Key Takeaways
- ISO 27001 certification unlocks enterprise deals and proves your security posture to demanding customers
- The 12-step implementation roadmap provides a clear path from initial scoping to ongoing maintenance
- Small SaaS companies can achieve certification in 3–6 months with focused effort and expert guidance
- Documentation and evidence collection are critical—build the habit from day one
- ISO 27001 serves as a strong foundation for multi-framework compliance (SOC 2, HIPAA, PCI DSS)
- Ongoing monitoring and improvement keep your ISMS operating effectively and your certificate valid
ISO 27001 Checklist At-a-Glance (Startup-Friendly Overview)
If you’re running a SaaS company and enterprise prospects keep asking “Are you ISO 27001 certified?” before moving forward, you already know the stakes. That security questionnaire sitting in your inbox isn’t just paperwork—it’s the difference between closing a six-figure deal and watching it slip to a competitor who checked the compliance box.
This checklist cuts through the noise. Here’s what building an information security management system actually looks like for a lean team:
Realistic timelines for small SaaS companies:
- With focused effort and external support: 3–6 months
- Going it alone without dedicated help: 9–12 months
- Average for a 20–80 person company with a consultant: 4–5 months to audit-ready
This checklist is specifically designed for companies with 10–250 people, cloud-first infrastructure (AWS, GCP, Azure), and mostly remote or hybrid teams. If that describes you, you’re in the right place.
SecureLeap works with seed-to-Series B SaaS companies to compress the path to audit-ready using prebuilt ISO 27001 templates, risk registers, and integrations with automation platforms like Drata, Vanta, and Secureframe.

Why ISO 27001 Matters for Small SaaS Companies
ISO 27001 certification is often the gatekeeper requirement for closing B2B and enterprise deals in 2025–2026. When procurement teams at Fortune 500 companies review your security posture, ISO 27001 is frequently the first checkbox they look for.
The pain is familiar: endless security questionnaires, stalled procurement cycles, and prospects ghosting after asking “Are you ISO certified?” Your sales team closes the demo, the champion is excited, and then legal or security puts the brakes on everything.
What ISO 27001 actually gives your SaaS company:
- A repeatable management system for information security that proves you take data protection seriously
- Mapped and documented security risks with clear risk treatment plans
- Defined security controls that auditors, customers, and investors can verify
- A recognized certificate valid for 3 years (with annual surveillance audits)
- A competitive differentiator that removes vendor risk objections before they arise
Real example: A fintech SaaS with under 50 staff secured a Fortune 500 pilot deal specifically because ISO 27001 certification removed the vendor risk objections that had stalled the deal for months. The certificate turned a 6-month procurement process into a 6-week signature.
This checklist is about being practical and lean. You’re not building a bloated enterprise-style ISMS that requires a dedicated compliance department. You’re building exactly what you need to protect sensitive data, satisfy customer security expectations, and achieve certification without derailing your product roadmap.
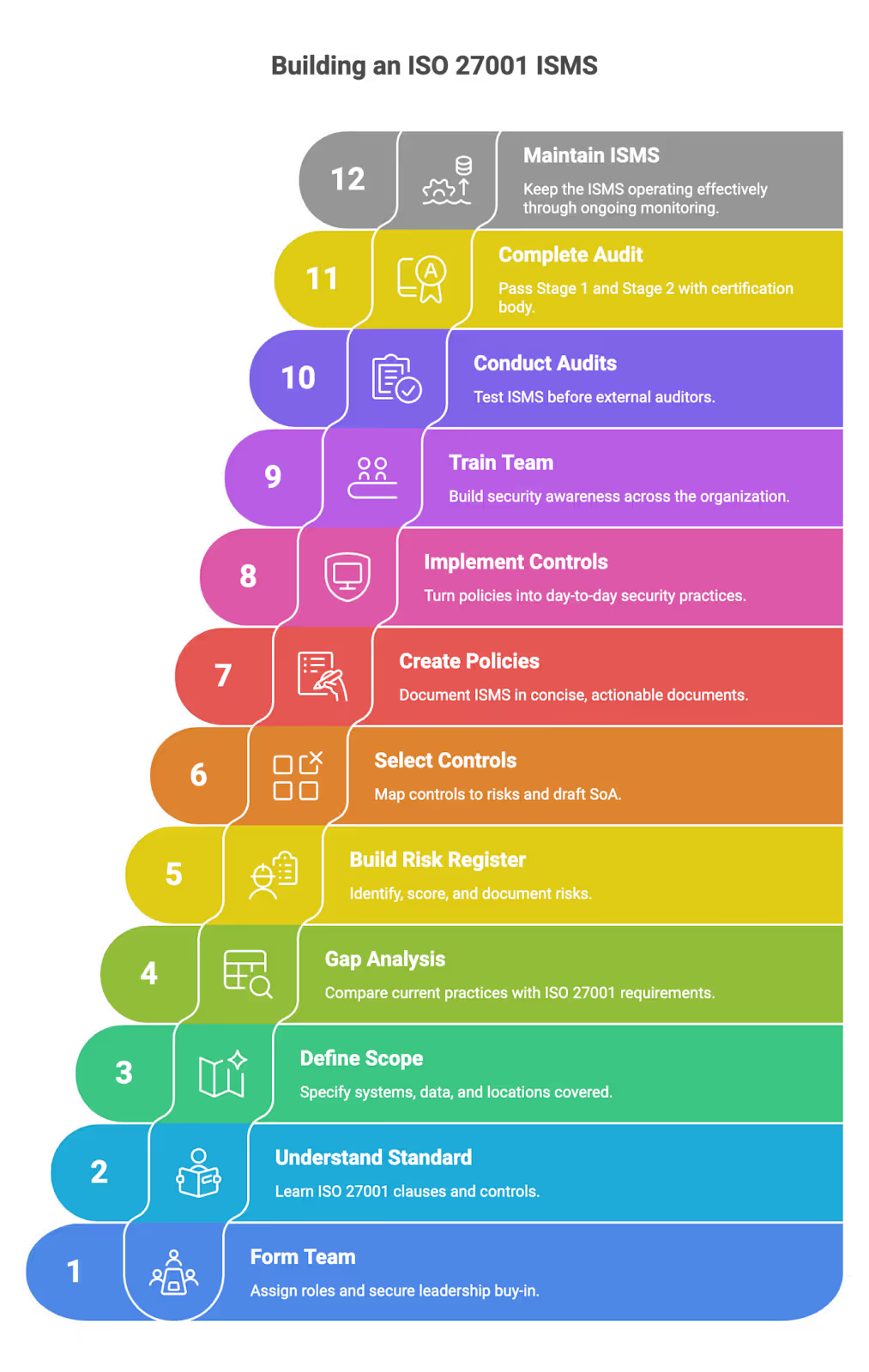
ISO 27001 Checklist: 12-Step Implementation Roadmap
This section is the core of the article: 12 concrete steps, in the order SecureLeap uses with seed–Series B SaaS clients. Each step builds on the previous one, and the sequence is designed to avoid unnecessary rework or over-engineering.
The roadmap assumes ISO/IEC 27001:2022 (the current version with 93 Annex A controls and updated clauses) and cloud-native environments running on AWS, GCP, or Azure. Where relevant, we’ll reference common tooling like Jira, Google Workspace, Okta, GitHub, and Slack to keep this grounded in real workflows.
Let’s break down each step.
1. Form a Lean ISO 27001 Implementation Team
You don’t need a massive committee. You need a small, empowered cross-functional team with clear ownership and sufficient resources to drive the implementation project forward.
