Introduction to Penetration Testing
In today’s fast-paced digital landscape, organizations face constant threats to their sensitive data and systems. Penetration testing—often called pen testing—is a proactive security assessment that simulates real-world attacks on your computer system, network, or web applications. The goal is to identify weaknesses and security vulnerabilities before malicious actors can exploit them. By conducting a thorough risk assessment, penetration testing helps organizations uncover potential entry points that could allow unauthorized users to gain access, ensuring your defenses are robust and your data remains protected.
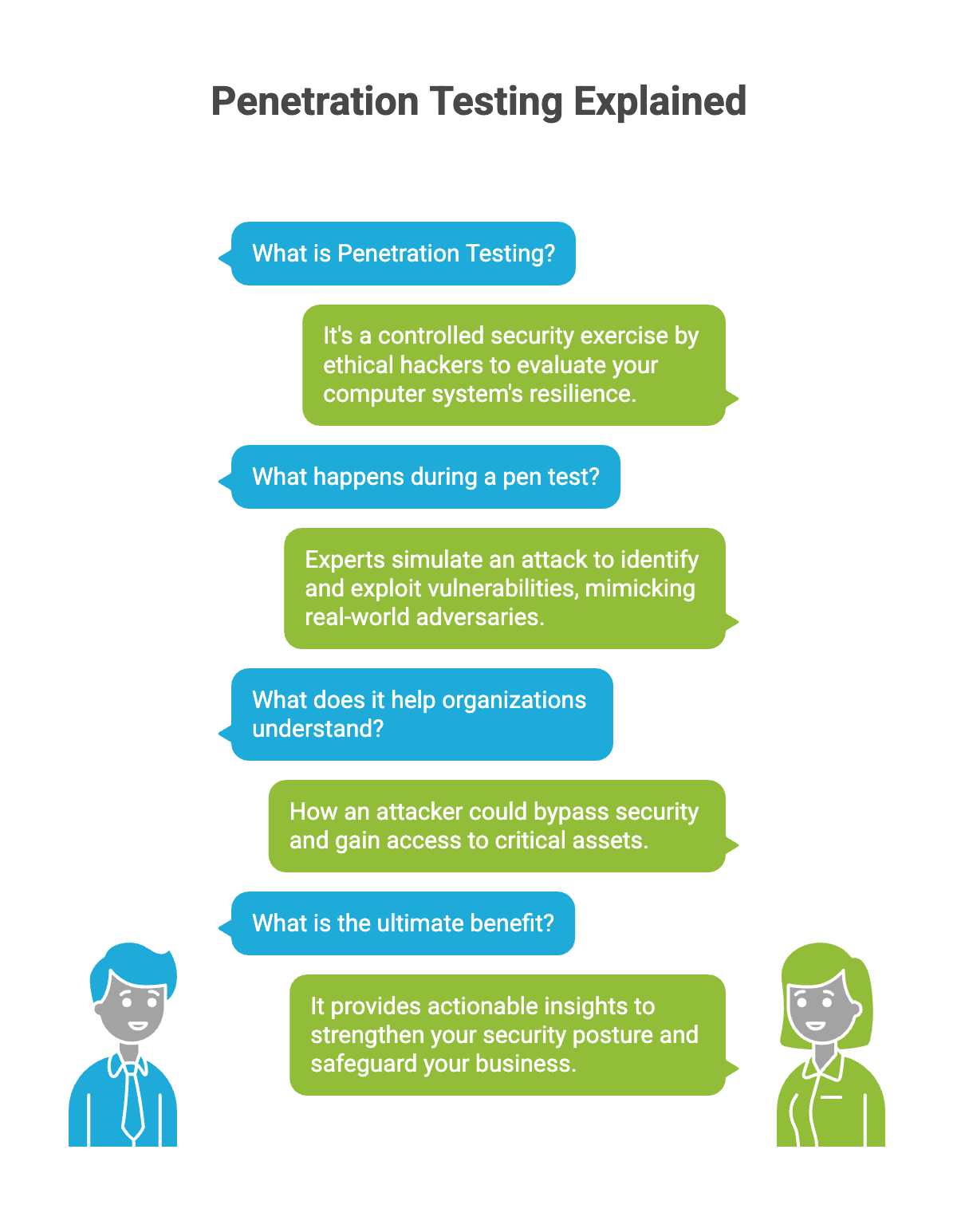
What is Penetration Testing?
