Key Takeaways
- SOC 1 focuses on Internal Control over Financial Reporting (ICFR), while SOC 2 focuses on security and the AICPA’s Trust Services Criteria (TSC).
- Both SOC 1 and SOC 2 have Type I (point-in-time) and Type II (over a defined period, typically 6–12 months) reports.
- Most SaaS startups and cloud-based vendors selling to enterprises in 2024–2026 primarily need SOC 2, not SOC 1.
- SOC 2 is not a certification—it’s an attestation report issued by an independent CPA firm that enterprise customers request during security due diligence.
- SecureLeap helps early-stage startups decide between SOC 1 and SOC 2, prepare for audits, and implement platforms like Drata, Vanta, and Secureframe.
What Is the Difference Between SOC 1 and SOC 2 Reports?
When prospective customers or business partners ask for your SOC report, they’re looking for independent assurance about how your company manages risk. But SOC 1 and SOC 2 serve fundamentally different purposes: SOC 1 addresses financial reporting controls, while SOC 2 evaluates information security and operational controls around customer data.
Both are part of the AICPA System and Organization Controls (SOC) framework, performed by independent CPA firms under SSAE 18 standards. The key differences lie in what each report examines and who typically requests it.
SOC 1 is scoped around controls that impact user entities’ financial statements—think payroll processing, billing systems, or transaction handling that flows directly into a client’s general ledger. External auditors performing financial statement audits rely on SOC 1 reports to understand how a service organization’s internal controls might affect their clients’ financial reporting accuracy.
SOC 2, on the other hand, evaluates a service organization’s controls against the five Trust Services Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy. It’s the go-to for demonstrating data protection and data security to enterprise buyers conducting vendor management programs.
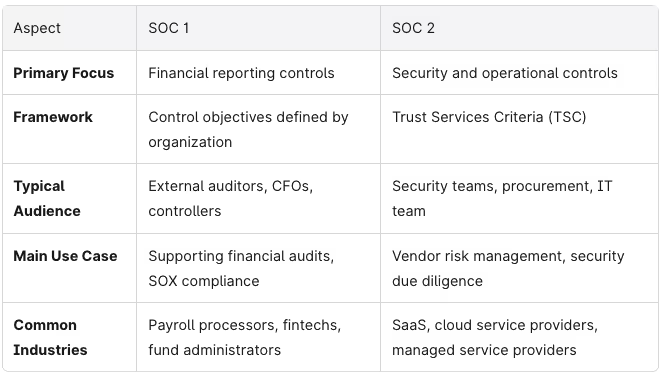
Many startups ask for “SOC certification” without realizing they must specifically choose SOC 1, SOC 2, or both. The good news is that your customer contracts and RFPs usually make the right choice clear—security questionnaires asking about data handling point to SOC 2, while questions about financial controls and transaction processing suggest SOC 1.

What Is a SOC 1 Report?
A SOC 1 report provides assurance on controls at a service organization that are relevant to user entities’ Internal Control over Financial Reporting (ICFR). If your service touches your customers’ financial statements—whether through payroll, billing, claims processing, or transaction handling—SOC 1 is likely on your radar.
SOC 1 reports are most relevant to:
- Payroll processors handling employee compensation data
- Billing platforms processing invoices and revenue
- Loan servicing companies managing payment streams
- Fund administrators tracking investment transactions
- Fintechs whose systems feed directly into customer ledgers
The report is performed under SSAE 18, AT-C Section 320, and is often used to support external financial audits under regulations like the Sarbanes-Oxley Act (SOX) of 2002. When a company outsources business processes that affect their financial data, their auditors need visibility into those service organizations to verify that financial reporting processes remain accurate.
An important distinction: SOC 1 does not evaluate your overall cybersecurity posture. It only considers security controls to the extent they affect financial reporting assertions such as completeness, accuracy, and timeliness. If your customers primarily care about data privacy and security breaches rather than accounting accuracy, SOC 2 is likely the better fit.
