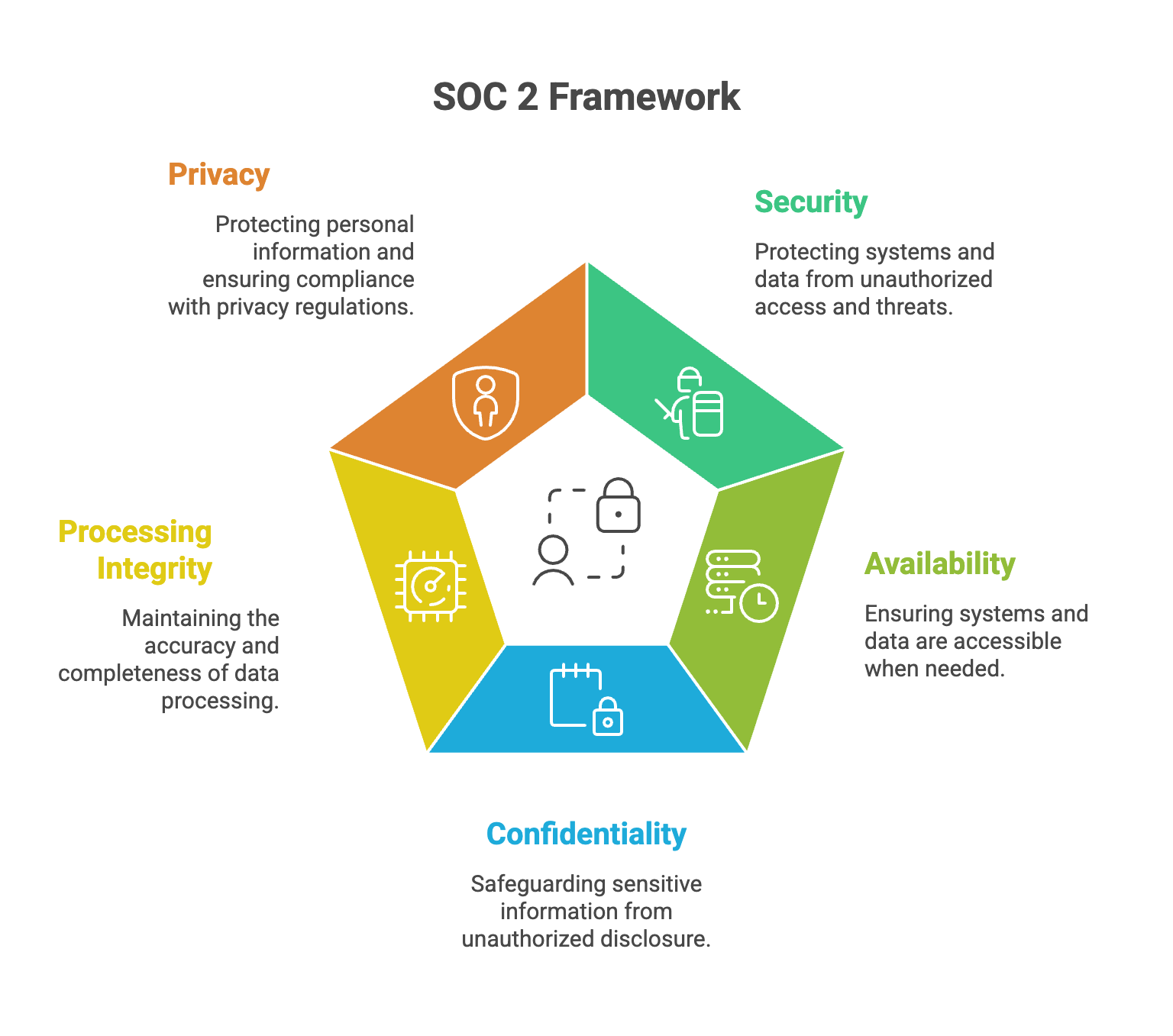
There are five trust services criteria (TSC) that can be included in a SOC 2 report: security, availability, confidentiality, processing integrity, and privacy. These principles determine the necessary security controls and internal processes required for SOC 2 compliance. The SOC 2 trust principles were created by the American Institute of Certified Public Accountants (AICPA), referencing international certified professional accountants, to help companies demonstrate their commitment to protecting sensitive information.