Penetration testing is a controlled security exercise performed by ethical hackers or security professionals to evaluate the resilience of your computer system. During a pen test, experts simulate an attack to identify and exploit vulnerabilities, mimicking the tactics of real-world adversaries. This simulated attack helps organizations understand how an attacker could bypass security measures and gain access to critical assets. Ultimately, penetration testing provides actionable insights to strengthen your security posture and safeguard your business from evolving threats.
Benefits of Penetration Testing
Penetration testing offers a wide range of benefits for organizations aiming to protect their assets and meet compliance requirements. By identifying vulnerabilities such as insecure direct object references, cross site scripting, and business logic flaws, pen testing helps you address weaknesses before they can be exploited. It also evaluates the effectiveness of your security controls and security practices, ensuring they align with industry standards and regulatory frameworks like PCI DSS. Beyond technical vulnerabilities, penetration testing uncovers business logic issues that automated tools might miss, providing a comprehensive view of your risk landscape and supporting continuous improvement of your security program.
1. Before The Penetration Test - A Whole Lot of Legwork
Getting Your ducks in a row: Clearly work out why you're even bothering with a penetration test in the first place.
- Meet those compliance requirements that are always looming over you
- Figure out where your security gaps are
- Allay any specific fears you might have
Getting Real Clear on What You Want to Test: Decide which systems, applications or networks you're going to test and what's absolutely off limits. Be super clear about what system you're looking at, so you can keep the assessment focused and actually get something out of it.
Gathering all the Background: Get hold of all the details about your organisation's:
- Application frameworks – if that's even a thing
- URLs - assuming it's not all just a load of internal IP addresses
- IPs - and don't forget the ones that are already exposed to the public
- User roles - who can even get into the system
- Tech stack - all the different bits of software you're using
- Environment setups - is it all just a load of different servers?
- API endpoints - just to be sure
- Open ports - because you don't want to be that person who gets caught out
Making sure You’re Ready to Rock and Roll
- Setting up a safe testing environment: Set up a testing environment that's a dead ringer for the ones in production - but ideally with none of the real-world consequences. Write it all down and make sure everyone knows which environment is the one they're supposed to be using. If you can, set it up so that you can test without messing up the live operations.
- Sorting out your communication channels: Get all the key players and communication channels sorted out so you know who to talk to, and when.
- Talking about timelines and what to expect: Set some realistic goals for yourself - and work out what success looks like.
- Who's on what: Make sure everyone knows what they're responsible for, and what's expected of them.
- Getting the higher-ups on board: You want someone at the top to be on board, so they can sort out any issues and make sure the whole thing stays on track.
Getting the Right Go-Ahead
- Getting everyone to sign off on it: Get everyone who's got a vested interest to agree that this is a good idea, and its all been properly thought through.
- Writing it all down: Record every single stage of this process, and make sure you've got all the details sorted out.
Penetration Testing Type
- Black-box penetration test: In this approach, the penetration testing team has no prior knowledge of the target system. They simulate an external attacker’s perspective, attempting to find vulnerabilities without any inside information, making it a true test of the system’s external defenses.
- Gray-box penetration test: This method provides the testers with limited knowledge about the target system, such as user credentials or network architecture. Gray-box testing combines the benefits of both black-box and white-box testing, offering a more focused and efficient assessment.
- White-box penetration test: Also known as clear-box testing, this approach gives testers full access to system information, including source code, architecture diagrams, and credentials. It allows for an in-depth examination of the system’s internal workings to uncover hidden vulnerabilities that might be missed in other testing types.
