Author: Marçal Santos, vCISO | +20 Years Cybersecurity Experience
Key Takeaways
- SOC 2 Type 2 is an independent CPA attestation that tests both the design and operating effectiveness of your security and privacy controls over a specified period, typically 6–12 months.
- Modern SaaS companies, cloud services providers, and managed service providers are routinely asked for a current SOC 2 Type 2 report to close enterprise deals and satisfy vendor due diligence requirements.
- The framework is built on the AICPA Trust Services Criteria covering Security, Availability, Processing Integrity, Confidentiality, and Privacy—with Security always in scope and others optional based on your business needs.
- This is not a one-time certificate but an annual cycle of audits, continuous monitoring, and remediation that becomes an integral part of your organization’s security posture.
- First-time SOC 2 Type 2 journeys typically take 6–18 months from project kickoff to final report, with external audit costs ranging from approximately USD 15,000–60,000+ depending on complexity.
Need a clear cost breakdown? Check our SOC 2 audit calculator to see exactly what your audit will cost.
What Is SOC 2 and Where Does Type 2 Fit?
If you’ve ever been asked to provide security documentation during a sales cycle with an enterprise client, you’ve probably encountered the term “SOC 2.” But what exactly is it, and why does the “Type 2” distinction matter?
System and Organization Controls (SOC) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to evaluate how service organizations manage data and protect customer interests. Think of it as a standardized way for third parties to assess whether your company has its security house in order.
The SOC family includes three main report types. SOC 1 focuses on controls relevant to financial reporting—it’s what your customers’ auditors care about when your services could impact their financial statements. SOC 2, on the other hand, addresses security, availability, processing integrity, confidentiality, and privacy of customer data—making it the go-to for technology companies handling sensitive information. SOC 3 is essentially a public-friendly summary of SOC 2, useful for marketing but lacking the detailed control testing that enterprise clients demand.
Within SOC 2, there are two examination types. Type 1 provides a point-in-time snapshot, testing only whether controls are suitably designed as of a specific date. Type 2 goes further by examining both design and operating effectiveness over an extended audit period, typically spanning 3 to 12 months.
To make this concrete, consider these typical SOC 2 use cases:
- A SaaS CRM platform storing client data for sales teams across multiple organizations
- A payment gateway processing credit card transactions alongside PCI DSS compliance
- A data analytics platform ingesting and processing business intelligence from enterprise customers
- A managed security service provider monitoring and responding to threats on behalf of clients
For any of these service providers, enterprise clients want evidence that security controls aren’t just documented—they’re actually working day after day.

What Is a SOC 2 Type 2 Report?
A SOC 2 Type 2 report is an attestation by a licensed CPA firm confirming that your controls were suitably designed and operated effectively during a stated audit period. For example, a report might cover the period from 1 July 2024 through 30 June 2025, demonstrating that throughout those 12 months, your organization consistently maintained the security controls it claimed to have.
Unlike SOC 2 Type 1, which only verifies that controls exist at a single point in time, Type 2 requires auditors to test real evidence: access logs, change management tickets, incident response records, backup verification, and more. This makes soc 2 type ii significantly more rigorous and, consequently, more valuable to prospective customers.

The report itself is private and typically shared under NDA. You’ll encounter requests for it during vendor security reviews, RFPs, and enterprise procurement processes. When a prospective customer asks “Can you share your SOC 2?”, they almost always mean the Type 2 report.
Standard audit period lengths range from 6 to 12 months, with 12 months being the gold standard for comprehensive coverage. First-time organizations sometimes start with a shorter 3-month period to get a report in hand faster, then extend to a full 12-month cycle in subsequent years.
The fundamental difference is evidence. Type 1 asks “Do you have policies?” Type 2 asks “Can you prove those policies worked consistently over the past year?”
At minimum, every SOC 2 Type 2 report must include the Security criterion (also called the Common Criteria). Organizations then optionally add availability processing integrity confidentiality or Privacy based on their service offerings and customer requirements.
Trust Services Criteria Covered in SOC 2 Type 2
The Trust Services Criteria (TSC) form the backbone of every SOC 2 report. Your scope determines which criteria appear in your report, and this decision should align with both your service offerings and what your customers actually need to see.
