What is SOC 2 Type 1?
SOC 2 Type 1 is an attestation report issued by an independent Certified Public Accountant (CPA) firm that evaluates whether a service organization’s internal controls are suitably designed and implemented to meet the AICPA’s Trust Services Criteria at a specific point in time. Unlike SOC 2 Type 2, which assesses the operational effectiveness of controls over a period, SOC 2 Type 1 provides a snapshot of the design and implementation of controls as of a single date. This report demonstrates that the organization has established security processes and controls intended to protect sensitive customer data, providing assurance to clients and stakeholders about the organization's commitment to data security and compliance.
Need a SOC 2 Type 1 audit? Try our free calculator to estimate your audit costs.
The “Type 1” designation refers to the temporal nature of the assessment. Unlike SOC 2 Type 2, which evaluates control effectiveness over an extended period (typically 6-12 months), Type 1 is a snapshot. The auditor examines your control environment on a single date and determines whether those controls are properly designed and implemented as of that moment.
SOC 2 itself is built around five trust service principles: security, availability, processing integrity, confidentiality, and privacy. Security is mandatory for every SOC 2 examination, while the others are optional depending on your business model and what your customers require. The framework was developed by the AICPA specifically for service organizations that store, process, or transmit data on behalf of their clients.
A few important clarifications often get overlooked:
- SOC 2 Type 1 is not a certification. There’s no pass or fail. Instead, it’s an auditor’s opinion issued under professional attestation standards (SSAE 18 / AT-C 105 and AT-C 205).
- The report is typically restricted-use, meaning it’s shared under NDA with potential customers, partners, and regulators rather than posted publicly.
- It’s issued only by licensed CPA firms with expertise in attestation engagements, not by consultants or software vendors.
For SaaS companies, cloud computing organizations, and IT managed service providers, SOC 2 Type 1 often serves as the entry point to demonstrating security maturity. It signals to enterprise clients and financial institutions that you take data protection seriously enough to submit your organization’s controls to independent examination.

If you’re building a SaaS product, running a cloud infrastructure company, or offering managed IT services, you’ve probably encountered the same question from enterprise prospects: “Do you have a SOC 2 report?”
For many growing companies, SOC 2 Type 1 is the fastest path to answering that question with confidence. It demonstrates that your organization has built security controls designed to protect sensitive customer data, even if you haven’t yet accumulated months of operational evidence.
This guide breaks down everything you need to know about SOC 2 Type 1, from the fundamentals of the Trust Services Criteria to the practical steps of preparing for and completing your first audit. Whether you’re a founder trying to close enterprise deals or a compliance lead building out your security program, you’ll find actionable guidance to move forward.

How SOC 2 Fits Into the SOC Framework (SOC 1, SOC 2, SOC 3, and Types)
Before diving deeper into SOC 2 Type 1, it helps to understand where it sits within the broader SOC reporting landscape. The AICPA developed multiple SOC report types to address different use cases and audiences.
SOC 1 focuses on internal controls over financial reporting. If your service affects your clients’ financial statements, like payroll processing, payment handling, or fund administration, SOC 1 is typically the relevant report. It’s governed by SSAE 18 AT-C 320 and is primarily used by user entities and their auditors to assess how your controls impact their financial transactions.
SOC 2 focuses on controls related to the relevant Trust Services Criteria, making it the standard choice for technology and cloud service organizations. If you’re handling customer data but not directly impacting financial reporting, SOC 2 is almost certainly what your prospects are asking for.
SOC 3 is essentially a condensed, general-use version of SOC 2. It contains the same auditor’s opinion but omits the detailed control descriptions and test results. Organizations sometimes use SOC 3 reports for public marketing because they can be shared without NDA restrictions.
Both SOC 2 Type 1 and SOC 2 Type 2 follow the same five Trust Services Criteria. The “Type” designation only indicates the audit period and testing depth:
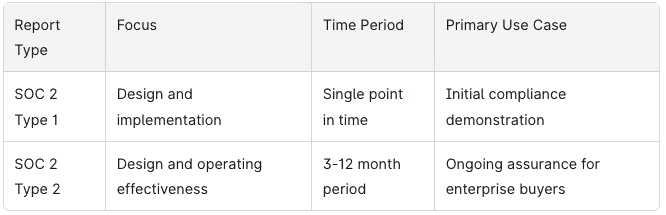
Understanding these distinctions helps you communicate clearly with auditors, customers, and internal stakeholders about exactly what you’re pursuing and why.
