Key Takeaways - ISO 27001 Audit
- An ISO 27001 audit validates that your information security management system actually works—not just that policies exist
- Internal and external audits serve different purposes: internal audits keep you honest; certification audits prove readiness to clients
- Startups under 100 employees can absolutely achieve certification with proper scoping, automation, and focused effort
- The certification process typically takes 4–9 months depending on your security maturity
- Continuous readiness between audits is cheaper and less stressful than periodic scrambles
- Early scoping and realistic planning are the two biggest levers for success
Introduction: Why ISO 27001 Audits Matter for Startups
If you’re a SaaS CEO or CTO at a pre-seed to Series B company, you’ve probably noticed something in your last few enterprise sales cycles: procurement teams aren’t just asking about SOC 2 anymore. They want to see ISO 27001 certification. For startups under 100 employees, this shift can feel like a curveball—especially when you’re already stretched thin shipping product and closing deals.
Here’s a scenario we see regularly: a 40-person B2B SaaS company reaches the final stage of a six-figure deal with a Fortune 500 buyer. Legal sends over a security questionnaire. Buried in section 4.2 is the question: “Please provide your current ISO 27001 certificate or most recent audit report.” The startup doesn’t have one. The deal stalls for months, or worse, goes to a competitor who does. This happens more often than most founders realize.
An ISO 27001 audit isn’t just a checkbox exercise. It’s a structured, evidence-based process that proves your information security is real, repeatable, and ready for scrutiny by enterprise clients and investors. This guide walks you through exactly what these audits look like, the difference between internal and external audits, realistic timelines and costs, and a step-by-step prep workflow built for lean startup teams.
At SecureLeap, we help startups design their ISMS, run internal audits, and coordinate with external certification bodies—often while integrating tools like Drata, Vanta, or Secureframe to reduce manual effort.

What Is an ISO 27001 Audit? (In Startup Terms)
An ISO 27001 audit is a formal, evidence-based review of your information security management system against the requirements of ISO/IEC 27001:2022. Think of it as a structured test that verifies whether your security policies, processes, and controls actually work—not just on paper, but in daily practice.
The term “audit” doesn’t refer to just one event. The full ISO 27001 journey includes several audit types: internal audits you run yourself (required by Clause 9.2), the initial certification audit conducted by an external certification body, annual surveillance audits during your 3-year certificate validity, and recertification audits when that cycle ends.
So what do auditors actually do? They interview your engineers about incident response. They review tickets in Jira to see how changes are approved. They sample access reviews in Okta and scan change logs in GitHub or GitLab. They examine your security policies, risk register, and evidence that controls are being followed. For most SaaS startups, the real goal is passing a Stage 2 external audit and walking away with a 3-year ISO certification—with surveillance check-ins in between.
ISO 27001 vs. SOC 2: A Quick Comparison

The ISO 27001 Standard and 2022 Version Timeline
ISO/IEC 27001 is the international standard for building and operating an information security management system. It’s jointly maintained by the International Organization for Standardization (ISO) and the International Electrotechnical Commission, which is why you’ll see it referenced as iso iec 27001 in formal documentation.
The current version is ISO/IEC 27001:2022, which updated the previous 2013 edition to reflect modern cybersecurity threats and practices. The 2022 revision reorganized Annex A controls and added more explicit requirements around threat intelligence and cloud security—both critical for today’s SaaS environments.
What Gets Audited: Clauses and Controls
The standard is built around two main components:
- Clauses 4–10: These cover your management system requirements—context of the organization, leadership commitment, planning, support resources, operations, performance evaluation, and continual improvement.
- Annex A Controls: 93 security controls organized into four themes: Organizational, People, Physical, and Technological.
For startups, here’s the key insight: controls are risk-based. A 25-person SaaS with one AWS region and a single office will implement a leaner control set than a 2,000-person multinational. Your Statement of Applicability (SoA) documents which controls apply to your specific risk profile and why.
Auditors will expect alignment to the 2022 Annex A structure. If you’re using policy templates or compliance tools, confirm they’re updated for the current version—otherwise you’ll burn time fixing misalignments during your audit.
