The core difference between manual and automated penetration testing lies in the battle between human intuition and machine efficiency. Before choosing an approach, it’s important to understand the key differences between automated and manual penetration testing, including their strengths, limitations, and the scenarios where each excels.
Manual penetration testing relies on the creativity and expertise of security professionals to find complex, context-specific vulnerabilities that require critical thinking to exploit. In contrast, automated penetration testing uses software-driven scanners to rapidly identify known flaws, outdated versions, and common misconfigurations across a large surface area. While machines excel at speed and repetition, they lack the “hacker’s mindset” required to chain minor issues into a major breach.
Understanding how these two methods differ is essential for building a robust security posture. When considering penetration test automated vs manual, organizations should weigh their unique needs, resources, and risk tolerance. Both automated and manual penetration testing are used to identify vulnerabilities in systems, applications, and networks, but their approaches differ: automated tools provide broad coverage and efficiency, while manual testing uncovers nuanced, complex issues that automation may miss.
Below, we break down why organizations choose one over the other, the pros and cons of each, and what the best strategy is for a growing startup.
Why People Choose Manual Penetration Testing
Despite the rise of sophisticated AI and scanning tools, manual testing remains the “gold standard” for deep security. Manual testers play a crucial role in complex cybersecurity scenarios, where automated tools may fall short. Skilled testers are able to find nuanced vulnerabilities that automated solutions often miss, making their expertise invaluable for comprehensive security assessments. People choose manual testing because security is rarely about a single broken door; it is often about a series of small, logical oversights that a human can see but a program cannot.
The “human element” allows a tester to understand business logic. For example, an automated tool might find that a website’s login page is secure. However, a manual tester might discover that by changing a single number in the URL after logging in, they can access another user’s private bank account. Because the code itself isn’t “broken” (it’s doing what it was told), a scanner won’t flag it as a vulnerability. A human, however, recognizes the privacy violation immediately. Ethical hackers and security experts use manual penetration testing methods to uncover vulnerabilities that automated tools overlook, relying on human expertise to identify subtle flaws in complex systems.
