If you’re a startup founder or security lead trying to figure out what a penetration test should actually cost in 2026, you’re in the right place. The short answer: it depends. The longer answer is what this guide is all about.
Penetration testing isn’t a commodity product with standardized pricing. What you’ll pay depends on what you’re testing, how deep you want to go, and what evidence you need to satisfy auditors or enterprise customers. But with the right understanding of cost drivers and realistic expectations, you can budget intelligently and avoid both overpaying and underbuying.
Executive summary: typical pentest pricing in 2026
Let’s start with the numbers you came here for. In 2026, pentest pricing for startup-focused engagements typically falls between $6,000 and $25,000. That said, you can find options ranging from around $4,000 for narrow-scope tests to $60,000+ for complex, multi-environment assessments.
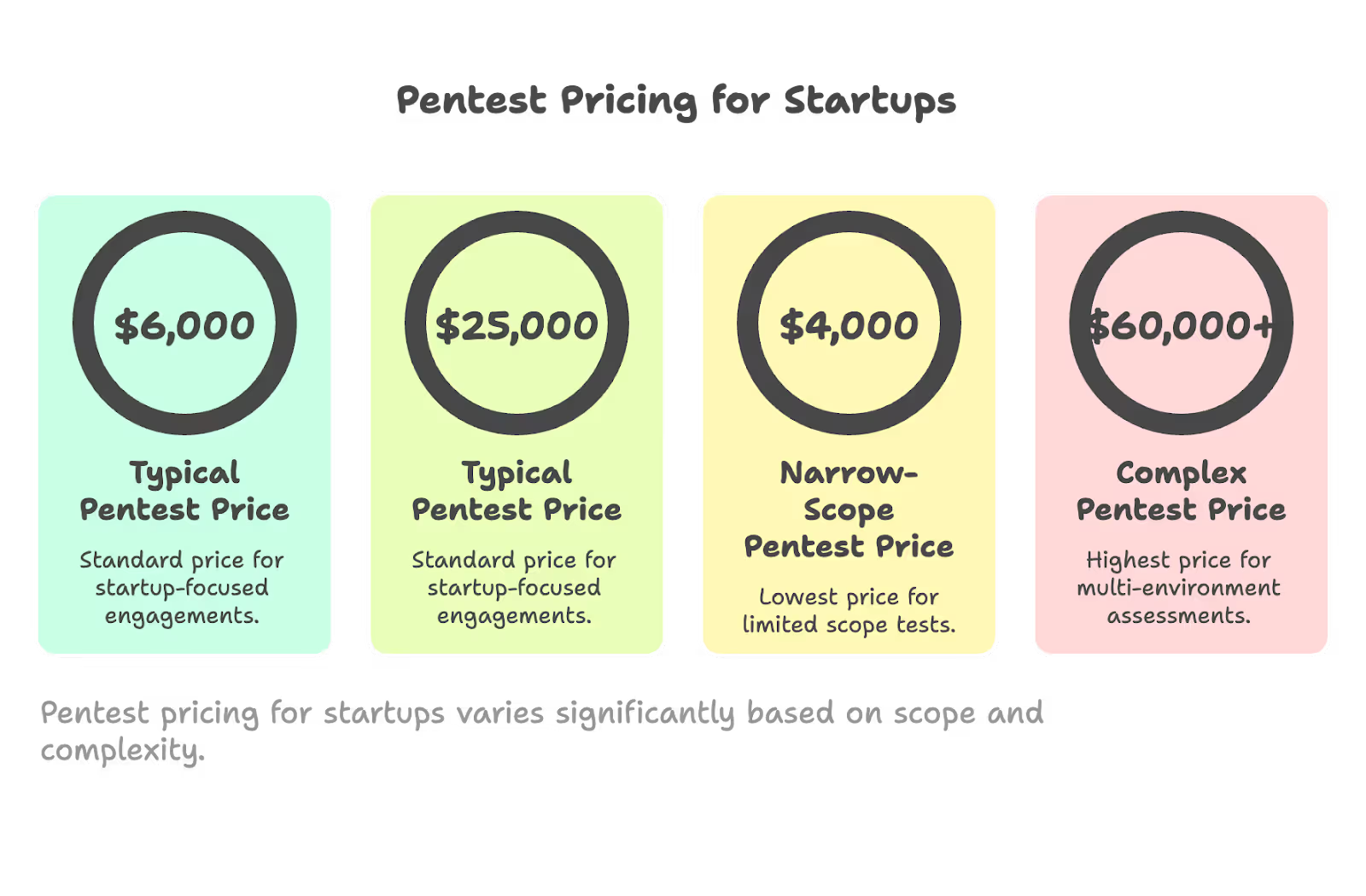
SecureLeap specializes in pricing tailored for SaaS, fintech, and healthtech startups. Our clients tend to have smaller technical footprints than enterprise organizations, but they face strict security requirements from enterprise buyers, SOC 2 auditors, and ISO 27001 certification bodies. This creates a specific need: thorough, compliance-ready penetration testing that doesn’t require a six-figure budget.