Types of ISO 27001 Audits (Internal, Certification, Surveillance, Recertification)
On your ISO 27001 journey, you’ll encounter four key audit types:
- Internal audits – Required by Clause 9.2, these self-assessments verify your ISMS works as designed
- Initial certification audit – A two-stage external audit that leads to your 3-year certificate
- Surveillance audits – Annual check-ins during years 1 and 2 of your certification cycle
- Recertification audit – Full review in year 3 to renew your certificate

Understanding how each works helps you plan resources and avoid surprises.
Internal ISO 27001 Audit for Startups
An internal audit is a systematic, evidence-based review performed by someone independent of the processes being audited. This can be an internal team member from a different department or an external consultant like SecureLeap—what matters is objectivity, not employment status.
For a 30–60 person SaaS company, here’s a practical structure:
- Annual full-scope internal audit: Cover all clauses and applicable Annex A controls once per year
- Quarterly targeted mini-audits: Focus on high-risk areas like access control, change management, and incident response
- Continuous monitoring: Use automation tools to flag control failures between formal audits
Your audit program should include planning documentation, an audit checklist based on clauses and controls, interviews with process owners (Head of Engineering, DevOps lead, HR), and a formal audit report with findings classified as major nonconformities, minor nonconformities, or opportunities for improvement.
Internal audits before certification should mimic the rigor of a real external audit. Soft-pedaling issues internally only creates surprises during Stage 1 and Stage 2.
Certification Audit: Stage 1 and Stage 2
The certification audit happens in two stages, conducted by an accredited certification body.
Stage 1: Document and Design Review
Stage 1 is typically remote (though sometimes on-site) and focuses on:
- ISMS scope and boundaries
- Information security policy and supporting procedures
- Statement of Applicability
- Risk assessment methodology and results
- ISMS readiness for Stage 2
For startups under 100 employees, Stage 1 usually takes 1–2 days. It typically occurs 2–8 weeks before Stage 2, giving you time to address any gaps the audit team identifies.
Stage 2: Operating Effectiveness
Stage 2 is the in-depth test. Auditors will:
- Sample controls across your SoA
- Review real tickets, logs, and evidence
- Interview employees about their roles in security processes
- Verify that controls have been operating effectively over a defined period (typically 3–12 months)
Both stages must be conducted by an ISO 27001 certification body accredited by a recognized accreditation body—such as the ANSI National Accreditation Board (ANAB) in the U.S. or UKAS in the U.K. Choose your certification body early; their audit calendar availability often drives your timeline.
Typical Certification Flow
- Book Stage 1 date (typically 4–8 weeks out)
- Pass Stage 1 or remediate findings
- Run ISMS “live” for 1–3 months with evidence collection
- Complete Stage 2 audit
- Receive official certification decision (30–60 days after Stage 2)
Surveillance and Recertification Audits
Once certified, you’re not done with audits—you’re entering a continuous cycle.
Surveillance Audits (Years 1 and 2)
These annual check-ins are shorter than Stage 2—typically 1–1.5 days for a lean SaaS. Auditors will:
- Verify that previous nonconformities were addressed with documented corrective actions
- Sample a rotating set of Annex A controls (roughly 50% each year)
- Look for evidence of continual improvement: updated risk registers, incident postmortems, security metrics
Recertification Audit (Year 3)
The recertification audit is similar in scope to Stage 2. The audit team will confirm your ISMS still matches your current organization. This is where growth-related misalignment often surfaces—if you’ve scaled from 20 to 120 employees, added new products, or expanded to new regions, your ISMS must reflect those changes.
Failing surveillance or recertification can lead to certificate suspension or withdrawal. Many organizations treat these audits casually and pay for it later.
What ISO 27001 Auditors Actually Evaluate
Auditors focus on two dimensions: design (are controls appropriate to your risks and scope?) and operating effectiveness (are they actually followed and producing evidence?).