Typical SOC 1 Control Areas:
- Change management for financial systems
- Access controls to GL-impacting systems
- Input and output controls for financial transactions
- Reconciliation procedures
- Processing completeness and accuracy checks
- Segregation of duties in information technology processes
SOC 1 Type I vs SOC 1 Type II
SOC 1 comes in two flavors—Type I and Type II—differing primarily in time coverage and depth of testing.
Type I provides an assessment of the design of controls at a specific date (e.g., “as of June 30, 2025”). It answers the question: “Do you have appropriate controls in place?” This snapshot approach works for organizations needing quick documentation but doesn’t prove controls operated effectively over time.
Type II assesses both design and operating effectiveness over a defined period, commonly 6 to 12 months (e.g., “July 1, 2025 to June 30, 2026”). The auditor tests whether controls operated as designed throughout that window, providing stronger evidence to user entities and their auditors.
First-time SOC 1 reports for young companies often start as Type I, then transition to Type II in the next cycle. This approach satisfies initial audit requirements while giving the organization time to mature its internal controls and demonstrate operational effectiveness.
SecureLeap typically recommends a readiness phase of 6–8 weeks before engaging a SOC 1 auditor, especially for startups going through their first SOX-relevant vendor reviews. This preparation ensures your control objectives are properly defined and your team can provide the evidence auditors need.
What Is a SOC 2 Report?
A SOC 2 report evaluates controls at a service organization relevant to the AICPA Trust Services Criteria (TSC). Unlike SOC 1’s financial focus, SOC 2 addresses how you protect, store, and process client data—making it essential for modern technology companies.
