Key Takeaways
- An ISO 27001 internal audit is a mandatory requirement under Clause 9.2—skip it or do it poorly, and you’ll fail your certification audit
- Internal audits verify that your information security controls are effectively implemented, not just documented
- Plan your internal audit programme as a 12-18 month roadmap, not a one-day checklist
- Auditor independence is non-negotiable; for small teams, this often means outsourcing to a firm like SecureLeap
- Document everything: scope, evidence, findings, and corrective actions
- Use internal audit results in your management review to drive continuous improvement and demonstrate security excellence to external stakeholders
Introduction: Why ISO 27001 Internal Audits Matter for Startup Founders
If you’re a CEO or CTO of a high-growth startup, you’ve probably encountered this scenario: you’re deep in negotiations with an enterprise customer, the deal is moving forward, and then their security team sends over a vendor questionnaire asking for proof of ISO 27001 certification and evidence of your internal audit program.
An ISO 27001 internal audit is the formal process of evaluating whether your information security management system actually does what it’s supposed to do. It’s not just checking if policies exist on paper—it’s verifying that your security controls are effectively implemented and protecting customer data in production environments. For B2B SaaS and venture-backed startups, this audit is often the difference between closing a six-figure enterprise contract and watching it slip to a competitor who can prove their security posture.
Here’s the reality: internal audits under Clause 9.2 of ISO 27001 are a mandatory requirement, not an optional nice-to-have. If you skip this step or treat it superficially, you will fail your external audit. According to IBM’s 2025 Cost of a Data Breach Report, the average breach costs small SaaS firms $4.45 million per incident.

The typical startup pain points around internal audits are predictable but painful:
- Limited security staff: You might have one security engineer, or none at all
- Engineers owning controls: Your DevOps lead is probably responsible for access management, change control, and incident response simultaneously
- Conflicting priorities: Every hour spent on audit prep is an hour not spent on the product roadmap
- Lack of audit experience: Most founders have never been through an ISO 27001 certification process before
SecureLeap specializes in helping seed-to-Series B SaaS companies build a lean, audit-ready ISO 27001 internal audit program that doesn’t derail your velocity. In this guide, we’ll walk you through Clause 9.2’s requirements in plain language, show you a pragmatic audit workflow designed for small teams, and outline your options if you lack independent auditors internally.
ISO 27001 Clause 9.2 Explained for Startups
Clause 9.2 (and specifically 9.2.2 in ISO/IEC 27001:2022) defines the core requirements for how organizations must conduct internal audits of their ISMS. Think of it as the rulebook that tells you what audits must cover, how often they need to happen, and what documentation you need to produce.
In founder-friendly language, here’s what Clause 9.2 requires:
Your internal audits must verify that your ISMS and the Annex A controls you’ve selected actually conform to ISO 27001’s requirements AND to your own internal policies and procedures.
This is a critical distinction. You’re not just checking against the international standard—you’re also checking against the security policies your organization has defined. If your access management policy says quarterly access reviews are required, the internal audit needs to verify those reviews are actually happening.
The internal audit process is about testing effectiveness, not just confirming documentation exists. An external auditor won’t be satisfied seeing a beautifully formatted access control policy if you can’t demonstrate that access reviews are being performed on real user accounts in your production AWS environment.
For startups running cloud infrastructure, this means your internal ISMS audit needs to cover:
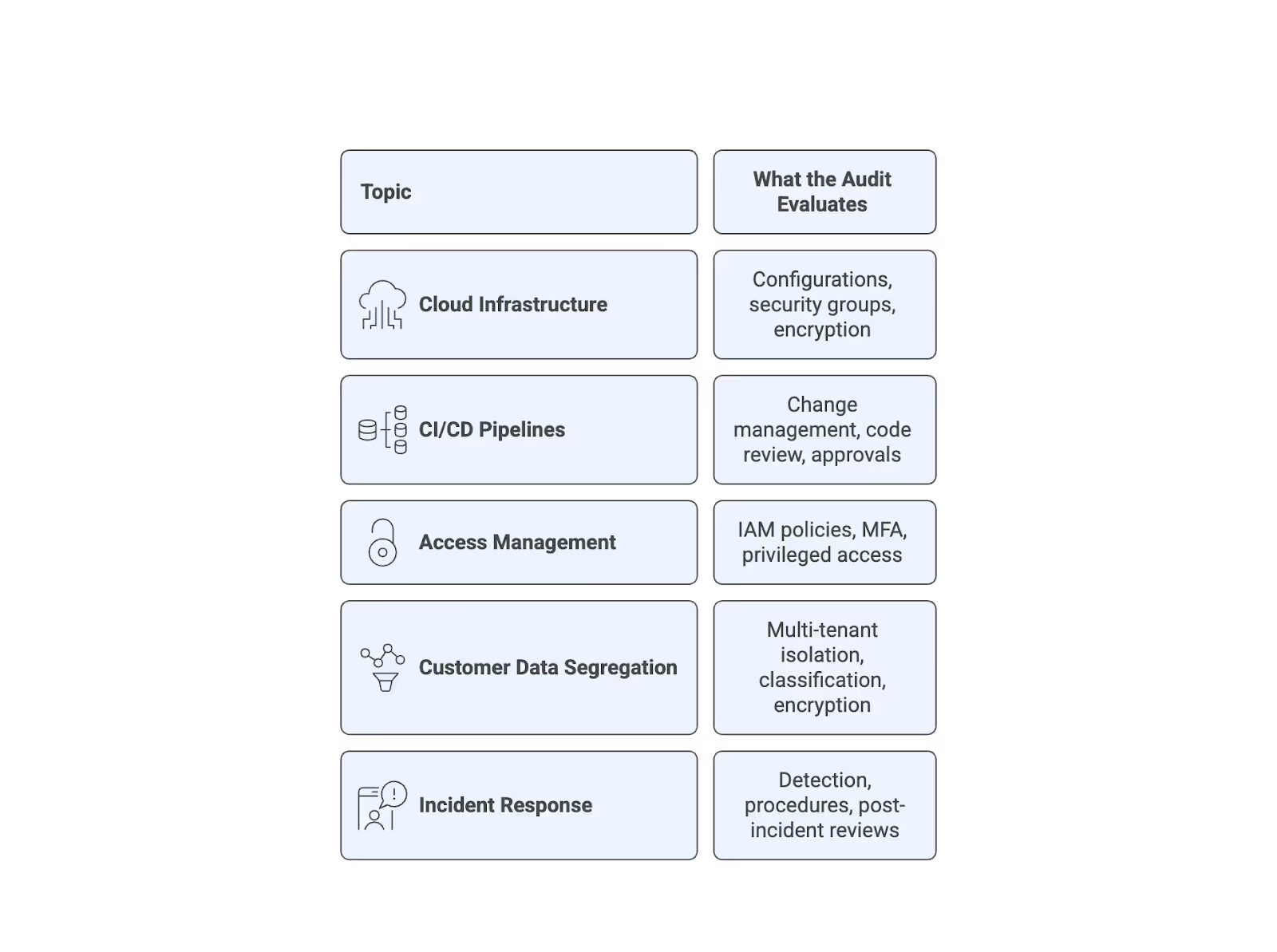
For the 2022 version of ISO 27001, your internal audit must cover the ISMS scope as defined in your documentation, the risks identified in your risk register, and the controls referenced in your Statement of Applicability (SOA). Most startups select between 50-70 of the 93 Annex A controls, focusing heavily on areas like A.5 (information security policies) and A.8 (asset management).