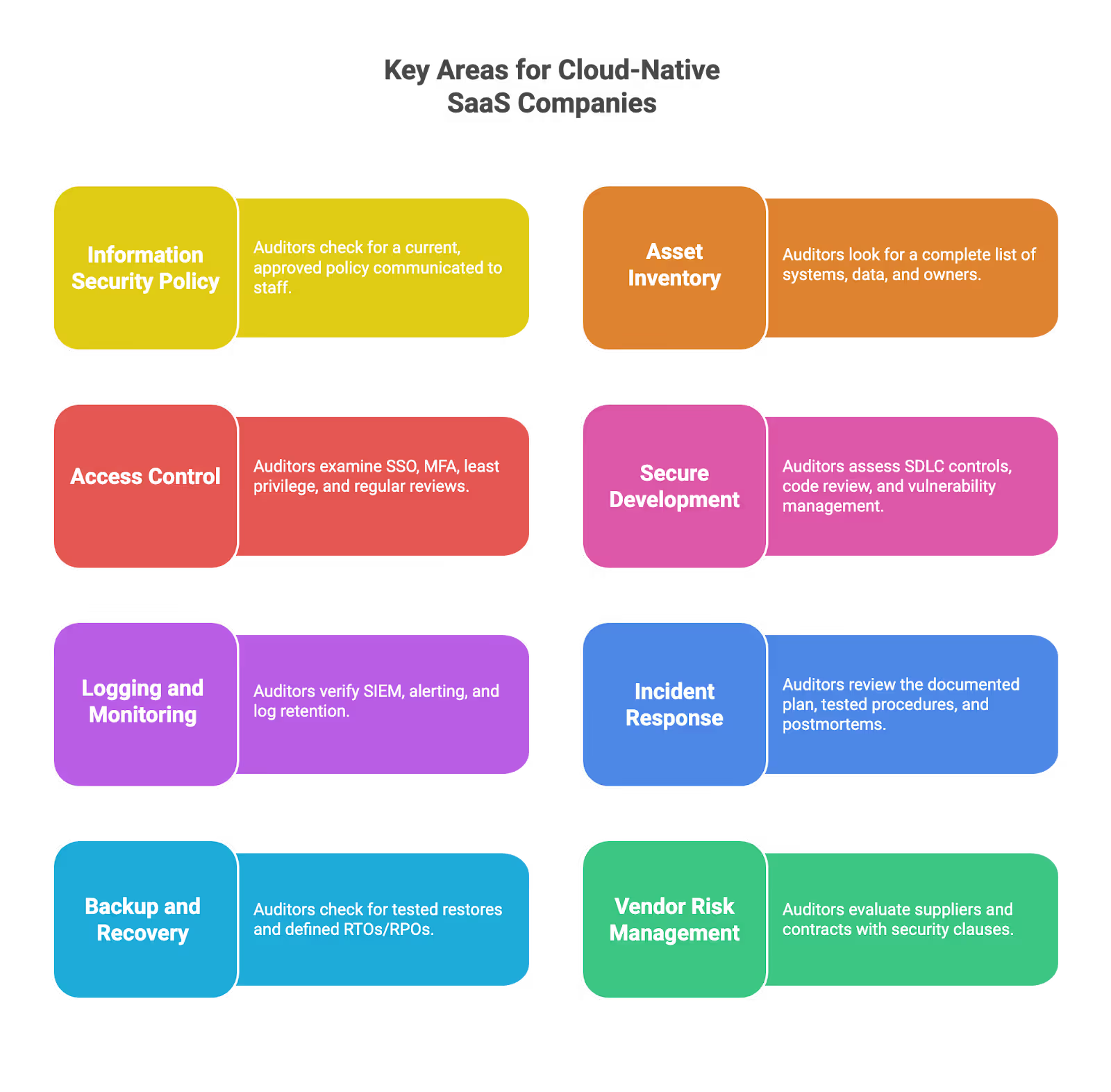
Auditors trace requirements end-to-end: from a risk in your risk register, to a control in your SoA, to a documented procedure, to tickets or logs showing execution, and finally to management review and improvement records.
Concrete Example: Access Reviews
For access reviews, an auditor might request 2–3 samples from the last year showing:
- Who initiated and approved the review
- What accounts were examined across AWS, Okta, GitHub
- How orphaned or excessive access was removed
- Where the completed review is documented
Auditors don’t expect perfection from a 30-person startup. They expect consistency, clear ownership, and a demonstrated willingness to fix issues quickly with proper corrective actions.
Common Nonconformities and How to Avoid Them
Audit findings fall into categories: major nonconformities (significant gaps that can halt certification), minor nonconformities (smaller issues requiring attention), and opportunities for improvement (suggestions, not blockers).