SOC 2 compliance is flexible—organizations can tailor their SOC 2 audit by selecting the applicable criteria most relevant to their services and customer needs. This flexibility allows alignment with core business objectives and compliance priorities. The audit process is conducted by an independent third party and serves as evidence of an organization’s commitment to data protection, building customer trust. SOC 2 compliance serves as a competitive differentiator, helps organizations demonstrate their commitment to protecting sensitive information, and builds trust with customers and partners. A targeted SOC 2 audit can save time and money while still delivering the assurance customers need.
The selection of SOC 2 trust principles should reflect the specific services provided, customer needs, unique business context, and contractual obligations, including those defined in service level agreements. Customer demands and contracts often drive the selection of SOC 2 trust principles. SOC 2 helps organizations streamline operations and formalize internal security processes through the audit process. SOC 2 reports show customers that they can trust a business with their most important data by evaluating its internal controls and security practices.
Introduction to SOC 2
In today’s digital landscape, service organizations are entrusted with vast amounts of sensitive customer data, from financial transactions and intellectual property to personally identifiable information (PII). Ensuring the security and integrity of this data is not just a best practice—it’s a business imperative. That’s where SOC 2 comes in.
SOC 2 (Service Organization Control 2) is a widely recognized framework developed by the American Institute of Certified Public Accountants (AICPA) to evaluate the internal controls of service organizations, particularly those that store, process, or transmit customer data in the cloud. At its core, SOC 2 is built on the Trust Services Criteria (TSC), a set of five foundational principles(security, availability, processing integrity, confidentiality, and privacy) that determine how organizations should protect and manage client data.
For high-growth startups and SMBs, especially in SaaS, fintech, and healthtech, SOC 2 compliance is often a prerequisite for doing business with enterprise customers. The SOC 2 trust principles guide organizations in implementing robust security controls and internal processes to safeguard customer data, mitigate security risks, and maintain a strong control environment. These principles help organizations address everything from physical access controls and logical access restrictions to incident response, data encryption, and risk assessment.
1. Security
The security principle is the foundational and only mandatory trust principle for SOC 2 compliance. Unlike the other criteria, the security TSC is required for all SOC 2 reports.
Security is the only principle that is required to become SOC 2 compliant, while the others are optional based on business needs.
The objective of the security TSC is to ensure information and systems are protected against unauthorized access, unauthorized disclosure of information, and damage to systems. Key controls under the security criterion include multi-factor authentication (MFA), firewalls, and intrusion detection.
