For a fast-growing startup, security is often a "catch-22." You need to move quickly to ship features, but one significant data breach could end your company’s journey before it truly begins.
As you start looking into security audits—perhaps to satisfy a big enterprise client or to prepare for SOC2 compliance—you’ll constantly run into two terms: Vulnerability Scanning and Penetration Testing. While they sound similar, they serve very different purposes.
Here is a breakdown of what each one is, how they differ, and which one your startup actually needs right now.

What is Vulnerability Scanning? (The Automated Check-up)
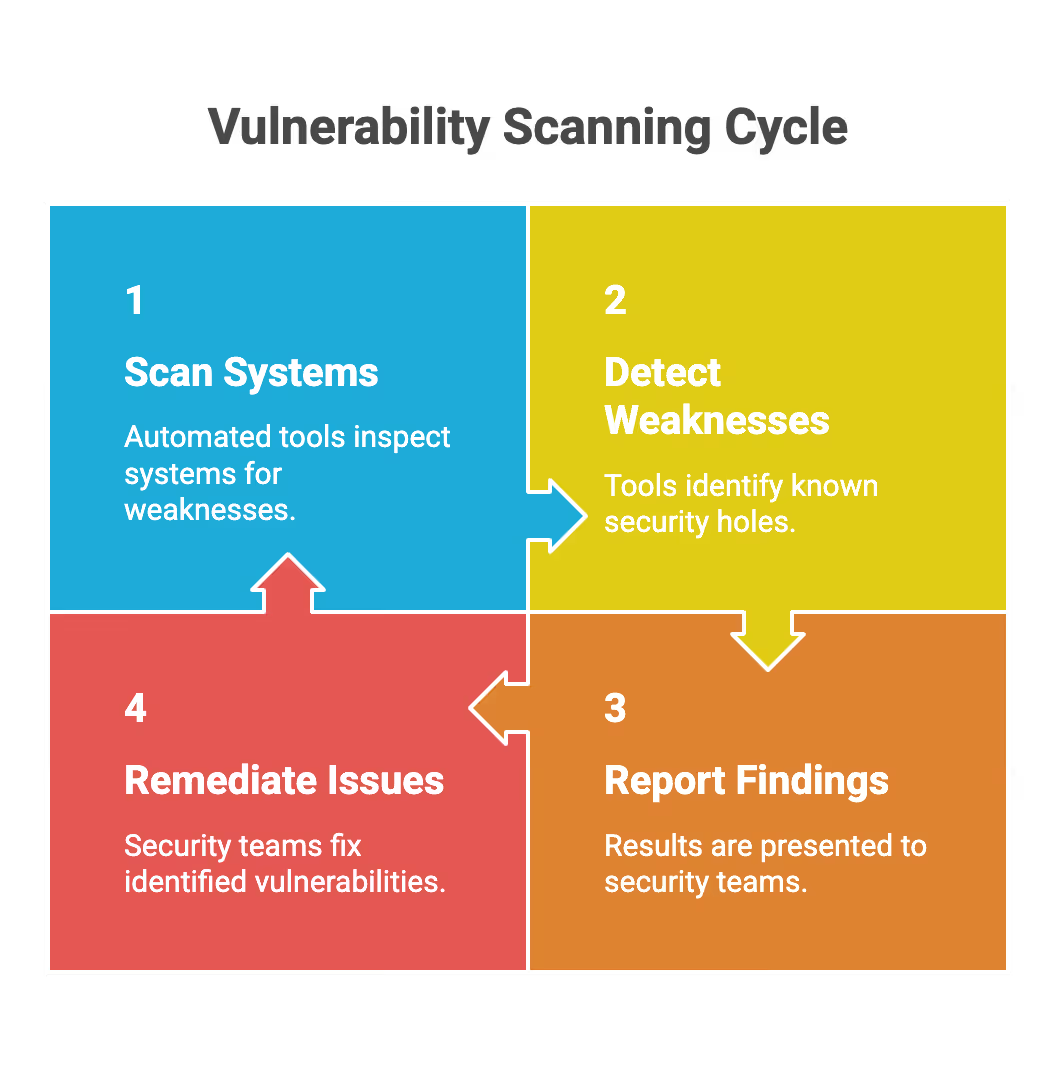
Think of a vulnerability scan as a high-tech smoke detector for your code and infrastructure. Vulnerability scanners are automated cybersecurity tools designed to detect security weaknesses across networks, web servers, and web applications. It is an automated tool that “inspects” your systems to find known security holes.