SOC 2 is widely requested from:
- SaaS providers serving enterprise customers
- Cloud infrastructure and cloud service providers
- Managed service providers handling IT operations
- IT service providers with access to client systems
- B2B platforms that store or transmit customer data
The five Trust Services Criteria form the backbone of every SOC 2 audit:
- Security (required for all SOC 2 reports): Protection against unauthorized access through logical and physical safeguards
- Availability: Systems perform as committed in SLAs and contracts
- Processing Integrity: Data processing is complete, accurate, timely, and authorized
- Confidentiality: Sensitive information is protected throughout its lifecycle
- Privacy: Personal information is collected, used, and disclosed appropriately
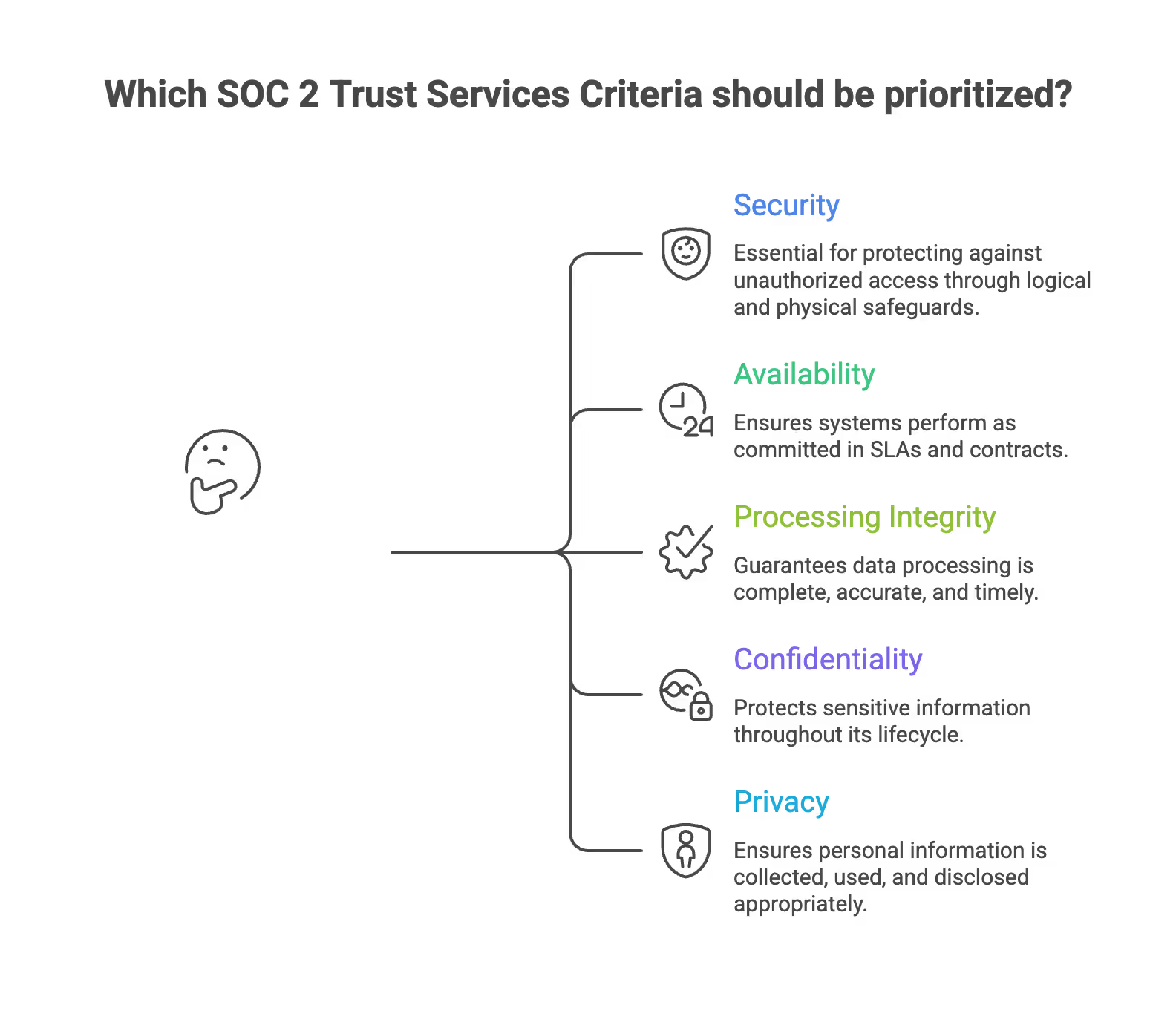
Most startups begin with Security (the common criteria) and add additional criteria over time based on customer requirements. A company processing customer data for analytics might add Confidentiality, while one offering uptime guarantees would include Availability.
SOC 2 audits are conducted under SSAE 18, AT-C 105 and AT-C 205. The final report includes an auditor’s opinion, a detailed system description, tests of controls, and results—providing digital assurance to prospective customers about your security posture.
These reports are typically shared under NDA with enterprise customers as part of security due diligence and vendor management programs. They’ve become the de facto standard for demonstrating compliance in tech-heavy industries, often replacing lengthy vendor questionnaires and on-site security assessments.