External auditors conducting your certification or surveillance audits will specifically look for evidence that internal audits were performed at planned intervals—at minimum annually—and that at least one complete internal audit cycle was completed before the first certification audit.
Breakdown of ISO 27001 Internal Audit Requirements (Clause 9.2.2)
Let’s break down Clause 9.2.2’s requirements into practical terms that make sense for a 30-person SaaS startup, not a Fortune 500 enterprise.
Documented Internal Audit Programme
You need a written internal audit programme (yes, the standard uses British spelling) that covers:
- Frequency: How often audits happen—typically annually for the full ISMS, with higher-risk areas potentially reviewed quarterly
- Scope: Which processes, teams, and systems are covered in each audit cycle
- Responsibilities: Who conducts the audits and who receives the results
- Methods: Interviews, document reviews, configuration checks, sampling of records
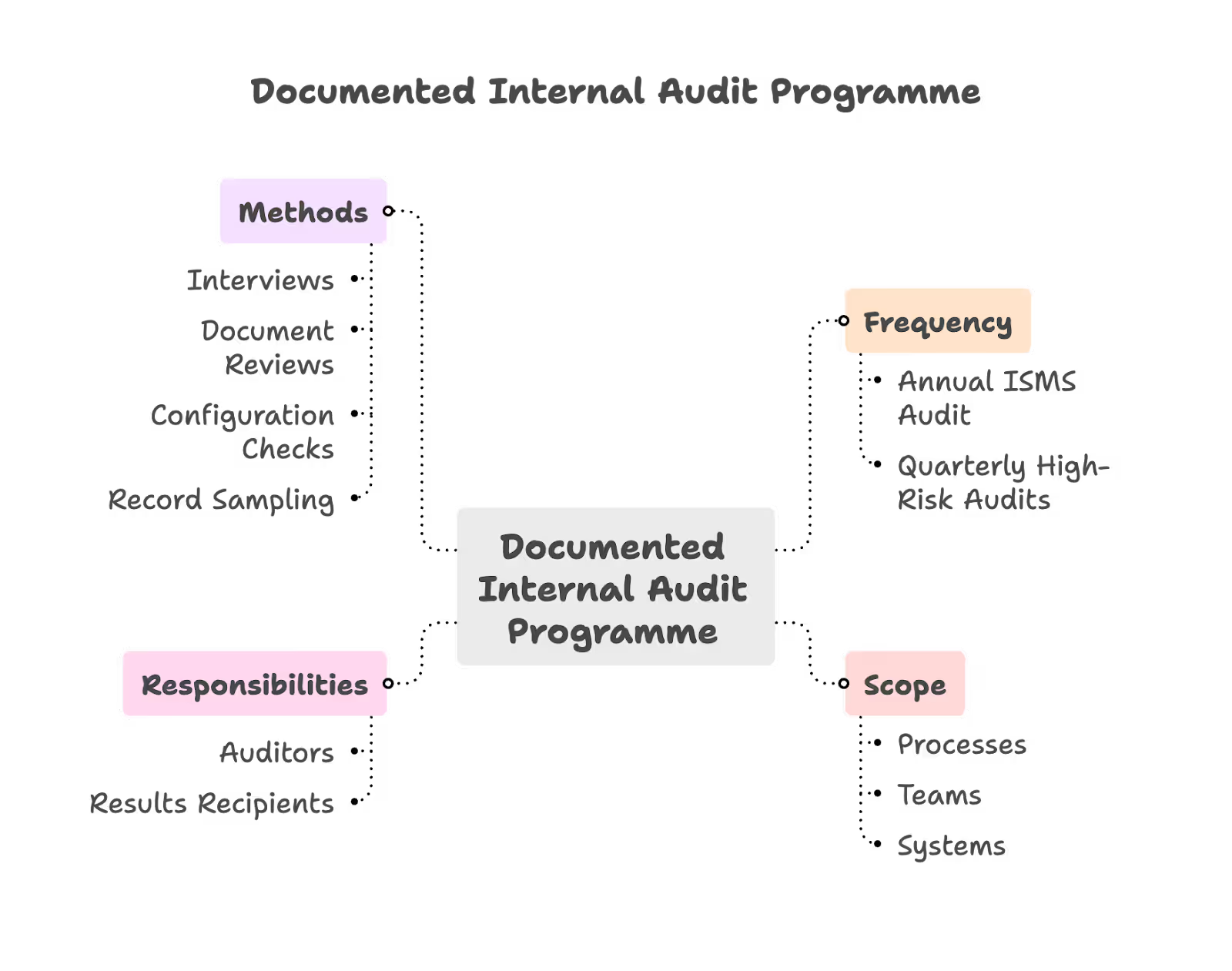
This doesn’t need to be a 50-page document. A simple table or schedule showing when each area will be audited, by whom, and against which audit criteria is sufficient.
