For B2B SaaS founders, the “Vendor Security Questionnaire” is often the bottleneck that kills sales momentum. When an enterprise prospect asks for your SOC 2 report, they aren’t just asking about firewalls; they are asking if your business is mature enough to be a trusted vendor.
SOC 2 compliance is quickly becoming a vital asset for startups handling sensitive customer data. Achieving SOC 2 and other compliance certifications demonstrates your commitment to security and can be showcased to clients and investors, building customer trust and establishing credibility. The SOC 2 compliance journey is an ongoing process that not only helps identify and address potential weaknesses, significantly lowering your startup’s risk profile, but also serves as a powerful marketing tool and provides a competitive advantage in crowded markets. Large enterprise customers often require a SOC 2 report as a mandatory part of vendor due diligence, and having SOC 2 compliance simplifies engagement with potential clients.
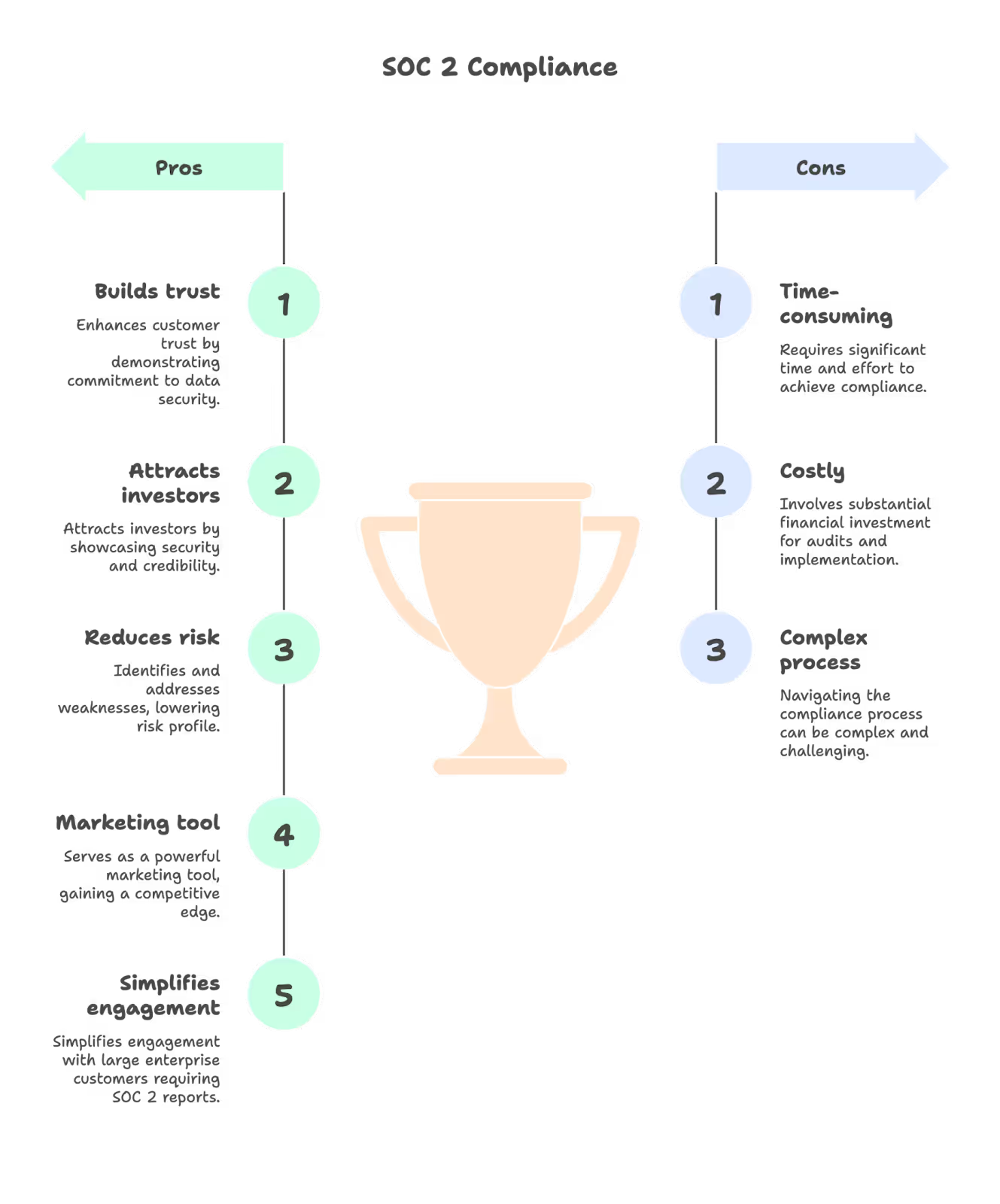
To succeed, startups must prioritize security compliance, align with established compliance frameworks, and build a strong foundation of policies and controls for future growth and ongoing compliance.
