Penetration testing is a sanctioned simulated attack on a computer system carried out by security teams or penetration testers to assess the organization's security posture. Essentially, it is a systematic examination of an organization’s IT infrastructure, network, or web application to identify potential vulnerabilities that could be exploited by hackers.
In this article, we explore the five key phases of penetration testing: Reconnaissance, Scanning, Vulnerability Assessment, Exploitation, and Reporting.
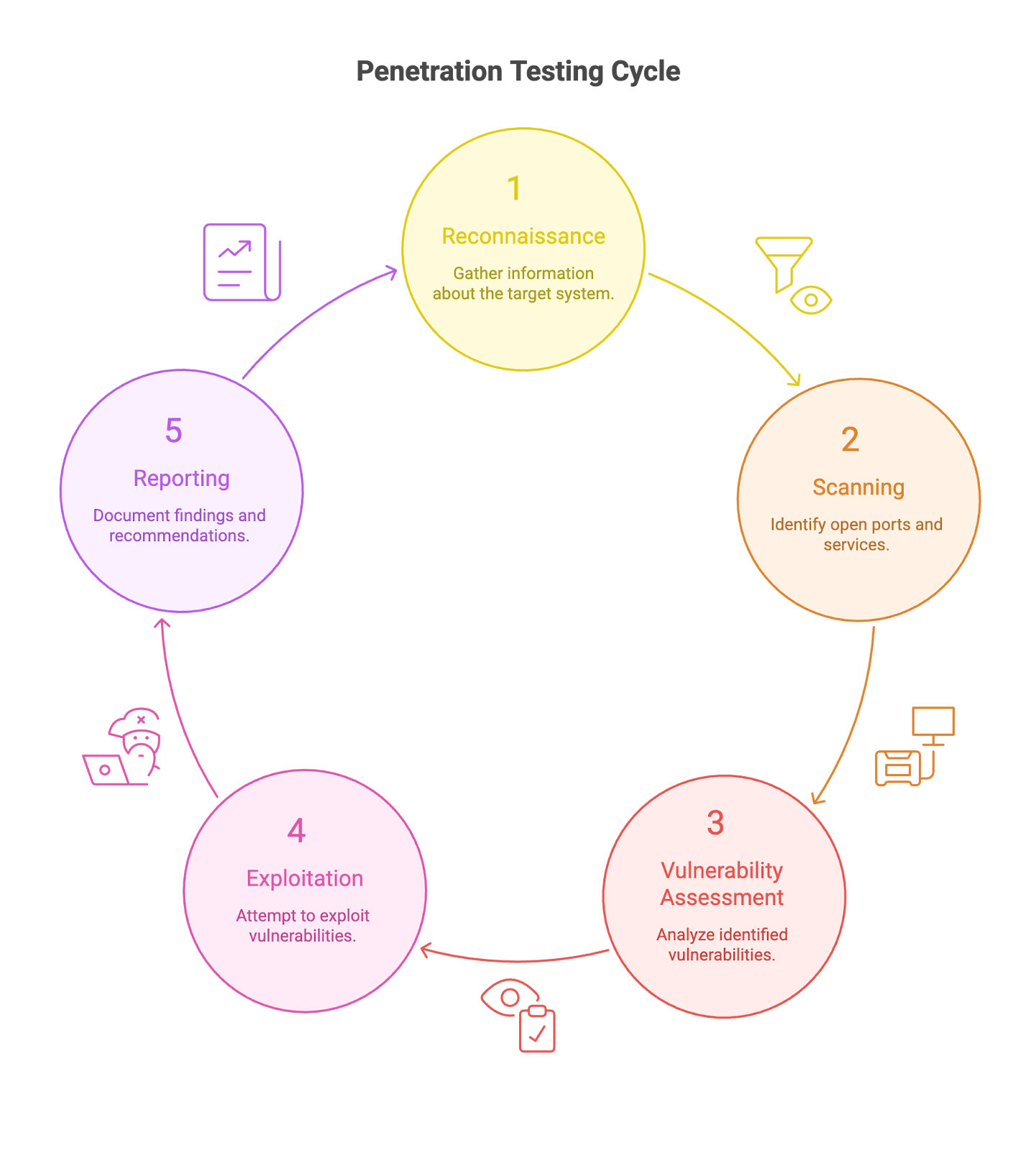
The structured methodology of penetration testing remains critical for identifying and remediating security risks in 2026.
Reconnaissance
The initial phase, Reconnaissance, lays the groundwork for the entire penetration testing process. During this stage, the tester embarks on a comprehensive information-gathering mission concerning the target system. Penetration testers aim to collect as much relevant data as possible about the target system, network, or application. This information can include details such as IP addresses, domain information, network services, mail servers, network architecture, user accounts, and other pertinent data.
