In the modern cybersecurity landscape, maintaining a “secure” network is no longer a static goal. It is a continuous, dynamic process of testing, defending, and evolving. To achieve this, organizations rely on two primary specialized groups: the Red Team and the Blue Team.
The Red Team and Blue Team are specialized groups within the broader cybersecurity team, which collectively works to identify vulnerabilities and enhance organizational security.
While they operate with opposing objectives, their ultimate goal is the same: to harden an organization’s security posture. This article explores the fundamental differences between these roles, their methodologies, and how their collaboration creates a more resilient defense.

Introduction to Cybersecurity Teams
In today’s threat landscape, cybersecurity teams are the backbone of an organization’s defense strategy. The two primary groups,red and blue teams, work in tandem to protect against a wide range of cyber threats.
The red team, made up of offensive security experts, takes on the role of simulated adversaries, probing for weaknesses and testing the limits of an organization’s defenses.
On the other side, the blue team consists of defensive security professionals who are dedicated to safeguarding systems, detecting intrusions, and responding to attacks in real time.
But the evolution doesn’t stop there. Enter the purple team: a collaborative approach that combines the strengths of both red and blue teams. Rather than working in silos, the purple team fosters knowledge sharing, allowing offensive and defensive experts to learn from each other and adapt quickly to new threats.
This synergy is essential for organizations aiming to elevate their security posture and stay ahead of attackers. By understanding how red and blue teams operate, and how the purple team combines their expertise, businesses can build a more resilient and adaptive cybersecurity program.
The Red Team: The Offensive Security Mindset
The Red Team consists of independent security professionals or ethical hackers who act as adversaries. Their primary mission is to challenge an organization’s security effectiveness by simulating real-world cyberattacks, utilizing penetration testing and red team exercises as key methods to identify and exploit vulnerabilities.
Core Objectives
- Identify Vulnerabilities: Find technical, physical, or human weaknesses that could be exploited.
- Simulate Real Threats: Use the same "Tactics, Techniques, and Procedures" (TTPs) as actual malicious actors.
- Test Detection Capabilities: Determine if the organization’s defensive tools and personnel can actually spot a breach in progress.
Common Tactics
Red teams don’t just look for software bugs; they look for any way in. This includes:
- Social Engineering: Phishing emails or "vishing" (voice phishing) calls to trick employees.
- Physical Penetration: Attempting to gain access to server rooms or offices.
- Exploitation: Using tools like Metasploit or SQLMap to bypass security controls and access "crown jewel" data.
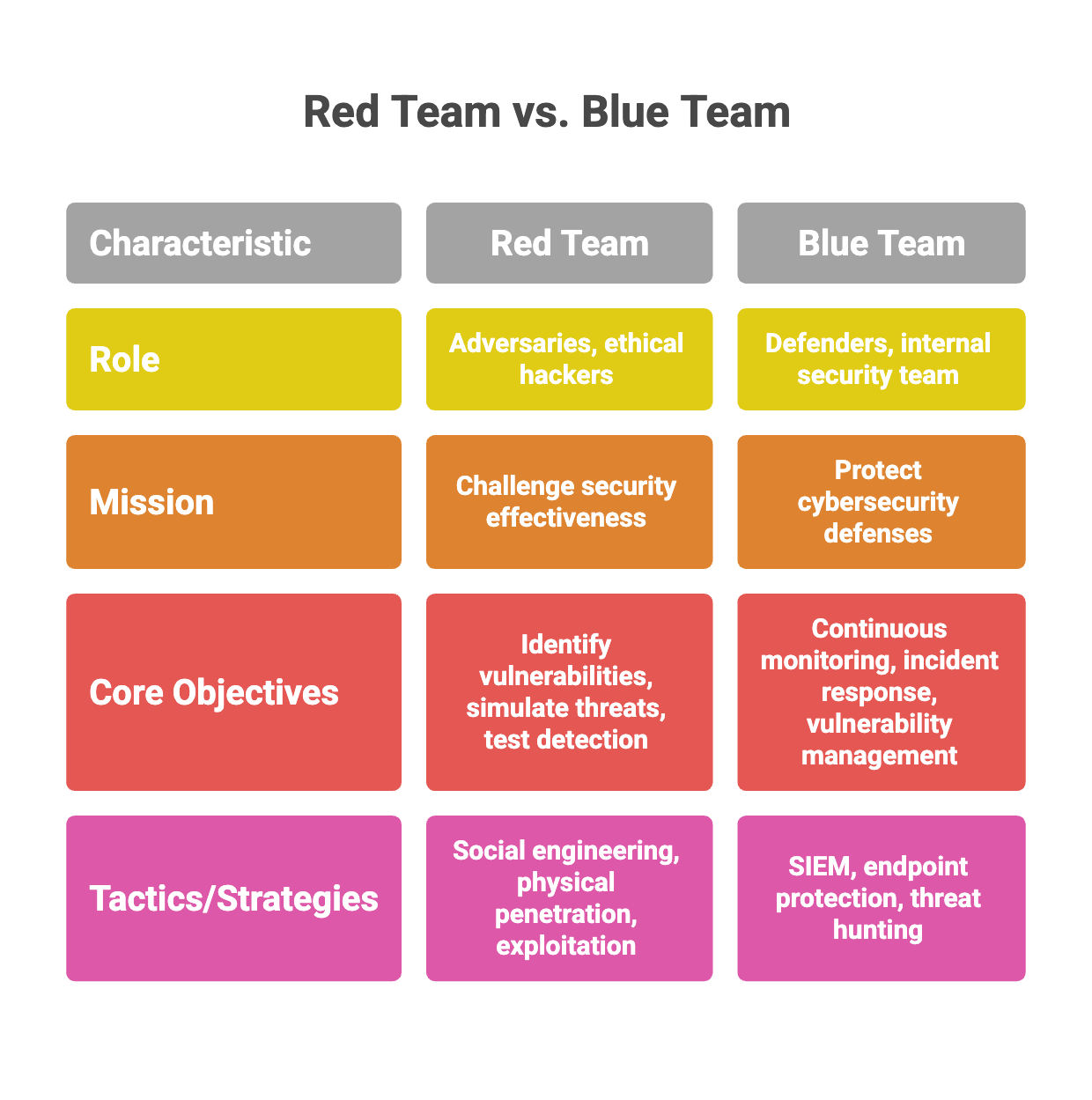
The Blue Team: The Defensive Security Professionals' Shield
The Blue Team is the internal security team responsible for maintaining the organization’s defenses through comprehensive blue team operations and blue team tasks such as incident response, threat hunting, and risk assessment.
They are the frontline responders who monitor, detect, and mitigate threats daily.