The Trust Services Criteria Behind SOC 2 Type 1
Every SOC 2 Type 1 report is scoped against one or more of the five Trust Services Criteria (TSC). Security is always required, but you choose which additional criteria to include based on your service organization’s system and customer expectations.
Security addresses protection against unauthorized access, unauthorized disclosure, and damage to systems. This includes access controls, network security, incident response, and vulnerability management. If you only include one criterion in your SOC 2, this is it.
Availability ensures that systems are accessible for operation and use as committed. For SaaS companies with uptime SLAs, this criterion validates that you have incident response planning, DDoS protection, disaster recovery, and capacity management controls in place.
Processing Integrity ensures that data processing is complete, valid, accurate, timely, and authorized. This matters for organizations handling financial transactions, automated workflows, or any service where data accuracy is critical to client operations.
Confidentiality protects sensitive information from unauthorized disclosure. This includes data encryption, access restrictions, and controls around how confidential data is stored, transmitted, and disposed of.
Privacy governs the collection, use, retention, disclosure, and disposal of personally identifiable information. Organizations subject to privacy regulations like GDPR often include this criterion.
Most early-stage companies pursuing SOC 2 Type 1 include security plus one or two additional criteria. For example, a SaaS platform with uptime commitments might scope security and availability. A company handling sensitive customer information for financial institutions might add confidentiality.
The TSC are aligned with the COSO 2013 framework’s 17 principles, which means your control environment naturally maps to recognized risk assessment and governance standards. The 2022 updated TSC refined certain points of focus but maintained the same underlying structure.
Here’s how specific controls map to criteria:
- Access control policies requiring unique user IDs and role-based permissions → Security
- Data retention schedules and secure deletion procedures → Confidentiality
- Uptime monitoring and automated failover systems → Availability
Choosing which criteria to include impacts your audit scope, timeline, and cost. Align your selections with actual customer requirements and regulatory expectations rather than checking every box for its own sake.
Deep Dive: What SOC 2 Type 1 Really Covers
SOC 2 Type 1 is fundamentally a snapshot report. It evaluates your service organization’s controls as of a specified date, not whether those same controls functioned properly over weeks or months. This makes it faster to complete than Type 2 but also less comprehensive in scope.
A SOC 2 Type 1 report contains several key components:
- Management’s Description of the System: A narrative describing the services you provide, the systems in scope, the relevant trust services criteria you’re addressing, and the controls you’ve implemented.
- Management’s Assertion: A formal statement from your leadership claiming responsibility for the control environment and asserting that controls are suitably designed and implemented.
- Independent Auditor’s Opinion: The CPA firm’s professional judgment on whether your controls meet the required trust services criteria as of the audit date.
- Detailed Controls Listing: A description of individual controls mapped to specific control objectives within the TSC.

During the audit, the auditor performs walkthroughs, reviews documentation, and conducts limited tests to confirm controls are implemented as designed. For example:
- Verifying that multi-factor authentication is configured and enforced across production systems as of the audit date
- Confirming that an incident response plan exists, has been formally approved by leadership, and is accessible to relevant personnel
- Reviewing access control lists to ensure that onboarding and offboarding procedures result in appropriate permission assignments
The auditor’s opinion typically states something like: “In our opinion, the description fairly presents the system, and the controls were suitably designed and implemented as of [date] to meet the applicable trust services criteria.” If design gaps exist, the report will note exceptions.
SOC 2 Type 1 reports are restricted-use documents. You’ll share them under NDA with customers, prospects, partners, and sometimes regulators. They’re not intended for public distribution.
The snapshot nature means Type 1 doesn’t prove that your controls operated effectively over time. It proves they exist and are properly designed at a single point. That distinction matters when enterprise clients evaluate your security posture for longer-term relationships.