How it works:The scanner runs through a massive database of “known vulnerabilities” (called CVEs). It looks at your servers, software versions, and configurations to see if anything matches a list of documented weaknesses.
Vulnerability assessment is the process of using automated tools to identify and analyze vulnerabilities in IT infrastructure, networks, and web applications.
Vulnerability testing includes both vulnerability scanning and other methods to identify and mitigate system weaknesses.
There are two main types of scans: unauthenticated scans, which are performed without login credentials to assess external attack surfaces, and authenticated scans, which use login credentials to provide deeper insight into internal vulnerabilities. Dynamic application security testing is a type of automated scan that identifies security weaknesses in web applications. Vulnerability scanners can detect open ports and insecure configurations on web servers, which are common entry points for attackers.
A comprehensive inventory of IT assets is essential for effective vulnerability assessment and testing. Analysis of scan results helps IT staff prioritize remediation efforts.
- The Output: An automated report listing potential vulnerabilities, usually ranked by severity (Low, Medium, High, Critical).
- The Pro: It’s fast, relatively inexpensive, and can be run weekly or even daily.
- The Con: It lacks “eyes.” It cannot tell the difference between a real threat and a “false positive.” It also can’t find “logic flaws” (e.g., a user being able to access someone else’s data because of a bug in your app’s permissions).
What is Penetration Testing? (The Ethical Hack)
If a vulnerability scan is a smoke detector, a penetration test (or “Pentest”) is hiring a professional fire inspector to actually try and start a controlled fire to see if your building burns down. Pen testing involves simulated attacks conducted in a controlled manner to identify security vulnerabilities, following established methodologies to ensure a thorough and authorized assessment.
How it works:A penetration test is a manual engagement performed by a human security expert. They don’t just look for “known bugs”; they use creativity and intuition to find ways to break into your system. They chain multiple small weaknesses together to achieve a “goal,” such as accessing your production database or gaining admin rights.
The goal of penetration testing is to mimic real-world attackers attempting to gain unauthorized access to sensitive systems or data.
- The Output: A detailed, hand-written report that includes a “Proof of Concept” (PoC)—actual evidence of how they got in—and specific advice on how to fix the hole. Penetration testing reports often include recommendations for remediation efforts to address identified vulnerabilities and ensure security controls remain effective.
- The Pro: It finds the “impossible” bugs that scanners miss, such as business logic errors.
- The Con: It is more expensive and takes more time (usually 1–3 weeks) because it requires high-level human expertise.

The Key Differences Every Founder Should Know
1. Logic vs. Code
A scanner can tell you if your version of "Linux" is outdated. It cannot tell you that your "Add to Cart" button allows a user to change the price of an item to $0.00. A penetration tester will find that business logic flaw immediately.
2. Breadth vs. Depth
Vulnerability scans are “a mile wide and an inch deep.” They check every single corner of your network for basic flaws. These scans are often scheduled as periodic scans—conducted weekly, monthly, or quarterly—to maintain ongoing security and keep up with evolving threats. Some scanning methods are non intrusive, passively monitoring network traffic without disrupting system operations. Penetration tests are “an inch wide and a mile deep.” The tester picks a target (like your web app) and goes as deep as possible to see what damage a real hacker could do.
3. False Positives
Scanners are notorious for "crying wolf." They often flag things that aren't actually dangerous, leaving your developers to waste hours investigating non-issues. A penetration test report is verified; if it’s in the report, it’s a real, exploitable problem.
4. Compliance and Trust
If you are trying to close a deal with a Fortune 500 company or get SOC2/ISO 27001 certified, a simple scan usually isn’t enough. Most enterprise partners want to see a Manual Penetration Test report to prove that a human has verified your defenses.
Regulatory compliance standards, such as PCI DSS, often require organizations to conduct regular vulnerability scans and penetration tests to ensure data security and protect sensitive information. Meeting these requirements is essential for maintaining compliance and building trust with customers and partners.