Typical roles for a startup:
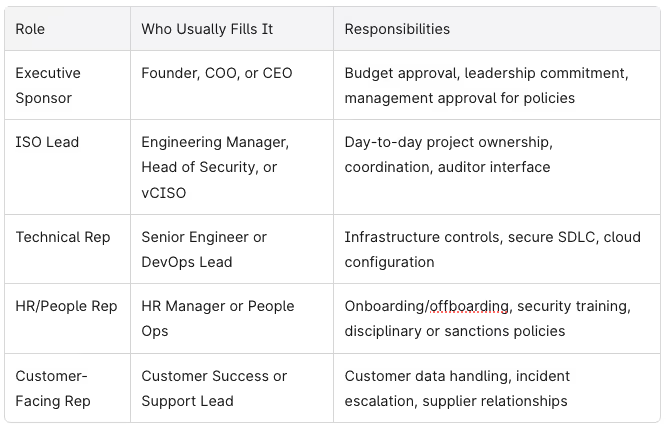
Simple RACI for startups:
- Responsible: ISO Lead owns the risk register, policies, and audit preparation
- Accountable: Executive Sponsor signs off on scope, budget, and management review
- Consulted: Technical and HR reps provide input on controls and implementation
- Informed: Full team receives updates and participates in training
Meeting cadence:
- During implementation: Weekly 30–45 minute standups
- Post-certification: Monthly check-ins for ongoing monitoring
If your company doesn’t have internal security leadership, SecureLeap often fills the vCISO or ISO lead role, providing the expertise you need without a full-time hire.
2. Understand ISO 27001:2022 Requirements (At a Startup Level)
ISO 27001 has two main parts: clauses 4–10 (the management system requirements) and Annex A (93 specific security controls). Here’s what each actually means for your SaaS company.
Clauses 4–10 in plain English:
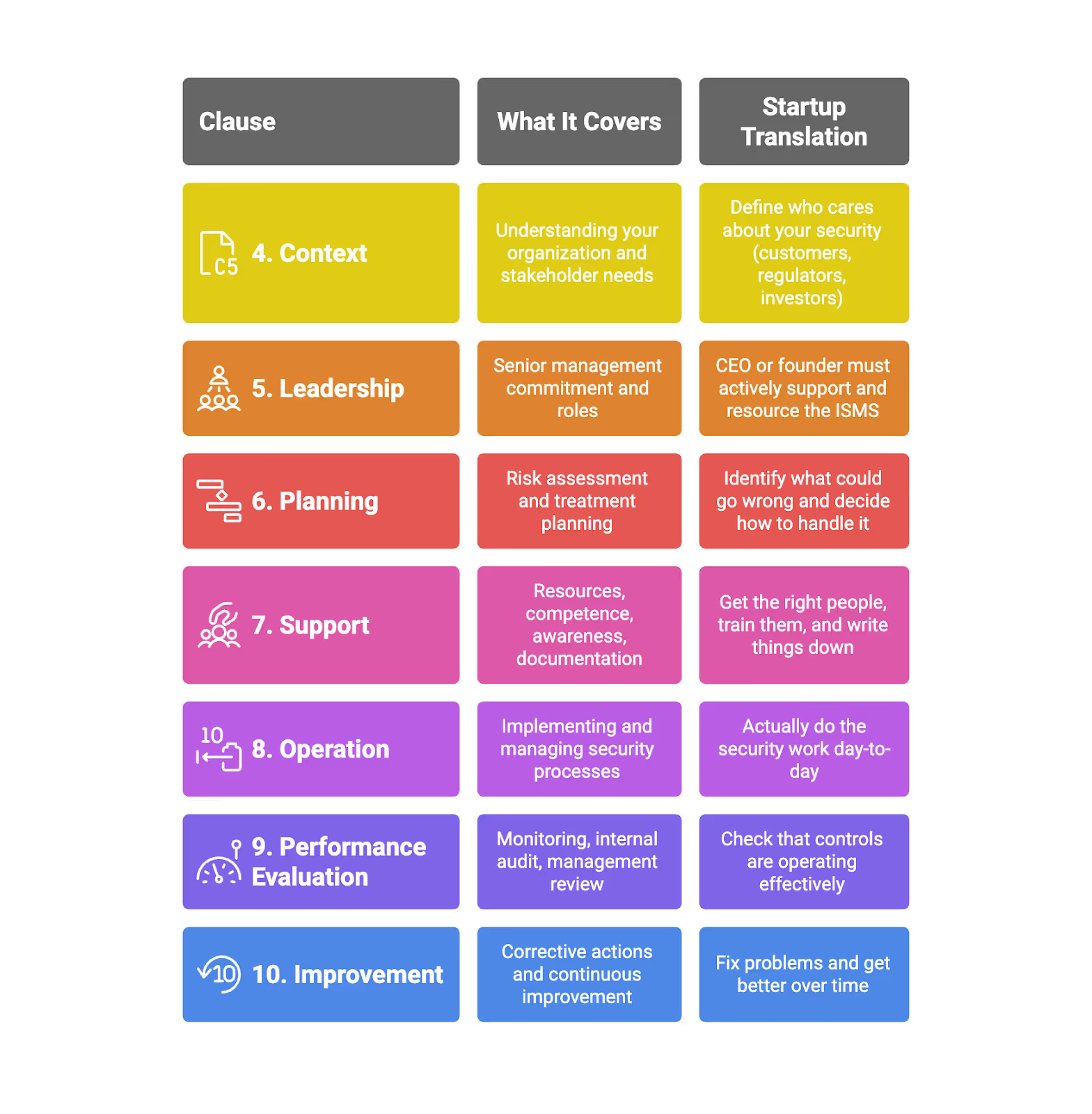
The four Annex A themes:
- Organizational controls (37 controls) – Policies, roles, asset management, supplier relationships
- People controls (8 controls) – Screening, awareness programs, security training, employment terms
- Physical controls (14 controls) – Physical security, physical security monitoring, secure disposal
- Technological controls (34 controls) – Access controls, encryption, network security, secure development
For most SaaS startups, the majority of effort concentrates in organizational controls and technological controls. Physical controls are lighter when you’re fully cloud-based.
ISO 27002:2022 provides detailed implementation guidance, but most startups rely on templates, advisors, or compliance automation platforms rather than reading the standard line-by-line. The goal is outcomes: a documented ISMS, risk-based security controls, and continuous improvement—not perfect adherence to legalese.
3. Define ISMS Scope for a Cloud-First SaaS
Scope is where you can either keep ISO 27001 manageable or accidentally create a monster. A well-defined scope focuses your compliance efforts on what actually matters.
Typical in-scope elements for SaaS:
- Production cloud environment (specific AWS regions, GCP projects, or Azure subscriptions)
- CI/CD pipeline and deployment infrastructure
- Code repositories (GitHub, GitLab, Bitbucket)
- Core SaaS application and customer-facing services
- Customer data stores and databases
- Key vendors and third-party services:
- Cloud provider (AWS, GCP, Azure)
- Authentication provider (Okta, Auth0, Google Workspace)
- Ticketing and support (Zendesk, Intercom)
- Logging and monitoring (Datadog, Splunk)
- Email and communication (Google Workspace, Slack)
- CRM (Salesforce, HubSpot)
Handling remote work:
For distributed teams, auditors realistically expect:
- Clear policies on acceptable use of personal devices and home networks
- Enforced endpoint security (MDM, encryption, antivirus)
- Role based access controls regardless of physical location
- Documentation that remote work is in scope (or explicitly excluded with justification)
Smart exclusions:
You can explicitly exclude non-critical elements from scope with proper justification:
- Non-production development environments (if they never touch real customer data)
- Legacy internal tools being deprecated
- Experimental projects not yet in production
- Subsidiaries or divisions that don’t handle customer data
Capture your scope in a simple ISMS Scope Statement:
- List all information systems, applications, and data in scope
- Specify physical and logical locations (cloud regions, office addresses if applicable)
- Define the business processes covered (product development, customer support, etc.)
