What's Penetration Testing?
Penetration testing, also known as pentesting, is a form of ethical hacking performed by security professionals. Think of it as hiring good hackers to find problems before the bad ones do. These security experts try to break into your systems (with your permission) to spot weak points. It’s like having someone try to pick your locks to prove they’re solid, but for your software.
A penetration test is a simulated attack designed to mimic real-world cyber threats. During the process, penetration testers attempt to exploit vulnerabilities to assess the effectiveness of your security controls. A penetration test simulates cyberattacks to identify and remediate security weaknesses in a startup's systems.
There are different types of penetration testing approaches. Black box penetration testing simulates an attack from an external threat actor with no prior knowledge of your systems, while white box penetration testing provides a complete inside-out view by granting full access to your systems.

Why Pentest is Important for Startups
If you’re running a SaaS company or building tech products, penetration testing is a critical step to safeguard your startup’s future. It helps you identify security weaknesses in your systems before attackers do, protecting your sensitive data and maintaining customer trust.
For startups, early testing is especially important because it uncovers vulnerabilities at a stage when fixes are easier and less costly. Penetration testing simulates real-world cyberattacks, showing how ethical hackers might exploit your startup’s SaaS platforms, applications, and infrastructure. This proactive risk management approach helps you stay ahead of threats, avoid costly data breaches, and meet compliance requirements.
Moreover, a thorough pentest demonstrates your startup’s security maturity to investors and partners, building confidence and giving you a competitive edge. By addressing security flaws early, you protect your digital assets, prevent disruptions to business operations, and establish a strong security posture that supports growth and scalability.
Quick Decision Guide: Do You Need a Pentest for Your Security Posture?
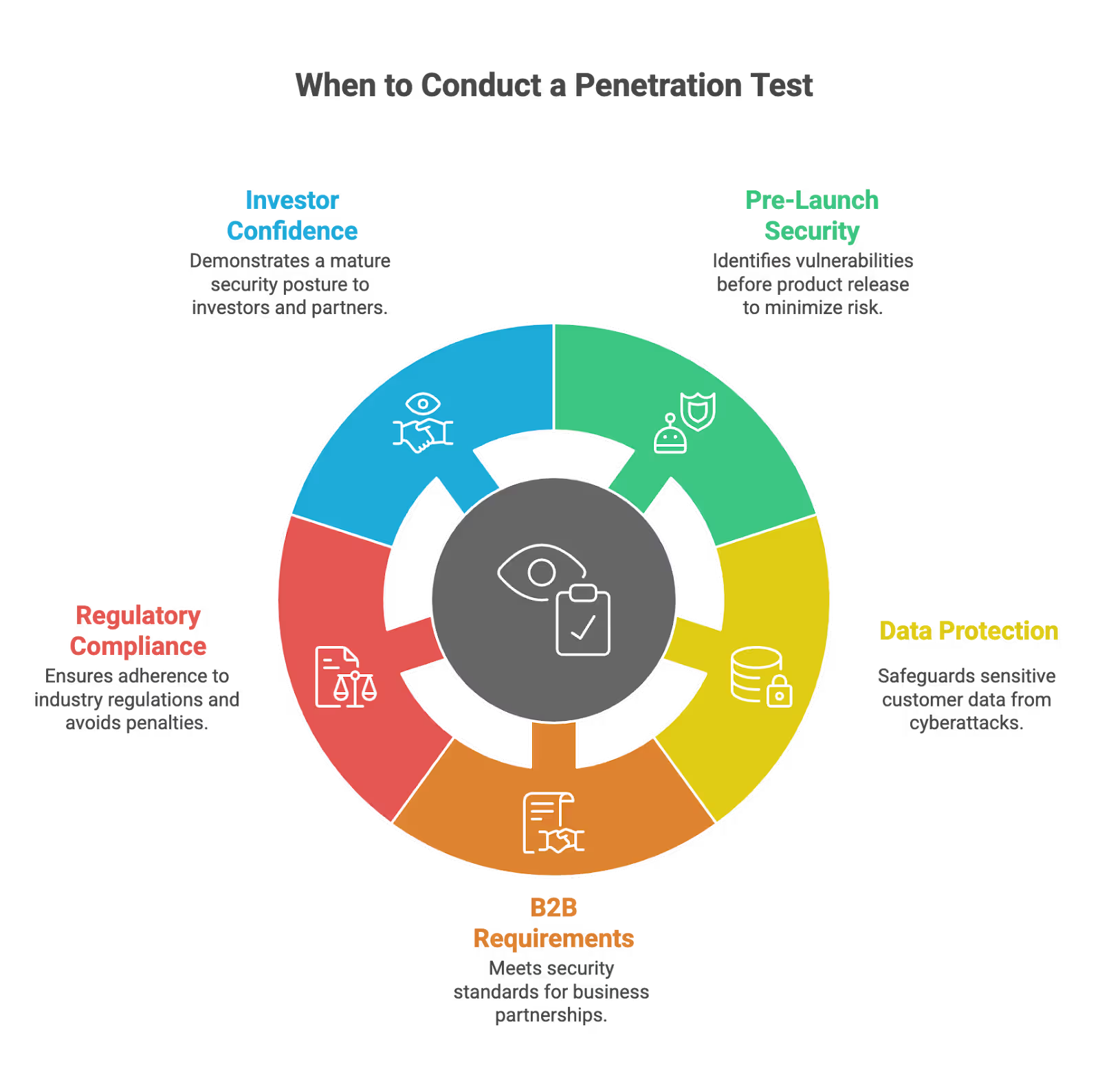
Starting a penetration test (pentest) for your startup is a crucial step in building a strong security foundation. But when exactly should you initiate this process? Here are key indicators that it’s time to schedule a pentest:
- Before launching your product: Conducting a pentest prior to launch helps identify and fix security vulnerabilities early, reducing the risk of breaches once your product is live.