Consideration of Process Importance and Changes
When planning your audit programme, you must consider:
- The importance of processes being audited (customer data handling is higher priority than internal wikis)
- Changes that have occurred since previous audits (new products, regions, or infrastructure)
- Audit results from prior cycles (areas with findings deserve more attention)
For startups, this means if you expanded from US-only to EU data processing since your last audit, the new scope needs to be covered. If your last audit found gaps in access reviews, that area should get deeper scrutiny this time.
Defined Audit Criteria and Scope
Each internal audit must have clearly defined:
- Audit criteria: What you’re auditing against—specific ISO 27001 clauses, Annex A controls, internal policies, or SLAs
- Audit scope: Which teams, systems, and locations are included (e.g., “AWS production account, engineering team, US operations”)
Auditor Independence
This is where many organizations struggle. The auditors conducting the audit cannot audit their own work. If your CTO designed the access control system, they cannot be the auditor evaluating whether access controls are effectively implemented.
For small startups without dedicated compliance teams, this often means:
- Cross-functional internal audits (finance audits engineering controls, engineering audits HR processes)
- Outsourcing the internal audit function to a firm like SecureLeap
Reporting to Relevant Management
Audit findings and internal audit results must be reported to relevant management—typically the CEO, CTO, or VP of Engineering. This isn’t optional. The management review process under Clause 9.3 specifically requires that internal audit results be considered as input.
Corrective Action Tracking
When the audit identifies nonconformities or control gaps, you must:
- Document the findings with evidence
- Assign owners and due dates for corrective actions
- Verify that corrections were actually implemented
- Retain records of the entire process
Designing an Internal Audit Programme for a High-Growth SaaS
An internal audit programme isn’t a one-day checklist. It’s a 12-18 month roadmap that ensures every relevant part of your ISMS gets evaluated before your external audit or surveillance audits.
Prioritizing Based on Risk
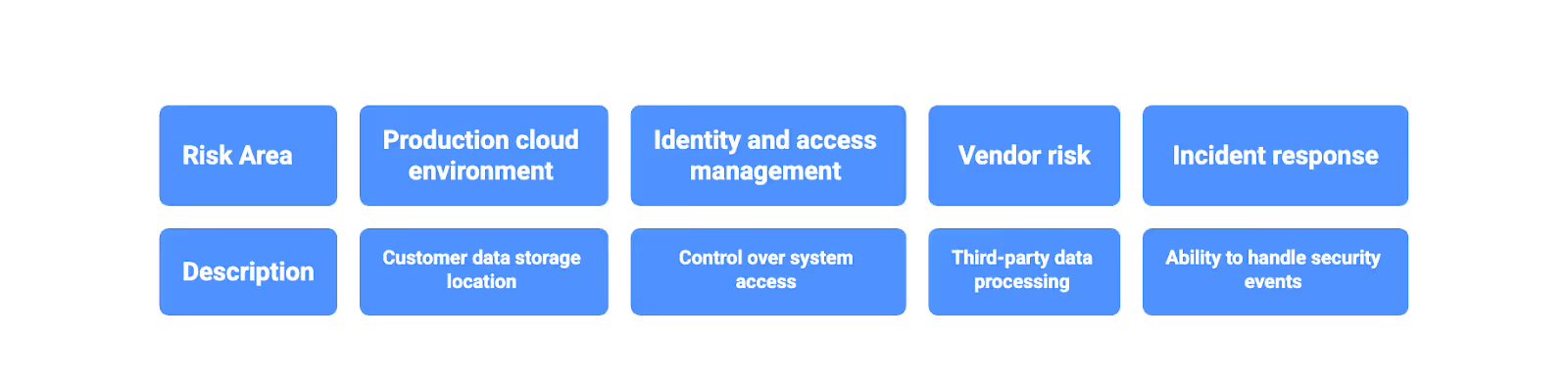
Not all processes carry equal risk. Your internal audit function should prioritize areas based on:
- Production cloud environment: Where customer data actually lives
- Identity and access management: The keys to your kingdom
- Vendor risk: Third-party SaaS tools that process your data
- Incident response: Your ability to detect and respond to security incidents
Lower-risk areas like physical security for a fully remote company, or procurement processes for a startup with minimal purchasing, can receive lighter coverage.
Aligning with External Audit Timing
If your certification audit (Stage 2) is scheduled for November, plan to complete your internal audit by July or August. This gives you 3-4 months to:
- Identify gaps and nonconformities
- Implement corrective actions
- Verify fixes are working
- Prepare documentation for the external auditor
Documenting the Programme
Your audit programme documentation can be as simple as a table with columns for:
- Process/area being audited
- Owner/responsible manager
- Audit period
- Assigned auditor(s)
- Status (planned, in progress, complete)
- Key findings summary
SecureLeap provides startup clients with a template audit programme specifically tuned for SaaS workflows and cloud-native controls, saving weeks of planning time.