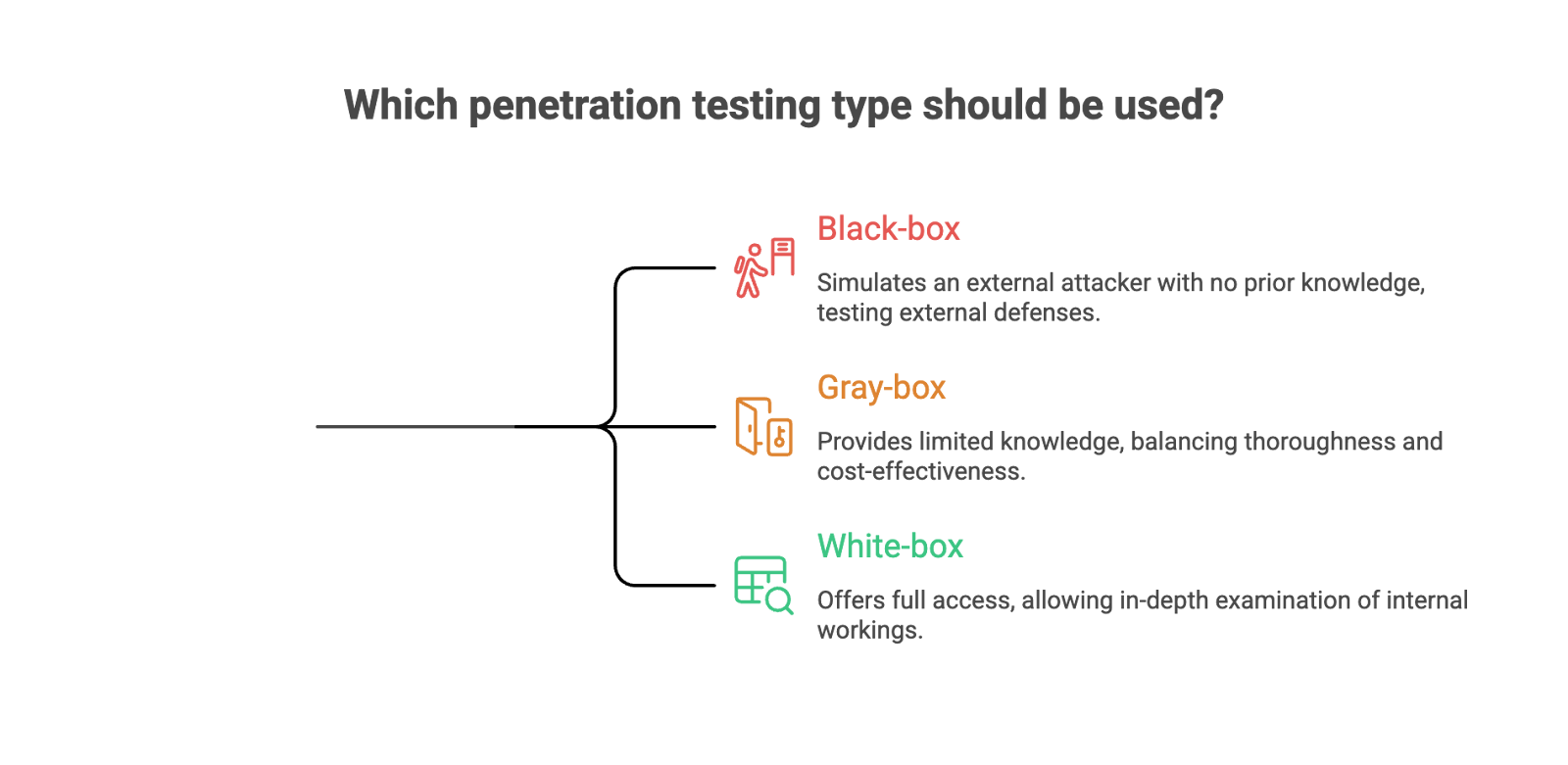
For startups, gray-box testing is often the best choice as it balances thoroughness with cost-effectiveness, helping identify critical vulnerabilities without requiring extensive resources.