- When handling customer data: If your startup collects, stores, or processes sensitive customer data, pentesting is essential to protect that information from potential cyberattacks.
- If you’re selling to businesses (B2B): Many business clients require proof of security measures, including penetration testing, before engaging in partnerships.
- To meet security standards and regulatory compliance: Regulations such as ISO27001, PCI-DSS, and SOC 2 often mandate regular penetration testing. Engaging in pentesting services helps ensure you meet these requirements and avoid costly penalties.
- When raising funding or working with larger companies: Investors and enterprise partners look for evidence of a mature security posture. A recent pentest report can build confidence and demonstrate your commitment to safeguarding digital assets.
Understanding these triggers will help you proactively plan your pentest and integrate it effectively into your startup’s growth journey. Remember, penetration testing is not just a one-time event but part of ongoing security efforts to identify and remediate vulnerabilities before attackers can exploit them.
Money Talk: What It Costs
Let’s cut to the chase, for most startups, a pentest typically ranges from $4,000 to $12,000.
Targeted tests that focus on specific high-value assets or complex cloud environments can significantly affect the overall cost. Small businesses may have different cost structures and unique cybersecurity needs, making it important to tailor the approach accordingly.
Developing a structured penetration testing plan that prioritizes your high-value assets—your 'crown jewels'—is essential for effective risk management and vendor evaluation. Startups should look for penetration testing providers that offer flexible pricing models to accommodate budget constraints. For those with limited budgets, phased testing or focusing on critical areas first is a common and effective approach.
What changes the price? Several factors influence the cost of a penetration test:
- The size of the target system — testing a single application versus multiple complex systems.
- The complexity of your setup — from a simple website to intricate microservices and operational technology environments.
- The depth of testing required — whether it’s a basic vulnerability scan or a comprehensive deep dive including manual testing and social engineering attempts.
By understanding these variables, startups can better plan their penetration testing budget and select the right level of testing to effectively protect their digital assets.
What Actually Happens During a Test?