Selecting Auditors and Ensuring Independence in a Small Team
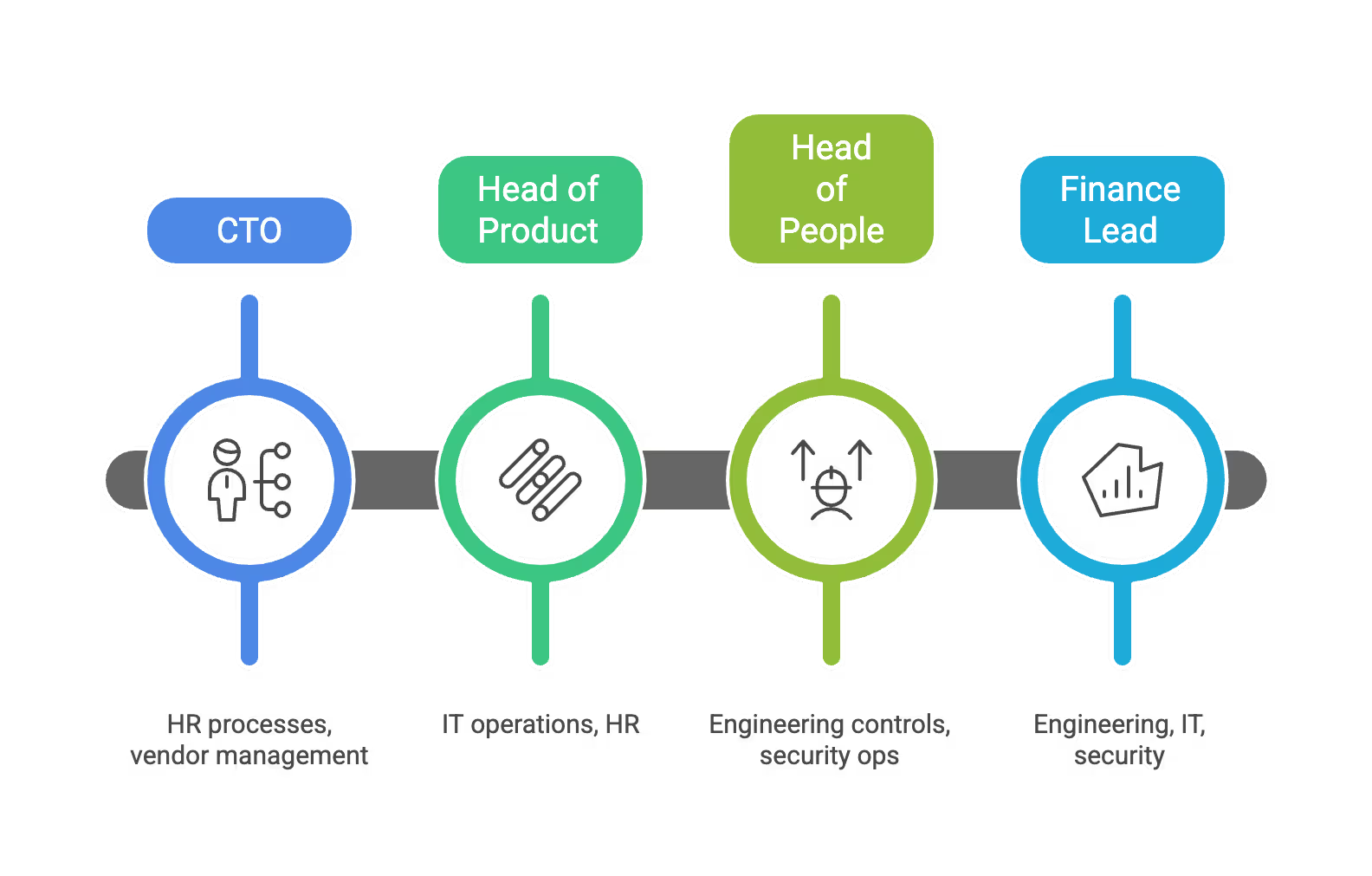
Here’s the founder dilemma: in a 25-person startup, everyone “owns” something in the ISMS. Your CTO owns engineering security, your Head of People owns HR processes, your Head of Product owns the SDLC. Finding someone truly independent to serve as an internal auditor feels impossible.
The Independence Requirement
ISO 27001 requires that auditors must be objective and impartial. They cannot audit areas where they have operational control or where they performed the work being evaluated. This isn’t a suggestion—it’s a requirement that external auditors will verify during certification audits.
Realistic Patterns for Startups
For small teams, consider these approaches:
Cross-Team Internal Audits
- Finance/Operations audits engineering access controls
- Engineering audits HR onboarding/offboarding processes
- Customer Success audits vendor risk management
- CEO/COO audits incident response readiness
External Support for Complex Areas
- Cloud security configuration reviews
- Vulnerability management and penetration testing results
- Cryptographic controls and key management
Example: Independence in a 25-Person Startup
Outsourcing the Internal Audit Function
Many startups find it faster and more effective to outsource their internal audit to a firm like SecureLeap. This approach:
- Satisfies independence requirements automatically
- Brings ISO 27001 expertise without hiring full-time staff
- Provides startup-friendly pricing aligned with your stage
- Frees your team to focus on product and customers
Documenting Auditor Competence
Whether using internal staff or external support, document the competence of your audit team:
- Short professional bios
- Experience with ISO 27001 audits
- Technical skills relevant to your stack
- Relevant certifications (CISM, CISA, ISO Lead Auditor)
Step-by-Step ISO 27001 Internal Audit Workflow for SaaS
This workflow is designed to be repeatable. Use it annually, or before each certification review or surveillance audit cycle.

Step 1: Define Scope and Objectives
Start by specifying exactly what you’re auditing:
- ISO clauses: Which sections of 27001 (e.g., Clause 7 Support, Clause 8 Operation)
- Annex A controls: Which controls from your SOA (e.g., A.8.2 Privileged access, A.8.16 Monitoring)
- Products and environments: Production vs staging, specific applications
- Regions: EU customer data, US operations, etc.
Document these in a brief scope statement that the audit team can reference throughout.
Step 2: Prepare the Audit Plan
Your audit plan should list:
- Systems to review: AWS accounts, GitHub organization, Jira/Linear, Okta/Google Workspace, ticketing tools
- People to interview: DevOps lead, security engineer (if you have one), HR manager, sales operations
- Timelines: Start date, fieldwork window, report due date
- Evidence to collect: Access logs, configuration exports, policy documents, training records
Step 3: Collect Documents and Evidence
Before conducting interviews, gather:
- Current policies and procedures
- Risk register and treatment plans
- Change management tickets (sample from past quarter)
- Access review records
- Penetration test and vulnerability scan reports
- Backup and recovery logs
- Incident records and post-mortems
- Security awareness training completion logs
Step 4: Perform the Fieldwork
This is where the audit team does substantive testing, not just document review:
- Interviews: Ask control owners to explain how processes work in practice
- Screen shares: Have engineers demonstrate access provisioning, change deployments, incident response
- Configuration reviews: Validate evidence by checking actual settings match documented policies
- Sample testing: Select 10-20 samples of JIRA tickets, Okta accounts, GitHub pull requests to verify controls operated correctly
The goal is to validate evidence that controls are operating as designed, not just that they exist on paper.
