Author: Marçal Santos, vCISO | +20 Years Cybersecurity Experience
Key Takeaways
- A SOC 2 bridge letter (also called a gap letter) is a short, management-signed memo that covers the period after your last SOC 2 Type II report end date up to a customer’s fiscal year end or the current date—typically spanning up to three months.
- The bridge letter does NOT replace a SOC 2 report; it simply states whether there have been any material changes in your control environment since the last report and provides temporary coverage until your next audit.
- The letter is written and signed by the service organization’s leadership (CEO, CFO, or CTO), not your CPA firm, and sophisticated customers will routinely ask for it during vendor due diligence.
- A clear, one-page bridge letter can prevent deal delays and repeated security questionnaires, especially when your SOC 2 report period ends before a customer’s year end.
- Aligning your audit timing and adopting continuous compliance practices can reduce how often you need bridge letters, but will rarely eliminate them entirely for growing SaaS vendors.
If you’re a CEO or CTO and someone from a customer’s security team just asked you for a “SOC2 bridge letter,” you’re not alone in wondering what that means. This request tends to catch first-time recipients off guard, especially when you’ve already invested significant time and resources into completing your SOC 2 audit.
The good news? Responding to this request is straightforward once you understand what’s being asked and why. This guide will walk you through everything you need to know—from the basics of what a bridge letter is, to a ready-to-use template structure you can adapt for your organization.

What Is a SOC 2 Bridge (Gap) Letter?
A SOC 2 bridge letter is a management letter that “bridges” the gap from the end date of your most recent SOC 2 report to a later date when your customer needs assurance. Think of it as a short memo that says, “Here’s what’s happened (or hasn’t happened) with our security controls since our last audit ended.”
This applies specifically to SOC 2 Type II reports, which cover 6–12 months of operating effectiveness for your security controls. Customers often request bridge letters when their organization’s fiscal year end (say, December 31) extends beyond your SOC report period (which might end September 30).
The letter states whether your internal control environment and key security, availability, processing integrity, confidentiality, and privacy controls have materially changed since your most recent SOC 2 report. It confirms that controls have been operating effectively to the best of management’s knowledge.
Here’s the important caveat: this assurance is “unverified.” There’s no new auditor testing involved. The bridge letter is a management representation, which means it carries less weight than your audited SOC 2 report.
While bridge letters can technically be used for SOC 1 or SOC 3 (system and organization controls reports focused on different criteria), this article focuses on SOC 2 because that’s what most SaaS CEOs and CTOs encounter when selling to enterprise customers.
Why Organizations Need SOC 2 Bridge Letters
If you’re suddenly being asked for a bridge letter, you’re probably wondering: why wasn’t my SOC 2 report enough?
The answer comes down to timing misalignment. Your SOC 2 report covers a fixed audit period—for example, October 1, 2023, through September 30, 2024. But your customer’s internal auditors and risk teams operate on their own reporting period, which rarely lines up perfectly with yours. This creates a coverage gap of one to three months that needs to be addressed.
Here are the most common scenarios where bridge letters become essential:
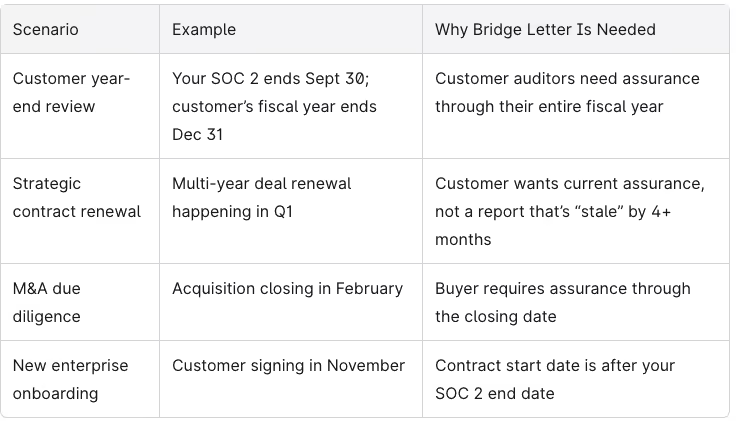
While not mandated by the AICPA, issuing bridge letters is widely considered best practice. It signals maturity, transparency, and a continuous focus on security—exactly what enterprise customers want to see from their service providers.
When Is a SOC 2 Bridge Letter Typically Requested?