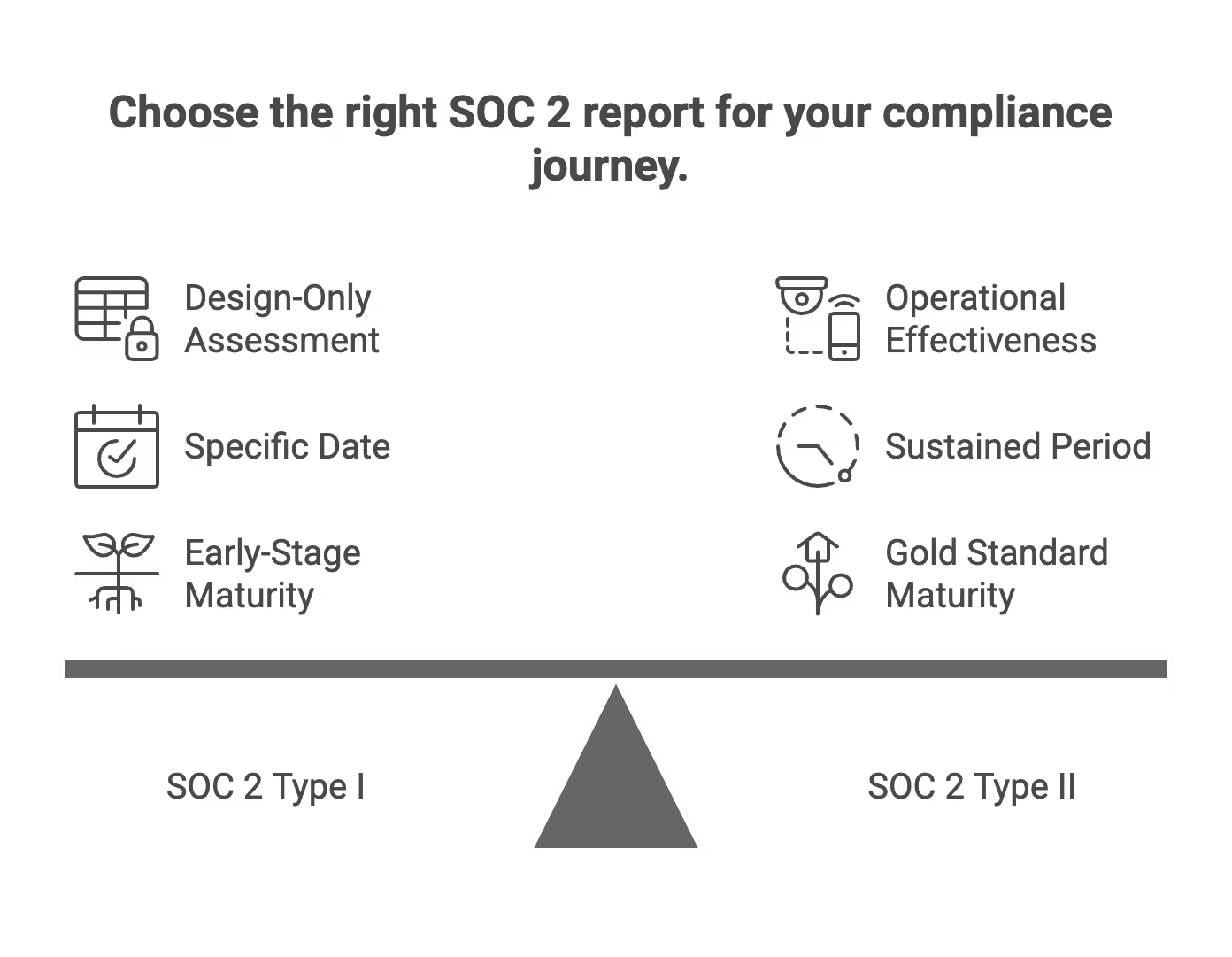
SOC 2 Type I vs SOC 2 Type II
Similar to SOC 1, SOC 2 offers both Type I and Type II reports—and understanding the difference is critical for planning your compliance journey.
SOC 2 Type I is a “design-only” report, assessing whether your security controls are suitably designed as of a specific date. It’s ideal for early-stage startups needing a fast signal of maturity for sales conversations, often achievable after implementing controls for 30–60 days. Think of it as proof that you’ve built the right security architecture.
SOC 2 Type II is the gold standard that most enterprise security teams expect. It covers control design plus operational effectiveness over 3, 6, or 12 months—with 6–12 month periods being most respected in 2025–2026 RFPs. This type ii report demonstrates that your controls not only exist but are operating effectively over a sustained period.
The practical path for many SecureLeap clients:
- Year One: Pursue a quick SOC 2 Type I to unblock enterprise deals and demonstrate compliance maturity
- Year Two: Complete a SOC 2 Type II once monitoring, logging, and incident response processes have matured
Compliance automation platforms (Drata, Vanta, Secureframe) combined with SecureLeap’s vCISO guidance significantly reduce the time needed to maintain evidence for Type II reports. What once required months of manual evidence collection can now happen through continuous monitoring and automated artifact gathering.
SOC Controls and Trust Services Criteria
“SOC controls” refer to the specific policies, procedures, and technical safeguards designed to meet SOC 1 identified control objectives or SOC 2 Trust Services Criteria. Understanding how these controls map to audit requirements is essential for efficient preparation.