Step 5: Evaluate Findings
Classify each finding into one of these categories:
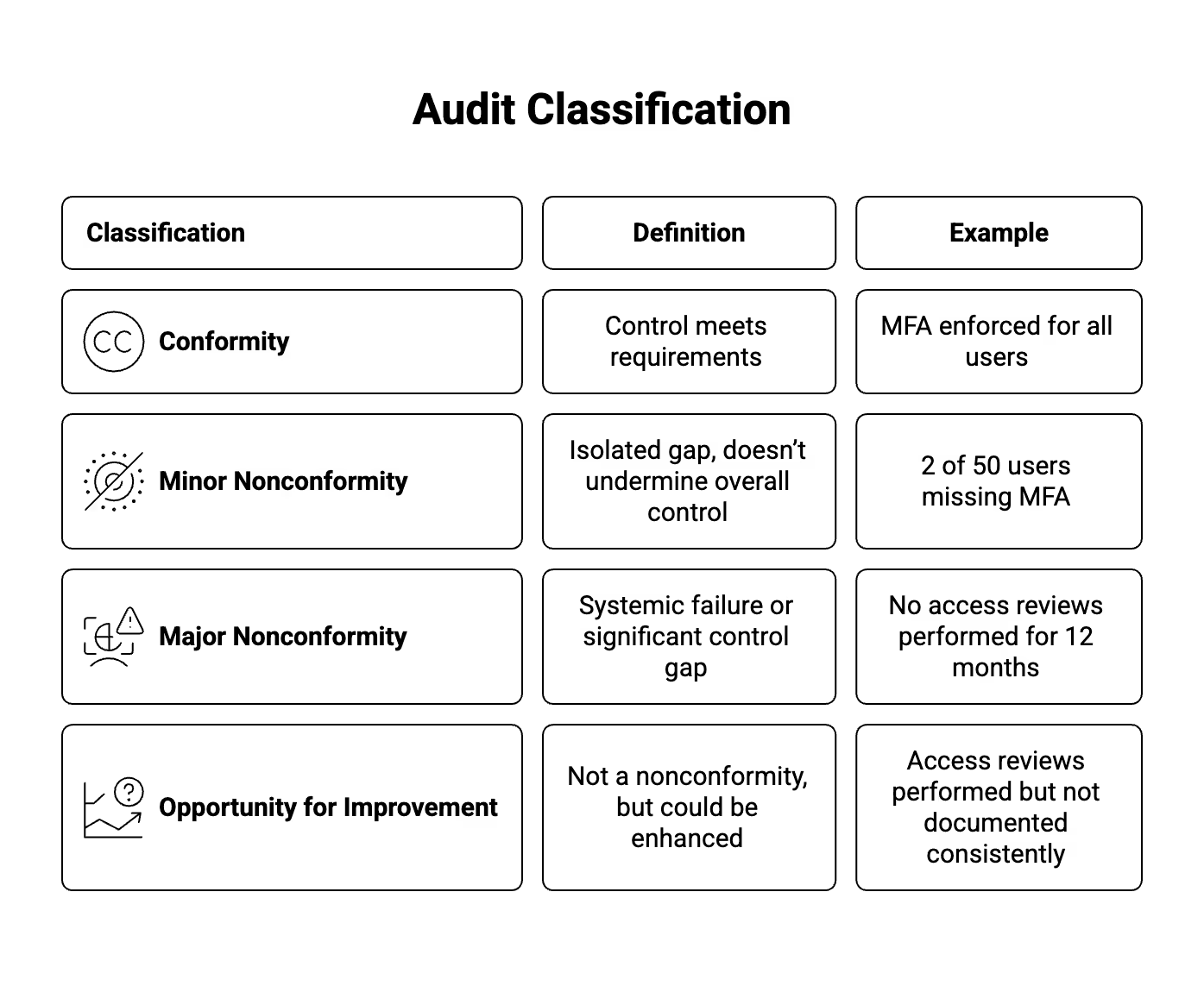
Map each finding to the relevant ISO clause or Annex A control reference.
Step 6: Report to Management
Your internal audit report should be written for leadership, not just security practitioners. Focus on:
- Key findings with business impact (e.g., “Unpatched systems could result in breach affecting 50,000 customer records”)
- Trends compared to previous audits
- Prioritized remediation recommendations
- Resource needs for corrective actions
The executive summary should resonate with your CEO—connect security gaps to customer trust, deal velocity, and regulatory requirements.
Step 7: Track Corrective Actions
Create an action log with:
- Finding reference number
- Description of the gap
- Assigned owner
- Due date for remediation
- Evidence of completion
- Verification date
Review this log in your management review meetings until all items are closed.
Evidence Collection & Documentation in a Cloud-Native Environment
SaaS startups running in AWS, GCP, or Azure have a major advantage: most evidence is digital and exportable. You’re not digging through filing cabinets—you’re pulling API outputs and dashboard screenshots.