Understanding the timing of these requests can help you anticipate them and avoid friction in your sales cycles.
Concrete timing example: Your SOC 2 Type II report covers October 1, 2023, through September 30, 2024. A Fortune 500 customer’s fiscal year end is December 31, 2024. Their procurement team asks for a bridge letter covering October 1 through December 31, 2024, so they can assure customers and their own auditors that your controls remained effective through their entire fiscal year.
Here are the most common triggers for bridge letter requests:
- Audit timeline delays: Your scheduled audit gets pushed back due to auditing firm capacity, scope expansion (new products or regions), or internal readiness issues, extending the gap between the last audit period and the next one.
- Q4 vendor reassessments: Procurement and vendor risk teams often trigger requests as part of annual vendor re-assessment workflows, particularly for critical or high-risk SaaS providers. Expect a spike in requests during October through December.
- Contract negotiations: New customers sometimes request a bridge letter immediately during onboarding if they’re signing a contract late in your SOC 2 coverage period. They want assurance that controls were operating effectively up to their contract start date.
- User entity audit requirements: When your customer (the user entity) undergoes their own audit, their auditors may require bridge letter coverage for all critical vendors whose SOC report period doesn’t match.
Key Components of a SOC 2 Bridge Letter
Think of this section as your checklist. There’s no official AICPA template for bridge letters, but most SOC 2 bridge letters contain a consistent set of essential elements that customer auditors expect to see.
The Must-Have Elements
1. Reference to Your Most Recent SOC 2 Report
- Report type (SOC 2 Type II)
- Scope (which systems and applicable trust services criteria were covered)
- SOC report period with beginning and end dates (e.g., “January 1, 2024 through September 30, 2024”)
- Name of the CPA firm that performed the SOC examination
2. Clear Bridge Period Coverage
- Specific dates covered by the bridge letter (e.g., “October 1, 2024 through December 31, 2024”)
- The current date when the letter is being signed
- Statement that this is the interim period between report issuance and the next audit
3. Statement About Material Changes
- Explicit confirmation of whether there have been significant changes to the organization’s control environment
- If there have been no material changes, state this clearly
- If there HAVE been changes, briefly describe them
4. Confirmation of Control Effectiveness
- Statement that security controls have continued to operate as designed
- Reference to the organization’s systems and organization’s processes
- Affirmation that the prior report’s findings still accurately reflect the current control environment
If Material Changes Did Occur
If your organization completed a major system migration, changed cloud providers, experienced leadership turnover in security roles, or made other significant changes, your bridge letter must describe them. Include:
- What changed
- When it changed
- What compensating controls were implemented
- Why you believe controls remain effective despite the change
Required Disclaimers
Every bridge letter should include a paragraph making it clear that:
- This is NOT a SOC 2 report
- It does not include independent assessment or auditor testing
- It is intended solely for the named customer
- It should be read in conjunction with the underlying SOC 2 report
- It provides reasonable assurance based on management’s knowledge, not an independent assessment
5. Signatures and Contact Information
- Printed on company letterhead
- Dated as of the signature date
- Signed by senior executives (CEO, CFO, CTO, or CISO)
- Contact information for follow-up questions

Who Issues and Signs the SOC 2 Bridge Letter?
Here’s a common misconception: your CPA firm issues the bridge letter. They don’t.
The service auditor’s responsibility ends at the audit period end date. They cannot attest to controls after that date without performing another examination. Your auditor might consult on the letter’s language, but they won’t sign it or take responsibility for its contents.
The bridge letter is a management representation. It is authored and owned by your organization, typically drafted by your security or compliance team and reviewed by legal before signature.
Who Should Sign?
Signatures should come from senior leadership with direct responsibility for the organization’s control environment:
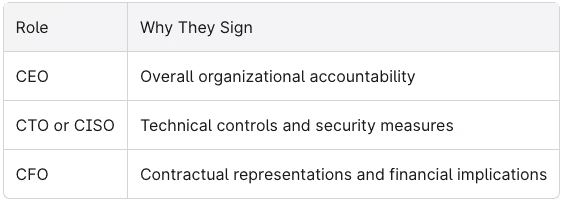
Most bridge letters include one or two signatures. Some organizations use all three for maximum credibility with enterprise customers.
Include a designated contact (e.g., “VP, Security & Compliance”) with an email address for follow-up questions from customer auditors. This shows you’re prepared and professional.
How Long Can a SOC 2 Bridge Letter Cover?