Most SecureLeap clients spend between $4,000 and $8,000 per annual pentest. This range satisfies SOC 2 Type II requirements, ISO 27001 certification audits, and the security questionnaires that enterprise prospects send during sales cycles. It covers manual testing of production web applications, APIs, and cloud configurations—the core attack surface for most B2B SaaS companies.
Here’s what drives that pricing:
- Scope: Number of applications, APIs, IP ranges, and cloud accounts in scope
- Methodology: Black box, grey box, or white box testing approach
- Compliance depth: Whether you need basic technical findings or audit-ready reports mapped to control frameworks
- Tester experience: Senior pentesters with certifications like OSCP command higher day rates
- Timeline: Rush engagements during peak audit seasons cost more
The rest of this guide breaks down each of these factors so you can estimate your own budget and evaluate quotes intelligently.
Core factors that drive pentest pricing
Penetration testing is not a commodity purchase. You can’t compare providers purely on price without understanding what drives that price. In 2026, pentest pricing is shaped by a predictable set of factors that every startup and SMB should understand before requesting quotes.
Here’s the practical insight: trimming or clarifying scope is often the fastest way founders can bring a quote from $25,000 closer to $12,000 without sacrificing compliance value. Understanding these factors puts you in control.
The primary cost drivers include:
- Scope and asset count: More apps, APIs, and IPs mean more testing hours
- Environment complexity: Legacy code, custom frameworks, and multi-tenant architectures require more manual effort
- Methodology: Black box testing takes longer; white box with code review adds specialized work
- Compliance requirements: SOC 2 and ISO 27001-aligned reports require more documentation
- Tester seniority: Experienced testers with certifications cost more per day
- Timeline: Rush engagements and peak-season scheduling carry premiums
- Reporting expectations: Executive summaries, control mappings, and remediation guidance add time

Scope size and technical complexity
The number of in-scope assets is the single largest factor that will influence your overall cost. More assets mean more testing hours, and testing hours drive price.
Key points to remember:
- Each additional web application typically adds $4,000-$8,000 to the engagement
- API testing adds to web app costs, but bundling often reduces the per-unit price
- Cloud accounts (AWS, GCP, Azure) each add $5,000-$15,000 depending on complexity
- Mobile application penetration testing adds $4,000-$10,000 per platform
- Detailed scoping up front prevents surprise change orders mid-engagement
When you request a penetration test quote, provide as much detail as possible about your test scope. Vague descriptions lead to padded quotes or, worse, incomplete testing.
Methodology: black box, grey box, and white box
The type of penetration test you choose affects both cost and coverage. Each methodology has trade-offs that impact pricing.
Black box testing: The penetration tester has no prior knowledge of your systems. They approach the engagement like an external attacker, using reconnaissance and enumeration to discover entry points. This simulates real world attacks but is time-intensive. Black box tests often cost 10-30% more than grey box for equivalent assurance because testers spend more time on discovery.
Grey box testing: The tester has limited access—typically user-level credentials, API documentation, or architecture diagrams. This focuses effort on higher-risk areas rather than basic reconnaissance. Most SOC 2 and ISO 27001-focused pentests use grey box approaches for efficiency.
White box testing: The tester has full access to source code, architecture documentation, and internal systems. This enables in depth testing and in depth analysis but requires specialized skills. White box with code review can add 30-70% over a basic grey-box test due to the additional effort involved.