SOC 2 (Service Organization Control 2) has evolved from a differentiator to a requirement. If you want to move upmarket, you need to understand exactly what you are getting into.
Part A: What is SOC 2? (The Deep Dive)
SOC 2 compliance is a voluntary cybersecurity auditing framework developed by the American Institute of CPAs (AICPA) that evaluates how a service organization manages sensitive customer data. Unlike PCI-DSS (for credit cards) or HIPAA (for healthcare), SOC 2 is not a government law. Instead, it is a voluntary reporting framework that demonstrates a startup's commitment to information security by proving that the organization meets recognized standards for protecting data and privacy. While SOC 2 compliance is not legally required, it is increasingly important for startups handling sensitive data due to rising compliance requirements from enterprise clients who expect robust security and regulatory practices.
The Trust Services Criteria (TSC)
The first step to achieving SOC 2 compliance is to understand the SOC 2 Trust Service Criteria.
A SOC 2 audit measures your company against five specific categories, known as the Trust Services Criteria. You do not need to be audited on all five.
- Security (Mandatory): This is the “Common Criteria.” It covers physical and logical access. (e.g., Do you use 2FA? Are your servers behind a firewall? Do you run background checks on employees?). 90% of startups start with Security only.
- Availability: Critical for SaaS companies with strict SLAs. It verifies that your system is available for operation and use as agreed. (e.g., Disaster recovery plans, uptime monitoring).
- Confidentiality: Relevant if you handle sensitive intellectual property. It focuses on data access restrictions and encryption, with a key focus on protecting sensitive information such as proprietary data and trade secrets.
- Processing Integrity: Critical for fintech or data analytics. It ensures system processing is complete, valid, accurate, and timely.
- Privacy: Relevant if you hold PII (Personally Identifiable Information) for consumers. It focuses on how you collect, use, retain, and dispose of personal info.

Only the security criterion is mandatory for SOC 2 compliance, while the other four criteria are optional.
Before your official SOC 2 audit, conducting a readiness assessment is a crucial diagnostic step. A readiness assessment helps identify gaps and vulnerabilities in your controls, ensuring you are fully prepared and reducing the risk of last-minute issues during the audit process.
Type I vs. Type II
Founders often confuse these. You need to know the difference to budget your time.
- Type I (Point-in-Time): The auditor looks at your system on a specific date (e.g., September 1st) and verifies that your security controls are designed correctly. A SOC 2 Type 1 report validates that controls are designed appropriately at a given point in time. SOC 2 Type 1 is considered a cost-effective choice, with costs typically ranging from $5,000 to $20,000.
Tip: Type 1 rapidly unblocking sales. It is faster and cheaper.
- Type II (Period of Time): The auditor observes your system over a period (usually 3 to 12 months). They test that your controls were not only designed correctly but operated effectively continuously. A SOC 2 Type 2 report offers proof of both the design and operational efficiency of your organization's security controls over a specific period of time. SOC 2 Type 2 provides a more comprehensive view of your security posture, with costs typically ranging from $8,000 to $40,000. Subsequent audits are required annually for Type 2 to verify ongoing operational efficiency of controls.
Tip: Organizations often obtain a Type 1 attestation before proceeding to a Type 2 report, but you can skip Type 1 and obtain Type 2 directly if desired. To maintain SOC 2 compliance, startups must provide evidence of continuous monitoring and validation of their security controls.