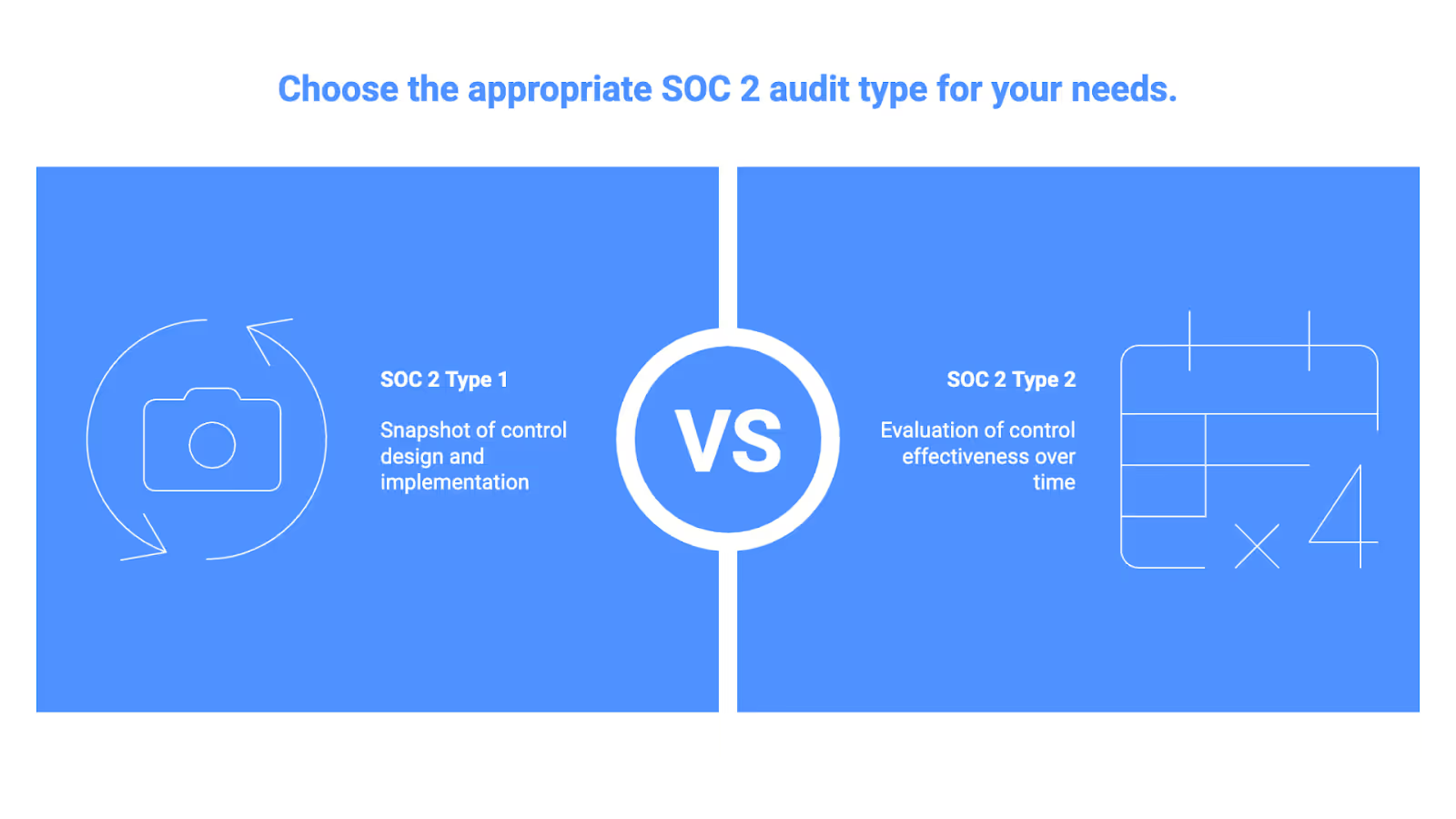
SOC 2 Type 1 vs. SOC 2 Type 2: Key Differences and When to Use Each
The most common question organizations ask is whether to pursue Type 1 or Type 2. The answer depends on your timeline, customer expectations, and current security maturity.
Both report types use identical Trust Services Criteria and require independent CPA firms. The difference lies entirely in what gets tested and over what period.
SOC 2 Type 1 evaluates only the design and implementation of controls as of a specific date. The auditor confirms that controls exist and are appropriately designed but doesn’t test whether they actually functioned correctly over time. No audit period is required beyond the single assessment date.
SOC 2 Type 2 evaluates both design and operating effectiveness over a defined monitoring period, typically 3-12 months. The auditor samples evidence from throughout that period to determine if controls consistently operated as intended. This requires ongoing logging, evidence collection, and documentation throughout the audit period.