Blue Teams are responsible for managing security incidents and ensuring the integrity of security systems. As part of their role in protecting the organization's cybersecurity defenses, Blue Teams also deploy and manage security software, including endpoint protection, intrusion detection systems, and anti-malware tools.
Core Objectives
- Continuous Monitoring: Analyzing network traffic and system logs for any sign of "anomalous" behavior.
- Incident Response: Reacting quickly to security breaches to minimize damage and restore operations.
- Vulnerability Management: Ensuring systems are patched, MFA (Multi-Factor Authentication) is active, and firewalls are correctly configured.
Defensive Strategies
Blue teams focus on visibility and resilience. Their toolkit often includes:
- SIEM (Security Information and Event Management): Software that aggregates logs to provide real-time alerts.
- Endpoint Protection (EDR): Monitoring individual devices for signs of malware or unauthorized access.
- Threat Hunting: Proactively searching through the network to find hidden threats that haven't triggered an alert yet.
Incident Response
Incident response is at the heart of any effective cybersecurity strategy. When a security incident occurs: whether it’s a data breach, malware infection, or unauthorized access. Blue teams play a pivotal role in managing the situation. These security teams are responsible for quickly detecting threats, analyzing the scope of the incident, and taking decisive action to contain and eradicate the threat.
Incident responders rely on threat intelligence and continuous monitoring to stay ahead of emerging threats. The incident response process typically involves several key steps: identifying the incident, containing its impact, eliminating the root cause, recovering affected systems, and conducting a thorough post-incident review.
This structured approach ensures that organizations can minimize damage, learn from each event, and strengthen their defenses for the future. Effective incident response is a team effort, requiring seamless collaboration between blue teams and other security professionals to protect the organization from evolving cyber threats.
Measuring Success: How Do They "Win"?
When comparing team vs team in cybersecurity, specifically red team vs blue team, it's important to understand how their roles differ in testing and improving security defenses. The red team simulates real-world attacks to identify vulnerabilities, while the blue team is responsible for defending, detecting, and responding to threats to strengthen the organization's defenses.
Because their roles are different, their metrics for success are distinct:
The red team vs blue team dynamic is essential for evaluating the organization's defenses. These team vs blue exercises help strengthen the blue team's defenses and overall security defenses by exposing gaps and enabling continuous improvement.
The Phases of a Joint Exercise
When a Red Team conducts a “Red Teaming” engagement against a Blue Team, it typically follows a structured lifecycle. Joint exercises involve both blue and red teams working together to test and improve enterprise security:
- Reconnaissance & Planning: The Red Team gathers intelligence (OSINT) about the target. This phase also includes a thorough risk assessment and evaluation of the organization's infrastructure, focusing on network security, critical assets, and adherence to data and industry standards. A “White Team” (referees) sets the rules of engagement to ensure the test doesn’t cause actual business downtime.