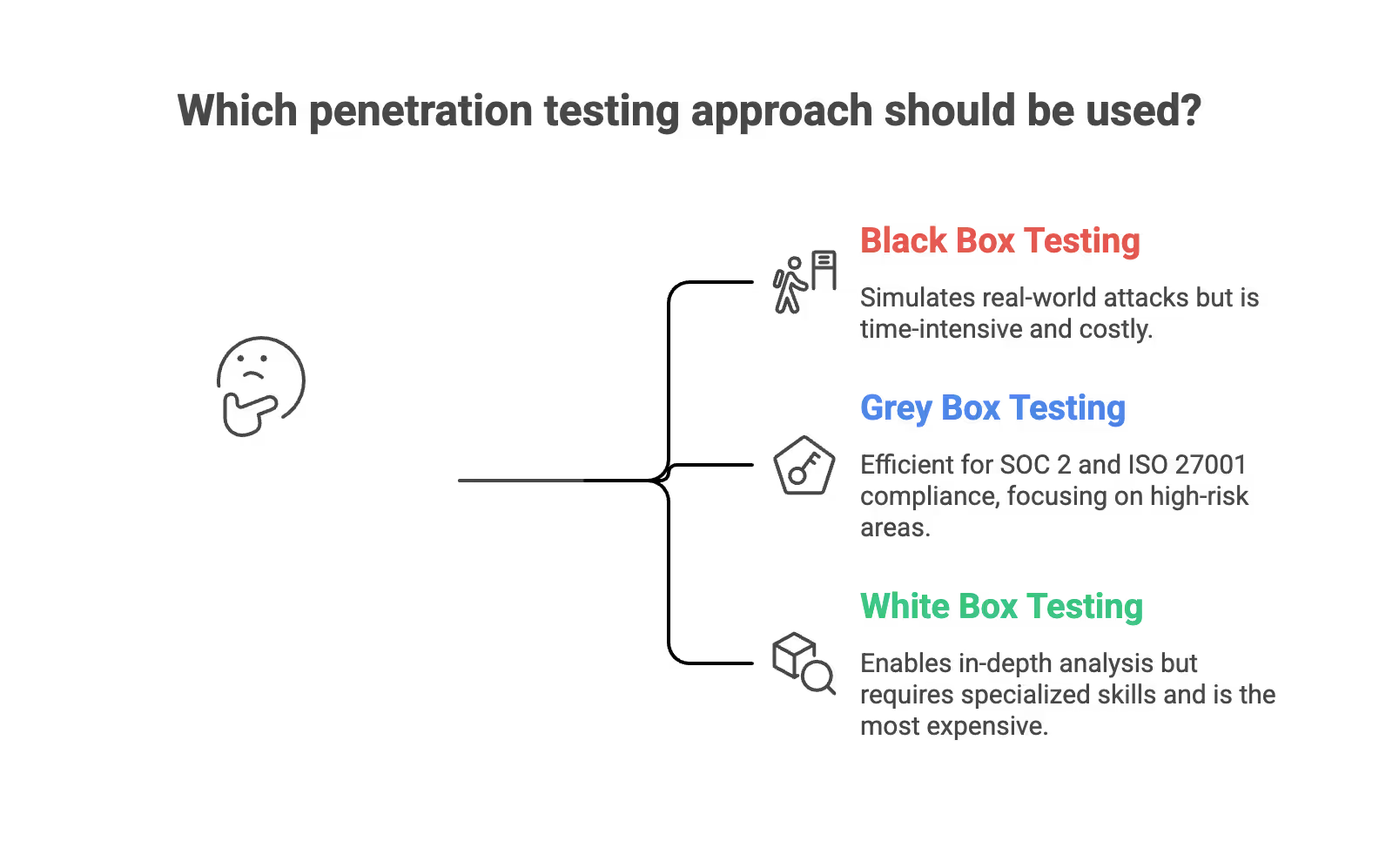
For SOC 2 and ISO 27001 evidence, SecureLeap typically recommends grey-box pentests with targeted white-box components for critical modules. This balances thoroughness with cost efficiency and produces the artifacts auditors expect.
Compliance, reporting depth, and evidence needs
Audits and enterprise customers in 2026 expect specific artifacts from your penetration testing engagements. A basic technical report may satisfy internal needs, but compliance requirements demand more.
What compliance-driven reports typically include:
- Executive summary suitable for board or leadership review
- Detailed technical findings with exploitation evidence
- Risk ratings aligned to industry standards (CVSS, custom severity scales)
- Remediation recommendations with prioritization
- Re-test results demonstrating issue closure
This additional reporting work adds 10-25% to cost versus a basic technical report.
SOC 2 Type II reports in 2026 nearly always ask when your last pentest occurred and whether high and critical findings were remediated. Having audit-ready documentation saves time during fieldwork and reduces auditor questions.