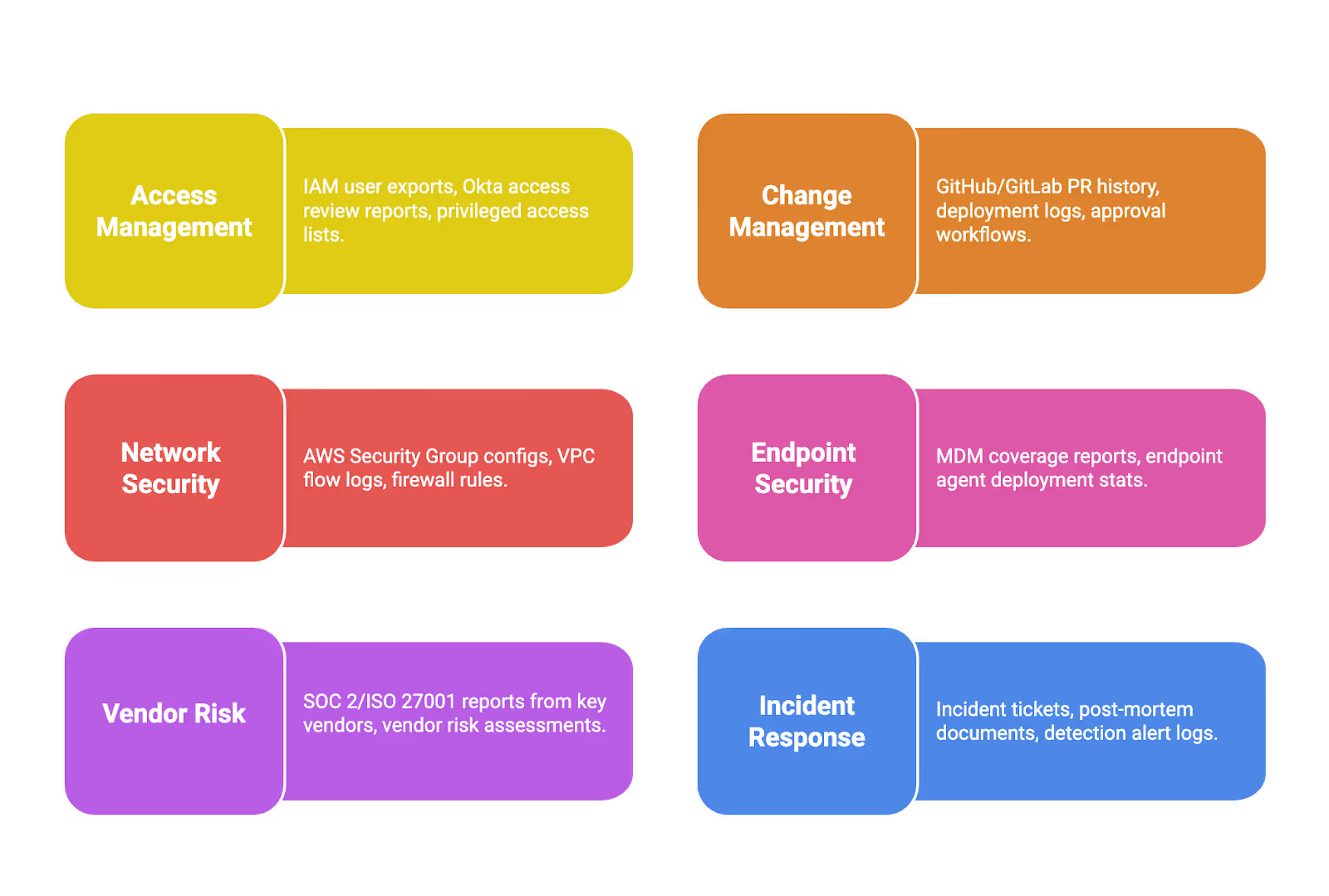
Common Evidence Types for SaaS Startups
Using Compliance Automation Platforms
Tools like Drata, Vanta, or Secureframe can dramatically reduce the manual work of evidence collection:
- Automatic evidence pulls from integrated systems (AWS, GitHub, Okta, HR platforms)
- Continuous monitoring of control effectiveness
- Pre-mapped evidence to both SOC 2 and ISO 27001 requirements
- Audit-ready exports for external stakeholders
Common SaaS Pitfalls
Watch out for these gaps that frequently surface during audits:
- Missing proof of quarterly access reviews: Policy says quarterly, but no records exist
- Undocumented incident triage: Incidents were handled but not formally logged
- Unlinked change tickets: Production changes deployed without corresponding tickets
- Orphaned accounts: Former employees still with active access
Building an Evidence Index
Create a mapping document (spreadsheet works fine) linking each ISO clause and Annex A control to:
- The specific evidence that demonstrates compliance
- Where that evidence is stored
- When it was last collected/updated
This same evidence index supports both your internal audit and external audit, reducing duplicate work.
SecureLeap helps startups set up evidence collection workflows inside these platforms, aligning SOC 2 and ISO 27001 requirements so you’re not doing everything twice.
Creating and Using an ISO 27001 Internal Audit Report
The internal audit report is often the first document that external auditors, enterprise customers, and potential acquirers ask to see. It demonstrates your organization’s commitment to objective review and continuous improvement.
Core Sections of the Report
A complete internal audit report should include:
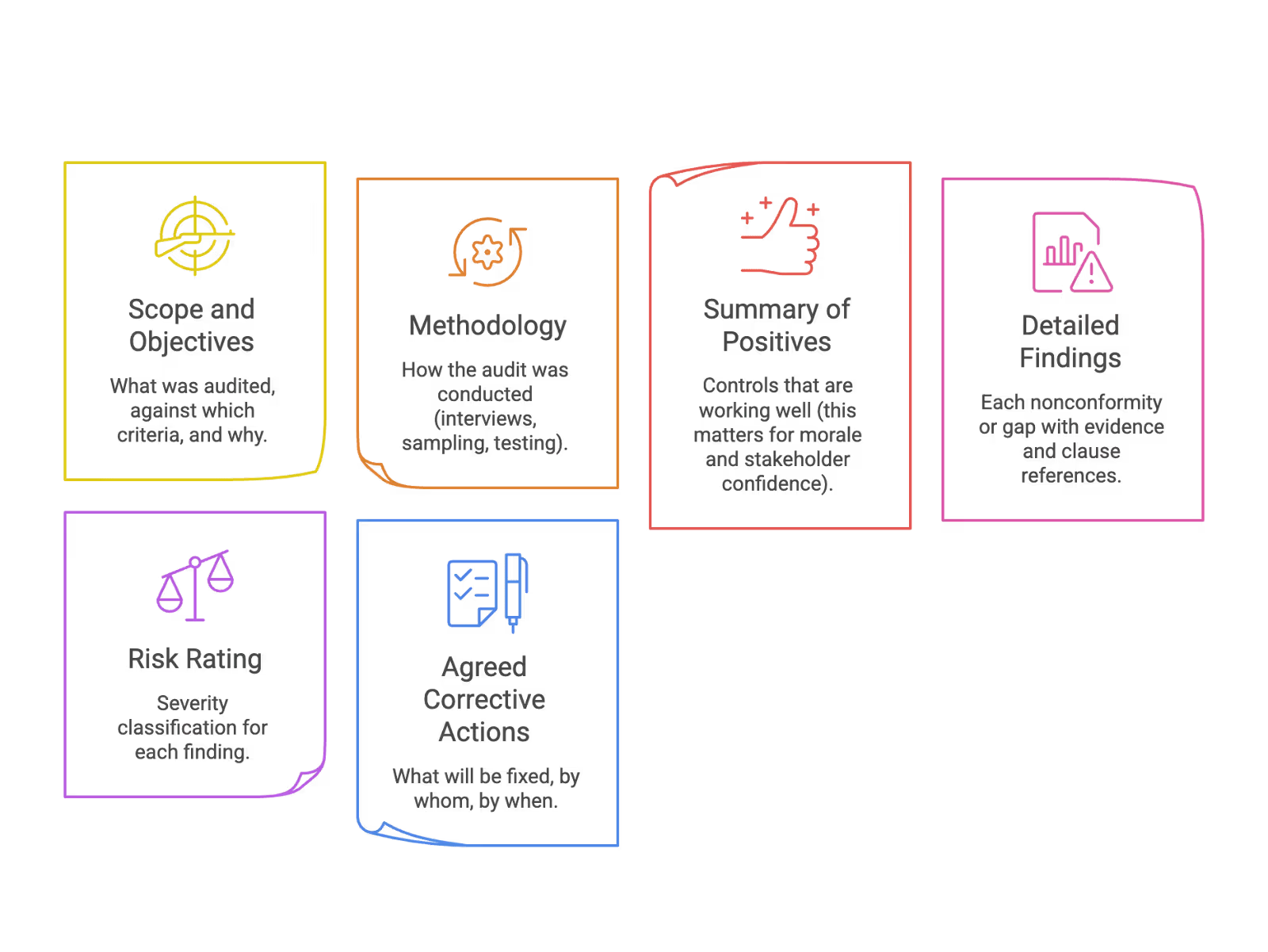
Writing for Leadership
Your CEO and board don’t need technical deep-dives on every finding. The executive summary should:
- Highlight 3-5 key findings with the highest business impact
- Quantify risk where possible (e.g., “Unaddressed access control gaps could result in $500K+ in potential fines”)
- Connect findings to customer trust and deal progression
- Summarize resource needs for remediation
Document Retention
Store signed-off internal audit reports in your ISMS document repository alongside:
- The audit plan and scope statement
- Evidence collected during the audit
- Corrective action log with completion status
- Management review meeting minutes referencing the audit
Showing Progress Over Time
Consider including a brief “maturity snapshot” showing improvement across audit cycles. This is powerful evidence for investors conducting due diligence and enterprise customers evaluating your security posture.
For example:
- Year 1: 12 nonconformities identified, 8 major
- Year 2: 6 nonconformities identified, 1 major
- Year 3: 3 nonconformities identified, 0 major
Management Review and Continuous Improvement After the Internal Audit
ISO 27001’s Clause 9.3 requires that management review consider internal audit results and drive continuous improvement. This isn’t a checkbox—it’s how your organization’s ISMS actually gets better over time.
Practical Cadence
For most startups, a quarterly security/ISMS review works well:
- Quarterly: 30-60 minute review of security KPIs, incident trends, and open risks
- Post-Audit Deep Dive: 90-minute session following the internal audit to review all findings and prioritize remediation
This review should be chaired by the CEO or CTO, with participation from relevant management across engineering, security, and operations.
Key Inputs for Management Review
Bring these to each review session:
- Internal audit report and findings summary
- Security KPIs (mean time to detect, patching timelines, training completion rates)
- Incident summaries from the period
- Risk register updates and new risks identified
- Customer security feedback and questionnaire themes
- Regulatory requirements changes affecting your organization’s operations
Aligning Security and Business Goals
Use management review to connect the security roadmap to business operations:
- Which security initiatives will unblock enterprise customers waiting on specific controls?
- Which risks pose the highest threat to revenue or reputation?
- What investments in security goals will provide competitive advantage?
Action Tracking
Maintain a simple action tracker (or OKR-style goals) that flows directly from internal audit findings and management decisions. Each action should have:
- Clear owner
- Due date
- Success criteria
- Status updates
SecureLeap can facilitate these management review sessions as a vCISO, translating technical audit findings into a 6-12 month security strategy that aligns with your growth plans.
Common ISO 27001 Internal Audit Mistakes in Startups
After working with dozens of seed-to-Series B companies going through first-time certification, we see these patterns repeatedly.
Mistake 1: Treating the Audit as a One-Day Checklist
An in depth analysis of your ISMS takes time. You cannot adequately sample transactions, conduct meaningful interviews, and test controls in a single afternoon. Plan for 20-40 hours of audit work for a typical startup scope.
Mistake 2: Having the ISMS Builder Audit Their Own Work
If your CTO or Head of Security designed and built the ISMS, they cannot serve as the sole internal auditor. This violates the independence requirement and will be flagged during your certification body’s Stage 2 audit.