- The Attack: The Red Team attempts to infiltrate the network. They might start with a simple phishing link and move laterally through the network to gain administrative privileges.
- The Response: The Blue Team attempts to identify the intrusion. Do their alerts fire? Does the incident response plan work? Can they “kick” the attacker out before they reach the data? Blue team exercises such as incident response, threat hunting, and security automation are critical in this phase to strengthen defenses.
- Debrief & Remediation: This is the most critical phase. Both teams meet to compare timelines. The Red Team shows how they got in, and the Blue Team explains why they did (or didn’t) see it. Both teams review the security techniques used, identify security gaps, and assess the organization's security posture to guide future improvements.
Red team exercises and blue team exercises are essential for continuous improvement, helping organizations align with industry standards and enhance their overall cybersecurity defenses.

Breach and Attack Simulation
Breach and attack simulation (BAS) has emerged as a powerful tool for organizations seeking to proactively test and strengthen their cybersecurity defenses. BAS platforms enable security teams to safely simulate real-world attack techniques within production environments, providing a continuous, automated way to identify vulnerabilities and gaps in security controls.
For red teams, BAS offers repeatable attack scenarios that mimic the tactics of real adversaries, making it easier to assess how well an organization’s defenses hold up under pressure. Blue teams benefit by gaining insights into which threats evade detection, allowing them to fine-tune their response capabilities and improve threat detection. Purple teams, which combine the expertise of both red and blue teams, use BAS to accelerate the cycle of attack, observation, remediation, and re-testing—driving measurable improvements in security posture. By continuously validating security controls and automating security testing, breach and attack simulation empowers organizations to keep pace with attackers and scale their defenses efficiently.
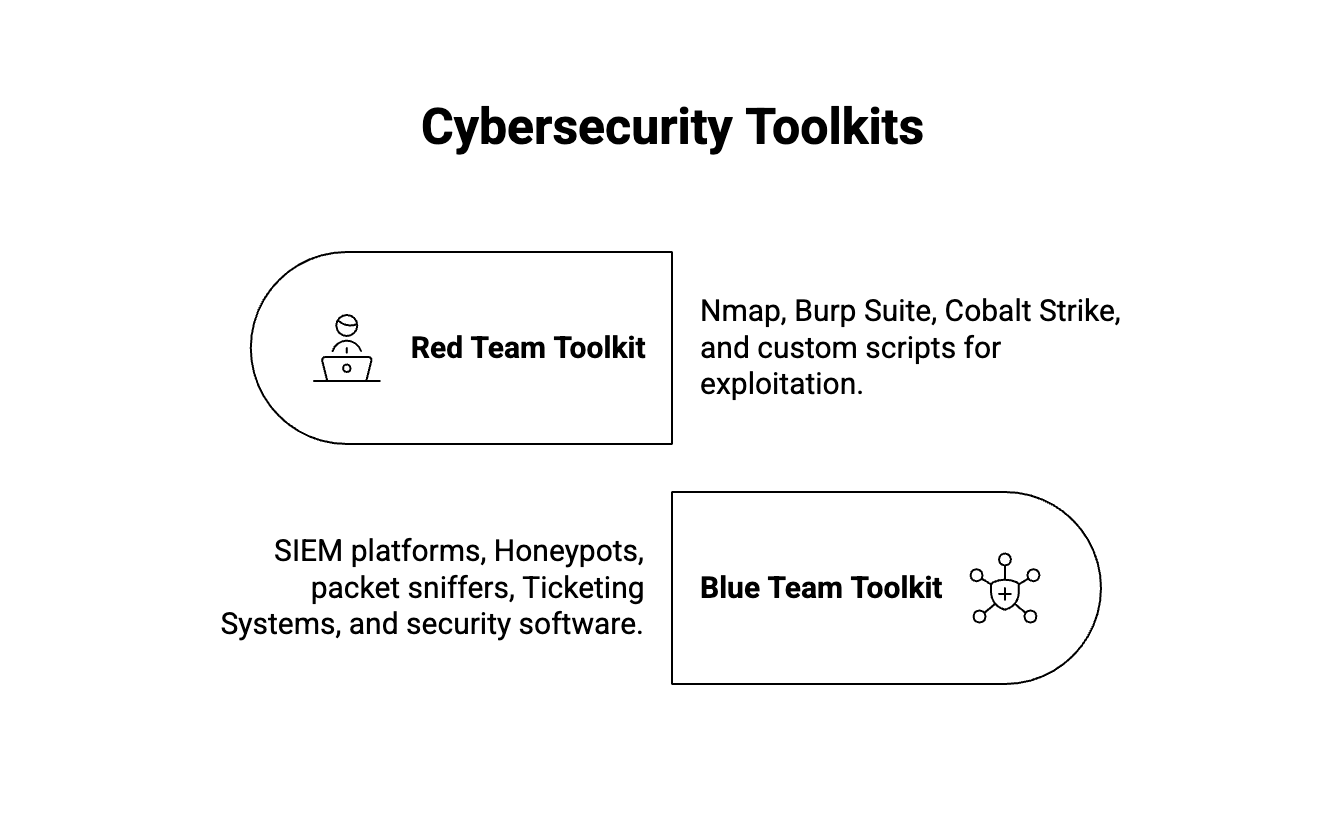
Tools of the Trade
- Red Team Toolkit: Nmap (network scanning), Burp Suite (web application testing), Cobalt Strike (adversary simulation), and various custom scripts for exploitation (often requiring advanced software development skills for coding and automation).