- Document any exclusions with clear rationale
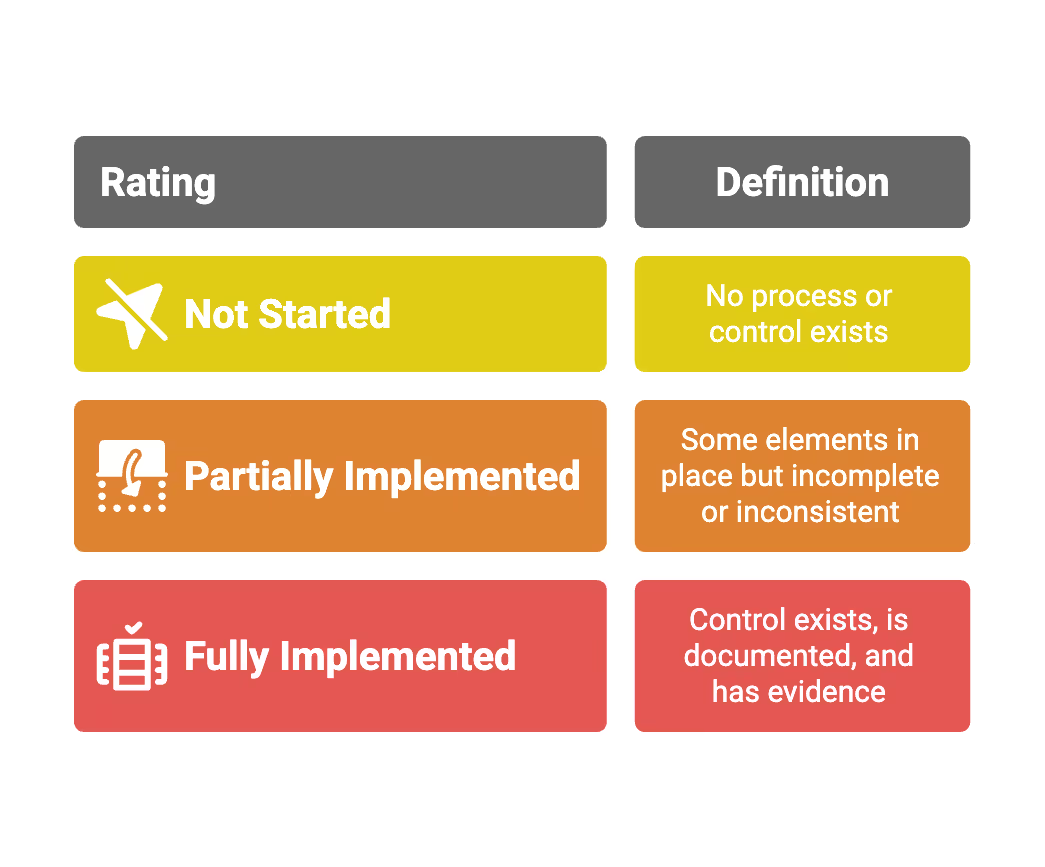
4. Perform a Practical ISO 27001 Gap Analysis
A gap analysis compares your current security practices against ISO 27001:2022 requirements. This tells you exactly where you stand and what work remains.
How to run the analysis:
Use a simple spreadsheet or checklist mapping each ISO 27001 clause and Annex A control. For each item, rate your current state:
Core areas to review for a SaaS company:
- Access management: SSO, MFA enforcement, user provisioning/deprovisioning
- Secure SDLC: Code review, vulnerability scanning, secure coding practices
- Cloud security: IAM policies, logging, backups, configuration management
- Incident response: Detection, escalation, communication, postmortems
- Vendor risk: Third-party assessments, contracts, data processing agreements
- HR security: Background checks, onboarding training, offboarding procedures
- Asset inventory: List of all information assets, data classification
- Change management: Approval workflows, rollback procedures, testing
Example finding:
During gap analysis, you discover MFA is not enforced on GitHub for all developers. This maps to Annex A control 8.5 (Secure authentication) and represents a high-priority gap because a compromised developer account could lead to data theft or malicious code injection.
SecureLeap typically runs this gap analysis in 1–2 weeks and delivers a prioritized remediation roadmap. If you’d like help identifying your gaps before committing to full implementation, book a gap review with our team.
5. Build a Risk Register and Run Your First Risk Assessment
This is the heart of ISO 27001. The entire management system exists to identify and manage information security risks to your SaaS product and operations.
Simple risk methodology for startups:
- Identify assets: Customer data, production databases, source code, API keys, employee laptops, intellectual property
- Identify threats: What could harm each asset (external attackers, insider mistakes, vendor outages)
- Identify vulnerabilities: Weaknesses that threats could exploit (misconfiguration, lack of MFA, unpatched software)
- Assess impact: What’s the business damage if this risk materializes (financial, reputational, regulatory)
- Assess likelihood: How probable is this scenario (rare, possible, likely)
- Score and prioritize: Use a 3×3 or 5×5 matrix to calculate risk level
Example risks for SaaS companies:
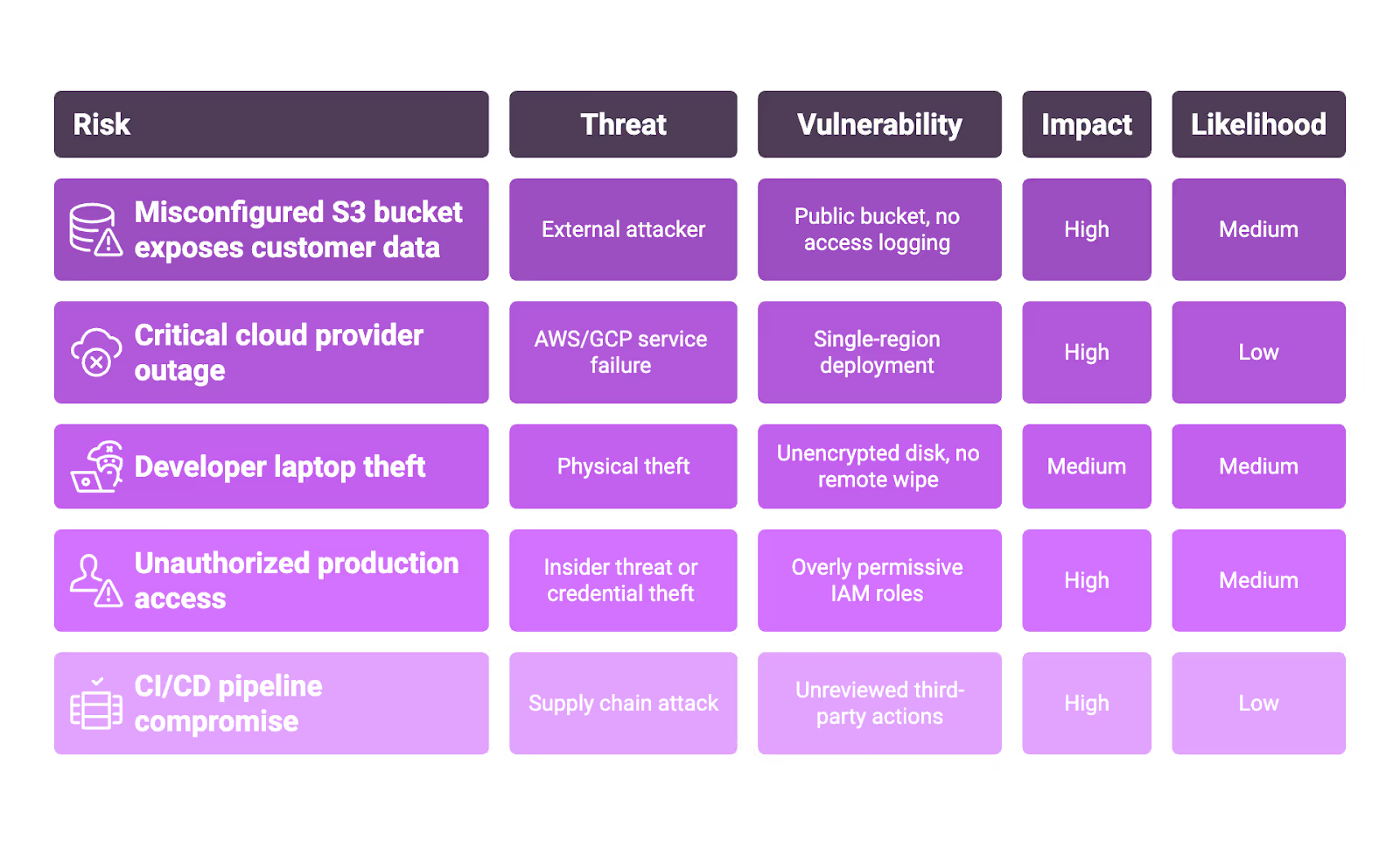
Output: The Risk Register
Your risk register is a living document (often in Google Sheets, Notion, or a GRC tool) that tracks:
- Risk description and category
- Asset(s) affected
- Threat and vulnerability
- Impact and likelihood scores
- Current controls in place
- Residual risk level
- Risk owner
- Review date
This register should be reviewed at least annually and after major changes (new product features, infrastructure migrations, security incidents).