Intelligence Gathering uses both Passive Reconnaissance and Active Reconnaissance to map the target's attack surface. Passive reconnaissance gathers publicly available information without interacting directly with the target, while active reconnaissance involves directly probing the system to identify live hosts and potential entry points. The data gathered during this phase is critical for understanding the target's environment and is used to inform later stages of the penetration test.
This proactive intelligence gathering offers invaluable insights, enabling the creation of a detailed blueprint of the target environment. Equipped with this knowledge, the tester can develop a well-informed testing strategy to effectively identify vulnerabilities, setting the foundation for the following phases of the penetration testing process.
Scanning
Next comes the scanning stage, which is one of the critical scanning phases in the 5 stages pentest process. This phase involves an in-depth technical review of the target system, where testers use automated scans to quickly identify known vulnerabilities. Attackers and defenders often use the same tools—such as vulnerability scanners, network mappers, and other automated assessment tools—during this phase to simulate real-world attack scenarios.
The scanning phase involves using tools to identify open ports and check network traffic on the target system. Techniques in scanning include port scanning, service fingerprinting, and vulnerability scanning, all aimed at collecting relevant data to uncover potential security flaws. Vulnerability databases like CVE and NVD are referenced to detect and prioritize known vulnerabilities.
Scanning allows testers to observe how the target application responds under various conditions and to pinpoint potential vulnerabilities that could be exploited. It charts the system’s digital landscape, helping the tester identify possible entry points an attacker might leverage.Validation of vulnerabilities is crucial in this phase, involving both automated scanners and manual reviews to confirm findings and eliminate false positives, thereby improving the reliability of the security assessment.
Vulnerability Assessment
Once the target system has been thoroughly scanned, the process proceeds to the Vulnerability Assessment stage. In this phase, the data gathered during earlier reconnaissance and scanning is used to identify and evaluate potential security weaknesses. Vulnerability assessment is a critical part of security assessments, helping organizations understand their risk exposure by systematically analyzing the system for vulnerabilities.