There are a total of 9 security ‘points of focus’ to be met in order to meet the security criteria. These include:
- CC1: Control Environment
- CC2: Communication and Information
- CC3: Risk Assessment
- CC4: Monitoring Activities
- CC5: Control Activities
- CC6: Logical and Physical Access Controls
- CC7: System Operations
- CC8: Change Management
- CC9: Risk Mitigation
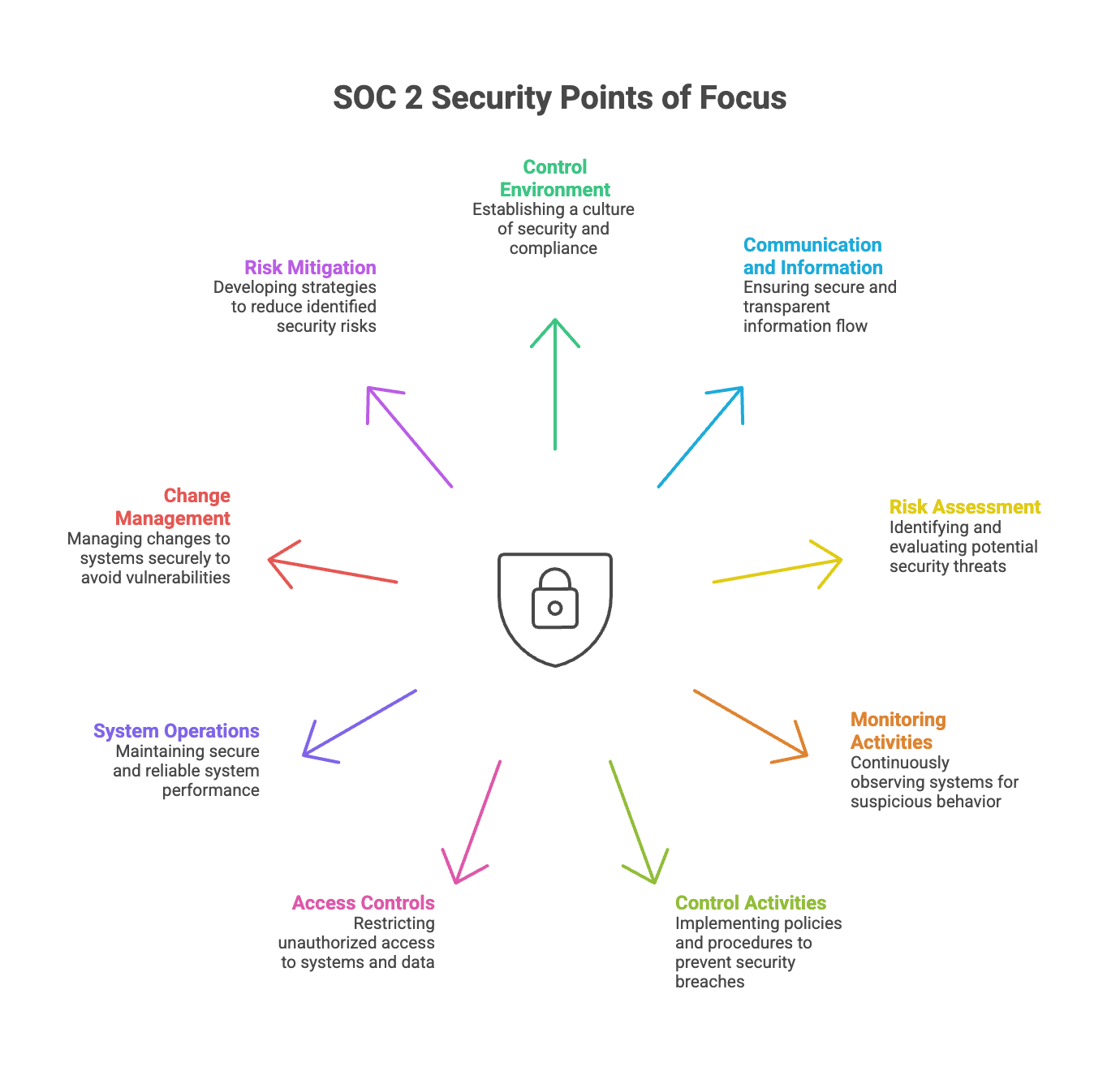
These are considered the common criteria for SOC 2 audits. Supplemental criteria, derived from frameworks like COSO, may also be required to meet comprehensive security requirements.
Organizations must implement control activities to fulfill the objectives of these ‘points of focus.’ Each point should be supported by at least two to three controls to ensure that if one control fails, the remaining controls continue to uphold the criteria, preventing a qualified audit opinion.
2. Availability
The objective of the availability TSC is to ensure that the availability principle is met by providing reliable access to system resources and data for customers and employees when needed for its intended purpose. Capacity management, including monitoring current processing capacity and planning for future growth, is essential to maintain system availability and meet service level agreements (SLAs). Recovery systems are critical for restoring access to data and services in the event of outages or technical failures. There are three additional ‘points of focus’ to meet to achieve the availability criteria.