Security (Common Criteria)
Security is mandatory for all SOC 2 reports. It covers how your organization protects system resources against unauthorized access through logical and physical access controls, system operations, change management, and risk mitigation. Practical controls include:
- Multi-factor authentication for all production systems
- Role-based access provisioning and timely de-provisioning
- Centralized logging and security monitoring
- Vulnerability management and penetration testing
- Physical access controls for data centers and offices
Availability
The Availability criterion addresses whether your systems operate with minimal downtime and meet service level commitments. This matters for any service organization relevant to business-critical customer operations. Controls typically include:
- Defined uptime SLAs with monitoring and alerting
- Capacity planning and baseline performance metrics
- Backup and disaster recovery procedures with regular testing
- Business continuity plans addressing environmental threats
Processing Integrity
Processing Integrity ensures that system processing is complete, accurate, timely, and authorized. Organizations handling transactions, calculations, or data transformations often include this criterion. Key controls involve:
- Input validation and data quality checks
- Change management processes with testing and approval gates
- Audit trails for all data modifications
- Error detection and correction procedures
Confidentiality
Confidentiality focuses on protecting confidential information from unauthorized disclosure. This applies when you handle proprietary business plans, intellectual property, or other sensitive data that isn’t personal information. Controls include:
- Data classification and labeling schemes
- Encryption at rest and in transit
- Secure file transfer mechanisms
- Data retention and destruction policies
Privacy
Privacy addresses how personal information is collected, used, retained, and disposed of. If your service processes consumer data subject to privacy expectations, this criterion demonstrates your commitment to data protection. Controls cover:
- Clear privacy notices using plain language
- Consent mechanisms for data collection
- Data subject access request procedures
- Data minimization and purpose limitation
Smaller SaaS companies often start with Security plus Availability, which covers the most common enterprise requirements. Organizations handling regulated data—such as health information or financial records—frequently add Confidentiality and Privacy to demonstrate comprehensive protection of sensitive data.
SOC 2 Type 2 vs. SOC 2 Type 1
Understanding when to pursue Type 1 versus Type 2 can save you time and money while ensuring you meet customer expectations.
Type 1 provides a snapshot at a single date—for example, “as of 31 March 2025.” The auditor examines whether controls are designed appropriately but doesn’t test whether they’ve been operating effectively over time.
Type 2 covers performance across a period—such as “1 January through 30 June 2025”—and requires evidence that controls actually worked throughout.
Here’s how they differ in practice:
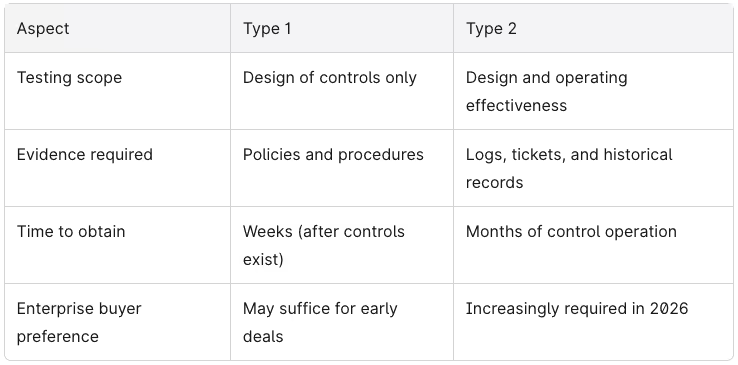
When to start with Type 1: If you’re a startup with early customer requests but haven’t had controls running long enough for a Type 2 examination, a Type 1 report can bridge the gap. It demonstrates you’ve built appropriate controls while you accumulate the operating history needed for Type 2.
When to go straight to Type 2: If your company’s internal controls have been operating for several months and you have enterprise clients in your pipeline who explicitly require Type 2, skip the intermediate step. There’s no regulatory requirement to complete Type 1 first.
The reality in 2026 is that mature buyers—especially in finance, healthcare, and technology—explicitly request “current SOC 2 Type 2” in vendor questionnaires. Type 2 has become the de facto standard for SaaS and cloud computing vendors pursuing enterprise clients.
What Does a SOC 2 Type 2 Report Contain?
A typical SOC 2 Type 2 report runs 80 to 150+ pages for complex environments. While that sounds intimidating, understanding the structure helps you navigate what matters for your stakeholders.
Management’s Assertion
This section contains management’s written confirmation about the system in scope, the relevant trust services criteria included, and the audit period covered. It’s essentially your organization asserting that you’ve designed and maintained controls meeting the applicable trust services principles.
Independent Auditor’s Report
The CPA firm’s opinion appears here. An unqualified (clean) opinion means the auditor found controls suitably designed and operating effectively. A qualified opinion indicates some exceptions or issues were identified. An adverse opinion—rare but possible—means significant control failures exist.

System Description
This narrative describes everything in scope: the services you provide, infrastructure components, operating software, personnel, data flows, and the internal control environment. Enterprise clients and their auditors use this section to understand exactly what the report covers and what falls outside the audit scope.