Reporting quality is a tangible line item in penetration testing pricing, not an afterthought. Ask providers explicitly what their deliverables include.
Timeline, urgency, and scheduling
When you need your pentest completed affects what you’ll pay. Compressed timelines trigger premium pricing across the industry.
Common scenarios and their cost impact:
- Standard scheduling (6-8 weeks notice): Best pricing, most flexibility
- Short notice (2-4 weeks): Expect 15-25% premium
- Rush engagement (under 2 weeks): Expect 30-50% premium, limited availability
Example: A $12,000 test might become $15,000-$18,000 if scheduled on short notice during peak audit seasons (Q1 and Q4 are particularly busy as companies prepare for year-end compliance deadlines).
Planning recommendations:
- Schedule pentests 60-90 days before SOC 2 or ISO 27001 audit fieldwork
- Account for remediation time—you’ll need 4-8 weeks to fix issues before re-testing
- Book follow up tests and retesting windows in advance
- Consider annual pentest plans if you have predictable renewal and audit dates
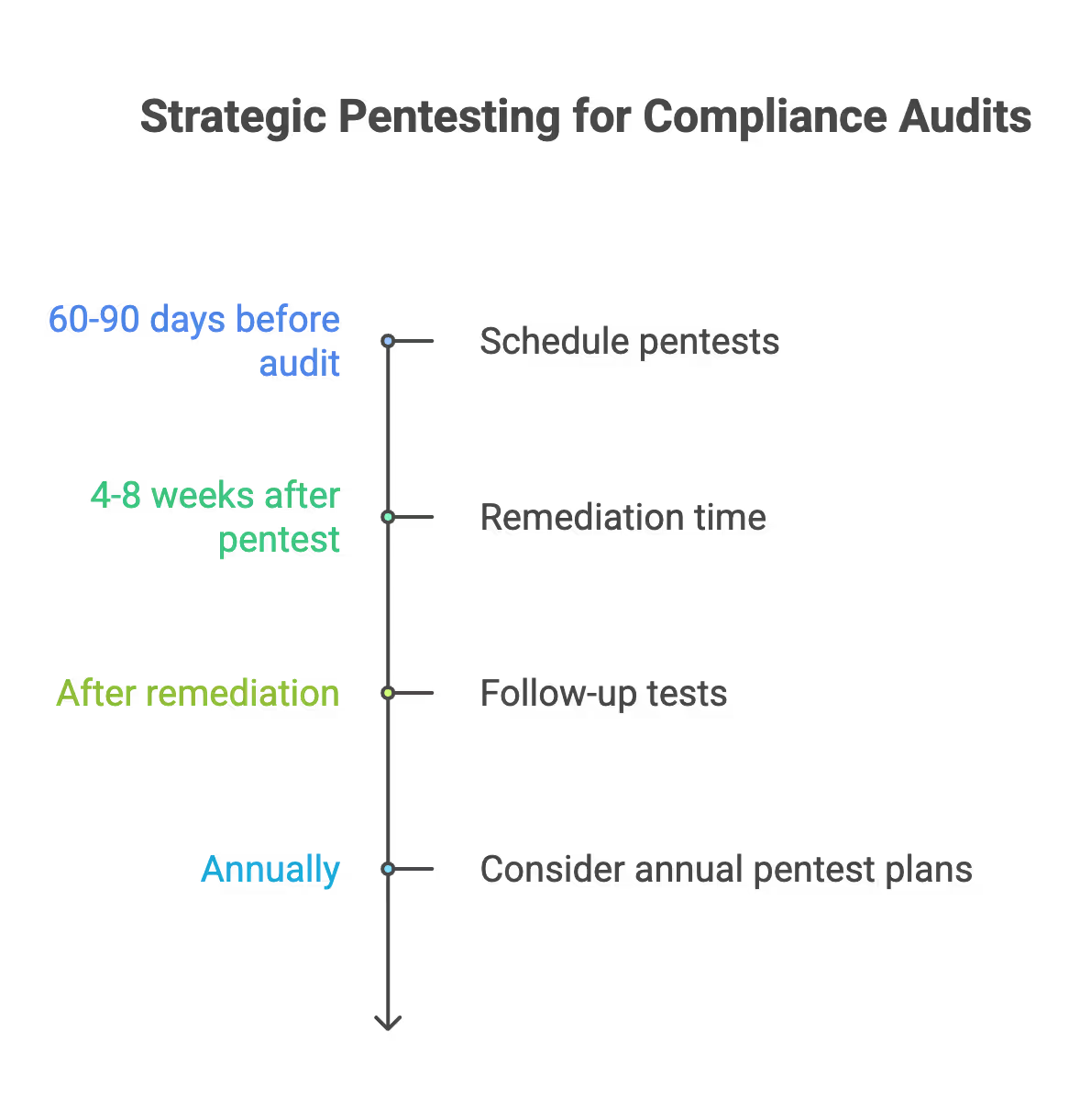
SecureLeap offers scheduled annual pentest plans for startups with predictable audit cycles. This locks in pricing, guarantees availability, and simplifies budget planning.