Part B: How to Obtain "Certification"
First, a correction on terminology: There is no such thing as “SOC 2 Certification.”
You do not “get certified.” You receive an Attestation. A CPA firm performs an examination and issues a report containing their opinion. You cannot pass or fail; you receive either an “Unqualified Opinion” (Clean report) or a “Qualified Opinion” (Exceptions found).
To achieve SOC 2 compliance, a startup must define its audit scope and relevant Trust Services Criteria, conduct a gap analysis, implement necessary security policies and controls, provide evidence to an independent auditor, and undergo their fieldwork to receive the final report.
Only certified public accountants (CPAs) are authorized to perform SOC 2 audits, and the attestation engagement must be conducted by an independent auditor to validate your organization’s security controls. The auditor’s reputation can influence the compliance experience, and choosing the right SOC 2 auditor is crucial for a smooth and effective process.
Who can issue it?
Only a licensed CPA firm (Certified Public Accountant) can perform the audit. You cannot self-assess, and you cannot use a general cybersecurity consultant to sign the final report.

The Cost of Admission
Founders must budget for two distinct costs:
- Preparation Tools: Most modern startups use compliance automation platforms (e.g., Vanta, Drata, Secureframe). These software tools can streamline compliance efforts, reduce manual work, and help make the process smooth and efficient. Managing SOC 2 compliance in-house can lead to an opportunity cost by diverting resources from core business activities, as the SOC 2 audit process typically requires a significant amount of time and resources to prepare for. Startups often face challenges with manual compliance processes, so prioritizing automation solutions can reduce the time and resources needed for SOC 2 compliance.
You can check prices for automation compliance tools here to find the best fit for your startup's SOC 2 compliance journey.
- The Audit Fee: The check you write to the CPA firm.
- Type I: Typically ranges from $5,000 to $20,000.
- Type II: Usually costs between $8,000 and $40,000.
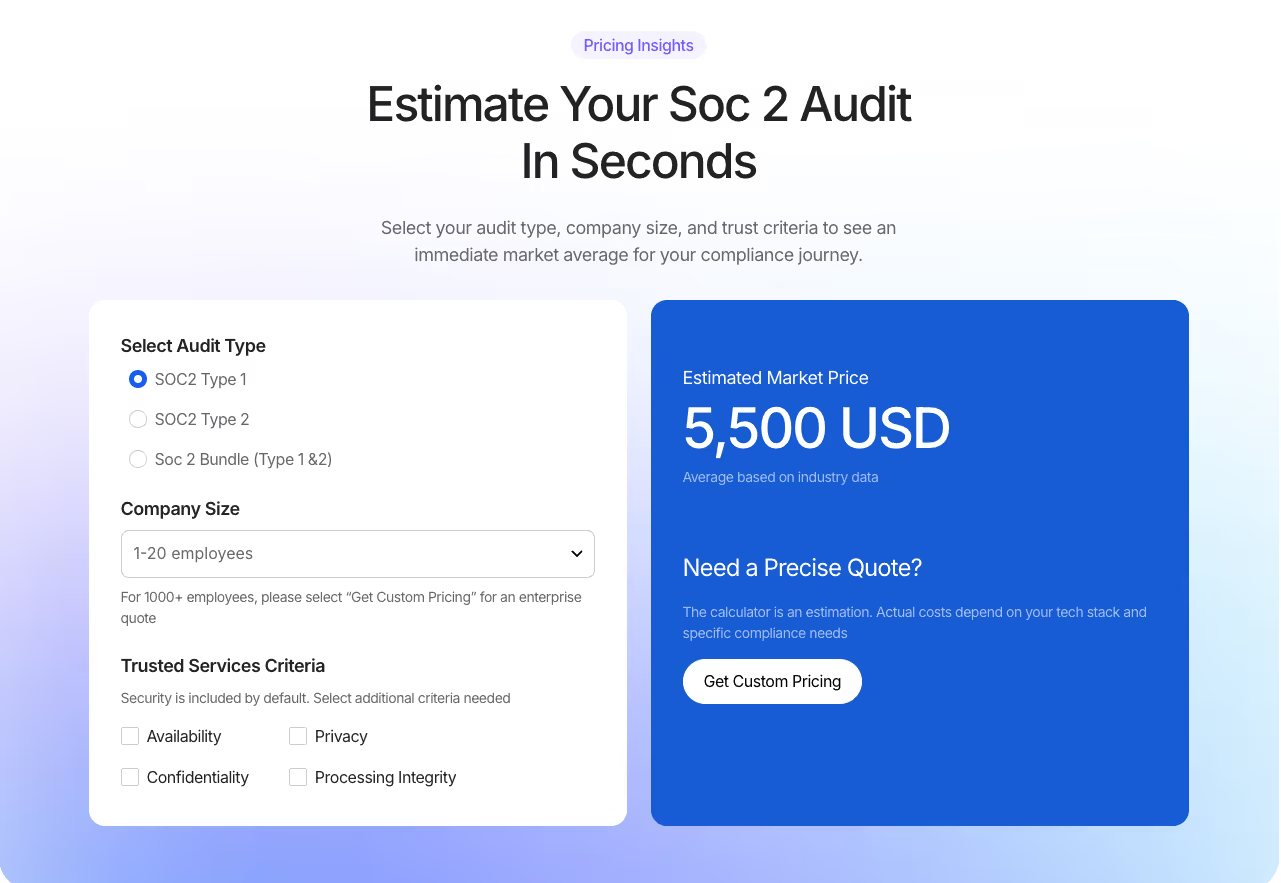
Looking to get a more accurate estimate for your SOC 2 compliance costs tailored to your startup's specific needs? Use our SOC 2 calculator to quickly understand the pricing based on your unique requirements. Check it out and plan your compliance journey with confidence!
Part C: The Typical Process (Step-by-Step)
