Author: Marçal Santos, vCISO | +20 Years Cybersecurity Experience
Introduction
SOC 2 compliance is a cybersecurity framework developed by the American Institute of Certified Public Accountants (AICPA) that establishes how service organizations should protect customer data through standardized security controls and operational practices. This voluntary compliance standard has become essential for SaaS companies, cloud services providers, and any organization that stores, processes, or transmits sensitive customer data on behalf of other businesses.

This guide covers SOC 2 requirements, the five trust services criteria, audit types, implementation steps, and ongoing compliance maintenance. It focuses specifically on SOC 2 and excludes SOC 1 (financial reporting controls) and SOC 3 (general-use reports). The target audience includes compliance managers, IT security professionals, and decision-makers at service organizations seeking to demonstrate data protection capabilities to business partners and user entities.
Direct answer: SOC 2 compliance is achieved when a third party auditor—specifically certified public accountants—validates that a service organization’s controls meet the trust services criteria for protecting customer data, with certification requiring either a point-in-time assessment (Type 1) or evaluation of operational effectiveness over 3-12 months (Type II report).
By the end of this guide, you will understand:
- How the five trust services criteria establish your compliance foundation
- When to pursue Type 1 versus Type II report certification
- Which internal controls and security policies your organization needs
- How to prepare for a SOC 2 audit and collect required evidence
- What ongoing activities maintain compliance and audit readiness
Understanding SOC 2 Compliance Framework
SOC 2 emerged from the AICPA’s System and Organization Controls suite to address growing concerns about data security among service organizations handling third-party information. Unlike prescriptive frameworks such as ISO 27001, SOC 2 takes a principle-based approach—asking whether your organization controls adequately protect customer data rather than mandating specific technical implementations.
This flexibility makes SOC 2 particularly valuable for organizations of varying sizes and industries. The framework requires you to design, implement, and document controls aligned with relevant trust principles, then demonstrate those controls are operating effectively over time.

Trust Services Criteria Foundation
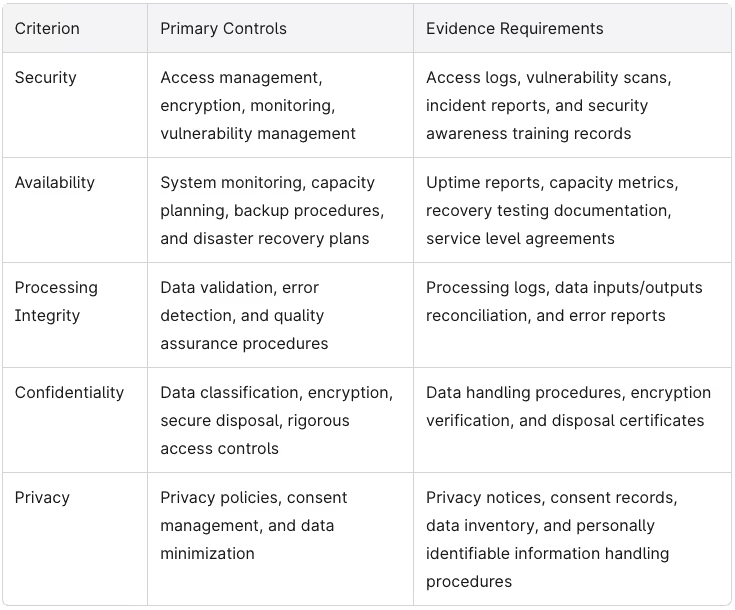
The security criteria form the mandatory baseline for every SOC 2 audit, encompassing measures to prevent and detect unauthorized access, security incidents, and data breaches. This security principle addresses access controls, intrusion detection, vulnerability scans, encryption protocols, and security awareness training.
Four additional criteria—availability processing integrity confidentiality and privacy—are optional and selected based on your specific business practices and customer requirements:
- Availability focuses on system availability through disaster recovery plans, capacity planning, and business continuity measures
- Processing Integrity ensures data processing activities produce accurate outputs and that data integrity is maintained throughout system processing
- Confidentiality protects confidential data and intellectual property through encryption and rigorous access controls
- Privacy governs how you collect, use, and disclose personally identifiable information and protected health information
Each criterion guides control implementation and determines what evidence auditors will examine during assessment.
Service Organization Scope
Cloud services providers, SaaS companies, managed IT services, and database-as-a-service vendors represent primary candidates for SOC 2 certification. Any organization that processes, stores, or transmits sensitive data on behalf of clients falls within the framework’s scope.
Qualifying data processing activities include hosting customer applications, managing customer data in multi-tenant environments, providing infrastructure services, and handling sensitive information like financial data or protected health information. Understanding your scope helps determine which specific criteria apply and directly influences your audit type selection.
SOC 2 Audit Types and Assessment Approaches
With the trust services criteria establishing what controls you need, the next consideration is how auditors will evaluate your service organization’s controls through either Type 1 or Type II report assessments.
Type 1 vs Type 2 Reports
A Type 1 report evaluates the design and operating effectiveness of your controls at a single point in time. Auditors assess whether you have implemented appropriate security controls, documented policies, and established processes that address the relevant trust principles. This snapshot approach requires moderate effort and offers faster certification, making it suitable for organizations new to SOC 2 or those needing quick proof of compliance for business partners.
A Type II report examines both design and operating effectiveness over a period of 3-12 months. Auditors test whether same controls operate consistently—reviewing quarterly access reviews, examining incident response documentation, and verifying that internal controls function as intended throughout the observation period. This rigorous assessment signals stronger operational effectiveness to buyers and provides deeper assurance about your security posture.
Choose Type 1 when establishing initial certification or when customers accept entry-level assurance. Pursue Type II when business partners require proven operational history, when serving enterprise customers, or when handling highly sensitive customer data.