Typical Nonconformities for Small SaaS Companies
- Risk assessment incomplete or missing key threats (supply chain, API vulnerabilities)
- SoA not aligned to 2022 Annex A structure
- No evidence of security awareness training completion
- Inconsistent change management (engineers deploying without documented approvals)
- Missing formal supplier/vendor evaluations
- Incident response plan exists but never tested
- Access reviews documented for some systems but not others
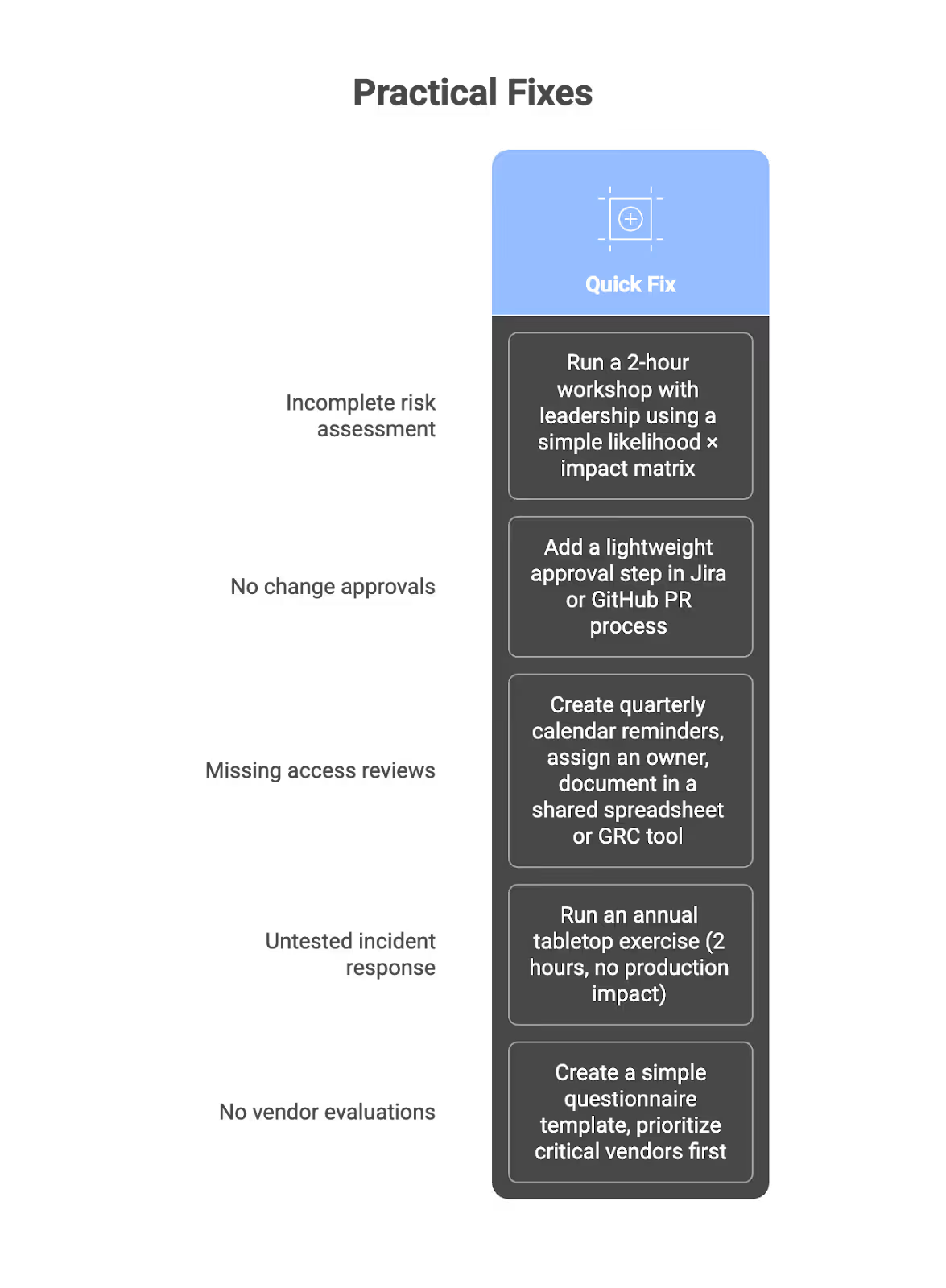
At SecureLeap, our audit readiness service includes a pre-audit gap analysis 2–4 months before Stage 1. This catches issues while there’s still time to fix them properly.
Step-by-Step ISO 27001 Audit Preparation Workflow for Startups
This workflow targets startups under 100 employees aiming to get certified in 4–9 months—often ahead of a major enterprise contract or funding round.