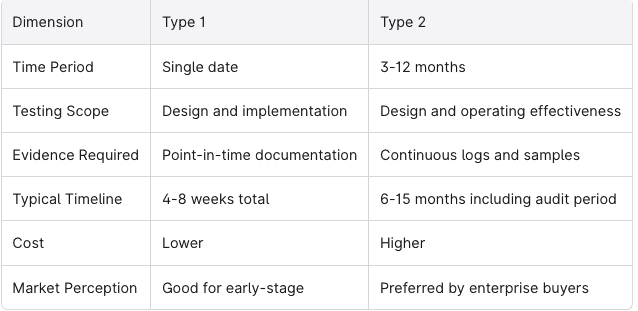
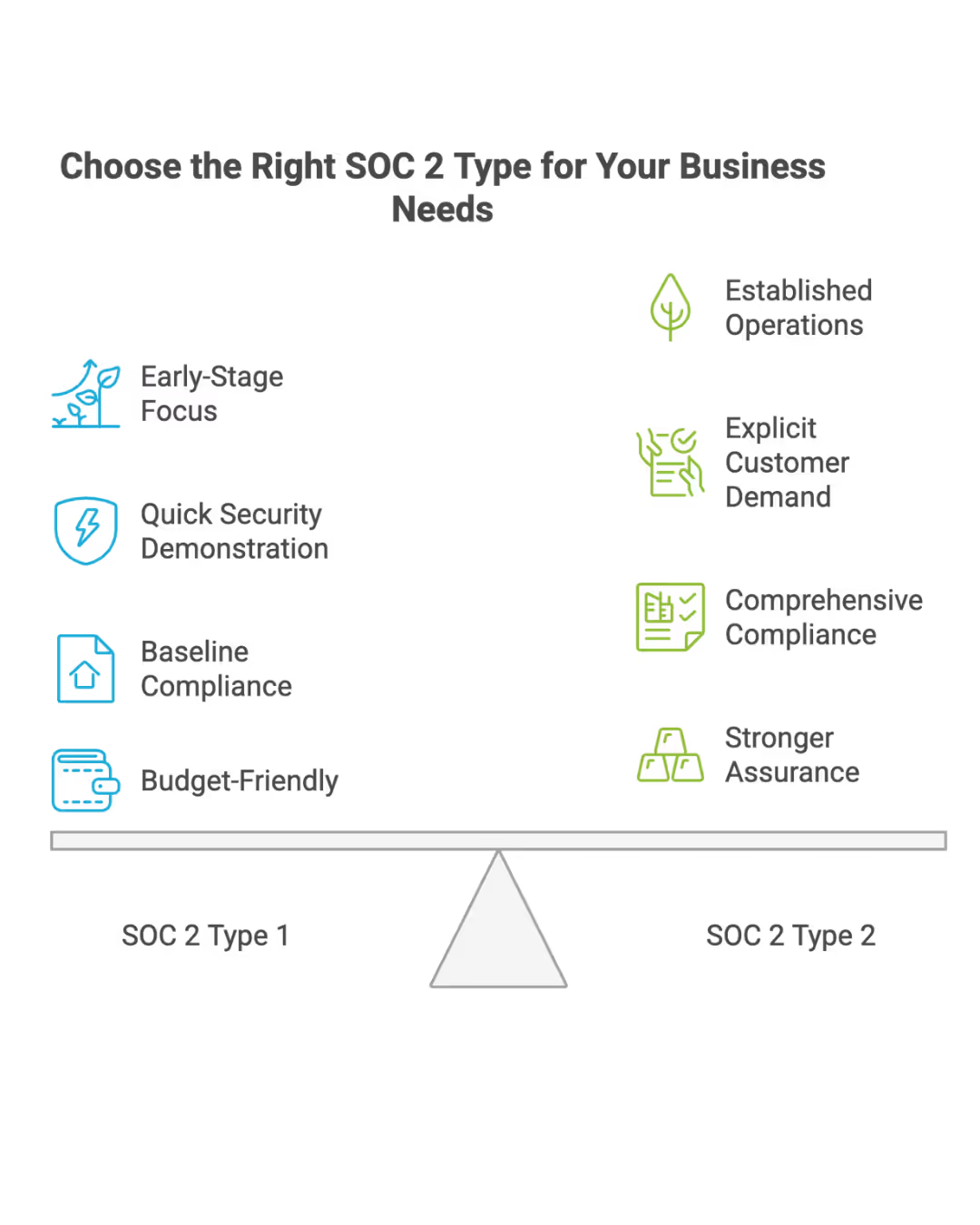
When to choose Type 1:
- You’re an early-stage company that hasn’t yet operated controls for several months
- You need to demonstrate security commitment quickly for a pending deal
- You’re building your compliance infrastructure and want a baseline before committing to Type 2
- Budget constraints make the fuller Type 2 engagement impractical right now
When to choose Type 2 (or skip directly to it):
- Your target customers explicitly require Type 2 reports
- You’re selling into highly regulated industries like healthcare or financial services
- You’ve already been operating controls for 6+ months and have the evidence to support it
- You want the strongest possible assurance for enterprise clients
Most organizations follow a staged approach: complete Type 1 first to validate control design, then pursue Type 2 within the following year. This lets you move business relationships forward while building the operational foundation for comprehensive compliance.