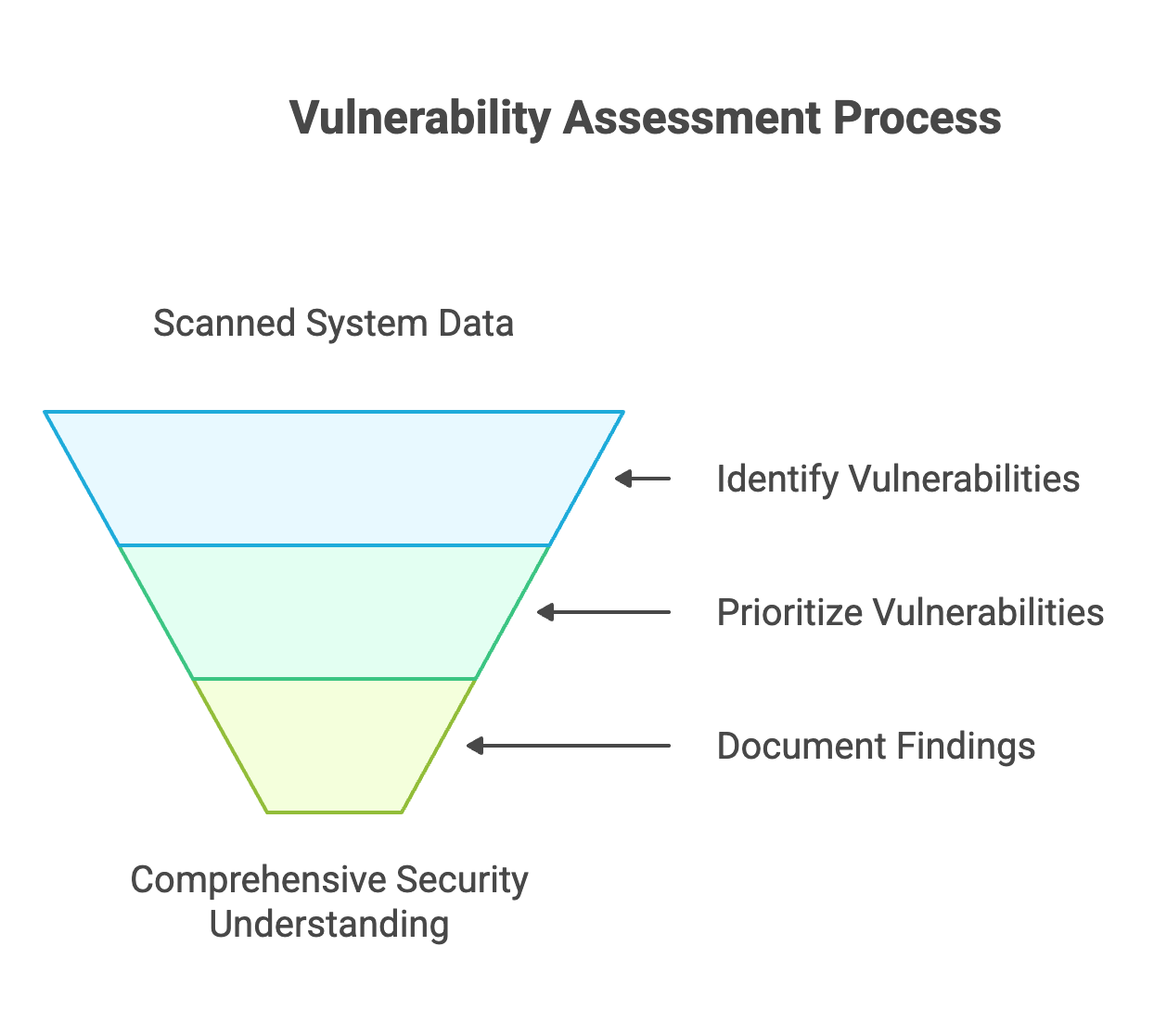
Using a combination of automated tools and manual methodologies, the tester scrutinizes the security of the systems, with a focus on identifying and prioritizing critical vulnerabilities that could pose significant risks. Findings are documented with detailed vulnerability descriptions, often within customizable and exportable report templates to guide remediation efforts. Prioritization of these findings is done using databases such as the Common Vulnerabilities and Exposures (CVE) list and CVSS scoring, ensuring that the most severe issues are addressed first.
This meticulous assessment ensures a complete understanding of the system’s security posture, flagging potential vulnerabilities that could be exploited by cybercriminals.
Exploitation
Once the Vulnerability Assessment is complete, the next stage is Exploitation. In this critical phase, the tester actively exploits vulnerabilities to gain unauthorized access to the target system. The exploitation phase may involve attempts to gain remote access, access sensitive data, and maintain access for deeper testing. The aim isn’t to cause damage but to ascertain the depth of the vulnerability and assess the potential damage it could cause.
During exploitation, testers exploit vulnerabilities to gain access, which might include data breaches, service disruption, or unauthorized access to sensitive information. Maintaining access is also evaluated, as attackers may try to stay connected to the compromised system and escalate privileges, similar to advanced persistent threats. Deeper testing may be performed to assess the full impact of exploited vulnerabilities. This stage needs to be carefully controlled and monitored to ensure that the system isn’t accidentally damaged during the process. Post-exploitation activities determine if a vulnerability can be used to achieve a persistent presence in the system. It’s a delicate balancing act between pushing the boundaries and maintaining the integrity of the system.
Reporting
The final stage of the pen testing process is Reporting and that's where the tester puts together a comprehensive report that documents everything they've found. For a test to be effective, the Reporting and remediation have got to go hand in hand - it's not just about highlighting vulnerabilities, but also actually doing something about them. At this point in the security testing process the report is usually a pretty detailed breakdown of all the vulnerabilities that turned up, how you managed to get to them, and some real practical advice on how to put things right.