A typical penetration testing process for startups unfolds over several weeks, carefully structured to balance thoroughness with minimal disruption to your operations. Here’s a detailed breakdown of what happens during each phase:
Week 1: Planning and Setup
This initial phase is all about preparation. The penetration testing team collaborates closely with your startup to define the scope of the test—deciding which digital assets, applications, and systems will be examined. Clear rules of engagement are established, specifying what is allowed and what is off-limits during testing to ensure safety and compliance. Legal authorizations and necessary agreements, such as nondisclosure agreements (NDAs), are finalized. The team also gathers relevant internal documentation and prepares testing environments, often setting up dedicated test accounts and ensuring logging is enabled to monitor activity during the test.
Weeks 2-3: Active Testing
During this period, penetration testers execute a combination of automated and manual testing techniques. Automated vulnerability scanners help identify known security weaknesses, while manual testing targets complex business logic flaws and attempts to exploit vulnerabilities actively. The testers simulate real-world cyberattacks such as dictionary attacks, SQL injections, and social engineering attempts to evaluate your startup’s security features and overall security posture. Tthree main types of penetration testing to assess your startup's security posture:
- Black Box Testing: In this approach, testers simulate an external attacker with no prior knowledge of your systems. They attempt to breach your defenses using publicly available information and common hacking techniques, mimicking real-world external threats. This method helps identify vulnerabilities that could be exploited by outside attackers.
- White Box Testing: Here, testers have full access to your internal systems, including source code, network configurations, and documentation. This inside-out perspective allows for a thorough and detailed examination of your security controls, uncovering vulnerabilities that might not be visible from the outside.
- Grey Box Testing (also known as Translucent Box Testing): This method blends both black box and white box approaches. Testers have limited knowledge or access, such as user credentials, providing a balanced and realistic assessment.
Grey box testing is often recommended for startups because it combines the perspective of an external attacker with some insider knowledge, making it effective and efficient.
Throughout this phase, testers maintain communication with your team to manage any issues and ensure minimal impact on business operations.
Week 4: Reporting and Reviewing Fixes
After completing the tests, the penetration testing team compiles their findings into a detailed final report. This report lists all identified vulnerabilities, exploited weaknesses, and their potential impact on your computer system and sensitive data. It also prioritizes issues based on severity and provides clear, actionable remediation tasks to help your team fix security vulnerabilities effectively. The testing team typically holds a debrief session to explain the results in plain language, answer questions, and assist with planning remediation efforts. Your startup can then begin addressing the findings, scheduling retests as needed to verify that fixes are successful and that no new vulnerabilities have been introduced.
Understanding this end-to-end process—from planning and execution to remediation and retesting—is crucial for startups to maximize the benefits of penetration testing. Establishing clear communication channels between the penetration testing team and your startup throughout the entire penetration testing process enhances collaboration, ensures transparency, and leads to a stronger security posture that protects your digital assets and customer trust.
What You Get After Testing: The Final Report
The testers will give you:
- List of security holes they found
- Final report: comprehensive documentation summarizing findings, exploited weaknesses, and recommendations for remediation
- How serious each problem is
- Clear steps to fix each issue
- Plain-English explanation of risks
- Follow-up call to explain everything
The final report should include a prioritized list of vulnerabilities and actionable steps for fixing vulnerabilities, helping you establish a strong security culture early and plan ongoing security improvements.
Side note: SecureLeap offers a free retest after the pentest is complete to ensure all issues are properly remediated.