SecureLeap provides prebuilt risk libraries tailored for SaaS, cutting weeks off the risk management process and ensuring you don’t miss common security threats.
6. Select and Map Annex A Controls (and Draft the Statement of Applicability)
Based on your risk assessment and scope, you now decide which of the 93 Annex A controls apply to your organization.
Creating the Statement of Applicability (SoA):
The SoA is a critical document that lists every Annex A control and indicates:
- Applied or Not Applied: Is this control relevant to your scope and risks?
- Justification: Why is it applied or excluded?
- Implementation Status: Is it fully implemented, in progress, or planned?
- Evidence Reference: Where can auditors find proof of implementation?
For most SaaS startups:
The majority of controls are marked as applied. Common justified exclusions include:
- Controls related to on-premises data centers (if you’re fully cloud-based)
- Physical controls for secure areas you don’t operate
- Controls for technologies you don’t use
Examples from each Annex A theme:
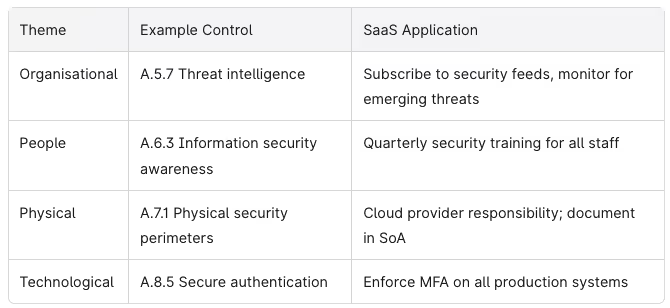
Important: Auditors will review the SoA carefully. It must be:
- Accurate and consistent with your risk register
- Updated when scope or risks change
- Under version control (git, SharePoint, or your documentation system)
The ISO 27001 annex controls form the backbone of your security posture. Take time to get the SoA right.
7. Create and Publish Core ISMS Policies and Procedures
Yes, this is the documentation-heavy step. But for small companies, policies can stay concise (2–6 pages each) and practical. The goal is to document how you actually work, not create shelfware.
Key documents auditors expect:
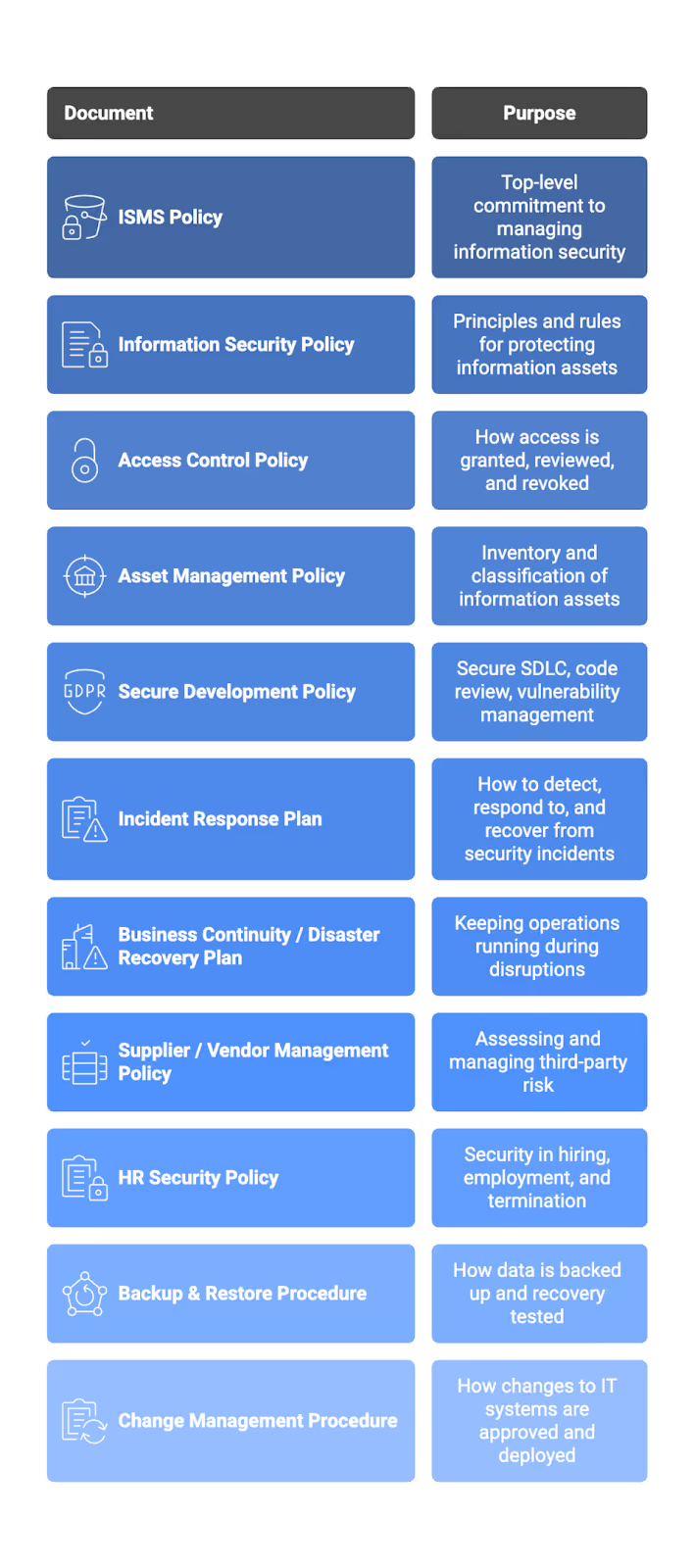
Align documents with actual workflows:
If you use Jira for change management, document that. If code reviews happen via GitHub pull requests, say so. Don’t invent new processes just for ISO—describe reality.
Document control basics:
- Version each document (v1.0, v1.1, etc.)
- Require management approval before publishing
- Set review cycles (at least annually)
- Store in a controlled location (Google Drive, Confluence, Notion) with access logging
SecureLeap provides policy templates tailored to cloud-first SaaS and helps customize them to reflect your actual operations—saving weeks of drafting time.
8. Implement and Operationalize Security Controls
Policies are just paper without implementation. This step turns documentation into day-to-day security practices with real security measures protecting your environment.
