regulators or large partners commonly request a current SOC report during vendor due diligence. Financial institutions and healthcare organizations are particularly likely to require SOC 2 as part of their vendor risk management processes.
How long is a SOC 2 Type 1 or Type 2 report considered valid?
There’s no official expiration date, but industry standards treat reports as current for about 12 months from the end of the audit period for Type 2. For Type 1, customers often consider reports relevant for 6–12 months from the as-of date, especially if there have been no major system changes. After that window, customers may request updated reports or ask about changes since the report date.
Can we skip Type 1 and go straight to Type 2 for our first SOC 2?
Yes, it’s possible and common for mature or regulated organizations to go directly to Type 2. However, you must already have well-documented, consistently operating controls and be prepared for more extensive evidence collection over several months. Organizations with existing security frameworks like ISO 27001 often have the foundation needed to start with Type 2.
Does SOC 2 cover legal requirements like GDPR, HIPAA, or PCI DSS?
SOC 2 is separate from these regulations and industry standards, but many cybersecurity controls overlap. A SOC 2 report can support regulatory compliance efforts and vendor risk conversations, but it doesn’t automatically guarantee full GDPR, HIPAA, or PCI DSS compliance. Think of SOC 2 as complementary to these requirements—demonstrating strong data protection practices—but not a replacement for specific regulatory obligations.
How should we talk about SOC 2 to customers while we are still in progress?
Be transparent about your current status. Use clear language like “in readiness phase,” “Type 1 scheduled for Q2 2026,” or “Type 2 period running July 2025–June 2026.” Share your roadmap and timeline when appropriate. Avoid implying you have a completed report when you don’t—security teams will verify, and misrepresentation damages trust. Many customers appreciate seeing a concrete plan with dates, even if the report isn’t yet complete.
Final Take: Get SOC 2 Certification Fast and Affordable with Secureleap
Achieving SOC 2 certification is a critical step in demonstrating your commitment to data security and winning the trust of enterprise customers. While the process can seem complex and costly, partnering with the right experts can make all the difference.
Secureleap specializes in helping organizations obtain SOC 2 certification quickly and at a very competitive price. With tailored services designed to streamline your audit process, reduce preparation time, and manage costs effectively, Secureleap ensures you get a credible, customer-trusted SOC 2 report without unnecessary delays or expenses.
Whether you're a startup or a growing mid-market company, Secureleap’s expertise and efficient approach can help you navigate the compliance journey smoothly, so you can focus on what matters most—growing your business with confidence.
Contact Secureleap today to learn how we can support your SOC 2 compliance needs and accelerate your path to certification.