Five Phases to Certification
- Define scope and select partners/tools
- Build and document your ISMS
- Run internal audit and remediation
- Navigate Stage 1 and Stage 2
- Stay ready for surveillance
Assign a single ISMS owner for this initiative. This is often a Head of Security, VP Engineering, or a PM-type compliance lead. Plan for 20–50% of their capacity during the initial build-out.

Phase 1: Define Scope, Timeline, and Partners
Defining Your ISMS Scope
Keep it focused. Include:
- Production infrastructure (e.g., AWS us-east-1)
- Core SaaS application and customer data
- Critical third parties (cloud providers, payment processors)
- Key internal functions (engineering, customer support, HR for access provisioning)
Exclude non-essential systems (marketing tools, sales demos) to reduce audit complexity. Document scope boundaries with a simple architecture diagram and data flow diagram.
Setting Your Timeline
Tie your certification target to a business milestone:
- “ISO 27001 certificate by Q3 2026 before Series B”
- “Certified before enterprise MSA signature in January”
Work backward from that date to set Phase 1–4 deadlines.
Selecting Partners
- Choose an accredited certification body early and confirm their audit calendar availability
- Evaluate compliance automation tools (Drata, Vanta, Secureframe) for evidence collection
- Consider working with a boutique partner like SecureLeap for policy drafting, risk workshops, and internal audit execution
Phase 2: Build and Document Your ISMS
Key Deliverables
- Information security policy (top-level document signed by leadership)
- Risk assessment and risk treatment plan
- Statement of Applicability mapping risks to Annex A controls
- Annex A control procedures (access control, change management, etc.)
- Incident response plan
- Business continuity and backup strategy
- Vendor management process
- Security awareness training program
Practical Workflow
- Start with business context workshops: Who are your interested parties? What are your key assets? What regulations apply?
- Run risk assessment workshops with founders and tech leads, identifying top threats (data breaches, ransomware, insider threats, third-party failures)
- Derive controls and SoA from identified risks
- Write policies in plain, actionable language—each specifying owner, activity frequency, and evidence expectations
Use realistic, startup-friendly controls. If you’re already using AWS-native security tools and GitHub Actions for CI/CD, build controls around those—don’t implement expensive enterprise systems you don’t need.
Configure automation tools to continuously collect evidence from AWS, Okta, Google Workspace, GitHub, and HRIS systems. This reduces manual scramble before audits.
Phase 3: Run the Internal Audit and Fix Gaps
Once your ISMS has been operating for at least 8–12 weeks, schedule a full internal audit.
Internal Audit Activities
- Plan audit scope and schedule
- Conduct document review of policies, procedures, and records
- Interview control owners (DevOps, HR, Finance)
- Sample tickets, logs, and evidence
- Compare actual practice to documented policy
- Document findings as major/minor nonconformities or improvement opportunities
- Assign corrective actions with due dates
Track findings in a simple system—Jira project, spreadsheet, or your GRC tool. Each finding needs an owner and resolution date.
For lean teams, outsourcing the internal audit to an experienced ISO 27001 consultant keeps the assessment independent and realistic. SecureLeap’s vCISO service often includes this.
Example Finding and Fix
After an internal audit, a startup discovers that contractors aren’t included in quarterly access reviews. The fix: add contractor accounts to Okta groups, update the access review checklist to explicitly include them, and schedule the next review to capture the change.
Phase 4: Navigate Stage 1 and Stage 2 External Audits
Preparation Checklist
- Complete remediation from internal audit findings
- Lock in Stage 1 date with your certification body
- Prepare an “audit pack”: policies, SoA, risk assessment, org chart, architecture diagram, key procedures
- Brief all control owners on what to expect
Stage 1: What to Expect
- 1–2 days of remote sessions (sometimes on-site)
- Document walkthroughs and Q&A about scope and context
- Audit report listing readiness status and any gaps to close before Stage 2
Between Stage 1 and Stage 2
Rapidly close any identified issues:
- Formalize that missing supplier evaluation checklist
- Add KPIs to your management review minutes
- Generate fresh evidence showing controls working post-Stage 1
Stage 2: What to Expect
- Live demonstrations: screen-sharing SIEM dashboards, showing CI/CD controls
- Review of actual incidents and postmortems
- On-the-spot evidence requests (“Show me a completed access review from Q2”)
- Interviews with key stakeholders across engineering, ops, and leadership
CEOs and CTOs should attend opening and closing meetings. Auditors expect leadership commitment under the leadership clause, and your presence demonstrates that security is a business priority.
