Most organizations often feel a false sense of security provided by automated vulnerability scanners. While these tools are excellent at catching low-hanging fruit and identifying common vulnerabilities such as SQL injection or XSS, they are consistently blind to one of the most damaging classes of vulnerabilities: Business Logic Flaws.
Modern applications introduce new challenges for security, as their complexity and dynamic features can create unexpected opportunities for attackers.
There are many possible scenarios that can lead to business logic flaws, including misinterpretation of requirements, complex interactions, and unanticipated usage that developers may overlook during the design and implementation process.
The Nature of the Flaw
Business logic vulnerabilities are not about breaking the code; they are about subverting the intent of the code, often resulting in unintended behavior that arises from flawed logic. These flaws manifest when an application fails to anticipate unusual user behavior or malicious sequences of actions.
For example, consider a multi-step password reset process. If a developer assumes a user will always go from Step 1 to Step 2 to Step 3, they might fail to validate the user’s identity at Step 3.
An attacker can “skip” the verification steps and jump directly to the final stage to reset a victim’s password. Technically, the code for the final stage works perfectly, but the logic governing the workflow is broken. Flaws in the design or implementation of such functions can lead to vulnerabilities that attackers may exploit. Secure implementation practices are essential to avoid these issues.
When designing workflows, user interactions and operations must be carefully considered to prevent logic flaws. Attackers, or even regular users, can exploit these flaws, either intentionally or unintentionally, if the application does not properly validate and manage all possible behaviors.
The Business Logic Layer
The business logic layer is the heart of any modern application, orchestrating the rules, workflows, and processes that define how the application operates. Acting as the bridge between the user-facing presentation layer and the underlying data access layer, the business logic layer encapsulates the essential business rules and operational logic that drive core functionality. This is where critical decisions are made, such as how transactions are processed, how user actions are validated, and how sensitive data is handled.
In many applications, the business logic layer is designed as a separate module, following the principle of separation of concerns. This modular approach not only enhances maintainability and scalability but also allows developers to update business rules without disrupting the user interface or data storage mechanisms. However, this separation can also introduce unique security challenges. If the business logic layer is not carefully implemented and validated, it can become a prime target for attackers seeking to exploit logic vulnerabilities.
Business logic vulnerabilities arise when attackers manipulate the intended functionality of an application, taking advantage of flawed logic or gaps in business rules to perform unauthorized actions. Unlike technical flaws such as SQL injection or cross-site scripting, business logic vulnerabilities are often subtle and context-dependent, making them difficult to detect with automated vulnerability scanners.
Attackers may exploit these weaknesses to bypass controls, gain access to restricted data, transfer funds without authorization, or abuse legitimate functionality in unexpected ways.
Why Automation Falls Short
Automated tools operate on “oracles”, predefined rules of what constitutes a “good” or “bad” response. A scanner knows that a 500 Internal Server Error is a potential sign of a bug, and a script tag in a text field is a sign of XSS.
However, logic is context-dependent. A scanner cannot identify:
- Parameter Tampering: Changing a “discount_percent” hidden field from 10 to 90, especially by manipulating post parameters in HTTP/HTTPS requests.
- Workflow Circumvention: Completing an order without a successful payment callback.
- Resource Exhaustion: Ordering a negative value, such as a negative quantity of items, to receive a credit to a balance.
Because the application returns a “200 OK” status and valid HTML, the scanner assumes the transaction was legitimate.
Robust input validation and careful monitoring of data flows within the application are essential to prevent these types of business logic vulnerabilities.
Common Categories of Business Logic Flaws
- Authentication/Authorization Bypasses: Finding ways to access restricted areas by manipulating cookies, session tokens, or URL parameters that dictate user roles, which can lead to privilege escalation if attackers gain unauthorized higher-level access.
- Integrity Violations: Modifying data during transit (like pricing or shipping addresses) that the server fails to re-validate before the final transaction, putting financial transactions at risk of fraud or theft.
- Sequence Manipulation: Performing actions out of order, such as applying a “first-time user” discount code multiple times by navigating back and forth in the browser history.