For SOC 2, the Trust Services Criteria published by the AICPA (most recently updated in 2017 and periodically refined) provide the framework for designing and testing controls. Rather than prescribing specific technologies, the criteria establish outcomes your controls must achieve—giving flexibility in how you implement them.
Example SOC 2 Security Controls for Startups:
- Centralized identity and access management (SSO, MFA enforcement)
- Vulnerability management with defined scanning cadence
- Secure SDLC practices and code review requirements
- Vendor risk management for third-party services
- Incident response procedures and tabletop exercises
- Logging, monitoring, and alerting for security events
- Encryption for data at rest and in transit
Written, version-controlled policies serve as the foundation for any SOC audit. You’ll need documentation covering information security, access control, change management, incident response, and risk management processes at minimum. Auditors test not just whether controls exist, but whether your organization follows its stated policies.
SecureLeap helps seed–Series B teams translate Trust Services Criteria into practical, lightweight controls that match their specific technology stack—whether that’s AWS, GCP, Azure, Kubernetes, or modern CI/CD pipelines. The goal is building a security program that satisfies auditors without creating operational drag on engineering teams.
SOC 1 vs SOC 2 – How to Choose for Your Business
Many founders and CTOs aren’t sure whether prospects need SOC 1, SOC 2, or both. The answer should be driven by how customers actually use your service and what risks they’re trying to mitigate.
Here’s a simple decision framework:
- If your service affects customers’ financial statements or ledger balances → consider SOC 1
- If you host, process, or analyze customer data regardless of financial impact → consider SOC 2
- If you do both (common in fintech and payroll) → you may need both a SOC 1 and SOC 2
Concrete examples for 2026:
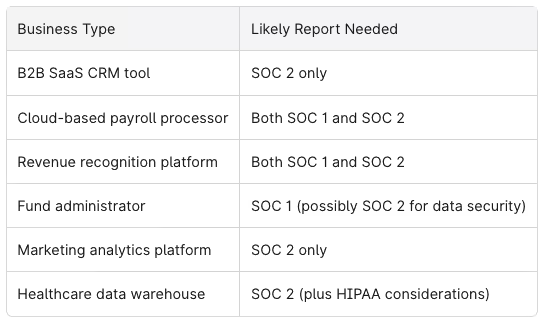
SOC 2 is typically the first ask in security questionnaires from large enterprises, healthcare systems, and financial institutions. It often appears alongside expectations for ISO 27001, compliance with the Health Insurance Portability and Accountability Act (HIPAA), the General Data Protection Regulation (GDPR), or PCI DSS—depending on your industry.
SecureLeap routinely reviews customer contracts, security addenda, and RFPs for clients to recommend the optimal report path and timing. This readiness assessment balances sales urgency with practical audit preparation, ensuring you pursue the right SOC compliance for your specific situation.
Other SOC Reports: SOC 3 and Beyond
Beyond SOC 1 and SOC 2, the AICPA offers additional report types worth understanding.
SOC 3 is a high-level, public-facing report covering the same Trust Services Criteria as SOC 2 but without detailed control descriptions or test results. Organizations typically obtain a SOC 3 only after completing a SOC 2 Type II, then publish it on their website or marketing materials as a transparency leader trust signal.
The AICPA has also introduced specialized reports:
- SOC for Cybersecurity: Focuses on enterprise-wide cybersecurity risk management
- SOC for Supply Chain: Addresses controls in production and distribution systems
These specialized reports remain less common in early-stage startup ecosystems compared to SOC 2. Most startups should not prioritize SOC 3 or specialized SOC reports until completing at least one mature SOC 2 cycle.
SecureLeap can help plan a roadmap beyond SOC 2 if customers or regulators later require SOC for Cybersecurity or ISO 27001 certification, ensuring your internal corporate governance and risk management processes scale with your business.
Cost and Timeline: SOC 1 vs SOC 2 for Startups
Actual costs vary significantly by scope, company size, and auditor selection, but realistic budgeting helps avoid surprises. Plan for both audit fees and the preparation work required to get audit-ready.