Benefits of Achieving SOC 2 Type 1 for Growing Companies
Beyond checking a compliance box, SOC 2 Type 1 delivers tangible business outcomes that directly impact revenue and operations.
Shortened sales cycles. Enterprise procurement teams often require evidence of third-party security validation before approving vendors. A SOC 2 Type 1 report reduces the volume of security questionnaires you need to complete and accelerates due diligence. Instead of answering 300 questions manually, you can point to an independent auditor’s opinion.
Demonstrated intent for early-stage companies. If you’re a Series A or early growth-stage company, you may not have 12 months of operational history to support a Type 2 report. Type 1 shows potential customers and investors that you’ve made the investment in security infrastructure, even if you’re still building your track record.
Internal gap discovery. The readiness assessment and audit preparation process forces you to systematically evaluate your cybersecurity controls. Many organizations discover existing gaps they didn’t know about, such as inconsistent access reviews, missing policies, or inadequate logging. Fixing these issues strengthens your overall security posture, not just your compliance status.
Competitive differentiation. In crowded markets, SOC 2 Type 1 compliance separates you from competitors who haven’t made the investment. This matters especially when selling to financial institutions, healthcare organizations, or any enterprise client with formal vendor risk management programs.
Board and investor confidence. Security incidents make headlines, and sophisticated investors increasingly scrutinize security practices during due diligence. A SOC 2 Type 1 report provides third-party validation that’s more credible than internal claims.
From a cost and timing perspective, Type 1 engagements typically run 4-8 weeks from readiness to final report for small to mid-size organizations. Costs vary based on scope, TSC coverage, and auditor selection, but they’re meaningfully lower than Type 2 because less evidence needs to be collected and reviewed.
Preparing for a SOC 2 Type 1 Audit: Step-by-Step
Preparation is often the longest and most important phase of a Type 1 engagement. The work you do before the auditor arrives determines how smoothly the audit process runs.

Step 1: Define Your Scope
Start by determining exactly what’s included in your SOC 2 report:
- Which systems and environments are in scope? Most organizations include production systems but exclude development or staging environments.
- Which Trust Services Criteria will you address? Security is required; select additional criteria based on customer expectations and your service commitments.
- What service commitments and system requirements apply? These are the promises you make to customers that your controls support.
Scoping decisions directly impact effort, cost, and timeline. Keep scope focused on what matters to your customers and business processes.
Step 2: Document Policies and Procedures
SOC 2 requires formal documentation of your control environment. At minimum, you’ll need:
- Information security policy
- Access control procedures
- Change management process
- Incident response plan
- Vendor management policy
- Human resources security procedures (onboarding, offboarding, background checks)
- Business continuity and disaster recovery plans
If you don’t have these documented, create them. Auditors need written evidence that controls exist and are communicated to relevant personnel.
Step 3: Conduct a Readiness Assessment
Before engaging an auditor, perform a gap assessment comparing your current practices against SOC 2 control requirements. This identifies remediation tasks you need to complete before the formal audit.