Core implementation areas for SaaS:
Identity and Access:
- Enforce SSO and MFA across Google Workspace, AWS/Azure/GCP, GitHub/GitLab
- Configure least-privilege IAM roles (developers don’t need admin access to production)
- Implement just-in-time access for sensitive operations
- Automate user provisioning and deprovisioning tied to HR systems
Logging and Monitoring:
- Enable CloudTrail (AWS), Cloud Audit Logs (GCP), or Activity Logs (Azure)
- Centralize logs in a SIEM or logging platform
- Set up alerts for suspicious security events (failed logins, privilege escalation, unusual data access)
- Implement continuous monitoring for configuration drift
Data Protection:
- Encrypt data at rest (AES-256) and in transit (TLS 1.2+)
- Implement data leakage prevention controls
- Configure backup schedules with tested restore procedures
- Classify data and apply appropriate handling rules
Development Security:
- Integrate vulnerability scanning into CI/CD pipelines
- Require code review before merging to main branches
- Scan dependencies for known vulnerabilities
- Maintain configuration management for infrastructure-as-code
Step-by-step example: Implementing MFA for production access
- Enable MFA requirement in AWS IAM for all users
- Create a privileged IAM role for production changes with time-limited sessions
- Require approval via Slack bot or Jira before assuming the role
- Log all production access in CloudTrail
- Capture screenshot of IAM policy, Slack approval workflow, and CloudTrail log sample as evidence
Evidence collection tip: Every time you implement a control, immediately capture evidence (screenshots, config exports, tickets, logs). Store it in your ISMS folder. This prevents the scramble before audits.
SecureLeap can hook these controls into platforms like Drata, Vanta, or Secureframe so configuration evidence is collected automatically.
9. Train Your Team and Build a Security-Aware Culture
According to data from Verizon, human error drives 74% of breaches. Your team is both your greatest asset and your biggest risk vector. Awareness programs are essential.
A simple, repeatable training program:
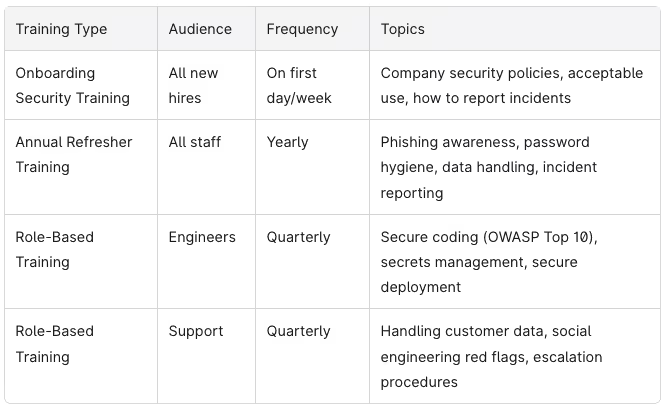
Key training topics for SaaS teams:
- Secure use of laptops (encryption, locking, public WiFi risks)
- Password and MFA hygiene
- Recognizing phishing and social engineering attempts
- How to report security incidents (who to contact, what to include)
- Secure coding practices (for engineers)
- Handling customer data in support tools (for customer-facing roles)
Evidence to keep:
- Attendance records (who completed training)
- Quiz or assessment scores
- Training content and materials
- Completion certificates
Regular phishing simulations (via platforms like KnowBe4 or built-in tools in security awareness platforms) help measure improvement and identify potential threats before real attackers do.
SecureLeap often provides curated security training content and tracks completion as part of an ISO readiness engagement.
10. Run Internal Audits and Management Review
ISO 27001 requires an internal audit before certification, plus regular management reviews to evaluate ISMS performance.
Running an internal audit:
The internal auditor must be independent of day-to-day ISMS operations. Options for startups:
- Appoint someone from a different department who wasn’t involved in implementation
- Engage an external firm (like SecureLeap) to perform the audit
Internal audit process:
- Create an audit plan covering scope, objectives, and schedule
- Develop checklists based on ISO 27001 clauses and Annex A controls
- Sample controls: Review evidence, interview staff, test configurations
- Document findings in an internal audit report
- Classify findings as major nonconformity, minor nonconformity, or observation
- Assign corrective actions with owners and due dates
Management review:
A structured meeting (typically 1–2 hours annually) where senior management reviews:
- ISMS performance metrics and KPIs
- Security incidents and their handling
- Nonconformities and corrective actions status
- Internal and external audit results
- Changes to risks or compliance requirements
- Resource allocation needs
- Improvement opportunities
Artifacts to keep:
- Audit plan and checklists
- Internal audit report with findings
- Management review meeting minutes
- Action items with owners and due dates
- Evidence of completed corrective actions
SecureLeap frequently performs independent internal audits for clients just before they go to a certification body. This de-risks the external audit and catches issues while there’s still time to fix them.
11. Prepare for and Complete the External ISO 27001 Audit
The certification process with an accredited certification body happens in two stages, leading to a certificate valid for 3 years.
Stage 1 Audit (Documentation Review):
- Auditor reviews your ISMS documentation
- Confirms scope, policies, and processes are defined
- Identifies any gaps before Stage 2
- Typically 1–2 days
Stage 2 Audit (Operational Effectiveness):
- Auditor verifies controls are implemented and operating effectively
- Interviews with staff across departments
- Evidence walkthroughs and sampling
- Review of access controls, incident logs, change history, ticketing records
- Typically 3–5 days depending on scope
What you need ready before Stage 1:
- Defined ISMS scope document
- Completed Statement of Applicability
- Risk register with risk treatment plan
- All core policies and procedures
- Internal audit report
- Management review minutes
- At least 2–3 months of evidence for key controls (access reviews, incident logs, change tickets, backup tests)
Example timeline:
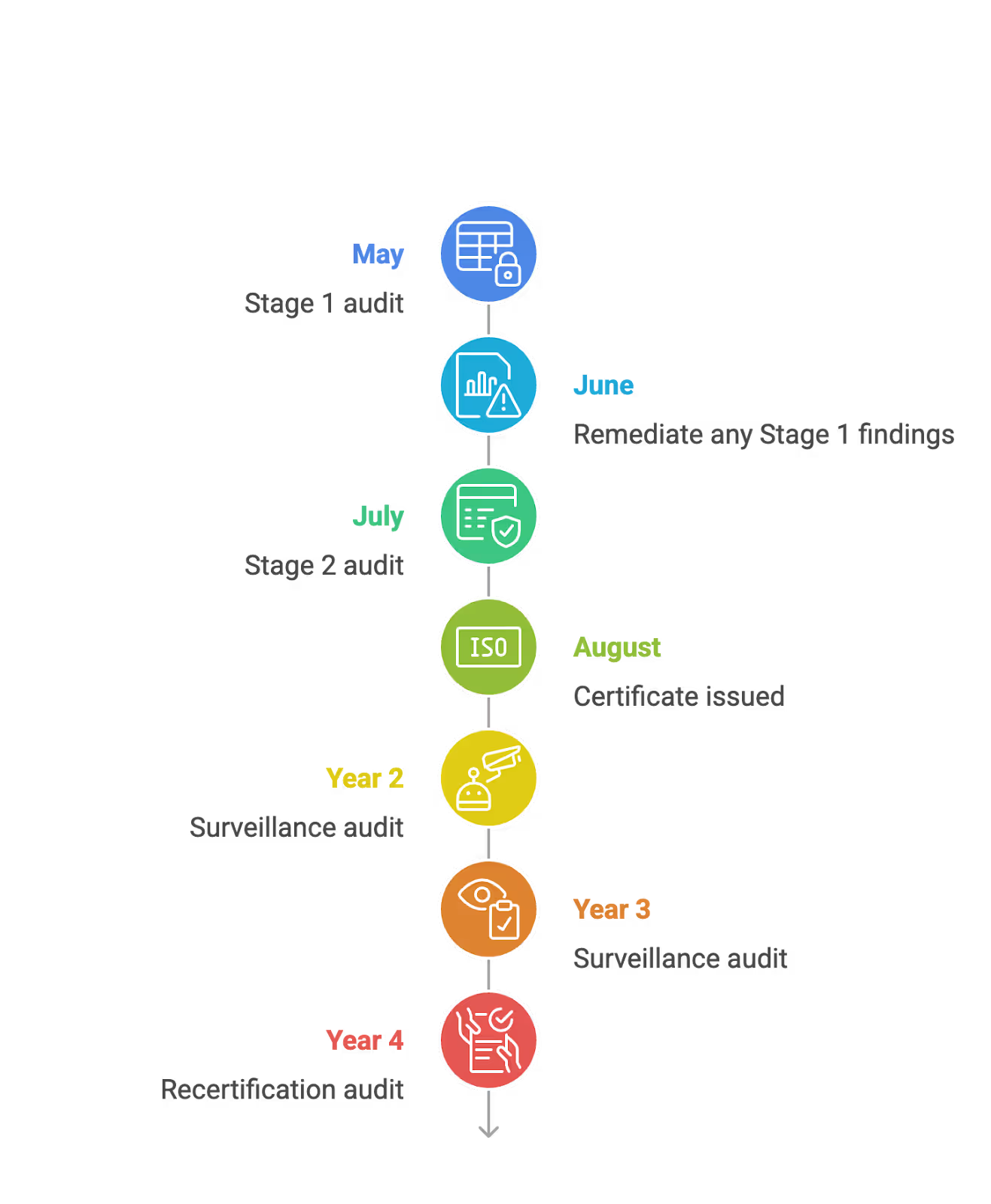
SecureLeap supports clients during the external audit with audit coaching, evidence preparation, and answering auditor questions. If you want expert support through your certification, speak with an ISO lead.