Customers and auditors are generally comfortable only with short, defined gaps—not open-ended assurances.
The standard: up to three months. Most bridge letters cover no more than 90 days. For example, if your last audit period ended September 30, 2024, a bridge letter covering October 1 through December 31, 2024, falls within acceptable limits.
Why the three-month limit? The further you get from the last report date, the less reliable a management-only representation becomes. Controls can drift. Personnel can change. Systems can be modified. Without ongoing auditor verification, there’s only so much assurance management can provide customers.
What If Your Gap Exceeds Three Months?
If you’re looking at a gap longer than 90 days, consider these alternatives:
- Accelerate your next scheduled audit timeline
- Adjust future audit cycles to better match major customers’ year ends
- Consider a “point-in-time” SOC 2 Type I report to provide assurance during an extended gap
Your bridge letter should always clearly state the “as of” date (e.g., “as of December 31, 2024”) so customers understand exactly how current the information is. A bridge letter valid beyond three months will raise questions with sophisticated customer audit teams.
Limitations and Risks of Relying on SOC 2 Bridge Letters
Before you start issuing bridge letters, understand what they can and cannot do. This isn’t about discouraging you—it’s about helping you avoid over-promising or treating the bridge letter as a substitute for strong security practices.
What a Bridge Letter Is NOT
- It’s not an audit. There’s no independent verification or testing of controls.
- It doesn’t include detailed findings. You won’t find test procedures, exceptions, or auditor opinions.
- It only reflects a point in time. Management’s knowledge is current only as of the signature date.
- It can’t guarantee future effectiveness. Controls may change after the letter is signed.
The Real Risks
Legal and reputational exposure: If a breach or control failure occurred during the gap period and was not disclosed, the bridge letter can become a focal point in customer disputes or regulatory reviews. Your bridge letter stating “no material changes” while knowing otherwise creates serious liability.
Customer trust erosion: If undisclosed material changes emerge later—whether through a breach, a failed audit, or customer discovery—your credibility with that customer (and potentially the market) takes a significant hit.
The bridge letter is only as reliable as your internal monitoring and incident detection processes. Before signing, make sure you can confidently state “no material changes” or accurately describe any that did occur.
Practical Steps: How to Prepare and Respond
This section is your mini playbook for handling bridge letter requests—especially if this is your first time.

Step 1: Establish Internal Ownership
Create a clear RACI for bridge letter requests:
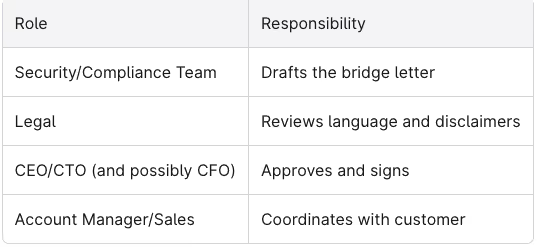
Step 2: Maintain a Change Log
From the moment your SOC 2 report period ends, start tracking:
- System architecture changes
- New vendors or subprocessors
- Security incidents (if any)
- Policy or procedure updates
- Personnel changes in key security roles
- Infrastructure migrations or significant upgrades
This log becomes your source of truth when drafting the “material changes” section of your bridge letter.
Step 3: Standardize Your Templates
Create two vetted bridge letter templates:
- No material changes version: For when nothing significant changed during the gap period
- Material changes version: For when you need to summarize and explain changes
Having these ready means you can respond to customer requests within days, not weeks.
Step 4: Align Future Audit Timing
If you’re repeatedly getting bridge letter requests because your SOC 2 ends in June but your biggest customers’ fiscal year ends in December, consider adjusting your audit period. Moving from a July–June period to an October–September period might better serve your customer base.
Step 5: Supplement When Necessary
For critical, regulated, or highly risk-sensitive customers, you may need to supplement the bridge letter with:
- Updated penetration test summaries
- Incident reports (if applicable)
- Updated security policies
- Evidence of specific controls operating effectively (access reviews, etc.)
Example Bridge Letter Structure
Below is a structure you can adapt for your own organization. This should be a one-page document on company letterhead with professional but accessible language.
[COMPANY LETTERHEAD]
SOC 2 Bridge Letter for [Your Company Name]
Date: [Current Date]
To: Security and Risk Management Teams at [Customer Name]
Reference to Most Recent SOC 2 Report:
[Your Company Name] (“the Company”) completed a SOC 2 Type II examination for the period [Beginning Date] through [End Date], performed by [Audit Firm Name]. A copy of this report has been provided to [Customer Name] separately / is attached hereto.