A readiness assessment typically reveals issues like:
- Missing or incomplete policies
- Access reviews not being conducted regularly
- Insufficient logging or monitoring
- Lack of formal risk assessment documentation
- Incomplete vendor security reviews
Step 4: Remediate Gaps
Based on your assessment, tackle remediation work:
- Enable centralized logging and alerting for security events
- Enforce multi-factor authentication across production systems
- Implement vulnerability scanning and patch management
- Define formal onboarding and offboarding procedures
- Set up backup and recovery testing
- Document your risk assessment process
Step 5: Collect Evidence
Gather documentation proving that controls are in place:
- Screenshots of system configurations
- Policy documents with approval signatures
- Access control lists
- Training completion records
- Vendor security assessment results
Many organizations use a compliance automation platform to streamline evidence collection and maintain ongoing alignment with auditor expectations. These tools can automatically pull configurations from cloud providers, track policy acknowledgments, and organize documentation for audit review.
The SOC 2 Type 1 Audit Process With a CPA Firm
The formal SOC audit begins only after you’ve defined scope, implemented controls, and gathered supporting evidence. Choosing the right auditor matters significantly.
Selecting Your Auditor
Look for a licensed CPA firm with specific experience in SOC 2 engagements and familiarity with organizations of your size and industry. Ask about:
- Number of SOC 2 reports issued annually
- Experience with your technology stack (AWS, Azure, GCP, etc.)
- Typical engagement timelines
- Communication style and availability
Certified public accountants must maintain independence, so select a firm that hasn’t provided consulting services that could create conflicts.
Audit Fieldwork
Typical audit activities include:
- Kickoff meeting: Align on scope, timeline, key contacts, and documentation requirements
- Request list: The auditor provides a detailed list of evidence needed, typically organized by control area
- Walkthroughs: Remote or onsite sessions where auditors review how controls function in practice
- Documentation review: Examination of policies, procedures, configurations, and logs
- Implementation testing: Limited tests confirming that key controls are in place as of the audit date
For a Type 1 engagement, auditors aren’t sampling evidence over months. They’re verifying that controls exist and are designed appropriately at the point of assessment.
Report Issuance
After fieldwork, the auditor drafts the SOC 2 Type 1 report. You’ll have an opportunity to review for factual accuracy, though you cannot negotiate the auditor’s opinion. Once finalized, you receive the official SOC report that can be distributed under NDA.
Expect 2-4 weeks of active fieldwork depending on organization size and readiness. The final report becomes your evidence of compliance for customer due diligence packages.

Cost, Timing, and Resource Expectations for SOC 2 Type 1
SOC 2 Type 1 is generally the faster and less expensive path compared to Type 2, but it still requires meaningful investment of time and resources.
Realistic Cost Ranges
Costs vary significantly based on scope, number of trust services criteria included, organization complexity, and auditor selection. General ranges:
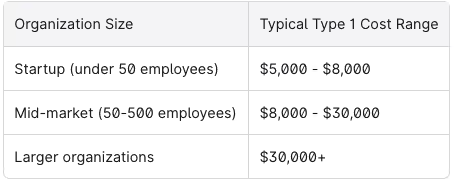
These estimates include auditor fees. If you need significant remediation work or external consulting support, add those costs separately. These pricing ranges are also aligned with information provided by Sprinto.
Timeline Expectations
A typical SOC 2 Type 1 project breaks down as:
- Readiness and remediation: 2-6 weeks depending on current maturity
- Audit fieldwork: 1-4 weeks depending on scope and organization size
- Report issuance: 1-3 weeks after fieldwork completion
Total time from decision to final report: approximately 4-12 weeks for most organizations.
Internal Resource Requirements
You’ll need dedicated involvement from:
- Executive sponsor (CISO, CTO, or COO): Strategic oversight, management assertion signing
- Technical leads (DevOps, security, IT): Control implementation, evidence gathering, auditor walkthroughs
- Operations/HR: Policy documentation, HR-related controls like background checks and offboarding
Using compliance tools, templates for policies and risk registers, and structured evidence collection can substantially reduce both time and cost compared to purely manual approaches.
Plan your SOC 2 work around business cycles. Avoid starting during major product launches, fundraising rounds, or peak sales periods when your team is already stretched thin.
Using SOC 2 Type 1 Strategically: From First Report to Ongoing Compliance
SOC 2 Type 1 is the beginning of your SOC compliance journey, not a one-time project. The organizations that extract the most value treat it as a foundation for ongoing security investment.