Tests of Controls and Results
This is the meat of the report. It contains detailed tables showing each control, the testing controls procedures the auditor performed, sample sizes, and any exceptions identified. For example:
Control: Access to production systems requires multi-factor authentication. Test: Selected a sample of 25 user accounts and verified MFA was enabled for each. Result: No exceptions noted.
User entity responsibilities also appear in the report, documenting what your customers must do on their end to maintain security. These complementary controls—like managing their own user access or protecting API keys—are worth reading carefully.
While the full report is lengthy, you’ll typically share relevant excerpts with non-technical stakeholders. Security teams review the detailed test results; executives care most about the auditor’s opinion and any noted exceptions.
Who Needs a SOC 2 Type 2 Report?
SOC 2 Type 2 has become a practical necessity for B2B service providers handling customer data or operating in regulated industries. If you’ve lost deals or faced lengthy security reviews in the past year, chances are a Type 2 report would help.
Organizations that most commonly need SOC 2 Type 2 include:
- SaaS platforms storing customer or end-user data (HR systems, CRM tools, marketing automation)
- Cloud and infrastructure providers offering managed hosting, IaaS, or PaaS
- Managed security service providers and IT outsourcers monitoring client environments
- Payment processors and fintech platforms already complying with PCI DSS but needing broader assurance
- Healthcare and health-tech vendors handling PHI/PII alongside Health Insurance Portability and Accountability Act obligations
Enterprise procurement teams—especially in technology, finance, and healthcare—commonly insist on a current SOC 2 Type 2 report as part of vendor onboarding. This applies whether you’re a 20-person startup or a 500-person scale-up.
Even companies based outside the U.S. find that selling into North American or global enterprises triggers SOC 2 Type 2 expectations. The framework has become a de facto international standard for demonstrating that organization complies with expected security practices.
If you’ve experienced missed or delayed deals in the last 6–12 months due to lack of SOC 2 evidence, that’s a strong signal you need a Type 2 report.

Benefits of SOC 2 Type 2 Compliance
With data breaches costing enterprises an average of $4.45 million globally per incident, demonstrating sustained security practices isn’t just about checking boxes—it’s about protecting your business and your customers.
Sales Enablement
A current SOC 2 Type 2 report can dramatically shorten sales cycles. Instead of answering hundreds of security questionnaire questions from scratch, you can point to your report as evidence. One SaaS vendor reported passing a bank’s 200-question security review with minimal follow-ups simply by providing their Type 2 report upfront.
Competitive Advantage
When prospects compare you against competitors who lack independent attestation, your SOC 2 Type 2 signals maturity and trustworthiness. For enterprise clients evaluating risk, this differentiation often tips the scales in your favor.
Operational Discipline
The audit process forces better documentation, incident response procedures, and change management practices. These improvements benefit your organization beyond just passing an audit—they reduce the likelihood of actual security incidents.
Third-Party Assurance
SOC reports simplify security discussions with business partners, regulators, and investors. Rather than explaining your entire security program from scratch, you can provide a standardized, independently verified assessment.
Reduced Risk Exposure
Implementing and maintaining controls that satisfy certified public accountants doesn’t just produce a report—it actually strengthens your defenses. Organizations that take SOC 2 seriously often identify and remediate vulnerabilities they didn’t know existed.
The key insight is that Type 2’s value stems from its evidence-based nature. You’re not just claiming to have controls; you’re proving they operated effectively over months of real-world use.
SOC 2 Type 2 Audit Process and Timeline
Understanding the audit process helps you plan realistically and avoid surprises that delay your report.
Phase-by-Phase Timeline
Scoping and Gap Analysis (2–4 weeks): Define which products, systems, and trust services principles are in scope. Conduct a readiness assessment comparing your current controls against SOC 2 requirements.
Remediation and Control Implementation (1–6 months): Address gaps identified during your gap analysis. This might involve deploying new security tools, documenting policies, implementing access reviews, or establishing incident response procedures.
Audit Period / Controls Operating (3–12 months): Your controls must run consistently throughout this window. A 12-month period is standard, though first-time organizations sometimes use 6 months to accelerate their initial report covering a shorter specified period.
Auditor Fieldwork and Report Drafting (4–8 weeks after period end): The auditor collects evidence, conducts interviews, and tests control samples. Expect requests for:
- Firewall and access control configurations
- User provisioning and de-provisioning records
- HR onboarding and offboarding documentation
- Incident tickets and response records
- Change management approvals
- Vulnerability scan results
Report Issuance: After resolving any follow-up questions, the auditor delivers your final report.