Typical pentest price ranges by test type (2026)
This section provides quick-reference pricing that founders and security leads can use to sanity-check quotes in 2026. These are realistic bands for North American and Western European providers doing mostly manual testing with startup-scale scopes.
These ranges assume 3-10 days of work, which is typical for seed to Series B startups.

Web application and SaaS pentest pricing
Web application penetration testing is the most common engagement type for B2B SaaS startups. In 2026, expect to pay $4,000-$25,000 per web or SaaS application. Most SecureLeap startup clients fall in the $4,000-$8,000 range.
Factors that push costs higher:
- Complex role-based access control with many user types and permission levels
- Multi-tenant data separation requiring isolation testing
- Integrations with critical third-party APIs (payment processors, identity providers)
- Heavy use of modern SPA frameworks with complex client-side logic
- Business logic flaws that require manual analysis to identify
Concrete examples help illustrate this:
- Simple scope: A single-tenant B2B SaaS with one production web app and one REST API, hosted on a single AWS account. Typical pricing: $4,000-$8,000.
- Medium scope: A multi-tenant SaaS with role-based access control, 3 microservices, separate staging and production environments. Typical pricing: $8,000-$20,000.
- Complex scope: Multiple customer-facing applications, extensive API integrations, mobile apps, and multi-cloud infrastructure. Typical pricing: $20,000-$40,000+.
SecureLeap includes both business-logic testing and OWASP Top 10 coverage in our standard SaaS pentest scope. Web application testing at this level goes well beyond automated vulnerability scanning to uncover security weaknesses that scanners miss.
API pentest pricing
APIs represent a growing portion of the attack surface for modern SaaS companies. In 2026, API-focused pentests typically range from $5,000-$20,000, depending on the number of endpoints and complexity of authentication flows.
Pricing factors:
- Number of endpoints: A 20-endpoint REST API costs less to test than a 200-endpoint platform API
- Authentication complexity: OAuth 2.0, JWT, API keys, mTLS all require different testing approaches
- Documentation quality: Well-documented OpenAPI specs reduce discovery time; undocumented APIs take longer
- GraphQL vs REST: GraphQL APIs often require specialized testing methodology testing
Where you fall in the range:
- Lower end ($5,000-$10,000): Single public REST API with well-documented OpenAPI specs and standard auth
- Upper end ($15,000-$20,000): Sprawling microservice APIs or GraphQL backends with complex authorization
SecureLeap often bundles API testing with web applications or mobile application testing for 10-20% less than purchasing separate engagements. For B2B SaaS with many integrations and partner-facing endpoints, API testing is essential—many SOC 2 customers in 2026 specifically request API pentest results during due diligence.
Mobile application pentest pricing
Mobile application penetration testing in 2026 ranges from $6,000-$25,000 per platform. Costs increase significantly when both iOS and Android plus backend APIs are in scope together.
Cost drivers for mobile testing:
- Platform count (iOS-only vs. iOS + Android)
- Use of biometrics and secure enclave features
- Offline data storage and encryption requirements
- Device binding and certificate pinning
- Integration with healthcare or fintech APIs requiring additional scrutiny
Budget optimization tip: Focus your initial test on your primary platform (e.g., iOS only) and critical user flows. This keeps the average cost manageable while still identifying the most important security gaps. Mobile application testing can be expanded in subsequent years as your security posture matures.
Cloud infrastructure pentest pricing (AWS, GCP, Azure)
Cloud penetration testing has become essential as startups run their entire infrastructure in AWS, GCP, or Azure. In 2026, expect $6,000-$35,000 for a focused cloud security assessment of a single primary account or subscription.