Bridge Period Coverage:
This bridge letter covers the period from [First Day After SOC 2 End Date] through [Current Date or Customer’s Fiscal Year End].
Statement Regarding Material Changes:
Option A (No Material Changes): Management confirms that there have been no material changes to the Company’s internal control environment, security controls, or organization’s systems since the last report referenced above. The controls described in the SOC 2 report have continued to operate as designed throughout the interim period.
Option B (Material Changes Occurred): Management notes the following significant changes since the dates covered by the referenced SOC 2 report:
- [Brief description of change #1 and compensating controls]
- [Brief description of change #2 and compensating controls]
Despite these changes, management believes the organization’s control environment continues to provide reasonable assurance regarding [security/availability/confidentiality/processing integrity/privacy] based on the applicable trust services criteria.
Disclaimers:
This letter is not a SOC 2 report and does not include independent auditor testing or an independent assessment of the Company’s controls. This letter is a management representation and should be read in conjunction with the Company’s SOC 2 Type II report. This letter is provided solely for the use of [Customer Name] and is not intended for general distribution.
Contact for Questions:
[Name, Title, Email Address]
Signatures:
[Name] Chief Executive Officer [Date]
[Name] Chief Technology Officer / Chief Information Security Officer [Date]
FAQs About SOC 2 Bridge Letters
What is a SOC 2 bridge letter?
It is a management-signed memo stating whether material changes occurred in your security controls since the last SOC 2 report ended. It bridges the gap between your audit end date and a customers fiscal year end or current date.
Who signs a SOC 2 bridge letter?
Senior leadership such as the CEO, CFO, or CTO must sign the letter to attest to the control environment. The CPA firm or external auditor does not sign or issue this document.
How long is a SOC 2 bridge letter valid?
Most customers and auditors accept a bridge letter coverage period of up to 3 months or 90 days. Gaps longer than this usually require a new audit or a point-in-time report to provide sufficient assurance.
What happens if material changes occurred during the gap period?
You must explicitly describe the changes, when they happened, and the compensating controls in the bridge letter. You cannot state there were no material changes if significant system updates or incidents occurred.
Is a SOC 2 bridge letter mandatory?
No, neither the AICPA nor regulators require bridge letters. However, many enterprise customers make them a contractual or policy requirement when a SOC 2 report doesn’t fully cover their organization’s fiscal year end. For practical purposes, if a major customer asks for one, you need to provide it.
Can we reuse the same bridge letter for multiple customers?
The core content can be templated, but each letter should be dated accurately, reflect the specific coverage period, and ideally be addressed to a specific customer. This prevents unintended reliance by third parties and shows customers you’re taking their specific request seriously.
What if there was a security incident during the gap period?
You cannot issue a “no material changes” letter if a significant incident occurred. Instead, briefly describe the incident, the remediation steps taken, and why you believe controls remain effective. Consider involving legal counsel to help with the wording, particularly for incidents that may have contractual or regulatory implications.
Will some customers reject a bridge letter and insist on a fresh SOC 2 report?
Yes, a minority of high-risk or highly regulated customers may require a report that covers their full fiscal year. Understand these requirements early in the deal cycle so sales and leadership can plan accordingly. Some organizations maintain multiple SOC 2 audit cycles for this reason.
How often should we plan to issue bridge letters each year?
Most growing SaaS companies see requests around quarter-ends and especially at calendar year-end. A realistic planning assumption is to handle several requests per year until your audit cycles and major customers’ requirements are better aligned. Maintaining good templates and a running change log makes this manageable.
What is SecureLeap and How We Can Help with Your SOC 2 Needs
SecureLeap is a trusted provider of comprehensive SOC 2 compliance solutions designed to help organizations navigate the complexities of SOC 2 audits and bridge letter requirements. We specialize in guiding service organizations through every step of the SOC 2 process, ensuring continuous compliance and minimizing the need for gap letters.
If you need assistance with preparing your SOC 2 bridge letter, aligning your audit timelines, or managing your overall SOC 2 compliance program, SecureLeap is here to help. Our team of experts offers tailored support to meet your unique business needs, helping you maintain trust with your customers and streamline your audit processes.
Contact SecureLeap today to learn more about how we can support your SOC 2 compliance journey and provide peace of mind to your stakeholders.