Common Findings and Critical Security Vulnerabilities in Startup Tests
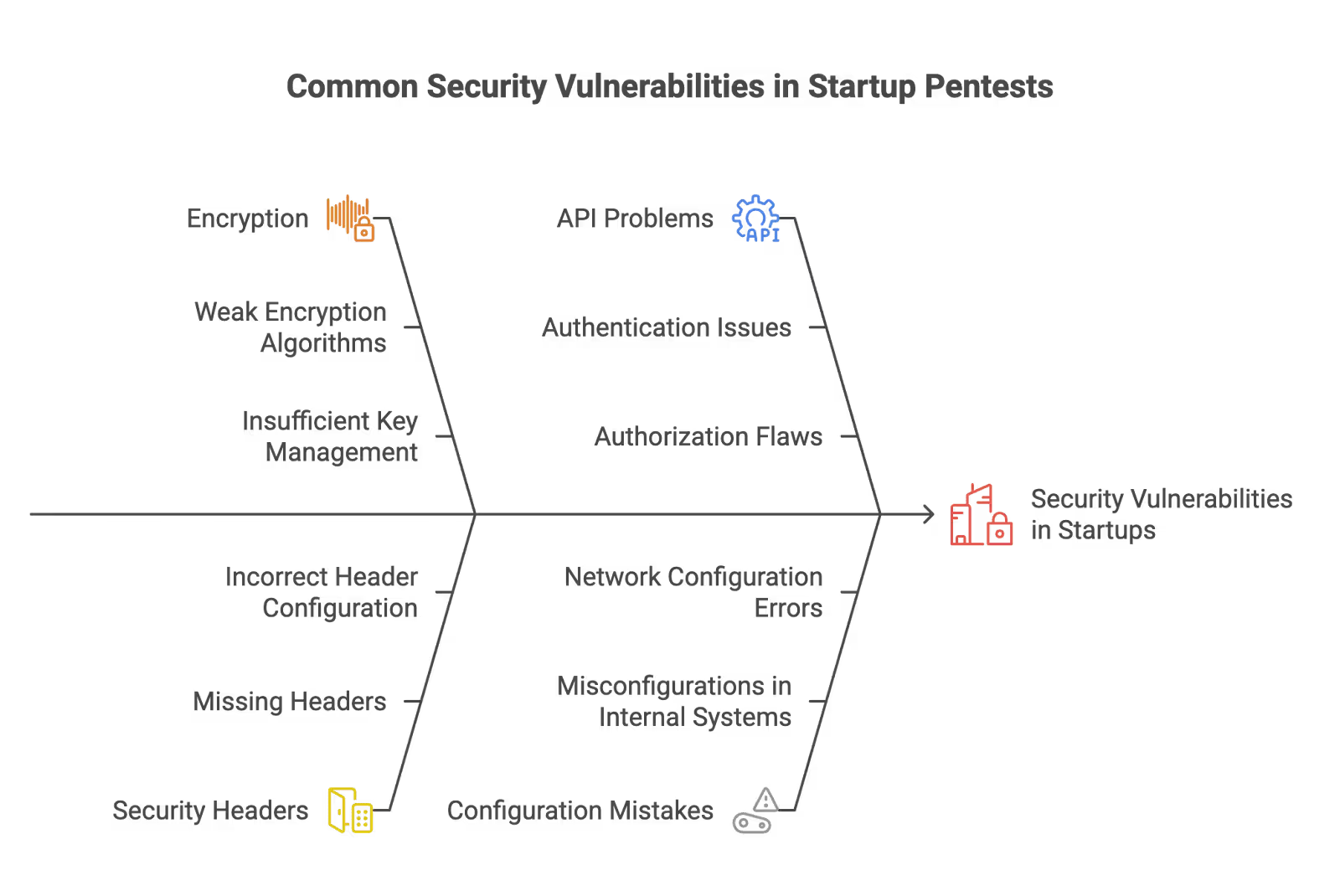
Typical issues we see:
- Weak encryption
- Missing security headers
- API problems
- Data exposure risks
- Configuration mistakes, including misconfigurations in internal systems and network configurations
- Unpatched, publicly documented vulnerabilities identified through security advisories or CVEs
Application penetration tests look for vulnerabilities in apps, web applications, and APIs. Network penetration tests can target both external and internal systems, simulating attacks from external hackers or malicious insiders.
