Grey box Pentest: This is the middle ground between whitebox and blackbox. The tester is given limited knowledge: usually a set of low-level user credentials and a high-level overview of the system architecture. In this context, gray box testers operate with partial access, simulating a semi-insider threat.
In a Greybox test, the “attacker” doesn’t waste time guessing usernames or trying to find your login page. They start from the perspective of a registered user or a partner, allowing them to focus their energy on the “meat” of your application’s security.
The level of administrative control granted to the tester—ranging from basic user to full admin—directly impacts the scope of the assessment and the types of vulnerabilities that can be uncovered. Authenticated testing is performed, enabling deeper analysis of access control, session management, and business logic.
Gray box pen testing, gray box penetration testing, and gray box pentest all refer to this hybrid approach, which combines elements of both black box and white box testing. The pen tester aims to find vulnerabilities by exploring various attack vectors and attempting to exploit vulnerabilities as a real-world attacker would. While gray box testers have more insight than a black box tester, they do not have full visibility into the inner workings of the application, which helps simulate realistic attack scenarios while still uncovering significant security flaws.

Types of Penetration Testing
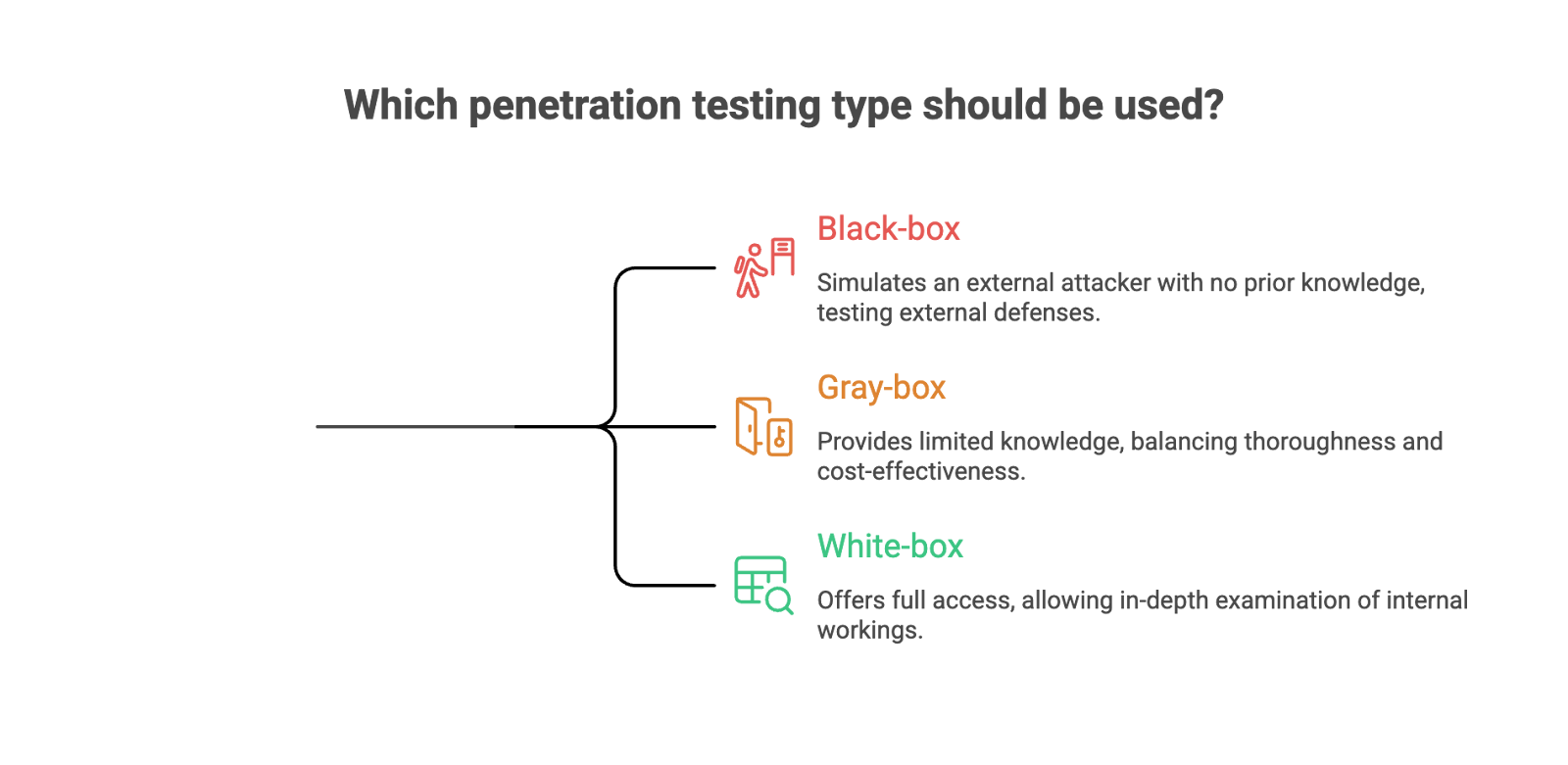
Penetration testing is a cornerstone of modern cybersecurity, helping organizations uncover security vulnerabilities before cyber criminals can exploit them. There are three main types of penetration testing—black box testing, gray box testing, and white box testing—each defined by the amount of prior knowledge the penetration tester has about the target system.