3. Confidentiality
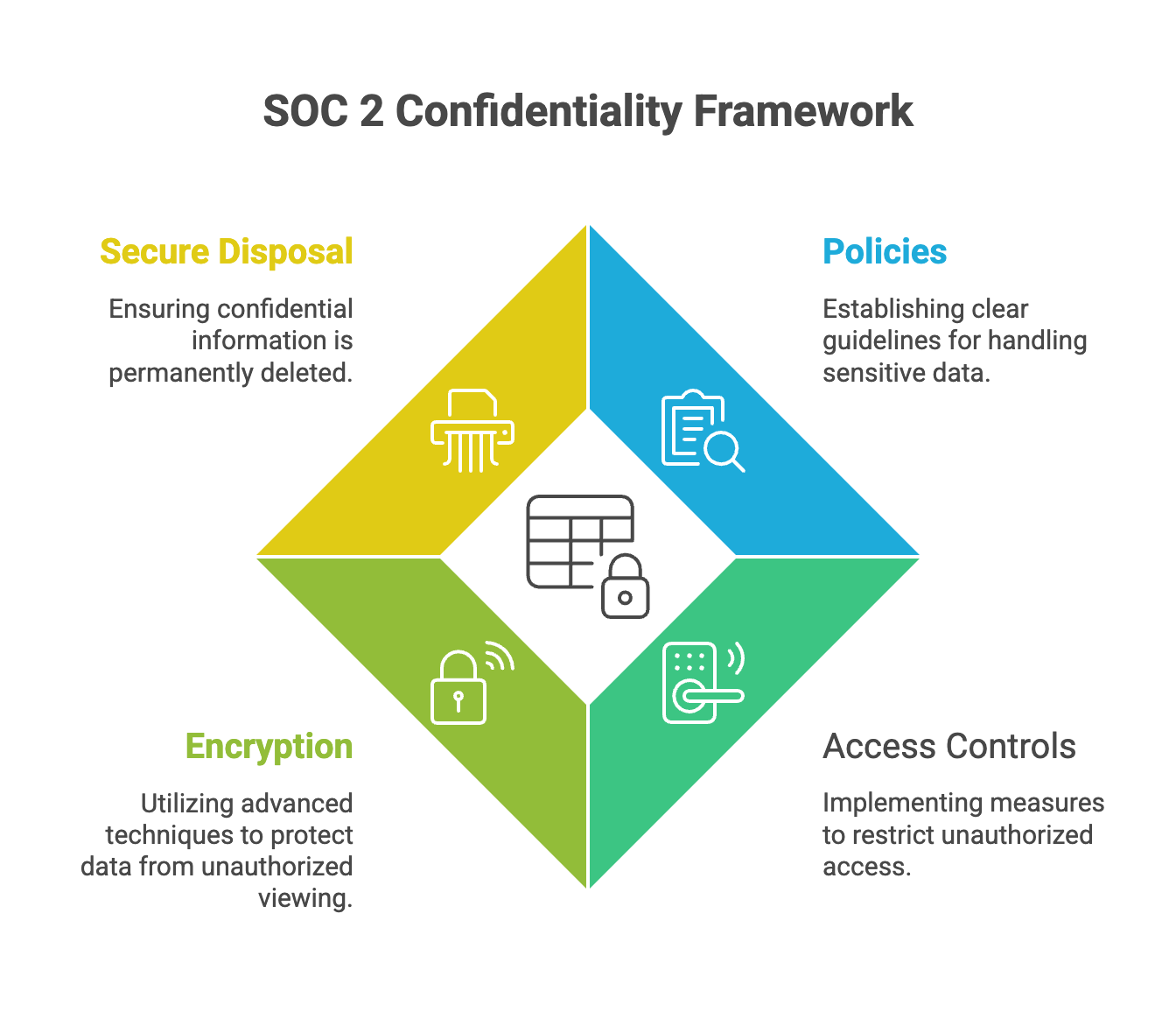
The confidentiality principle in SOC 2 refers to an organization's ability to safeguard confidential information, including sensitive business information such as business plans and financial data, through every phase of its processing. Protecting confidential information involves implementing policies, access controls, encryption, and secure disposal procedures. Confidentiality in SOC 2 protects information designated as confidential and focuses on encryption and access limitations. The objective of the confidentiality TSC is to ensure that information defined as confidential within the system is protected. There are two additional ‘points of focus’ to meet to achieve the confidentiality criteria.