Your Pentest Prep Checklist
Before you start:
- Identify and prioritize critical data and high-value assets ('crown jewels') for testing
- Gather internal documentation to support the testing process
- Clearly define the scope of the penetration test, specifying which systems and applications will be tested
- Ensure legal authorization and necessary agreements (including NDAs) are in place before testing
- List what needs testing
- Gather tech documentation
- Pick a testing window
- Alert your team
- Budget for fixes
- Clear your calendar for review
Best Practices for Penetration Testing for startups
To get the most value from penetration testing, startups should stick to a few key best practices. Start by defining a clear scope and objectives for your test—know what digital assets, sensitive data, and financial data are most important to protect. Choose a reputable penetration testing team with experience in startup environments, and make sure all testing happens in a controlled, safe environment.
Focus your efforts on critical systems and assets, and schedule regular tests—at least once a year—to catch new security vulnerabilities as your business evolves. Grey box penetration testing is often the sweet spot for startups, combining the realism of real world attacks with enough insider knowledge to provide actionable insights into your security controls. By following these steps, you’ll maintain a strong security posture, protect what matters most, and stay ahead of compliance requirements.
Frequently Asked Questions About Pentest for Startups
What is penetration testing / pen testing?
Penetration testing, or pentesting, is a form of ethical hacking where security professionals simulate a cyberattack on your systems. The goal is to identify and fix security vulnerabilities and weak points before malicious hackers can exploit them.
How much does a penetration test cost for a startup?
For most startups, a penetration test typically ranges from $4,000 to $12,000. Factors that influence the price include the size of the target system, the complexity of the setup, and the depth of testing required.
When should a startup perform a penetration test?
Startups should schedule a pentest before launching a product, when handling sensitive customer data, or to meet compliance standards like SOC 2 and HIPAA. It is also essential when B2B clients require proof of security or when raising funding from investors.
What are the different types of penetration testing?
The three main types are Black Box (external attack simulation), White Box (full internal access), and Grey Box (mixed access) testing. Grey Box testing is often recommended for startups as it balances efficiency with a realistic external attack perspective.
What happens during the penetration testing process?
The process spans several weeks, starting with planning and scoping, followed by active automated and manual testing to find flaws. Finally, the team provides a detailed report with prioritized vulnerabilities and actionable steps for remediation.
Is penetration testing mandatory for SOC 2?
While penetration testing is not explicitly mandatory for SOC 2 or ISO 27001 compliance, it is highly recommended and increasingly expected by customers and partners. Conducting these tests demonstrates effective security controls, strengthens your security posture, and provides necessary proof to auditors and customers of your commitment to security.
Making It Work for Your Budget
If money’s tight:
- Start with critical systems only
- Look for penetration testing providers that offer flexible pricing models to accommodate your budget constraints
- Prioritize your high-value assets when budgeting for penetration testing to ensure critical vulnerabilities are addressed first
- Consider phased testing or focusing on critical areas first as a strategy if your budget is limited
- Get a basic test now, deeper dive later
- Fix the big problems first
- Plan for yearly tests in your budget
How SecureLeap Can Help
Looking for a pentest partner who gets startups? SecureLeap brings 20+ years of startup security experience to your team. Here’s what makes us different:
- Startup-focused testing: We understand tight budgets and fast development cycles
- Penetration testing services delivered by security professionals: Our team consists of experienced security professionals who specialize in simulating real-world cyber threats to identify vulnerabilities.
- Proven expertise and strong reputation: SecureLeap is trusted by high-growth startups for our proven expertise and strong industry reputation.
- Recognized certifications: Our team holds certifications such as OSCP, OSWE, GPEN, and CREST, ensuring high standards in every engagement.
- Industry and asset-specific experience: We have extensive experience with startups across SaaS, fintech, healthtech, and B2B, and understand the unique assets and risks in these sectors.
- Clear communication: No security jargon - just plain talk about what matters
- Fixed pricing: No surprise costs or hidden fees
- Quick turnaround: Results in 2-3 weeks, not months
- Practical fixes: Real solutions that work for your team size and stack