Black box testing simulates an external attacker with no insider knowledge. The tester approaches the target system as an outsider, with no access to internal details, source code, or user credentials. This method closely mirrors real world attacks from cyber threats outside your organization, focusing on what an attacker could discover and exploit from scratch. While black box penetration testing is valuable for identifying vulnerabilities in your external infrastructure, it may miss deeper issues hidden behind authentication or privilege boundaries.
White box testing (sometimes called white box penetration testing) gives the tester full knowledge of the system, including source code, architecture diagrams, and security controls. This approach allows for the most thorough assessment, as the tester can analyze data flows, input fields, and internal workings in detail. White box testing is ideal for uncovering complex logic flaws and privilege escalation risks, but it can be time consuming and resource-intensive—often more than what a fast-moving startup needs.
Gray box testing (or grey box penetration testing) strikes a balance between the two. Here, the tester is provided with partial knowledge—such as standard user permissions, limited insider knowledge, or basic documentation. This approach simulates attacks from someone with initial access, like a compromised user account or a third party partner. Gray box testing is highly effective for identifying privilege escalation paths, sensitive data exposure, and insider threat scenarios, making it a popular choice for startups seeking actionable insights without the overhead of a full white box assessment.
By understanding the differences between black box, gray box, and white box penetration testing, organizations can choose the right approach to match their security posture, compliance requirements, and business needs.
Why Gray Box Penetration Testing is the Most Recommended Method for Startups
1. The Best "Bang for Your Buck" (ROI)
Startups operate on lean budgets. A Whitebox audit can cost a fortune because of the manual hours required to read every line of code. Conversely, a Blackbox test might be cheaper but often returns “surface-level” results that your team could have found with a basic automated scanner.
Greybox testing provides the highest ROI. By giving the tester credentials, you ensure they spend 90% of their time testing your actual business logic and sensitive data controls rather than 50% of their time just trying to bypass a login screen. To maximize efficiency, testers leverage common resources such as industry-standard tools and frameworks like OWASP during gray box pentests.
2. Speed and Agility
Startups move through development cycles in weeks, not years. Greybox testing is significantly faster than a full code review. Because the tester understands the basic “pipes” of your system, they can navigate to high-risk areas—like payment processing or administrative panels—immediately. Well-designed test cases further enable efficient and thorough coverage of these critical components, ensuring that key vulnerabilities are assessed quickly and systematically. This allows you to get a comprehensive report back in time for your next sprint or board meeting.

3. Simulating the Most Realistic Threats with Partial Knowledge
Most modern breaches aren’t the result of “Mission Impossible” style hacking. They happen because of broken access controls (where User A can see User B’s data) or privilege escalation (where a regular user becomes an admin), as well as privilege misuse during business logic testing—such as improper permission handling or unauthorized access in workflows like checkout or profile updates.
A Blackbox test might never see these flaws because the tester never makes it past the signup page. A Greybox test assumes a “breach” has already occurred or that the threat is a malicious user, including the risk of insider threats—internal actors exploiting vulnerabilities or misusing access. This mimics the real-world scenarios that actually take down startups.
4. Overcoming the "Enterprise Gatekeeper"
If you are a B2B startup trying to close a deal with a large enterprise, their security team will put you through a grueling procurement process. They want to see a penetration test report that goes deeper than just an automated scan of your homepage.
A Greybox report demonstrates to enterprise clients that you have tested your internal permissions, your API endpoints, and your data isolation. It also shows that your critical assets—such as key components, trust boundaries, and entry points—have been thoroughly tested for vulnerabilities. This provides the level of assurance needed to sign those high-value contracts.