12. Maintain, Monitor, and Continually Improve Your ISMS
ISO 27001 certification is not a one-time project. The certificate requires ongoing monitoring and periodic surveillance audits to remain valid.
Annual compliance calendar for a small SaaS:
Note: The suggested frequencies below are typical recommendations; your organization's specific needs and risk profile may require adjustments to this schedule.
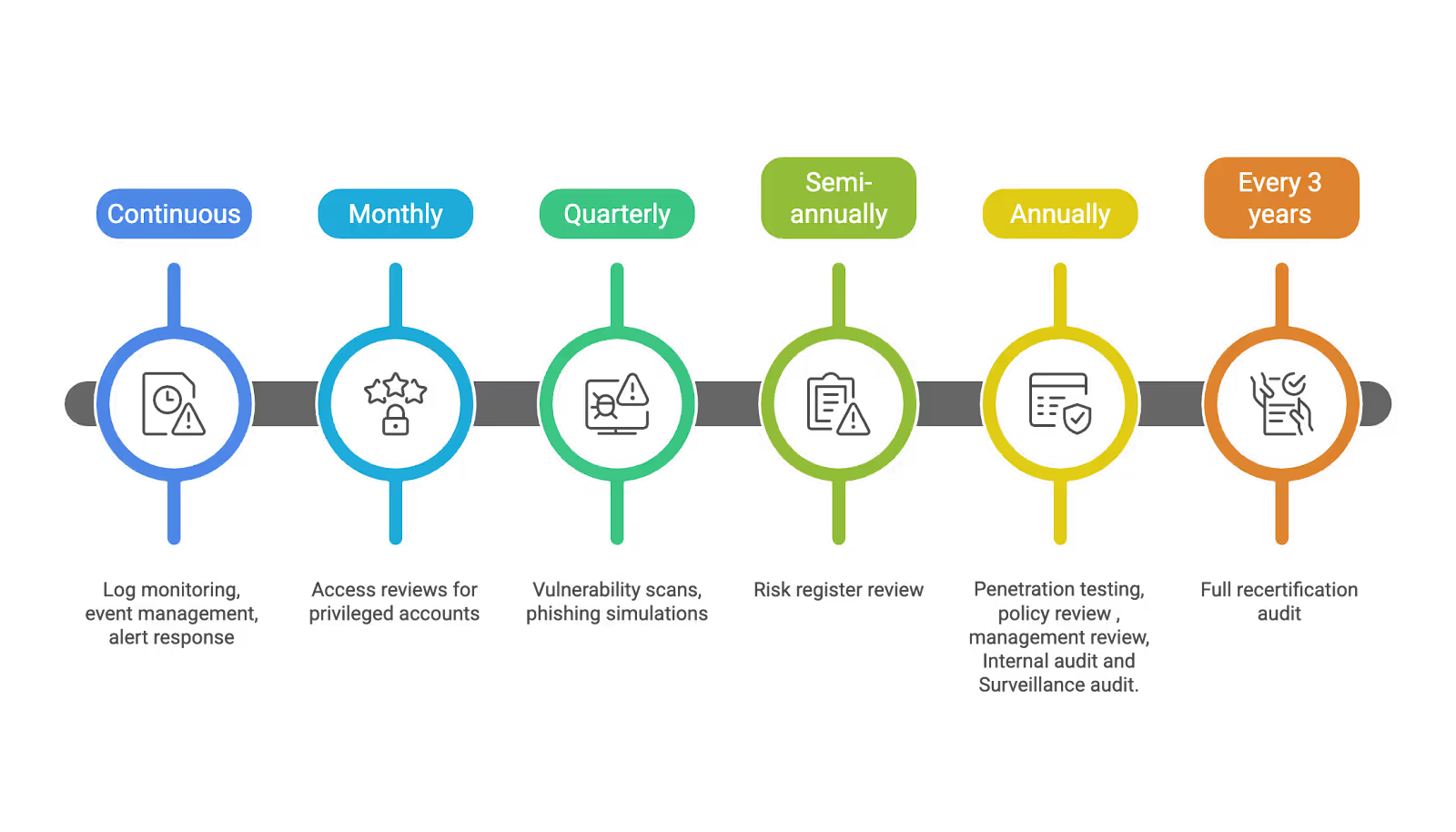
Role of tools in ongoing maintenance:
- SIEM/logging: Detect and respond to security events in real-time
- Ticketing systems: Track corrective actions and review procedures to completion
- Compliance automation (Drata, Vanta, Secureframe): Continuous evidence collection, automated control monitoring, gap alerting
Example: Adjusting risk treatment after a change
Your company adds a new payment processor to handle customer billing. This triggers:
- Update to the asset inventory (new third-party system)
- Vendor risk assessment of the processor
- Update to data flow documentation
- Possible new controls (encryption in transit, access restrictions)
- Risk register update with new identified risks
- SoA update if new controls apply
This is the risk management process in action: your ISMS adapts to business changes rather than becoming stale documentation.
SecureLeap offers ongoing vCISO and managed ISO services where these recurring tasks are tracked and driven by an external security lead. Contact us about continuous compliance support.

Key ISO 27001 Documents and Evidence for SaaS Startups
Many small companies underestimate documentation and evidence requirements. This section makes it concrete and manageable.