For a typical mid-size SaaS company, the first-time SOC 2 Type 2 journey takes 6–18 months from project kickoff to final report, depending on your existing security posture and chosen TSC scope.
Costs and Ongoing Validity of SOC 2 Type 2
SOC 2 Type 2 represents both a financial investment and an ongoing operational commitment. Understanding the true costs helps you budget appropriately.
First-Time Audit Costs (2026 Estimates)
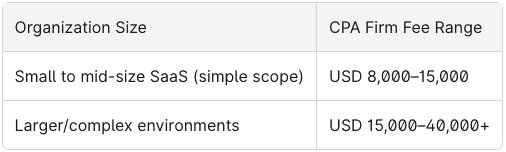
Ready to budget for your compliance journey? Stop guessing and check our SOC 2 audit calculator for a customized pricing estimate in minutes.
Beyond the audit fee, factor in:
- Internal staff time for preparation and evidence gathering
- Compliance automation platforms (typically USD 6,000–25,000 annually)
- Security tools like vulnerability scanning, SIEM, and endpoint protection
- Potential remediation costs for identified gaps

Report Validity and Annual Cycle
SOC 2 Type 2 reports don’t technically “expire,” but customers expect report covering a period that ended within the last 12 months. This means ongoing maintenance through annual audits rather than a one-time effort.
Most organizations establish overlapping or back-to-back audit periods to maintain continuous coverage:
- Year 1: 1 July 2024 – 30 June 2025
- Year 2: 1 July 2025 – 30 June 2026
- And so on…
Significant changes—like migrating to a new cloud provider, acquiring another company, or launching a new product line—may require adjusting scope or timing to keep your report credible.
Practical Roadmap to Achieve SOC 2 Type 2
Here’s a concrete, actionable checklist for compliance managers and security leaders planning their first Type 2 audit.
Phase 1 – Scope and Objectives
- Identify which products, services, and data types are in scope
- Determine locations and teams included in the audit
- Select TSC categories based on customer requirements (Security is mandatory; add others as needed)
- Decide whether to pursue Type 1 first or go directly to Type 2
Phase 2 – Gap Analysis and Design
- Compare current controls against SOC 2 criteria
- Document policies for access control, change management, incident response, and vendor risk management
- Identify gaps requiring remediation before the audit period begins
Phase 3 – Implementation and Evidence
- Deploy missing controls (MFA enforcement, centralized logging, encrypted backups)
- Establish your information security management system documentation
- Run security awareness training for all employees
- Begin collecting artifacts that will serve as audit evidence
Phase 4 – Operating Period
- Maintain controls consistently throughout the audit window
- Track security metrics and key control indicators
- Remediate issues promptly with documented evidence
- Conduct periodic internal reviews to catch problems early
Phase 5 – Work with the Auditor
- Select a CPA firm experienced in SOC 2 for your industry
- Agree on scope, TSC categories, and the exact audit period
- Respond promptly to evidence requests via the auditor’s secure portal
- Address follow-up questions with complete documentation
Phase 6 – Continuous Improvement
- Review findings and exceptions from the completed audit
- Fix root causes rather than just individual issues
- Refine processes for efficiency in subsequent cycles
- Implement continuous monitoring to maintain control effectiveness year-round
Practical Tip: Start logging and retaining access records at least 12 months before your first Type 2 period. This ensures you have sufficient history when auditors begin testing.
Automation platforms for compliance can significantly reduce manual evidence gathering and alert teams to control drift before it becomes an audit finding. Many organizations report reducing preparation time by up to 50% with the right tooling.

SOC 2 Type 2 and Other Frameworks (ISO 27001, PCI DSS, HIPAA, HITRUST)
Many organizations align SOC 2 Type 2 efforts with other standards to leverage common controls and reduce duplicated work.
ISO/IEC 27001
ISO 27001 is an international information security management system certification that’s more process-oriented and often preferred outside North America. SOC 2 remains more common for U.S. enterprise customers, but organizations serving global markets sometimes pursue both. The good news: risk assessment, access control, and incident response controls overlap significantly.
PCI DSS
PCI DSS focuses specifically on cardholder data with prescriptive technical controls. Payment platforms often maintain both PCI DSS compliance and SOC 2 Type 2 reports, since PCI addresses payment card data while SOC 2 covers broader data security and regulatory compliance concerns.