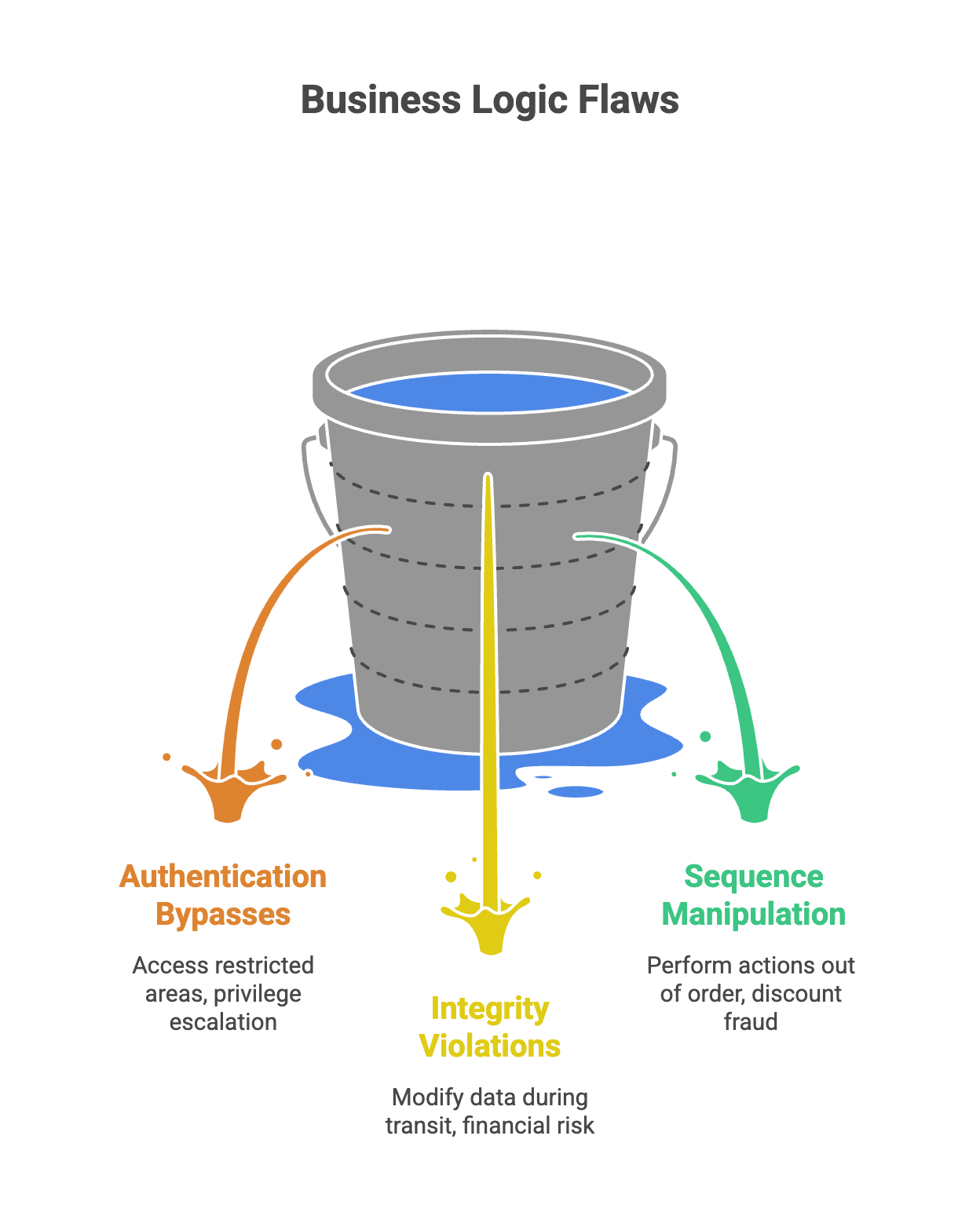
These categories represent potential vulnerabilities that can be exploited through business logic attacks, allowing attackers to compromise the system and bypass intended security controls.
The Role of the Penetration Tester
To find these flaws, a penetration tester must think like a “malicious user” rather than just a “hacker.” This requires a deep dive into the application’s “Abuse Cases” scenarios, where the tester asks, “What happens if I do this out of order?” or “What if I provide a value the developers didn’t expect?”
Testing for BLVs involves:
- Workflow Mapping: Understanding every step of a business process (e.g., the journey from “Add to Cart” to “Delivery”).
- State Tampering: Attempting to modify the application’s “state” across different sessions or roles.
- Manual Verification: Using an intercepting proxy (like Burp Suite) to manually edit every piece of data sent to the server to see how the logic reacts and to identify how attackers might bypass client-side controls and exploit vulnerabilities.
Careful analysis by functional testers is essential for uncovering business logic abuse cases that automated tools often miss. Their expertise in understanding business processes and performing unconventional, logic-based testing helps identify complex vulnerabilities.
Based on the findings from manual testing, it is crucial to implement security controls and develop custom policies, or implement custom policies tailored to the application's specific business logic, to prevent future logic flaws.
Conclusion
As applications become more complex and API-driven, especially across web applications, mobile apps, and services, the surface area for logic errors grows. While automated tools are necessary for baseline security, they are no substitute for the creative, context-aware analysis of a human tester. A secure development process—incorporating thorough planning, design, and quality assurance—plays a critical role in identifying and mitigating business logic flaws early. To truly secure an application, organizations must look beyond the syntax of the code and examine the integrity of the business rules themselves. Only by identifying these “invisible” flaws can a company prevent the significant financial and reputational damage that results from exploited logic, including data breaches. It is essential to implement measures that prevent users from abusing business logic vulnerabilities.
FAQ for Business Logic Flaws
What are business logic flaws?
Business logic flaws are vulnerabilities that arise when an application fails to anticipate unusual user behavior or malicious sequences. These flaws allow attackers to subvert intended workflows rather than breaking code syntax.
Why do automated scanners miss these vulnerabilities?
Scanners rely on predefined rules and cannot understand the specific context of unique business rules. Because logic attacks often return a standard 200 OK status, automated tools assume the transaction is valid.
What is an example of parameter tampering?
An attacker might change a hidden field like a discount percentage from 10 to 90 during an HTTP request. This exploits the failure of an application to re-validate data before the final transaction occurs.
How does a penetration tester find these flaws?
Testers map every step of a business process and attempt to perform actions out of order. They use proxies to manually edit data to see how the logic reacts to unexpected or malicious values.
How can organizations prevent business logic vulnerabilities?
Prevention requires robust input validation and the creation of custom security policies for specific business workflows. Human analysis through manual testing is essential to identify and mitigate these complex risks early.