What cloud testing typically covers:
- Configuration review against CIS benchmarks and cloud services best practices
- IAM analysis (roles, policies, privilege escalation paths)
- Storage controls (S3 bucket permissions, encryption settings)
- Network controls (security groups, VPC configuration)
- Limited exploitation of identified misconfigurations
Cost multipliers:
- Multi-account environments (production + staging + compliance) increase scope significantly
- Multi-cloud setups (AWS + GCP) effectively double the work
- Complex networking (Transit Gateway, VPC peering, hybrid connectivity) adds time
External and internal network pentest pricing
Traditional network penetration testing remains relevant even for cloud-native companies. External network testing evaluates your internet-facing perimeter; internal network testing examines what happens if an attacker gains a foothold inside your environment.
2026 benchmarks:
- External penetration test (up to 25 IPs): $5,000-$15,000
- External penetration test (50-100 IPs): $12,000-$25,000
- Internal penetration testing (small office or co-located environment): $8,000-$25,000
For remote-first startups with minimal traditional internal network infrastructure, external and cloud testing often take priority. Many of our clients can deprioritize internal network testing in early stages because their “internal network” is essentially employee laptops connecting to cloud services.
SecureLeap prioritizes external, SaaS, and cloud penetration testing services for cloud-native companies. This keeps total pentest spend manageable while covering the attack surface that actually matters for your security risks and compliance considerations.
Red team and advanced scenarios for scaling companies
True red team exercises—including social engineering tests, physical access testing, and multi-vector attack simulations—typically run $40,000-$120,000+ in 2026. These are comprehensive assessments that test your entire security program, not just individual systems.
SecureLeap typically recommends red teaming only once a company has:
- A mature security program with defined policies and controls
- Completed several standard penetration tests and addressed findings
- An internal security team or SOC capable of detection and response
- Incident response playbooks and baseline defenses in place
For early-stage startups, red teaming is usually overkill. You’ll get far better ROI from targeted web, API, and cloud testing combined with a vCISO-guided security roadmap. Save red teaming for post-Series B when your security posture can actually benefit from adversarial simulation.
Pentest pricing models: how providers structure costs
Beyond the price itself, how a provider structures their pricing affects your budget predictability, flexibility, and ability to align testing with your development cycles. In 2026, you’ll encounter several common models.
SecureLeap primarily uses transparent fixed-fee engagements for startups. We find this matches how startups budget and provides the predictability founders need for board reporting and investor updates. We also offer annual bundles that combine penetration testing services with compliance and vCISO support.
Fixed-price project engagements
Fixed-price pentests are the most common model for defined scopes. You agree on scope, deliverables, and timeline upfront, and pay a single number (e.g., $12,500 for 8 days of testing and reporting).
Benefits:
- Easy budget approval—one number to get signed off
- No surprise invoices at project end
- Clear deliverables mapped to SOC 2 or ISO 27001 needs
- Simpler vendor management
Risks to watch for:
- Under-scoped fixed-price work can lead to incomplete testing if the provider underestimated complexity
- Scope changes mid-engagement may trigger change orders
- Some providers pad quotes to protect themselves from underestimation
This model generally works best for early-stage startups with defined applications and clear compliance requirements.
Time and materials (T&M)
Time and materials billing charges based on actual hours or days used. Typical blended hourly rates for reputable firms in 2026 run $200-$350 per hour.
When T&M makes sense:
- Evolving or experimental scopes where requirements aren’t fully defined
- Rapid testing of new prototypes during active development
- Unstructured environments where discovery is part of the engagement
- Add-on work requested mid-project
Downsides:
- Harder to forecast total spend
- Risk of scope creep if not actively managed
- Requires more effort to manage the engagement
Credits and retainer-based models
Credits or retainers involve purchasing a bucket of pentest days or hours upfront—for example, 20 days to use over 12 months at a discounted effective rate.
This model works well for:
- Companies with frequent releases requiring ongoing testing
- Regulated sectors needing multiple tests per year
- Organizations wanting testing frequency flexibility
- Continuous testing programs tied to CI/CD pipelines
Watch out for:
- Unused credits expiring and becoming sunk cost
- Pressure to use credits on low-value work
- Complexity in tracking utilization
Bundled pentest + compliance services
Bundled services offerings package penetration testing with SOC 2, ISO 27001, or HIPAA readiness work and compliance automation tool implementation (Drata, Vanta, Secureframe).