Auditor Requirements and Selection
Only licensed CPA firms can perform SOC 2 audits. The third party auditor must maintain independence from your organization and possess relevant industry expertise. Look for firms with AICPA accreditation and experience in your sector—whether cloud services, financial services, or healthcare.
Professional qualifications extend beyond licensing to include familiarity with your technology stack, understanding of controls relevant to your operations, and experience with similar service organizations. The right auditor becomes a valuable partner in strengthening your information security practices.
Report Distribution and Usage
SOC 2 reports are restricted-use documents intended for management, user entities, and business partners who need assurance about your organization controls. Unlike general-use SOC 3 reports, SOC 2 findings contain detailed information about your control environment.
Organizations commonly use SOC 2 reports for customer due diligence during vendor management evaluations, demonstrating regulatory compliance to regulators, and providing evidence to existing and prospective business partners. Understanding report usage helps frame your implementation planning and prioritize controls relevant to customer requirements.

SOC 2 Implementation Process and Control Design
Moving from audit selection to practical execution, successful SOC 2 implementation requires systematic preparation across documentation, technical controls, and organizational processes.
Pre-Audit Preparation Steps
Allow 6-12 months for comprehensive readiness when targeting a Type II report. The preparation timeline should account for gap remediation, policy development, and evidence collection before engaging your auditor.
- Conduct gap analysis against Trust Services Criteria — Assess existing controls against each applicable criterion to identify deficiencies in access controls, monitoring, documentation, and data protection practices.
- Develop policies and procedures documentation — Create security policies covering access management, data handling, incident response, and vendor management. Document standard operating procedures for employee onboarding/offboarding, code deployment, and security incidents.
- Implement technical and administrative controls — Deploy security tools including multi-factor authentication, role-based access controls, encryption (TLS for transit, AES-256 at rest), intrusion detection, and antivirus software. Establish administrative controls like risk assessments and asset inventories.
- Establish evidence collection and monitoring processes — Implement automated logging systems with centralized repositories for access logs, change management records, and security incident documentation. Create schedules for quarterly reviews and periodic testing.
- Train personnel on SOC 2 requirements and responsibilities — Conduct security awareness training covering data protection obligations, incident reporting procedures, and individual accountability for maintaining a strong control environment.
Trust Services Criteria Implementation Comparison
Prioritize criteria based on your business model and customer requirements. A SaaS company handling financial data may emphasize all five trust services criteria, while a development tools provider might focus primarily on security availability processing integrity. Customer access to sensitive information often drives Confidentiality criteria inclusion.
Understanding these distinctions helps allocate resources effectively and prepares your organization for common implementation challenges.