Manual penetration testing also provides detailed reports with actionable insights, helping organizations understand their security gaps and prioritize remediation.

Comparing the Solutions
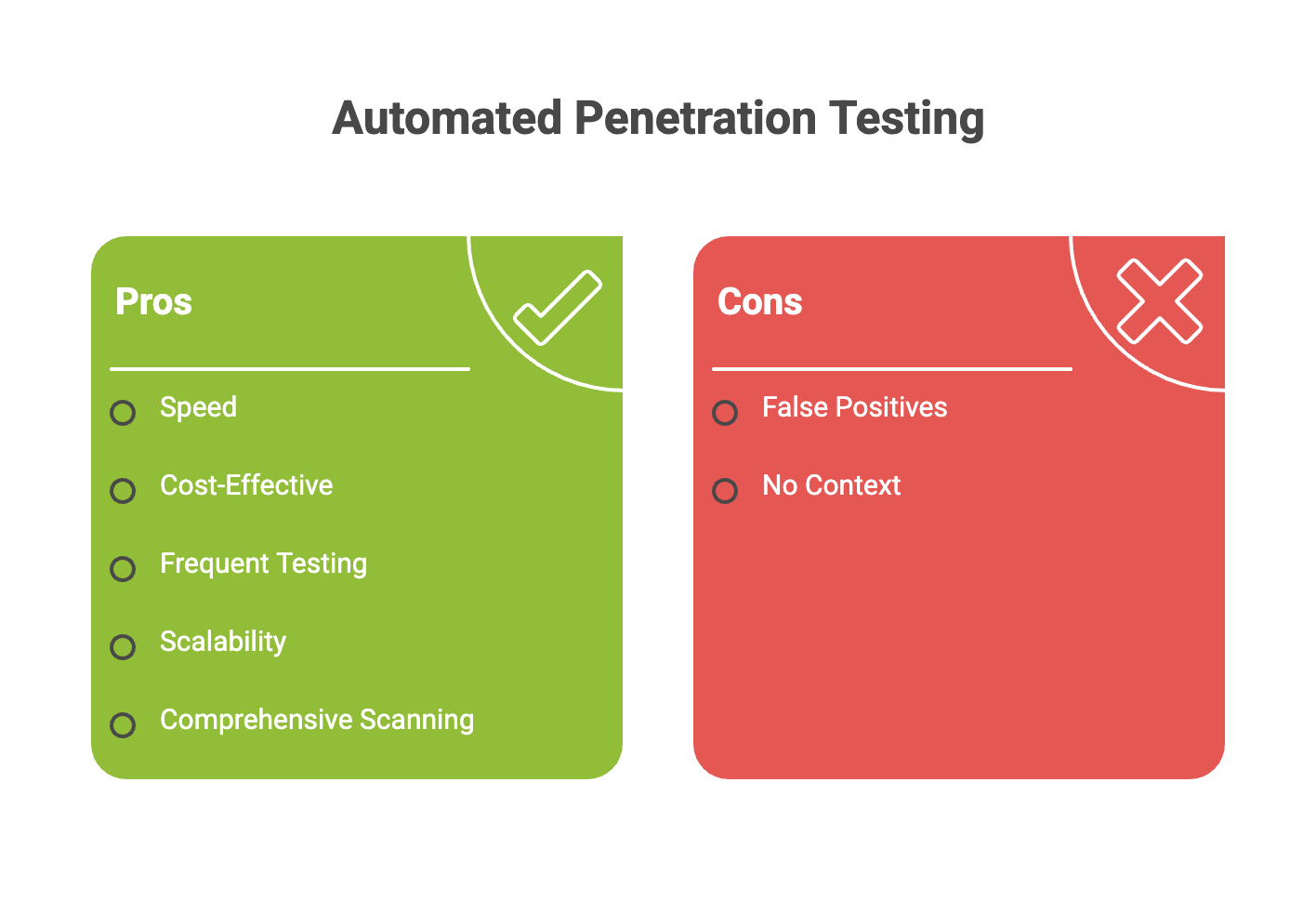
1. Automated Penetration Testing (Vulnerability Scanning)
Automated scanners are designed to quickly scan code, networks, and applications against a massive database of known vulnerabilities (like CVEs), but it's important to distinguish between basic automated scanners and automated pen testing.
Automated pentesting goes beyond simple scanning by leveraging AI and adaptive techniques to simulate real attack scenarios, mimicking hacker behaviors at scale. Automated security testing uses advanced software tools to efficiently scan, identify vulnerabilities, and generate detailed security reports.
The Benefits:
- Speed: Scans can be completed in minutes or hours.
- Cost-Effective: Once the software is purchased, running a scan costs very little.
- Frequent Testing: Automated security testing enables frequent testing, making it ideal for agile and DevOps environments where regular assessments are needed.
- Scalability: Can scan thousands of IP addresses or endpoints simultaneously.
- Scanning Process: The scanning process is highly efficient, covering large environments and systems comprehensively.
- Find Vulnerabilities: Automated pentesting can find vulnerabilities and report discovered vulnerabilities by simulating attacks and exploiting weaknesses, including misconfigurations and logic flaws.
- Outdated Software Versions: Automated security testing helps detect outdated software versions and unsupported components that could be exploited by attackers.
The Cons:
- False Positives: Scanners often flag issues that aren’t actually risks, wasting developer time.
- No Context: Tools cannot understand the “intent” of an application.
- Repetitive Tasks: Automated tools are best suited for repetitive tasks and may miss complex vulnerabilities that require human analysis, such as authorization bypasses or multi-step exploit chains.
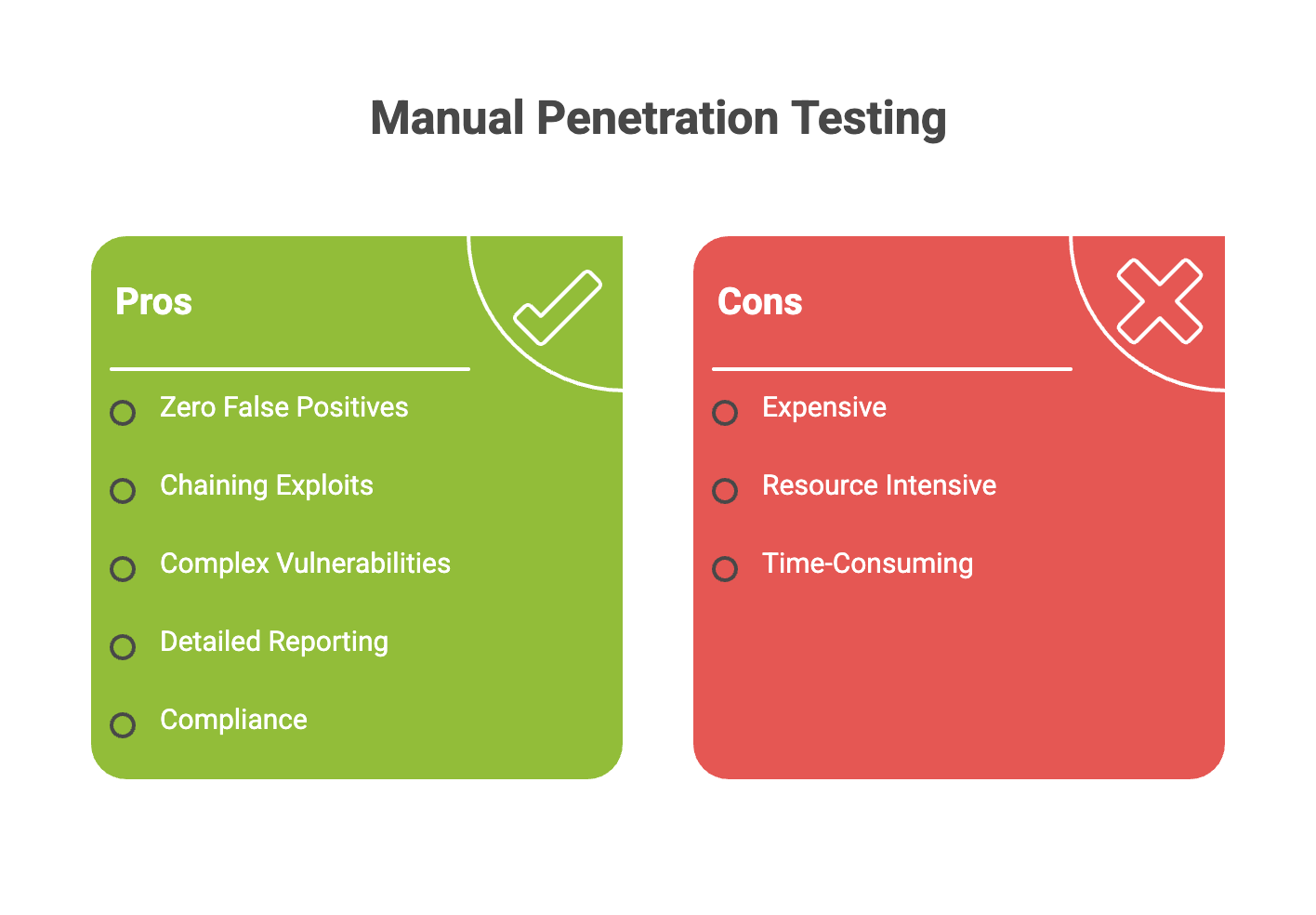
2. Manual Penetration Testing
Manual testing, also known as manual pentesting or manual pen testing, is a hands-on engagement where a Senior Security Engineer, or penetration tester, attempts to breach your systems just as a real-world attacker would. These experts leverage their skills to carefully examine your target environment, understanding its structure and components to maximize the effectiveness of the assessment.