Application Security Best Practices for Startups
For startups, building secure applications isn’t just about checking a box: it’s about protecting your business, your users, and your reputation from ever-evolving cybersecurity threats. The most effective approach to application security combines proactive vulnerability scanning, targeted penetration testing, and a strong vulnerability management process to stay ahead of potential attackers. Here’s how you can put these best practices into action:
- Integrate Vulnerability Scanning into Your Development Pipeline: Use automated scanning tools to regularly check your code, web applications, and infrastructure for known security weaknesses. By running vulnerability scans as part of your CI/CD process, you can quickly identify vulnerabilities before they reach production, reducing the risk of exposing sensitive data.
- Schedule Regular Penetration Testing: While automated scans catch common vulnerabilities, periodic penetration testing by security experts uncovers deeper, more complex security weaknesses that automated tools might miss. Penetration testing simulates real-world attacks, helping you identify and fix potential weaknesses before they can be exploited.
- Establish a Continuous Vulnerability Management Program: Don’t treat security as a one-time event. Implement a vulnerability management process that includes tracking, prioritizing, and remediating security issues as they arise. This ongoing effort ensures that new vulnerabilities—whether from unpatched software, third-party vendors, or changes in your application—are addressed promptly.
- Educate Your Team on Secure Coding Practices: Application security starts with your developers. Provide regular training on how to avoid common security pitfalls like SQL injection, cross-site scripting, and improper authentication. Empower your team to identify and fix security gaps early in the development cycle.
- Monitor for New and Emerging Threats: Stay informed about the latest cybersecurity threats and updates to the common vulnerability scoring system (CVSS). Subscribe to security advisories and leverage threat intelligence to adapt your security strategy as new risks emerge.
- Document and Test Your Security Policies: Create clear security policies and procedures for your team, and test them regularly. This not only helps you meet compliance requirements like SOC 2 or ISO 27001, but also ensures everyone knows how to respond to potential security incidents.
By following these application security best practices, startups can build a strong foundation to identify vulnerabilities, address security weaknesses, and protect their digital assets from potential threats—without slowing down innovation.
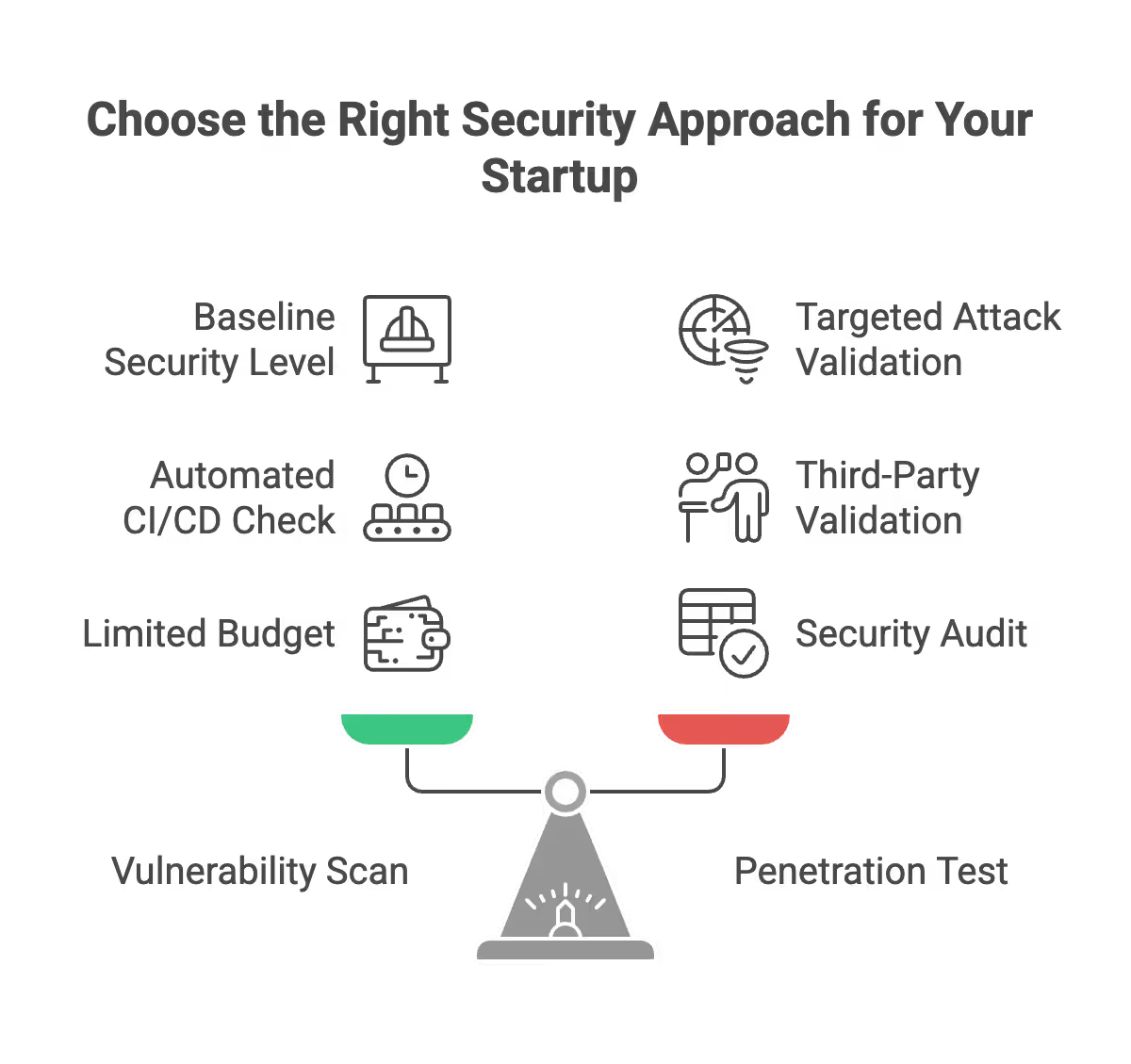
Which One Does Your Startup Need?
You need a Vulnerability Scan if:
- You want to maintain a “baseline” level of security.