4. Processing Integrity
The objective of the processing integrity TSC is to ensure that organizations process data and system processing is complete, valid, accurate, timely, and authorized to meet the entity’s objectives. Maintaining accurate data and high data quality is essential for reliable outputs and compliance. Processing integrity is especially critical for organizations that provide financial reporting services, as it ensures the accuracy and validity of financial transactions and reports. This principle is particularly important for fintech or data-heavy organizations, where processing integrity in SOC 2 ensures that system processing is robust and trustworthy. There are five additional ‘points of focus’ to meet to achieve the processing integrity criteria.
5. Privacy
There are eight additional ‘points of focus’ to meet to achieve the privacy criteria. The privacy principle focuses on how an organization gathers, stores, uses, preserves, reveals, and disposes of personal information, including personal identifiable information (PII) and other sensitive data. SOC 2 focuses on the collection, use, retention, disclosure, and disposal of PII, and organizations must have processes for handling access requests from individuals regarding their personal data. Secure data storage is essential for maintaining privacy and compliance with privacy criteria. This can be the biggest lift for most entities, both due to the sheer number of privacy points of focus there are and due to the specific requirements within each of those points of focus.
Notably, the availability, confidentiality, processing integrity, and privacy TSCs are optional. These additional criteria are not required to have a complete SOC 2 report, but can be useful additions. Typically, an entity will add additional criteria when there is a business need or when a customer requires them to highlight the processes and procedures surrounding one or more of these areas.
Including additional criteria does come at a cost and involves additional control activities, but most audit firms can and will highlight existing controls from the security category to help clients achieve the additional criteria, making it less of a hassle. Adding additional criteria, when necessary, can be a great way to add value and build trust with customers.
That said, a common mistake we see is companies piling on additional criteria without a business need. An example could be a company wanting to add the privacy TSC, even though they don’t maintain personal information within their system. This creates more work for the organization when the payoff may be minimal to the customers.
How Secureleap Can Help Me?
SecureLeap supports your organization throughout the entire SOC 2 compliance process—from developing thorough security policies and implementing essential controls to preparing for and successfully passing the audit.With expert guidance designed specifically for high-growth startups and SMBs, SecureLeap helps you efficiently and effectively meet all SOC 2 trust principles, build customer trust, and accelerate business growth. Contact SecureLeap today for a free consultation and start your journey toward SOC 2 compliance with confidence.
FAQ for SOC2 5 Principles
What are the 5 SOC 2 principles?
The five principles are security, availability, confidentiality, processing integrity, and privacy. These Trust Services Criteria determine the necessary security controls and internal processes for compliance.
Which SOC 2 principle is mandatory?
The security principle is the only mandatory requirement for all SOC 2 reports. It ensures information and systems are protected against unauthorized access, disclosure, and damage.
Are all SOC 2 principles required for compliance?
No, only security is required, while availability, confidentiality, processing integrity, and privacy are optional. Organizations select additional criteria based on business needs and customer requirements.
What is the focus of the privacy principle in SOC 2?
The privacy principle focuses on how an organization gathers, stores, uses, reveals, and disposes of personal information. It specifically addresses the handling of personal identifiable information and sensitive data.
Why should a company include optional SOC 2 principles?
Adding optional criteria helps build trust with customers who require assurance in specific areas like data availability or processing accuracy. However, companies should only include them if there is a clear business need to avoid unnecessary work.