Typical Cost Ranges:
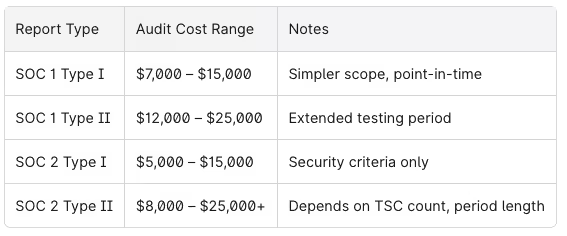
Readiness and remediation work—developing policies, implementing controls, deploying tooling—can add similar or greater costs, especially for companies without an existing security program. A startup going from zero to SOC 2 Type I might spend $10,000–$40,000 on preparation before audit fees.
Realistic Timelines for First SOC 2:
- Readiness phase: 4–8 weeks for a lean SaaS startup using automation tools
- Control observation period: 3–12 months for Type II
- Audit fieldwork and report: 2–4 weeks after observation period ends
SecureLeap offers bundled services—readiness assessment, vCISO leadership, penetration testing, and coordination with auditors and automation platforms—to compress timelines while keeping your program defensible for regulatory oversight.

How SecureLeap Helps You Navigate SOC1 and SOC2
SecureLeap is a B2B cybersecurity and compliance partner specializing in seed–Series B startups and SMBs. We understand that early-stage companies need to demonstrate compliance quickly to close enterprise deals—without building a massive internal security team.
Our core services include:
- SOC 2 Readiness: Gap assessment, policy development, control design, and evidence preparation
- SOC 1 Scoping and Readiness: Defining key control objectives and preparing documentation for financial reporting controls
- vCISO Leadership: Fractional security leadership to guide strategy and handle security questionnaires
- Penetration Testing: Technical validation that complements your compliance program
- Ongoing Compliance Operations: Maintaining audit readiness between cycles
We also support ISO 27001 certification, HIPAA compliance, and PCI DSS—helping companies build a unified security program instead of treating each audit as a separate checklist. This integrated approach means controls you implement for SOC 2 also support future certifications.
SecureLeap helps clients select and implement compliance automation tools (Drata, Vanta, Secureframe), then coordinates smoothly with independent auditors to minimize disruption to engineering and product teams. We’ve seen what works across dozens of startups and bring that pattern recognition to every engagement.
Ready to determine your compliance path? Schedule a free consultation to review your customer requirements, decide between SOC 1 and SOC 2, and build a practical roadmap to audit readiness and long-term security maturity.
FAQ: SOC 1 vs SOC 2
Do we need both SOC 1 and SOC 2?
Only services that directly impact customers’ financial statements typically need SOC 1. Many SaaS vendors only need SOC 2 unless they process transactions that flow into financial statements. A CRM platform needs SOC 2; a payroll processor likely needs both. Review your customer contracts—they usually specify which reports are required.
Is SOC 2 a certification?
No, SOC 2 is not a “certification” but an attestation report issued by a CPA firm. Unlike ISO 27001 where you receive a certificate, SOC 2 produces a detailed report that customers review. Enterprise buyers will ask for your latest report and management responses to any exceptions rather than a certificate to hang on your wall.
How often should we renew SOC reports?
Most enterprises expect updated SOC 1 and SOC 2 Type II reports every 12 months. The report covers a specific audit period, and customers want assurance that controls operated recently—not two years ago. Bridge letters can cover short gaps between audit periods, but planning for annual renewals keeps you responsive to vendor questionnaires.
How does SOC 2 compare to ISO 27001?
SOC 2 is an attestation for a specific period and system description, while ISO 27001 is a certifiable information security management system (ISMS) standard. SOC 2 is more common for U.S. enterprise sales; ISO 27001 carries more weight internationally. Many scaling companies eventually pursue both, typically starting with SOC 2 to support initial enterprise deals.
When should an early-stage startup start working on SOC 2?
Start readiness work 3–6 months before your first large enterprise deals or before a major funding round where investors may ask about security posture. Earlier is better—retrofitting security controls is harder than building them into your development practices from the start. SecureLeap can help founders assess ideal timing based on current pipeline and customer demands.