Phase 5: Staying Audit-Ready Between Certifications
Continuous readiness prevents the frantic scramble before surveillance audits.
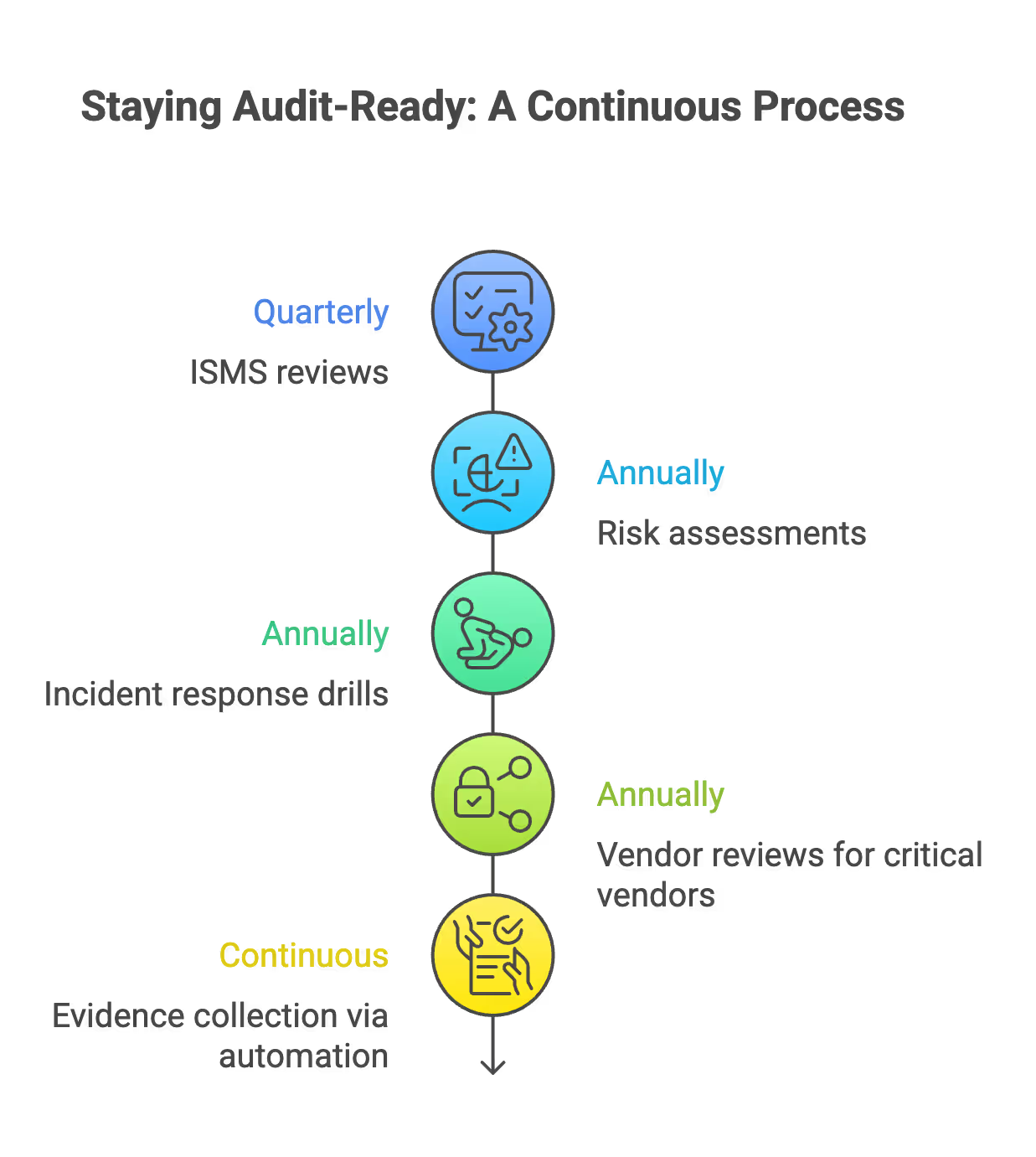
Use a single source of truth—your GRC platform—where all policies, procedures, evidence links, and audit results live. This eliminates version control chaos.