The timeline from “decision” to “report in hand” is typically 3 to 9 months. Achieving SOC 2 for startups involves building a comprehensive compliance program—a structured framework of policies, controls, and processes designed to meet SOC 2 standards. This compliance program requires a methodical approach, from initial gap assessment to implementation and ongoing monitoring. Importantly, the process of achieving SOC 2 compliance forces startups to implement robust internal controls early, which can significantly reduce the likelihood of costly data breaches.
Phase 1: Scoping and Gap Analysis (Weeks 1–3)
You must define the scope. Does the audit cover the whole company or just the production environment? Which Trust Criteria will you include?
Once scoped, you perform a “Gap Analysis.” You will compare your current state to SOC 2 standards to identify compliance gaps—areas where your security controls or processes do not meet SOC 2 requirements. Conducting a gap analysis helps identify vulnerabilities early in the SOC 2 implementation process.
- Typical Gaps: Lack of formal offboarding processes for terminated employees, no annual penetration test, developers having direct write-access to production databases without approval.
Risk assessment and risk management are critical at this stage to proactively identify, document, and mitigate risks that could lead to compliance gaps. Once compliance gaps are identified, you should develop a gap remediation plan, prioritizing gaps under the security criterion first to address the most critical vulnerabilities.
Phase 2: Remediation (Weeks 4–8)
This is the heavy lifting. You must implement controls to close the gaps.
- Technical Controls: Establish and enforce security policies and technical controls such as multi-factor authentication, encryption (AES-256 for data at rest, TLS 1.2+ for data in transit), and centralized logging, in addition to turning on AWS GuardDuty, enforcing disk encryption on all fleet laptops, and setting up vulnerability scanning.
- HR/Legal Controls: Creating an org chart, writing a Code of Conduct, ensuring every employee (contractors included) signs confidentiality agreements, and implementing background checks for all new hires.
- Process Controls: You must institute a Change Management process. You can no longer push code to production directly; every pull request needs a reviewer and approval evidence.
Effective risk mitigation through these controls is essential for reducing security risks and demonstrating trustworthiness to customers and partners. Expert support can guide startups through the remediation process, providing tailored strategies and industry insights. Startups should also document SOC 2 control implementation to expedite the audit process.