Core document categories auditors expect:
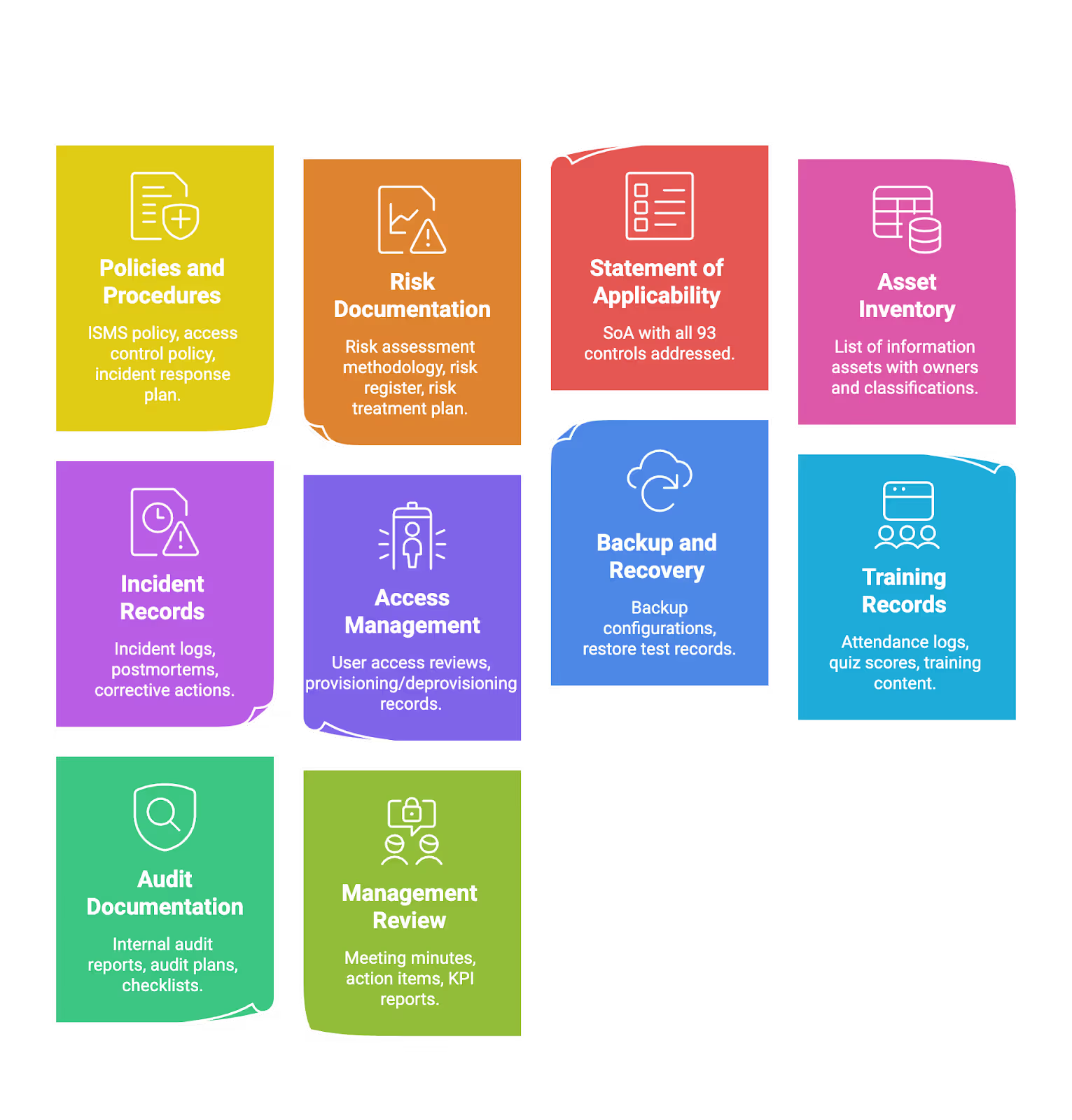
Simple organization approach:
Create a central “ISMS” folder with subfolders:
- /policies – All approved policies and procedures
- /risk – Risk register, risk assessments, treatment plans
- /evidence – Organized by Annex A control or clause
- /audits – Internal and external audit documentation
- /training – Training materials and completion records
- /management-review – Meeting notes and action tracking
Use clear naming conventions: AccessControlPolicy_v2.1_2026-01-15.pdf
Retention guidance:
- Keep at least 3 years of relevant records (aligned with certification cycle)
- Store in a system with access controls and audit logging (Google Drive with sharing restrictions, Confluence, Notion, or a dedicated GRC platform)
SecureLeap routinely builds this evidence structure for clients ahead of audits. Request an ISO evidence checklist tailored to your stack.
Common ISO 27001 Challenges for Small SaaS – and How to Avoid Them
Even with a solid checklist, implementation hits real-world obstacles. Here are the patterns we see across early-stage clients and how to mitigate risks.
Challenge 1: Limited Internal Security Expertise
The scenario: No CISO, no dedicated security team. An engineering leader is wearing the security hat alongside their day job, and nobody has deep familiarity with ISO 27001 wording or what auditors actually expect.
Practical mitigation:
- Use vetted policy templates rather than writing from scratch
- Leverage compliance automation platforms for control monitoring and evidence collection
- Engage external expertise at critical phases: scope definition, risk assessment, internal audit
- Focus on knowledge transfer so you can maintain the ISMS after initial certification
Example: A 35-person B2B SaaS company engaged a part-time vCISO for 4 months to design their ISMS, run the gap analysis, and prepare for audit. After certification, the engineering manager maintained the system internally with quarterly vCISO check-ins.
SecureLeap’s vCISO and audit readiness packages are designed for exactly this scenario—avoiding false starts and expensive rework while building internal capability.
Challenge 2: Time and Resource Constraints
The scenario: Everyone is already stretched thin. Engineers are shipping features, ops is fighting fires, and leadership is closing deals. Nobody has 20 hours a week to dedicate to ISO.
Practical mitigation:
- Run time-boxed ISO sprints (2 weeks documentation, 3 weeks implementation) rather than open-ended projects
- Assign a project manager to track milestones and unblock issues
- Integrate ISO tasks into existing tools (Jira epics, Asana projects) rather than creating parallel tracking
- Reuse existing processes instead of inventing new ones—if you already do code review, document it; don’t create a separate “ISO code review”
- Prioritize high-risk, high-visibility controls first (access management, backups, incident response) to show early progress
Automation via Drata, Vanta, or Secureframe can cut repetitive evidence tasks significantly—but proper setup matters. SecureLeap provides implementation support for these platforms as part of our services.
Challenge 3: Documentation and Evidence Gaps
The scenario: Controls exist in practice but aren’t documented. Engineers configured MFA months ago, but there’s no evidence. This results in nonconformities or delays during the audit.
Practical mitigation:
Build a documentation-first habit: every time you implement or change a control, immediately capture evidence.
Top 10 evidence items startups forget:
- Access review logs (who reviewed what, when, decisions made)
- Backup restore test records (not just backups—actual recovery verification)
- Incident postmortems (even for minor security events)
- Supplier risk evaluations (vendor security assessments)
- Change approval records (who approved production deployments)
- Vulnerability scan results and remediation tracking
- User provisioning/deprovisioning tickets
- Security training attendance and quiz results
- Asset inventory with owners and last review date
- Risk register update history
SecureLeap provides an evidence map that tells clients exactly what to capture per control, tied to ISO 27001 clauses and Annex A references. Clean, organized evidence shortens audit time and reduces friction.
Challenge 4: Aligning ISO 27001 With SOC 2, HIPAA, or PCI DSS
The scenario: Your SaaS needs ISO 27001 for European customers, SOC 2 for U.S. enterprise deals, and maybe HIPAA if you’re in healthtech. Running three separate compliance programs is unsustainable.
Practical mitigation:
Design your ISMS once and map controls across frameworks. A single access control policy can satisfy ISO 27001 A.5.15, SOC 2 CC6.1, and HIPAA’s access management requirements.
ISO 27001 serves as a strong backbone that simplifies adding other security standards later. The documented risk management process, control framework, and evidence collection infrastructure transfer directly.
SecureLeap specializes in multi-framework alignment. We help design one control set that satisfies ISO 27001, SOC 2, HIPAA, and PCI DSS requirements, avoiding duplicate work and accelerating your overall compliance efforts.
How SecureLeap Helps Startups Use This ISO 27001 Checklist
This checklist provides the roadmap. SecureLeap provides the execution support that gets seed-to-Series B SaaS companies across the finish line.
Typical engagement flow:
- Discovery and Gap Analysis – We assess your current state against ISO 27001:2022, identify gaps, and prioritize remediation
- Roadmap Creation – Custom implementation plan with realistic timelines for your team size and maturity
- Policy and Control Implementation – We provide templates, customize them to your reality, and help deploy controls
- Automation Tool Setup – Configuration and integration of Drata, Vanta, or Secureframe for continuous evidence collection
- Internal Audit – Independent audit before you go to the certification body
- Audit Support – Coaching, evidence prep, and real-time support during Stage 1 and Stage 2
Why bundle with SecureLeap:
SecureLeap bundles vCISO consulting, ISO 27001 audit readiness, and penetration testing so startups handle multiple compliance requirements in one coordinated program.