Manual testers meticulously plan tests to avoid disrupting critical systems, ensuring business continuity. By simulating real world attacks, they can uncover real world vulnerabilities that automated tools might miss. The primary goal is to identify exploitable vulnerabilities before attackers do, providing a proactive defense.
The Benefits:
- Zero False Positives: Every vulnerability is manually verified by the expert before it reaches the report.
- Chaining Exploits: Humans can combine three “low-risk” bugs to achieve a “high-risk” compromise, uncovering chained exploits that automated tools often miss.
- Manual Testing Excels: Manual testing excels at identifying complex, subtle, or customized vulnerabilities that require human intuition and expertise.
- Detailed Reporting: You receive a “storyboard” of how the attack happened and tailored advice on how to fix it.
- Compliance: Many high-level regulations (like PCI DSS or SOC2) specifically require manual testing.
The Cons:
- Expensive: You are paying for the time and specialized knowledge of an expert.
- Resource Intensive: Manual penetration testing is resource intensive, requiring significant human effort and time.
- Time-Consuming: A thorough test can take one to three weeks.
- Point-in-Time: It only tells you how secure you are on the day the test was performed.
Business Logic Flaws: The Hidden Risks
Business logic flaws are some of the most elusive and dangerous vulnerabilities in modern IT systems. Unlike traditional security weaknesses—such as outdated software or misconfigured servers—business logic flaws stem from the way an application is designed to function. These vulnerabilities arise when an attacker manipulates the intended workflow or exploits gaps in the logic that governs how users interact with the system.
Manual penetration testing excels at uncovering these complex business logic flaws. Skilled human testers can step into the shoes of a real attacker, thinking creatively to simulate attack scenarios that automated tools often overlook. For example, a manual tester might discover that by manipulating the sequence of actions in a shopping cart, a user can apply unlimited discounts or bypass payment entirely: an issue that automated penetration testing might miss because the underlying code appears to function as intended.
While automated penetration testing is highly effective at identifying known vulnerabilities and performing routine scans, it typically struggles with logic flaws that require contextual understanding and human intuition.