Common Challenges and Solutions
Service organizations frequently encounter predictable obstacles when pursuing SOC 2 certification. Addressing these proactively accelerates audit readiness and reduces the risk of unfavorable findings.
Inadequate Evidence Collection
Many organizations maintain effective controls but fail to document them consistently. Without evidence, auditors cannot verify design and operating effectiveness.
Implement automated logging and monitoring systems that capture control activities in real-time. Establish a centralized evidence repository organized by criterion, and assign ownership for maintaining documentation throughout the audit period.
Control Design Gaps
Organizations often discover that existing controls don’t fully address trust service principles or lack the specificity auditors require.
Engage experienced SOC 2 consultants for independent gap analysis before audit engagement. Their perspective helps identify blind spots in risk management, vendor management, and information security practices that internal teams may overlook.
Resource and Timeline Constraints
Comprehensive SOC 2 readiness demands significant investment in personnel, technology, and process development—resources many growing organizations struggle to allocate.
Start with a Type 1 audit for initial certification to demonstrate commitment while building operational maturity. Plan a 6-12 month timeline for Type II readiness, allowing adequate time to establish control history and collect evidence across multiple review cycles.
Ongoing Compliance Maintenance
SOC 2 certification isn’t a one-time achievement. Controls must operate effectively continuously, and any exceptions appear in annual reports.
Establish quarterly internal assessments mirroring auditor testing procedures. Implement continuous monitoring programs that flag control deviations in real-time, enabling rapid remediation before exceptions accumulate.
Conclusion and Next Steps
SOC 2 compliance provides service organizations with a proven framework for demonstrating data protection capabilities to business partners, customers, and regulators. By implementing controls aligned with the five trust services criteria and validating them through independent certified public accountants, you establish trust that translates to competitive advantage and expanded market opportunities.
Immediate actions to begin your SOC 2 journey:
- Assess your current security posture against the trust services criteria
- Define which criteria (security availability processing integrity confidentiality privacy) apply to your operations
- Document existing controls and identify gaps requiring remediation
- Engage a qualified CPA firm with relevant industry experience
- Establish evidence collection processes and assign ongoing ownership
Organizations successfully maintaining SOC 2 compliance often explore ISO 27001 integration for international markets, industry-specific requirements like HIPAA for protected health information, and advanced security frameworks that build upon the SOC 2 foundation.
FAQ
What is SOC 2 compliance?
SOC 2 is a cybersecurity framework developed by the AICPA that establishes how service organizations protect customer data through standardized security controls. It is essential for SaaS companies and cloud providers to demonstrate they safeguard sensitive information.
What are the 5 Trust Services Criteria for SOC 2?
The five criteria are Security, Availability, Processing Integrity, Confidentiality, and Privacy. Security is the only mandatory category, while the others are optional based on specific business needs and customer requirements.
What is the difference between SOC 2 Type 1 and Type 2?
A Type 1 report evaluates the design of security controls at a single point in time. A Type 2 report assesses the operational effectiveness of those controls over a period of 3 to 12 months.
Who can perform a SOC 2 audit?
Only licensed CPA firms can perform SOC 2 audits. Organizations must select an independent auditor with relevant industry experience to validate that controls meet the Trust Services Criteria.
How long does SOC 2 implementation take?
Preparing for a Type 2 report typically requires 6 to 12 months for gap analysis, policy development, and evidence collection. This timeline ensures the organization is ready for the audit observation period.
Additional Resources
- AICPA Trust Services Criteria documentation: Official guidance on criterion definitions, illustrative controls, and points of focus for each trust principle
- SOC 2 audit costs calculator: Check out SecureLeap's SOC 2 audit calculator to quickly evaluate your organization's compliance costs.
Final Take: Get SOC 2 Certification Fast and Affordable with Secureleap
Achieving SOC 2 certification is a critical step in demonstrating your commitment to data security and winning the trust of enterprise customers. While the process can seem complex and costly, partnering with the right experts can make all the difference.
Secureleap specializes in helping organizations obtain SOC 2 certification quickly and at a very competitive price. With tailored services designed to streamline your audit process, reduce preparation time, and manage costs effectively, Secureleap ensures you get a credible, customer-trusted SOC 2 report without unnecessary delays or expenses.
Whether you're a startup or a growing mid-market company, Secureleap’s expertise and efficient approach can help you navigate the compliance journey smoothly, so you can focus on what matters most—growing your business with confidence.
Contact Secureleap today to learn how we can support your SOC 2 compliance needs and accelerate your path to certification.