Startups change fast. When you add new products, teams, offices, or regions, update your ISMS immediately. Don’t wait until recertification to discover your scope is outdated.
Ready to Get Started?
Book a free 30–45 minute consultation with SecureLeap to review your current state and build a lightweight, founder-friendly audit readiness roadmap.
ISO 27001 Audit Costs, Timelines, and Resourcing for Small SaaS Companies
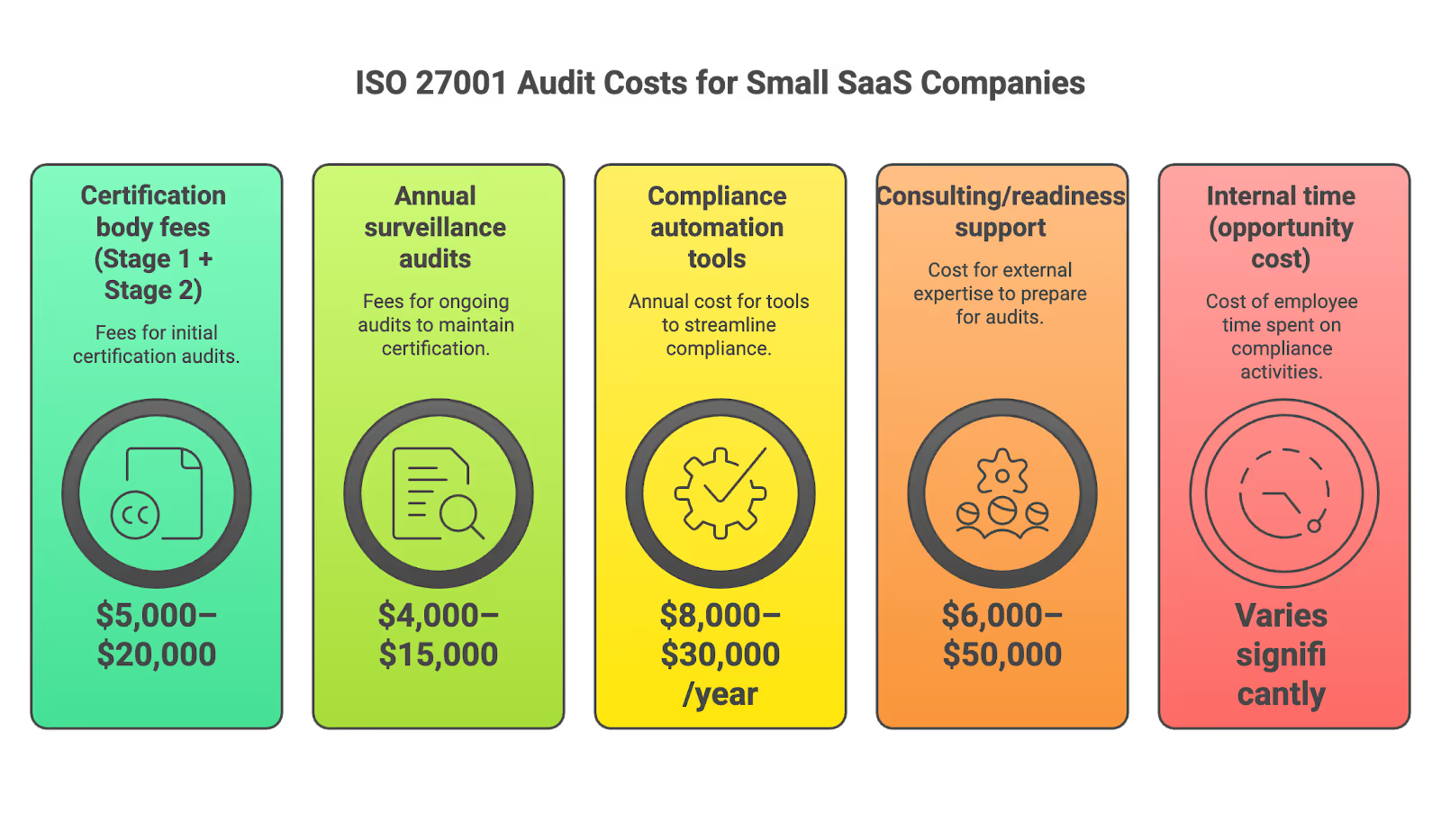
Total “all-in” cost for a first-time certification typically lands between $22,000–$50,000 for small firms. Frame this against expected revenue impact: unlocking a $100K–$1M enterprise pipeline makes the investment worthwhile.