Choosing a Penetration Testing Vendor
Selecting the right penetration testing vendor is a critical step in your security journey. Look for a provider with a team of certified professionals experienced in both manual testing and automated scanning across diverse environments, including web applications, cloud environments, and network pentesting.
Defining Test Objectives and Scope
A successful penetration testing engagement starts with clearly defined objectives and scope. Establish what you want to achieve—such as identifying weaknesses, evaluating security controls, or meeting compliance requirements—and determine which systems, networks, and applications will be tested. Outline the testing approach, timelines, and any specific compliance or industry standards that must be met. Ensure all necessary permissions and non-disclosure agreements are in place to protect sensitive data and maintain legal compliance. By setting clear goals and boundaries, you maximize the value of your penetration test and ensure actionable, relevant results.

2. During the Penetration Test: Execution and Monitoring
- Get the right teams at the table: Make sure the people who matter most - the testers & security teams in this case - have a seat at the table and are actively contributing to the test process, not just sitting on the sidelines.
- Find your traffic breaking point: Keep a close eye on traffic levels to avoid overwhelming the system and causing problems for your users.
- Keep things from falling apart: Make sure the testing environment holds up under the test load - you don't want things to start falling apart mid-test.
- Communicate constantly: Keep the testing team & internal stakeholders in the loop at all times, so any issues can get addressed the minute they come up. Designate a channel for flagging critical issues that need a super-fast response.
- We've got your back during the test: Our team will be on call the whole time, helping to figure out the tricky problems & keeping your team in the know every step of the way.
After the Penetration Test: Post-Assessment and Sensitive Data Reporting
Review and analyze test results: Conduct a thorough analysis of the findings from the test.
Assign responsibility for findings: Identify who within your organization is responsible for addressing each vulnerability.
Prioritize vulnerabilities: Classify vulnerabilities based on their severity and the potential impact on your organization.
Supporting remediation efforts: Establish an escalation plan for high-risk findings and ensure relevant development teams are aware of high-risk issues as they are reported.
Confirm documents received after engagement:
- Executive summary
- Technical summary
- Appendices
- Scope of the engagement
- Methodology and approach
- Testing team, including contact information for the assigned team
- Letter of attestation
- Final report (comprehensive documentation of findings and outcomes)
Addressing the identified vulnerabilities is essential for maintaining data security and ensuring your organization remains compliant with relevant regulations.
Schedule a retest (if necessary): Plan for a follow-up test to ensure that vulnerabilities have been properly addressed.
Important Note: Don’t forget to remove permissions granted to penetration testers once the testing engagement is complete to maintain your system’s security integrity.
FAQ for Pentest checklist
What is a penetration test?
A penetration test is a simulated security attack where ethical hackers identify vulnerabilities in your systems. It helps organizations find and fix weaknesses before malicious actors can exploit them.
What is the difference between black-box and white-box testing?
Black-box testing simulates an external attack with no prior system knowledge. White-box testing provides testers with full access to source code and internal architecture for an in-depth review.
Why is gray-box testing recommended for startups?
Gray-box testing balances thoroughness and cost by providing testers with limited information like user credentials. This approach helps identify critical vulnerabilities efficiently without requiring excessive resources.
What information is needed before starting a penetration test?
Organizations should gather technical details including application frameworks, URLs, IP addresses, and API endpoints. It is also important to define user roles and specify the technology stack being used.
Ready to Get Started with a Penetration Testing Vendor?
Looking for expert penetration testing tailored specifically for startups?
At SecureLeap, we specialize in delivering comprehensive penetration testing services designed to meet the unique security challenges of high-growth startups. Our team of security experts goes beyond standard scans to uncover complex business logic vulnerabilities and potential risks in your environment.
We collaborate closely with you to develop a customized testing strategy that aligns with your startup’s technology stack and business goals, helping you achieve compliance and strengthen your security posture efficiently.