HIPAA
HIPAA establishes U.S. healthcare privacy and security requirements. SOC 2—especially with Privacy and Confidentiality criteria in scope—helps demonstrate complementary safeguards. Healthcare SaaS vendors frequently use SOC 2 Type 2 to show third party vendors and covered entities that they protect data beyond minimum HIPAA requirements.
HITRUST
HITRUST provides a prescriptive framework particularly popular in healthcare. Some organizations pursue HITRUST certification alongside SOC 2 attestation for stronger assurance to risk-averse healthcare buyers.
The practical benefit of multi-framework alignment is evidence reuse. Training records, risk assessment documentation, access reviews, and incident logs often satisfy requirements across multiple standards. A well-organized internal control environment pays dividends across all your compliance obligations.
FAQs about SOC 2 Type 2
These questions address practical concerns not fully covered above.
What is a SOC 2 Type 2 report?
A SOC 2 Type 2 report is an independent CPA attestation confirming that your security controls were designed and operated effectively over a specific period. Unlike Type 1 reports that check a single point in time, Type 2 verifies that controls worked consistently over a 6 to 12 month observation window.
What is the difference between SOC 2 Type 1 and Type 2?
SOC 2 Type 1 provides a snapshot of control design at a specific date, while Type 2 evaluates operating effectiveness over a duration of 3 to 12 months. Enterprise clients prefer Type 2 because it proves security controls actually work day after day rather than just looking good on paper.
How much does a SOC 2 Type 2 audit cost?
External audit fees typically range from $8,000 to $30,000 depending on the complexity of your environment and the scope of the audit. Organizations must also budget for internal staff time, compliance automation tools, and security software which can increase the total investment
How long does the SOC 2 Type 2 process take?
A first-time SOC 2 Type 2 journey generally takes 6 to 18 months from project kickoff to the final report. This timeline includes scoping, gap analysis, remediation, and the mandatory observation period where controls must operate consistently.
What Trust Services Criteria are included in SOC 2?
The Security criterion is mandatory for all SOC 2 reports and covers protection against unauthorized access. Organizations may optionally add Availability, Processing Integrity, Confidentiality, and Privacy based on their specific business needs and customer requirements.
Who needs a SOC 2 Type 2 report?
B2B service providers such as SaaS platforms, cloud infrastructure providers, and managed security services often require this report to close deals. Enterprise buyers in finance and healthcare frequently insist on a current Type 2 report before sharing sensitive data with vendors.
Is there a “SOC 2 certification” for Type 2?
SOC 2 is not a certification—it’s an attestation report. The CPA firm issues an opinion on your controls, but there’s no official pass/fail stamp or certificate you hang on your wall. You receive a report that customers and auditors review to evaluate your security practices.
Can a company fail a SOC 2 Type 2 audit?
Reports can contain qualified or adverse opinions when auditors identify significant control deficiencies. The report will list specific exceptions where controls did not operate effectively. Customers then decide how to weigh those findings—some may accept qualified opinions with explanations, while others may require clean reports.
How often should we repeat a SOC 2 Type 2 audit?
Most organizations perform SOC 2 Type 2 annually, maintaining near-continuous coverage so customers always have a recent report. Bridge letters can provide interim assurance between annual reports if there’s a gap.
Does SOC 2 Type 2 cover AI or machine-learning systems?
The trust services criteria are technology-agnostic. Any system processing client data—including AI models, ML pipelines, or automated decision systems—must meet the same controls for security, confidentiality, and privacy. If your AI system handles customer data, it falls within audit scope.
When is the best time for a startup to start SOC 2 Type 2?
Once you have a repeatable product, paying customers, and core security controls in place, it’s reasonable to begin planning. If larger prospects are asking for SOC 2 evidence or you’re losing deals to competitors with reports, that’s your signal. Starting the process 12–18 months before you absolutely need the report gives you adequate runway for remediation and the operating period.
Final Take: Get SOC 2 Certification Fast and Affordable with Secureleap
Achieving SOC 2 certification is a critical step in demonstrating your commitment to data security and winning the trust of enterprise customers. While the process can seem complex and costly, partnering with the right experts can make all the difference.
Secureleap specializes in helping organizations obtain SOC 2 certification quickly and at a very competitive price. With tailored services designed to streamline your audit process, reduce preparation time, and manage costs effectively, Secureleap ensures you get a credible, customer-trusted SOC 2 report without unnecessary delays or expenses.
Whether you're a startup or a growing mid-market company, Secureleap’s expertise and efficient approach can help you navigate the compliance journey smoothly, so you can focus on what matters most—growing your business with confidence.
Contact Secureleap today to learn how we can support your SOC 2 compliance needs and accelerate your path to certification.