Realistic Timelines
- 4–6 months: Companies with existing security baseline (some policies, configured tools, security-aware engineering culture)
- 6–9+ months: Greenfield environments or immature security practices
Resourcing Advice
- Nominate 1–2 internal champions to own the initiative
- Budget 0.5 FTE for 3–6 months during active implementation
- Avoid starting right before a major product launch—competing priorities doom audit prep

How SecureLeap Helps Startups Win Their ISO 27001 Audit
At SecureLeap, we partner with seed-to-Series B SaaS and tech companies to make ISO 27001 certification achievable without building a massive security team.
What We Offer
- ISO 27001 Readiness Assessments: Gap analysis against the standard, tailored to your risk profile and timeline
- Policy and Control Design: Startup-friendly documentation that passes auditor scrutiny without enterprise bloat
- vCISO Leadership: Fractional security leadership to guide strategy and own your audit program
- Internal Audits: Independent assessments that prepare you for the real thing
- Certification Body Coordination: We help you select and work with accredited bodies efficiently
- Penetration Testing: Comprehensive pentest services to identify vulnerabilities and strengthen your security posture
- Bundled Packages: Cybersecurity consulting + audit readiness + penetration testing in one engagement
- Tool Implementation: Drata, Vanta, and Secureframe setup mapped correctly to ISO/IEC 27001:2022
Ready to Start Your Certification Journey?
Schedule a free ISO 27001 audit readiness call to review your timeline, budget, and best path to certification.
FAQs about ISO 27001 Audits for Startups
How soon before a big enterprise deal should we start ISO 27001?
Plan for 6–9 months from kickoff to certificate in hand. If you have an urgent RFP deadline, communicate that to your certification body and consulting partner—compressed timelines are possible but require more resources and fewer scope changes.
Can a startup with 20 people realistically pass an ISO 27001 audit?
Yes. Many organizations of this size achieve certification successfully. The key is scoping appropriately (don’t include every system you touch), using automation for evidence collection, and ensuring leadership is genuinely engaged—not just delegating to a single overwhelmed employee.
Do we need both ISO 27001 and SOC 2?
It depends on your customer base. U.S.-centric enterprises often accept SOC 2. European and APAC enterprises typically require ISO 27001. Increasingly, we see startups pursuing dual certification since over a decade of market evolution has made both standards table stakes for serious enterprise sales.
What happens if we fail Stage 2?
A failed Stage 2 usually means major nonconformities that require action plans and re-audit of affected areas. You won’t receive certification until these are resolved. The certification body will schedule a follow-up assessment—typically within 90 days—to verify corrective actions were effective.
Do we need a dedicated security hire before starting?
Not necessarily. Many startups work with a vCISO or consultants seeking to build their program. What you do need is clear ownership: someone accountable for driving the initiative, even if they have other responsibilities. A fractional approach often makes more sense than a full-time hire at the early stages.
Will tools like Drata, Vanta, or Secureframe guarantee we pass?
No. These tools are excellent for automating evidence collection and monitoring, but they don’t replace the fundamental concepts of process ownership, risk management, and leadership engagement. Auditors seeking evidence will still interview your team, probe your understanding of risks, and verify that controls operate as designed. Tools support the process; people run the process.
How much of my team’s time will this take?
Expect your ISMS owner to spend 20–50% of their time during active build-out (3–6 months). Key stakeholders (engineering leads, DevOps, HR) will need a few hours per month for interviews, reviews, and feedback. The burden decreases significantly after certification, assuming you maintain continuous readiness.
What’s the biggest mistake startups make?
Scope creep and late starts. Trying to include every system inflates costs and complexity. Starting 3 months before a hard deadline leaves no room for findings remediation. Early planning and realistic scoping are the two biggest levers for a smooth ISO 27001 audit journey.
If you’re a SaaS founder or CTO looking to close enterprise deals that require ISO 27001 certification, start now. The process takes longer than most expect, but the payoff—in revenue, trust, and operational maturity—makes it worthwhile.
Connect with SecureLeap to build your path to certification.