- Blue Team Toolkit: SIEM platforms (like Splunk or ELK), Honeypots (decoy systems to lure attackers), packet sniffers (Wireshark), Ticketing Systems to track and resolve vulnerabilities, and security software such as anti-malware tools and intrusion detection systems for threat mitigation.
Common Challenges
Despite their unique roles, red and blue teams often face similar challenges that can hinder their effectiveness. Limited staffing, overwhelming alert volumes, and the ever-expanding attack surface make it difficult for security teams to keep up with the pace of modern threats. The sheer number and complexity of security tools can also obscure true defensive effectiveness, making it challenging to identify and address security weaknesses.
One of the most significant hurdles is the lack of continuous validation—without regular, realistic testing, organizations may not know if their defenses are truly effective. Purple teaming helps bridge this gap by integrating red and blue teams, fostering real-time collaboration, and enabling continuous improvement of security measures. By working together, red and blue teams can overcome these common obstacles and build a more robust defense against cyber threats.
The "Purple" Synergy
The ultimate evolution of this dynamic is known as a Purple Team. A Purple Team isn’t necessarily a new department; rather, it is a mindset of total collaboration. Instead of the Red Team operating in secret and the Blue Team operating in a vacuum, the two teams work side-by-side. During purple team exercises, blue teams collaborate with red teams to enhance the organization's cybersecurity defenses by jointly identifying and addressing security gaps.
In a Purple Team exercise, the Red Team explains an attack while they are doing it, allowing the Blue Team to adjust their sensors and detection logic in real-time. Blue teams share insights with red teams throughout these exercises to improve detection and response strategies, creating a feedback loop that accelerates security improvements far faster than traditional, siloed testing.
Future of Cybersecurity
Looking ahead, the future of cybersecurity will be defined by adaptability, collaboration, and innovation. As cyber threats become more sophisticated, security teams must leverage advancements in artificial intelligence, machine learning, and automation to stay ahead of attackers. The integration of red, blue, and purple teams will be crucial, as knowledge sharing and joint exercises help identify vulnerabilities and drive continuous security improvements.
Key areas such as cloud security, endpoint protection, and identity and access management will remain central to defending against emerging threats. Organizations that invest in their security teams, embrace new technologies, and prioritize ongoing training will be best positioned to strengthen their security posture. Proactive strategies—rooted in continuous monitoring, threat intelligence, and robust incident response—will be essential for navigating the evolving threat landscape. By fostering collaboration between red, blue, and purple teams, organizations can build resilient defenses and ensure long-term cybersecurity success.
FAQ for Red Team Vs Blue Team
What is the difference between a Red Team and a Blue Team?
Red Teams use offensive tactics to simulate real-world attacks and find vulnerabilities in a network. Blue Teams focus on defensive strategies like continuous monitoring and incident response to protect the organization.
What is a Purple Team in cybersecurity?
A Purple Team is a collaborative approach where offensive and defensive teams work together to share real-time feedback. This cooperation helps close security gaps and improves detection logic much faster than working in silos.
How does a Blue Team measure its success?
Success is measured by metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR). They also focus on the accuracy of alerts and the improvement of security configurations over time.
What is Breach and Attack Simulation?
Breach and Attack Simulation or BAS uses automated platforms to safely test security controls against common attack techniques. It allows teams to continuously validate their defenses without causing business downtime.
What tools are commonly used in Red Team exercises?
Red Teams frequently use tools like Nmap for scanning, Burp Suite for web testing, and Cobalt Strike for adversary simulation. They also develop custom scripts to exploit technical or human weaknesses.