Phase 3: The Observation Window (The "Audit" Period)
- For Type I: You select a date. On that date, the auditor requests evidence (screenshots, configuration exports) to prove the controls exist.
- For Type II: You enter a 3 to 6-month observation window. You must not slip up. If you turn off MFA for a week, or hire someone without a background check, the auditor will find it, and it will appear as an “exception” in your final report. After the initial audit, continuous monitoring and regular assessments and validations of your security controls are necessary to maintain SOC 2 compliance.

Phase 4: The Fieldwork and Report (2–4 Weeks)
The auditor reviews the evidence. Collecting evidence is a crucial step in the audit process, as it ensures that all necessary documentation and records are available for review. Auditors in 2026 prioritize consistent control operation over just having documentation, so demonstrating that your controls are operating effectively over time is essential. They will likely ask “Clarifying Questions” or request more samples (e.g., “Show me the onboarding tickets for these 3 employees hired in May”).
Once satisfied, they draft the report.
- Management Assertion: You sign a letter stating you believe your system is secure.
- Auditor’s Opinion: The CPA signs off that they agree with you.
- System Description: A long narrative explaining your software architecture and processes. This section provides a comprehensive view of the organization's security posture, detailing how your controls align with SOC 2 trust service criteria.
Phase 5: Maintenance
SOC 2 is an annual recurring requirement. A Type I report expires quickly. Once you have it, you immediately begin your observation period for your Type II, which must be renewed every 12 months.
Maintaining SOC 2 compliance is an ongoing compliance journey that requires a dedicated compliance team and a security-first culture across your organization. Strong, formalized leadership and the involvement of senior leadership are critical for effective SOC 2 implementation and clear communication between teams. Regular assessments and validations of your security controls are necessary to maintain compliance and prepare for subsequent audits.
Prioritizing SOC 2 compliance early helps startups avoid higher costs and complications as they grow. Ongoing compliance not only reassures and retains existing customers but also establishes a solid foundation to attract and serve bigger customers as your business matures.
FAQ for SOC 2 for Startups
What is SOC 2 compliance for startups?
SOC 2 is a voluntary cybersecurity framework by the AICPA that evaluates how an organization manages sensitive customer data. It helps startups prove their security maturity to enterprise clients and serves as a vital asset for closing B2B deals.
What is the difference between SOC 2 Type 1 and Type 2?
Type 1 validates that security controls are designed correctly at a specific point in time, making it faster and cheaper. Type 2 verifies that controls operated effectively over a period of 3 to 12 months and is often required by large enterprises.
How much does a SOC 2 audit cost?
A Type 1 audit typically ranges from $5,000 to $20,000, while a Type 2 audit usually costs between $8,000 to $40,000. Startups must also budget for preparation time and compliance automation tools.
What are the SOC 2 Trust Services Criteria?
The five criteria are Security, Availability, Confidentiality, Processing Integrity, and Privacy. Only the Security criterion is mandatory for compliance, while the others are optional based on business needs.
Who is authorized to issue a SOC 2 report?
Only a licensed CPA firm can perform the audit and issue the final attestation report. You cannot self-assess or utilize a general cybersecurity consultant to sign the final documents.
How long does the SOC 2 process take?
The timeline typically ranges from 3 to 9 months from the initial decision to having the report in hand. This duration includes scoping, gap analysis, remediation, and the observation window.
Final Take: Get SOC 2 Certification Fast and Affordable with Secureleap
Achieving SOC 2 certification is a critical step in demonstrating your commitment to data security and winning the trust of enterprise customers. While the process can seem complex and costly, partnering with the right experts can make all the difference.
Secureleap specializes in helping organizations obtain SOC 2 certification quickly and at a very competitive price. With tailored services designed to streamline your audit process, reduce preparation time, and manage costs effectively, Secureleap ensures you get a credible, customer-trusted SOC 2 report without unnecessary delays or expenses.
Whether you're a startup or a growing mid-market company, Secureleap’s expertise and efficient approach can help you navigate the compliance journey smoothly, so you can focus on what matters most—growing your business with confidence.
Contact Secureleap today to learn how we can support your SOC 2 compliance needs and accelerate your path to certification.