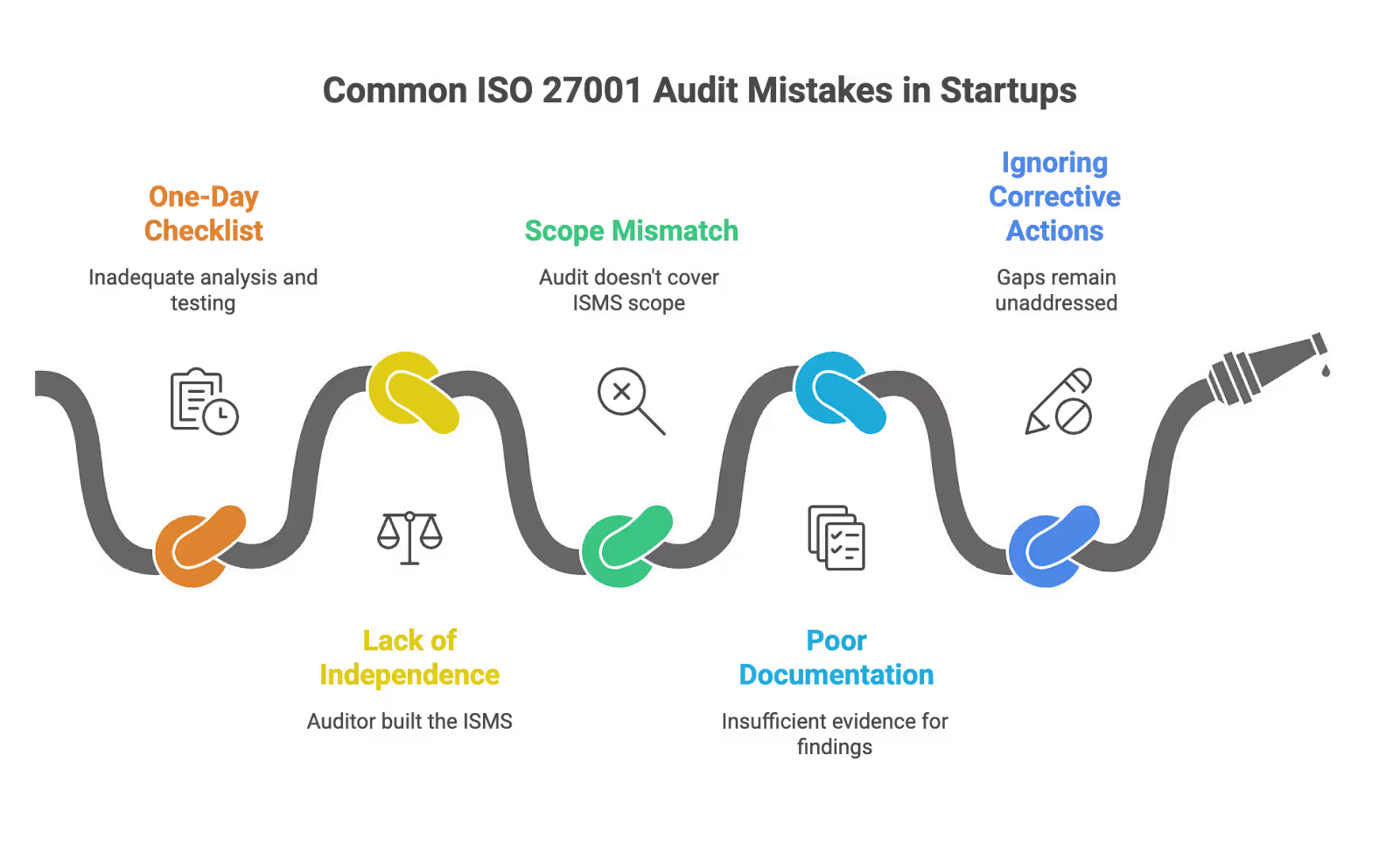
Mistake 3: Scope Mismatch
Your internal audit scope must align with your formal ISMS scope statement. If you added a new product, expanded to new regions, or onboarded significant new infrastructure mid-year, the audit needs to cover it.
Mistake 4: Poor Evidence Documentation
“We reviewed access controls and they were fine” is not acceptable documentation. Auditors must record:
- What was sampled
- How it was tested
- What evidence was reviewed
- What conclusions were drawn
Without this, the external auditor will challenge your findings and may require re-work.
Mistake 5: Ignoring Corrective Actions
Identifying gaps is only half the job. If corrective actions from the internal audit aren’t completed before the certification audit, those same issues will surface as findings—potentially major nonconformities that block certification.
SecureLeap’s audit readiness services are specifically designed to help startups avoid these issues on their first audit cycle, ensuring you’re compliance audit ready when the external auditor arrives.
How SecureLeap Helps Startups with ISO 27001 Internal Audits
SecureLeap works exclusively with early-stage, cloud-native SaaS companies—not sprawling enterprises with hundreds of security staff. We understand that your security team might be one person (or zero), and that every hour spent on compliance is an hour not spent shipping product.

Internal Audit Support
Our internal audit offering includes:
- Risk-based audit planning: We help you design an internal audit programme that focuses effort on your highest-risk areas
- Independent audit execution: Our auditors satisfy the independence requirement so your CTO can stay focused on building
- Detailed reporting: Clear findings with clause references, evidence documentation, and prioritized remediation guidance
- Management review facilitation: We translate technical findings into business language for your leadership team
Integration with Your Existing Tools
Already using Drata, Vanta, or Secureframe? We integrate with these platforms and reuse evidence you’ve already collected for SOC 2, reducing duplication for ISO 27001 internal processes.
Bundled Services
Many organizations find value in bundling internal audit with:
- Penetration testing: Identify gaps in your security controls before the auditor does
- vCISO advisory: Ongoing strategic guidance to mature your security program across various industries and use cases
This gives founders a single partner for audit, remediation, and strategy—instead of juggling multiple vendors.
Ready to Get Started?
If you’re preparing for ISO 27001 certification and need support with your internal audit, we’d love to help. Book a free consultation to review your planned scope, internal audit schedule, and current readiness. We’ll give you an honest assessment of where you stand and what it will take to get audit ready.
FAQ About ISO 27001 Internal Audit
What is an ISO 27001 internal audit?
An ISO 27001 internal audit is a formal process that evaluates whether your information security management system is functioning correctly. It verifies that your security controls are effectively implemented and compliant with both the ISO standard and your internal policies.
Is an internal audit required for ISO 27001 certification?
Yes, internal audits are mandatory under Clause 9.2 of the ISO 27001 standard. You must complete at least one full internal audit cycle before you can pass your external certification audit.
Who can conduct an ISO 27001 internal audit?
The standard requires audits at planned intervals, which is typically annually for the full system. However, higher risk areas such as production environments or access management may benefit from quarterly reviews.
What steps are involved in the internal audit workflow?
The workflow involves defining the scope, creating an audit plan, collecting evidence, and performing fieldwork like interviews. After testing, you must report findings to management and track corrective actions for any nonconformities.