The Greybox Process: What to Expect in Identifying Security Vulnerabilities
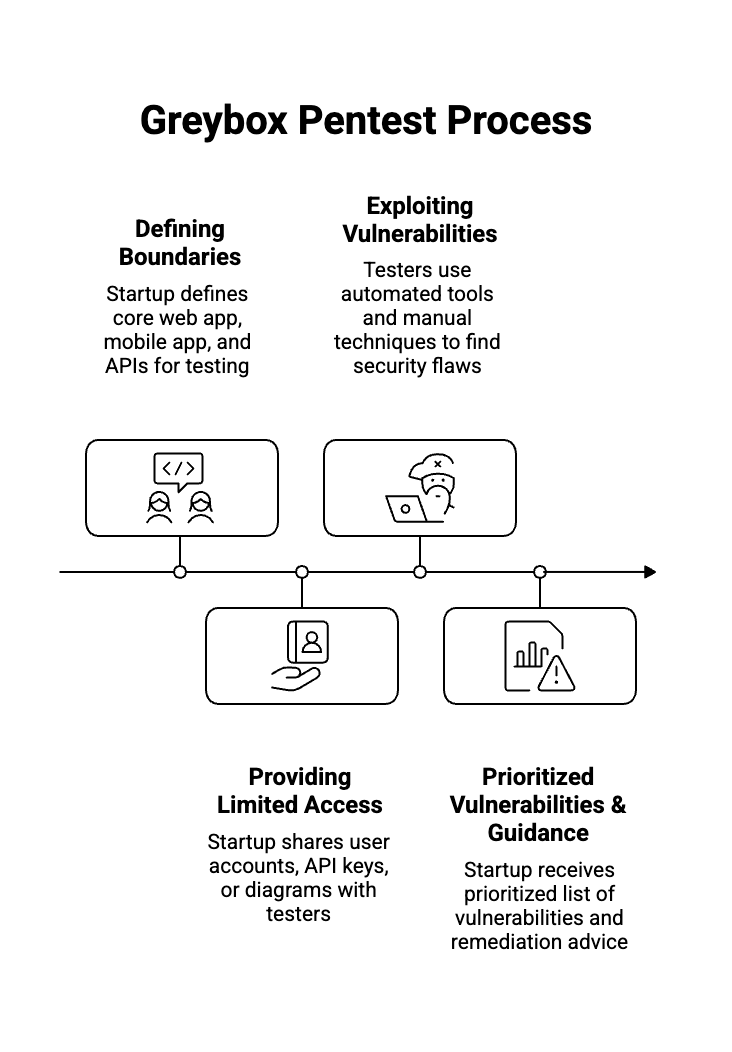
If you decide to move forward with a Greybox pentest, the process generally follows four distinct phases:
- Scoping: You define the boundaries. For a startup, this usually means your core web application, your mobile app, and the APIs that connect them. The scope may also include integrations with third party services, which can impact the complexity and duration of the assessment.
- Information Sharing: You provide the testers with “limited” access—standard user accounts, an API key, or perhaps a basic architectural diagram. Gray box testing also supports compliance with standards like PCI DSS by providing evidence that your systems meet required security controls.
- Active Testing: The testers use a mix of automated tools and manual exploitation. Security testing at this stage is crucial for identifying vulnerabilities that could impact your business. They will try to “break out” of their user role, access other users’ data, or manipulate the application’s logic (e.g., changing the price of an item in a checkout cart), and will specifically test user input for validation and security flaws.
- The Report: You receive a prioritized list of vulnerabilities. For a startup, the most valuable part of this is the remediation guidance, which tells your small dev team exactly how to fix the holes.
Choosing the Right Path
While every organization’s needs are different, the efficiency and depth of Greybox testing make it the industry standard for a reason. Pen tests are a crucial part of a proactive security strategy, helping organizations assess vulnerabilities through different testing methodologies, with gray box penetration testing offering a balanced and effective approach. It respects the limited resources of a startup while providing the rigorous security validation required in today’s market.
FAQ for Grey Box Pentest
What is gray box penetration testing?
It is a hybrid security assessment where the tester has partial knowledge of the target system, such as user credentials or architectural diagrams. This methodology simulates realistic attacks from semi-insider threats or compromised user accounts.
How does gray box testing differ from black box testing?
Black box testing involves an attacker with zero prior knowledge, while gray box testing provides limited access like standard user permissions. Gray box testing is more efficient because testers focus on internal business logic rather than bypassing initial login screens.
Why is gray box testing the best choice for startups?
It offers a high return on investment by balancing speed and depth. Gray box reports provide the security assurance needed to pass enterprise procurement by proving that data isolation and internal permissions are secure.
What are the typical phases of a gray box pentest?
The process involves scoping the environment, sharing limited credentials, active testing, and receiving a remediation report. This structured approach helps identify critical flaws like broken access controls and privilege escalation paths.
Can gray box penetration testing help with compliance?
Yes, gray box testing supports compliance standards like SOC 2 and PCI DSS by validating security controls. It provides evidence that an organization has tested its internal APIs and trust boundaries against potential breaches.
The Bottom Line: SecureLeap offers pentest services tailored for startups, helping them identify vulnerabilities before attackers can exploit them. By choosing a Greybox pentest, you gain a proactive, cost-effective, and thorough approach to protecting your product, your customers, and your company’s future. Gray box testing enables organizations to simulate attacks and uncover weaknesses early, ensuring stronger security posture and peace of mind.
Ready to Get Started with a Penetration Testing Vendor?
Looking for expert penetration testing tailored specifically for startups?
At SecureLeap, we specialize in delivering comprehensive penetration testing services designed to meet the unique security challenges of high-growth startups. Our team of security experts goes beyond standard scans to uncover complex business logic vulnerabilities and potential risks in your environment.
We collaborate closely with you to develop a customized testing strategy that aligns with your startup’s technology stack and business goals, helping you achieve compliance and strengthen your security posture efficiently.