In 2026, bundles often reduce unit pentest costs by 10-30% compared to buying pen testing services separately. The real value, though, is operational: one partner that understands both the technical and audit side reduces back-and-forth and eliminates duplicate work.
SecureLeap’s bundle concept combines cybersecurity consulting, audit readiness, and pentesting—designed specifically for seed to Series B SaaS companies with looming enterprise deals. When you’re racing to close a customer that requires SOC 2 evidence, having a single team handle both the pentest and the compliance preparation dramatically reduces coordination overhead.

Pentest pricing for compliance: SOC 2, ISO 27001, HIPAA, PCI
Many startups come to SecureLeap because an enterprise prospect, board member, or auditor specifically requested a pentest tied to a compliance framework. This context affects both scope and cost.
Compliance-driven pentests emphasize:
- Scope that covers in-scope systems defined by the compliance framework
- Testing methodology that aligns with control requirements
- Reporting that maps findings to specific controls
- Evidence artifacts that auditors can consume directly
For a Series A SaaS firm preparing for their first SOC 2 Type II, or a healthtech startup processing PHI under HIPAA, the pentest isn’t just a security exercise—it’s a compliance deliverable with specific requirements.
SOC 2-focused pentest pricing
SOC 2-aligned pentests for SaaS startups typically cost $4,000-$8,000 in 2026. This covers production web apps, APIs, and cloud configurations—the systems included in most SaaS companies’ SOC 2 scope.
Timing matters:
- Schedule your pentest 60-90 days before SOC 2 audit fieldwork
- Allow 4-6 weeks for remediation of high and critical findings
- Plan for re-testing before auditors arrive
SOC 2 auditors in 2026 expect at least one meaningful pentest during the reporting period, with evidence that high/critical issues were remediated. A “pentest with no findings” is fine; a “pentest with critical findings and no evidence of fixes” creates audit issues.
SecureLeap provides reports and control mappings that auditors and compliance platforms (Drata, Vanta, Secureframe) can easily consume. Our clients don’t spend hours reformatting pentest results to fit their compliance workflow.
ISO 27001 and global frameworks
ISO 27001 doesn’t prescribe a specific pentest frequency, but auditors expect risk-appropriate technical security testing as part of your ISMS. Typical cost of a penetration testing engagement is similar to SOC 2 ($4,000-$8,000), with adjustments for multi-region or multi-cloud scopes.
Companies targeting EU and UK customers in 2026 may need to align pentests with:
- DORA (Digital Operational Resilience Act) for financial services
- NIS 2 for essential and important entities
- Local data protection authority expectations
HIPAA, PCI DSS, and high-sensitivity environments
Handling protected health information (HIPAA) or cardholder data (PCI DSS) pushes pen testing costs higher. These environments require stricter data-handling rules, more complex segmentation testing, and closer coordination with compliance teams.
2026 ranges for compliance-specific testing:
- HIPAA-aligned pentest: $12,000-$30,000+ depending on environment size and data flows
- PCI DSS pentest: $15,000-$35,000+ depending on cardholder data environment scope and segmentation
These tests often require coordination with compliance officers and legal teams, adding to overall effort and cost. Data breaches in these environments carry regulatory penalties and reputational damage far exceeding typical cost ranges.
Retesting, remediation support, and “hidden” pentest costs
The initial penetration test quote is only part of the true cost. Remediation, retesting, and internal time investment all matter when budgeting for security testing.
Common additional costs to plan for:
- Fix validation (retesting): Confirming that vulnerabilities were actually fixed
- Advisory sessions: Calls with engineers to explain findings and remediation approaches
- Documentation updates: Revising policies and procedures based on findings
- Tooling: Licenses for security tools recommended in the report
- Engineering time: Developer hours spent implementing fixes
Remediation guidance and engineering time
Your engineers will spend significant time acting on pentest results:
- Reproducing findings to understand root causes
- Patching code and hardening configurations
- Updating CI/CD pipelines to prevent regressions
- Documenting changes for compliance evidence
This internal labor can equal or exceed the external pentest fee. A startup discovering 10 high/medium issues might spend 2-4 sprints fully addressing them—that’s real engineering cost diverted from feature development.
Retesting and evidence for customers and auditors
Retesting matters because customers and auditors want to see that vulnerabilities were fixed, not just identified. A pentest report showing critical vulnerabilities with no re-test evidence raises questions during due diligence.