Building Toward Type 2
Most companies use their first Type 1 report to establish a baseline, then target SOC 2 Type 2 in the following fiscal year. This approach allows you to:
- Satisfy immediate client demands with Type 1
- Operate controls for 6-12 months while collecting evidence
- Demonstrate operational effectiveness in your Type 2 report
Establishing Continuous Monitoring
Immediately after Type 1, implement practices that will support your future Type 2:
- Regular log reviews and security monitoring
- Quarterly access reviews
- Periodic risk assessments
- Ongoing evidence collection through automation
These practices ensure you’re not scrambling to generate evidence when your Type 2 audit period begins. Tools Like Vanta and Drata helps this task.
Integrating With Other Frameworks
SOC 2 shares significant overlap with other compliance frameworks. Leverage shared controls across:
- ISO 27001: Common focus on access management, risk assessment, and incident response
- HIPAA: Overlapping security and privacy controls for healthcare data
- PCI DSS: Shared access control, encryption, and monitoring requirements
- GDPR: Aligned privacy and data protection expectations
Organizations pursuing multiple frameworks can often use the same controls and documentation for each, reducing duplicate compliance efforts.
Using Your Report in Sales
Your SOC 2 Type 1 report becomes a sales enablement asset:
- Host it on a secure trust center or customer portal
- Share under NDA during procurement due diligence
- Prepare executive summaries for non-technical stakeholders highlighting key aspects like audit scope and auditor’s opinion
- Reference it proactively in security questionnaire responses
Long-Term Value
Ongoing investment in security and compliance delivers compounding returns: reduced breach risk, smoother future audits, stronger customer trust, and differentiated market positioning. The companies that treat SOC 2 as continuous improvement rather than periodic checkbox exercises build durable competitive advantages.
Frequently Asked Questions About SOC 2 Type 1
What is SOC 2 Type 1?
SOC 2 Type 1 is an attestation report issued by a CPA firm that evaluates the design and implementation of internal controls at a specific point in time. It provides a snapshot demonstrating that a service organization has established security processes to protect customer data.
What is the difference between SOC 2 Type 1 and Type 2?
Type 1 evaluates control design at a single date while Type 2 tests operating effectiveness over a period of 3 to 12 months. Type 1 is faster to obtain but Type 2 provides greater assurance to enterprise buyers regarding long-term security performance.
How much does a SOC 2 Type 1 audit cost?
Audit fees typically range from $5,000 to $8,000 for startups and $8,000 to $30,000 for mid-market organizations. These costs cover the CPA firm fees but exclude expenses for remediation tools or external consulting.
How long does the SOC 2 Type 1 process take?
The entire timeline usually spans 4 to 12 weeks from readiness preparation to the final report issuance. The active audit fieldwork portion typically lasts between 1 to 4 weeks depending on the scope and organization size.
Is SOC 2 Type 1 mandatory?
No. SOC 2 is a voluntary attestation, not a legal requirement in most jurisdictions. However, it has become an industry standard for technology service providers, particularly those serving enterprise clients or handling sensitive data. Many procurement teams treat it as a practical requirement for vendor approval.
Can we skip Type 1 and go straight to Type 2?
Yes, if you’ve already been operating controls effectively for several months and have the evidence to support it. Organizations with mature security programs sometimes skip directly to Type 2. However, most early-stage companies find Type 1 valuable for validating control design before committing to the longer Type 2 audit period.
Final Take: Get SOC 2 Certification Fast and Affordable with Secureleap
Achieving SOC 2 certification is a critical step in demonstrating your commitment to data security and winning the trust of enterprise customers. While the process can seem complex and costly, partnering with the right experts can make all the difference.
Secureleap specializes in helping organizations obtain SOC 2 certification quickly and at a very competitive price. With tailored services designed to streamline your audit process, reduce preparation time, and manage costs effectively, Secureleap ensures you get a credible, customer-trusted SOC 2 report without unnecessary delays or expenses.
Whether you're a startup or a growing mid-market company, Secureleap’s expertise and efficient approach can help you navigate the compliance journey smoothly, so you can focus on what matters most—growing your business with confidence.
Contact Secureleap today to learn how we can support your SOC 2 compliance needs and accelerate your path to certification.