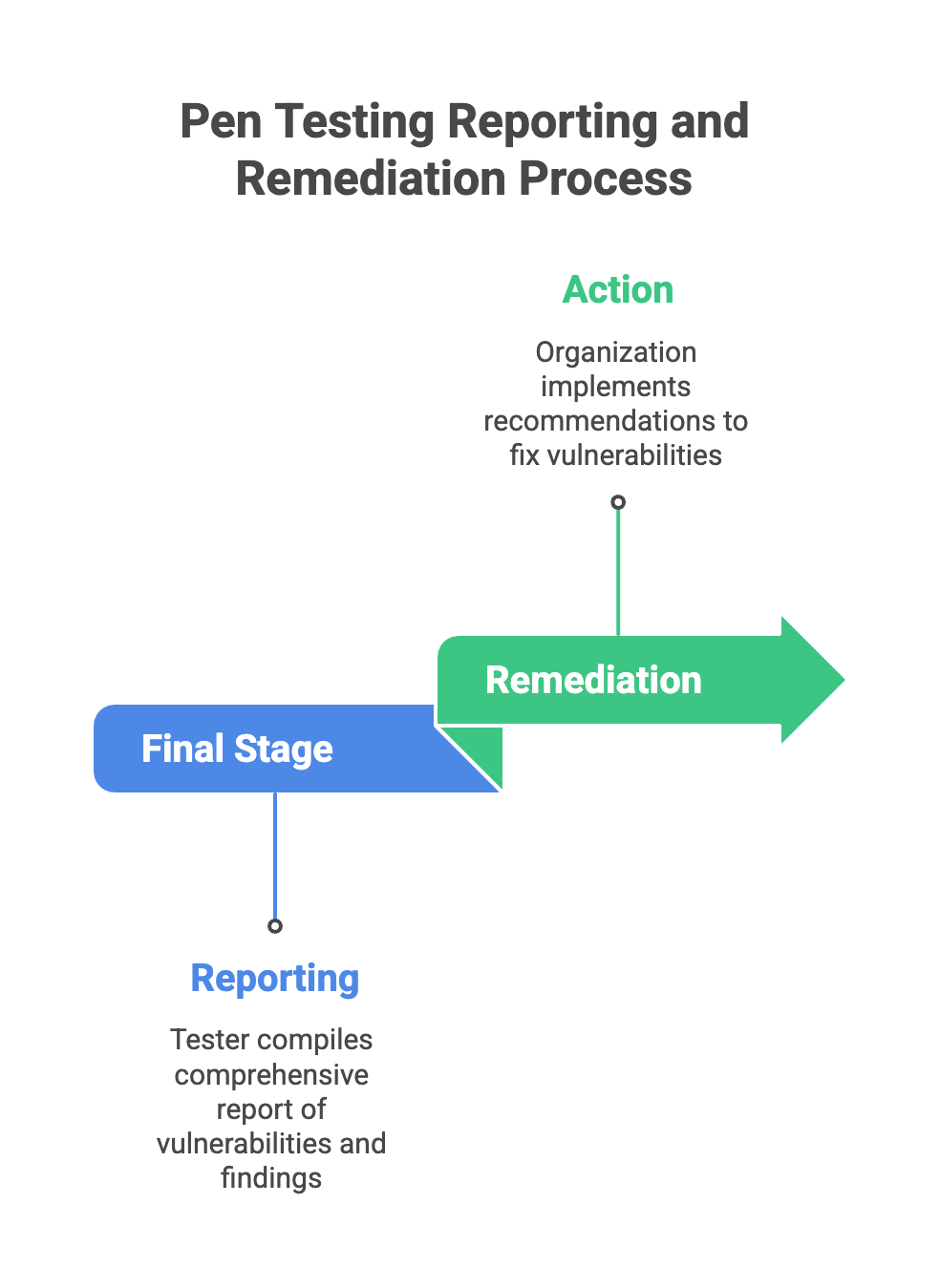
The way the report is put together is pretty important, so it usually has an executive summary to get the business folks on board, the nitty gritty technical details for the IT team to peruse, and some practical advice for the devs on how to make the necessary changes. It's not just a list of things that went wrong - its actually got some substance to it, including things like software updates, reconfiguring things, and revised security policies.
By the time you're done, you should have taken some pretty esoteric technical findings and turned them into real business insights that an actual business can use, turning the whole shebang into a roadmap that gets the organisation pointed in the right direction - a more secure IT setup is what you're aiming for.
Choose SecureLeap for Expert Penetration Testing
SecureLeap delivers top-notch penetration testing tailored for startups and SMBs aiming for SOC 2, ISO 27001, and HIPAA compliance. Our skilled team uncovers security gaps and protects your sensitive data with precise, actionable reports.
Whether you need to meet customer demands or boost your cybersecurity, SecureLeap is your trusted partner. Contact us today for a free consultation and secure your business’s future.
FAQ for 5 Stages of Pentest
What are the 5 stages of a penetration test?
The five distinct phases are Reconnaissance, Scanning, Vulnerability Assessment, Exploitation, and Reporting. This structured methodology helps security teams systematically identify and fix security weaknesses in IT infrastructure.
What happens during the reconnaissance phase?
Testers gather comprehensive data about the target system, such as IP addresses, network architecture, and domain information. This stage involves both passive and active intelligence gathering to map the attack surface.
How does the scanning phase differ from vulnerability assessment?
Scanning uses automated tools to identify open ports, live hosts, and service fingerprints. Vulnerability assessment analyzes this data to prioritize risks based on databases like CVE and CVSS scoring.
What is the purpose of the exploitation phase?
Security professionals actively exploit identified vulnerabilities to gain unauthorized access and assess potential damage. This controlled simulation determines if a weakness can lead to data breaches or persistent threats.
Why is the reporting phase important in pentesting?
The reporting phase documents all findings and provides a detailed roadmap for remediation. It translates technical vulnerabilities into actionable business insights to help organizations achieve compliance and better security.