Benefits for startups:
- Faster time-to-certification (4–5 months vs. 9–12 DIY)
- Less engineering time diverted from product development
- Better alignment with customer security expectations
- Confidence going into audit with expert support
Ready to get started?
Schedule a free ISO 27001 readiness consultation or request a sample ISO 27001 startup checklist tailored to your stack.
ISO 27001 Checklist FAQs for SaaS and Small Companies
How Long Does ISO 27001 Certification Take for a Startup?
Realistic ranges:
- With focused effort and external support: 3–6 months
- Entirely in-house, starting from scratch: 9–12 months
- Average with consultant support: 4–5 months to audit-ready
Key dependencies:
- Readiness of existing cloud configurations and security controls
- Responsiveness of leadership for approvals and management review
- Availability of auditor slots (book early—popular certification bodies have waitlists)
SecureLeap engagements are typically structured to get clients audit-ready within 12–16 weeks, depending on current maturity.
What Does ISO 27001 Cost for Small SaaS Companies?
Typical cost bands for 10–250 employee companies:
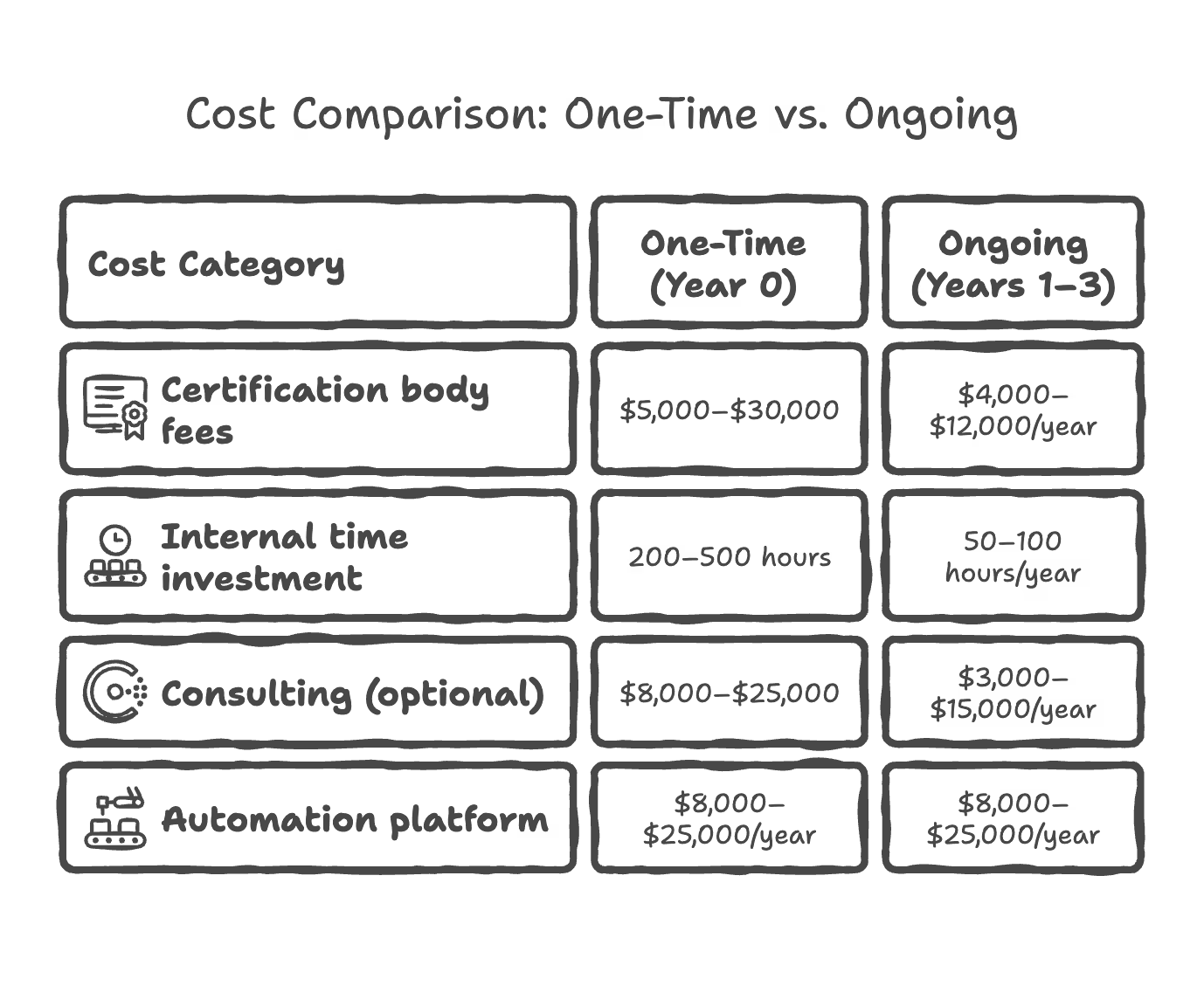
Bundling services (consulting + audit prep + penetration testing) via SecureLeap can reduce overall spend compared to buying everything separately.
Warning: Under-investing often leads to failed Stage 1 or heavy remediation work, which costs more in the long run than getting it right initially.
Do We Need ISO 27001 If We Already Have SOC 2?
Key differences:
- ISO 27001 is a certifiable management system standard with global recognition, especially strong in Europe and enterprise procurement
- SOC 2 is an attestation report tailored to U.S. markets, based on Trust Services Criteria
When ISO 27001 is typically requested:
- Global enterprise customers (especially EU-based)
- Regulated sectors (financial services, government, healthcare)
- Large supply chain requirements (Fortune 500 vendor programs)
- International expansion plans
Many controls overlap significantly. If you have SOC 2, you’re not starting from zero—much of the control work transfers directly.
SecureLeap frequently helps SaaS clients go from SOC 2-only to SOC 2 + ISO 27001 using a unified control set that minimizes duplication.
Does ISO 27001 Need to Cover Our Entire Company?
ISO 27001 allows a defined scope, but for SaaS, most critical functions must be included for the certificate to satisfy customer expectations.
Typically in-scope:
- Product engineering and development
- Production infrastructure and cloud environments
- Customer support (if handling customer data)
- Core business operations
Smart scoping examples:
- Exclude non-production marketing websites that don’t process customer data
- Exclude legacy internal tools being deprecated
- Exclude experimental R&D projects not yet in production
Caution: Overly narrow scope can create customer distrust or auditor skepticism. The scope should be defensible and clearly documented.
SecureLeap helps clients strike the right balance to keep scope lean without making the certificate appear meaningless.
What Happens If We Fail or Get Major Nonconformities in the Audit?
Nonconformity types:
- Major: Significant gap that could lead to system failure or breach; must be resolved before certification
- Minor: Issue that doesn’t threaten the system but needs correction; can be resolved within a defined timeframe
Typical remediation process:
- Root cause analysis of the finding
- Develop corrective action plan with specific steps
- Implement the fix and gather evidence
- Submit evidence to certification body
- Auditor reviews and closes the finding
Most issues stem from missing evidence or inconsistent implementation, not malicious neglect or fundamental security failures. With proper preparation, major nonconformities are rare.
SecureLeap often assists clients responding to nonconformities and tightening their ISMS in advance of follow-up reviews.
ISO 27001 certification doesn’t have to drain your engineering team or derail your product roadmap. With the right approach—lean scope, practical controls, and smart use of external expertise—you can turn information security compliance into a competitive advantage.
Ready to start your ISO 27001 journey?
Schedule a free ISO 27001 readiness consultation with SecureLeap and get a prioritized roadmap tailored to your SaaS company.