However, as automated tools evolve, some now incorporate machine learning to analyze behavioral patterns and flag potential anomalies. Still, when it comes to identifying nuanced vulnerabilities and complex business logic flaws, the expertise and adaptability of human testers remain unmatched.
Hybrid Approach to Security Testing
A hybrid approach to security testing brings together the best of both worlds: the efficiency of automated penetration testing and the depth of manual expertise. By leveraging automated tools for routine scans and rapid vulnerability identification, organizations can maintain continuous coverage of their attack surface and quickly catch common issues. This frees up skilled human testers to focus on more challenging tasks, such as uncovering business logic flaws, simulating multi step attacks, and analyzing nuanced vulnerabilities that automated scans might miss.
This combination not only enhances overall security posture but also helps reduce the number of false positives generated by automated testing. Human testers can review and validate the results from automated scans, ensuring that only genuine vulnerabilities are prioritized for remediation. By integrating manual and automated testing, organizations benefit from both broad, ongoing surveillance and targeted, in-depth analysis—making the most effective use of their security resources.
Ultimately, a hybrid approach to penetration testing enables organizations to identify a wider range of vulnerabilities, from routine misconfigurations to sophisticated logic flaws, while optimizing both time and cost. This strategy is especially valuable for startups and growing businesses that need to balance comprehensive security with operational efficiency.
Comparison Summary Table
Security Testing Best Practices
To maximize the effectiveness of security testing, organizations should adopt a set of proven best practices. First, conduct regular vulnerability assessments using a blend of automated and manual methods. Automated penetration testing provides continuous monitoring and rapid detection of known vulnerabilities, while manual testing delivers a thorough evaluation of complex vulnerabilities and real-world attack scenarios.
Second, tailor your security testing to the unique needs and risks of your business. Consider the sensitivity of your data, the complexity of your systems, and the potential impact of a breach when designing your testing strategy. Third, ensure that testing is performed by skilled professionals who have the expertise to identify subtle flaws and simulate sophisticated attack scenarios.
Fourth, integrate security testing into every stage of your development lifecycle. By embedding security considerations from design through deployment, you can catch issues early and reduce the risk of introducing vulnerabilities. Finally, treat security testing as an ongoing process, not a one-time event. Continuous monitoring and regular reassessment are essential to stay ahead of evolving cyber threats and maintain a strong security posture.
By following these best practices, organizations can uncover complex vulnerabilities, respond quickly to new risks, and build a resilient foundation for long-term security.
What is Best for Startups?
For a startup, resources are thin, but the cost of a data breach can be fatal. The best approach is rarely “one or the other”. It is a Hybrid Strategy.
Phase 1: The Automated FoundationStartups should implement automated scanning as soon as they have a live product. Integrating a scanner into your development process ensures that you don’t push code with “easy” mistakes, like default passwords or unpatched libraries. This is a low-cost way to maintain a baseline of security. Based on the findings from automated scans, you should implement appropriate security measures to address discovered vulnerabilities such as misconfigurations, outdated software, and logic flaws.
Phase 2: The Manual MilestoneYou should invest in a manual penetration test when:
- You are about to launch a major feature: If you are handling user payments or sensitive data, you need a human to check the logic.
- Enterprise Sales: Large clients will often refuse to sign a contract unless you can provide a manual penetration test report.
- Fundraising: Investors may look for third-party security validation during due diligence.
After manual testing, review the discovered vulnerabilities to prioritize remediation steps and further strengthen your security posture.
The Verdict: For a startup, Automated testing is for maintenance, but Manual testing is for trust. Start with automation to catch the basics, but hire a manual expert at least once a year to ensure your “fortress” doesn’t have a hidden back door that a machine missed.
FAQ Fro Manual and automated Pen testing
What is the difference between manual and automated penetration testing?
Manual testing uses human intuition to find complex logic flaws while automated testing uses software to scan for known vulnerabilities. Humans find nuanced issues that machines often miss due to a lack of context.
Why is manual penetration testing important for compliance?
Many high-level regulations like SOC 2 or PCI DSS specifically require manual testing for a thorough evaluation. It provides the deep security validation needed for enterprise-level trust.
What are the main benefits of automated security scanning?
Automated tools are fast and cost-effective for identifying common risks and outdated software across large environments. They are ideal for frequent testing within agile and DevOps workflows.
What are business logic flaws in cybersecurity?
These flaws occur when an attacker manipulates the intended workflow of an application to bypass security. Because the code is not technically broken, these issues usually require a human expert to detect.
When should a startup invest in a manual penetration test?
Startups should perform manual tests before major feature launches or when required for enterprise sales and fundraising. While automation handles daily maintenance, manual testing builds the trust needed for growth.