Pricing guidance for retesting:
- Many providers charge 15-30% of the original fee for a separate re-test
- Some limit included retesting to high/critical issues only
- Retesting outside the original engagement window typically costs extra
Questions to ask when comparing quotes:
- Is retesting included? For which severity levels?
- What’s the time window for included retesting?
- What’s the cost for additional re-test cycles if needed?
Getting these answers in writing before signing prevents surprise invoices after remediation is complete.
SecureLeap offers free retests for up to 60 days after the initial penetration test to ensure that any identified vulnerabilities have been properly addressed and remediated, providing added confidence in your security posture without extra costs.
How to choose a pentest partner and budget realistically
The “right” penetration testing pricing is the price that matches your risk profile, stage, and compliance goals—not simply the lowest quote you receive. Cheap penetration tests that miss critical vulnerabilities or produce unusable reports waste money rather than save it.
When evaluating providers in 2026:
- Compare 2-3 quotes using a simple matrix: price, depth of manual testing, reporting quality, and compliance support
- Look beyond the number to understand testing methodology and tester qualifications
- Ask specifically about deliverables and how they map to your compliance needs
- Check references from similar companies (stage, industry, compliance requirements)
SecureLeap is a strong fit for B2B SaaS, fintech, and healthtech startups from seed to Series B that need both pentest evidence and guidance identifying vulnerabilities and closing security gaps. We understand the urgency of enterprise deals and the specific requirements of SOC 2 and ISO 27001 audits.
FAQ for Pentest Pricing
How much does penetration testing cost for startups in 2026?
In 2026, penetration testing for startup-focused engagements typically falls between $6,000 and $25,000. However, basic narrow-scope tests can start around $4,000, while complex multi-environment assessments can exceed $60,000.
What are the main factors that determine pentest pricing?
The primary cost drivers are the scope of assets (apps, APIs, IPs), the testing methodology (black, grey, or white box), and compliance requirements. Additionally, rush timelines can add premiums of 30-50%.
How much should I budget for a SOC 2 penetration test?
Most SaaS startups spend between $4,000 and $8,000 per annual pentest to satisfy SOC 2 Type II requirements. This range generally covers manual testing of production web applications, APIs, and cloud configurations.
What is the cost of API penetration testing?
API-focused penetration tests in 2026 typically range from $5,000 to $20,000, depending on the number of endpoints and authentication complexity. Bundling API testing with web application assessments often reduces the total cost by 10-20%.
How much does a cloud infrastructure pentest cost?
For a focused cloud security assessment of a single primary account (AWS, GCP, or Azure), expect to pay between $6,000 and $35,000. Costs increase significantly for multi-cloud environments or complex networking setups.
Does white box testing cost more than black box testing?
Yes, white box testing with code review can add 30-70% to the cost compared to a basic grey-box test. This is due to the additional time and specialized skills required to analyze source code and internal architecture.
SecureLeap’s pentest pricing approach for startups
At SecureLeap, we believe penetration testing should be transparent, startup-friendly, and aligned with real business outcomes—not just a checkbox exercise.
Our approach:
- Transparent pricing: Detailed scoping upfront so you know exactly what you’re paying for
- Manual-first testing: Senior-led teams using proven methodologies, not just automated scans
- Compliance alignment: Reports that satisfy SOC 2, ISO 27001, and HIPAA requirements
- Sales enablement: Evidence that helps you close enterprise deals, not just satisfy auditors
T
ypical SecureLeap packages in 2026:
- SaaS Essentials Pentest: 1 web app + 1 API, ideal for early-stage startups with a focused product ($4,000-$8,000 range)
- Growth Bundle: SOC 2 readiness + annual pentest + vCISO advisory, designed for Series A companies pursuing enterprise customers
- Compliance-Ready Package: Pentest + policy documentation + compliance platform implementation (Drata, Vanta, or Secureframe)
We help clients implement and tune their compliance automation platforms so pentest results flow directly into their evidence collection. No reformatting, no duplicate data entry, no compliance theater.
Ready to get a realistic pentest quote for 2026? Book a free consultation to discuss your scope, timeline, and compliance needs. We’ll walk through your specific situation and provide a transparent quote—no pressure, no hidden costs.
Whether you’re preparing for your first SOC 2 audit, responding to an enterprise security questionnaire, or simply want to understand your security posture before your next funding round, SecureLeap can help you budget intelligently and get the security testing evidence you need.