- You are shipping code daily and want an automated check in your CI/CD pipeline.
- You have a very limited budget but want to catch “low-hanging fruit” vulnerabilities.
- Small businesses and startups often choose vulnerability scanning because limited resources and IT staff make it a practical first step for identifying and managing security risks.
You need a Penetration Test if:
- You are about to launch a major new product or feature.
- You are going through a security audit (SOC2, HIPAA, PCI).
- You are selling to enterprise customers who require a third-party security validation.
- You want to ensure your “crown jewels” (customer data) are actually safe from a targeted attack.
- Penetration testing is essential for organizations seeking to validate remediation of vulnerabilities and to strengthen overall network security.
The Bottom Line
For most startups, it’s not an “either/or” situation. The most successful security strategy is to automate the boring stuff with regular vulnerability scans and bring in the experts for a penetration test once or twice a year. While vulnerability scans are effective at identifying known vulnerabilities, they may miss unknown vulnerabilities, such as zero-day exploits, that require expert analysis to uncover.
By combining the speed of automation with the intuition of a human hacker, you can protect your company’s reputation and focus on what you do best: building your product. This combined approach also helps safeguard sensitive information from both common and emerging threats.
FAQ for Vulnerability scan vs Penetration testing
What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is an automated check for known security holes while penetration testing is a manual assessment by a human expert. Scanning offers a broad overview and pentesting provides a deep simulation of real world attacks.
Does SOC 2 compliance require penetration testing?
Most enterprise partners and auditors expect a manual penetration test report to verify your security controls. Human verification is often necessary to achieve SOC 2 or ISO 27001 certification.
Can automated scanners find business logic flaws?
No, automated tools usually cannot detect logic errors like unauthorized access to user data through application bugs. Only a human penetration tester can identify these complex and creative security weaknesses.
How frequently should startups run vulnerability scans?
Startups should run automated scans weekly or even daily by integrating them into the development pipeline. This helps catch basic security weaknesses quickly before they reach production servers.
When is a penetration test better than a vulnerability scan?
A penetration test is better when preparing for a major product launch or satisfying requirements for large enterprise customers. It provides a higher level of trust by proving that your systems can withstand a targeted manual attack.