No, SOC 2 and ISO 27001 are not the same, although they share similarities in focusing on information security and protecting customer data. SOC 2 is a U.S.-based attestation report developed by the American Institute of Certified Public Accountants (AICPA) that evaluates a service organization’s controls related to security, availability, processing integrity, confidentiality, and privacy based on the Trust Services Criteria.
It is primarily used by service organizations to demonstrate their operational effectiveness in safeguarding data, especially for U.S. customers. The relationship between iso 27001 and soc, and the frequent comparison of 27001 and soc 2, is important because organizations often consider both frameworks to enhance data security, build customer trust, and meet different regulatory or market requirements.

ISO 27001, on the other hand, is an international standard developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). It provides a comprehensive framework for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). As one of the leading compliance frameworks, ISO 27001 helps organizations achieve security compliance by establishing best practices for managing information security risks. ISO 27001 certification involves a formal audit process and demonstrates that an organization manages information security risks systematically and continuously.
In summary, SOC 2 results in an attestation report focused on specific controls relevant to service organizations, while ISO 27001 results in a formal certification of an organization’s overall information security management system. Both frameworks require external audits to validate compliance, and there is roughly an 80% to 100% overlap in security controls between SOC 2 and ISO 27001, though they differ in structural approach and usage. SOC 2 and ISO 27001 are both well-respected security and compliance standards designed to demonstrate to clients that organizations can be trusted with their data. SOC 2 reports are better known in North America and typically carry more weight than ISO certifications in the US, while ISO 27001 is the international standard for data protection created by ISO and IEC.
Key differences between SOC 2 and ISO 27001 include their audit processes, scope, and recognition: SOC 2 is primarily used in North America and results in an attestation report, while ISO 27001 is globally recognized and results in a formal certification. Understanding these key differences helps organizations determine which compliance standard aligns better with their specific needs and regulatory environment.
Quick Answer: Is SOC 2 or ISO 27001 Better for Startups?
For US-focused B2B SaaS startups, SOC 2 is typically the better first choice because most of US enterprise buyers request it during procurement. SOC 2 reports are better known in North America and typically carry more weight than ISO certifications in the US, especially for regulatory compliance in the US market. It costs $15,000-$50,000 and takes 6-9 months for Type 2 compliance.
Choose ISO 27001 information security management system first if:
- 70%+ of your revenue comes from EU/UK/international customers
- Your prospects explicitly request ISO 27001 in RFPs
- You're in heavily regulated industries (finance, healthcare)
Bottom line:
Choose based on where your customers are located and what they're asking for in security questionnaires.
Why This Choice Is Hard (And Where Smart Teams Slip)
Both sound similar. “Security certification, audit, trust, blah blah.” But SOC 2 and ISO 27001 are different instruments used by different buyers. Many organizations pursue both ISO 27001 and SOC 2 to meet comprehensive requirements and strengthen their security posture.
Sales pressure is real. A prospect dangles a big contract; you sprint into an audit… before you’re ready or before you’re sure it’s the right standard. Implementing both standards also enables an organization to maintain its security system robustly, as both ISO and SOC 2 frameworks have comprehensive requirements that address a wide range of security and compliance needs.
Tool ≠ outcome. Automation helps, but it won’t pick the right framework, write your SoA, or pass Stage 2 alone.
Your job: pick the standard that shortens your sales cycle and sets up a sane path to the other later.
Decision Framework: Which Certification Should You Pursue First?
Use this in order. If you answer “yes” to a line, pick that path.
1) Where are your current and next 12 months' deals?
- Mostly US mid-market SaaS, IT buyers familiar with SOC 2? → SOC 2 first
- EU/UK-heavy or selling into global enterprises/government frameworks? → ISO 27001 first
2) What do your largest target customers explicitly require in contracts/security questionnaires?
- “SOC 2 Type II report” → SOC 2 first
- “ISO 27001 certification from an accredited body” → ISO 27001 first
3) How fast do you need a badge to unstick deals?
- Under 90 days, need something credible for NDAs/pilots → SOC 2 Type I now, Type II next
- You have a 3–6 month runway, enterprise pilots depend on a formal certificate → ISO 27001
4) How global is your go-to-market in 2025?
- US-only or US-first → SOC 2
- Multiregional now or soon (EU, APAC, public sector) → ISO 27001
5) Internal maturity and appetite:
- You want a lighter attestation focused on controls in practice → SOC 2
- You want an ISMS (risk-led management system) you can scale across business units → ISO 27001
SOC 2 vs ISO 27001: Quick Comparison Table
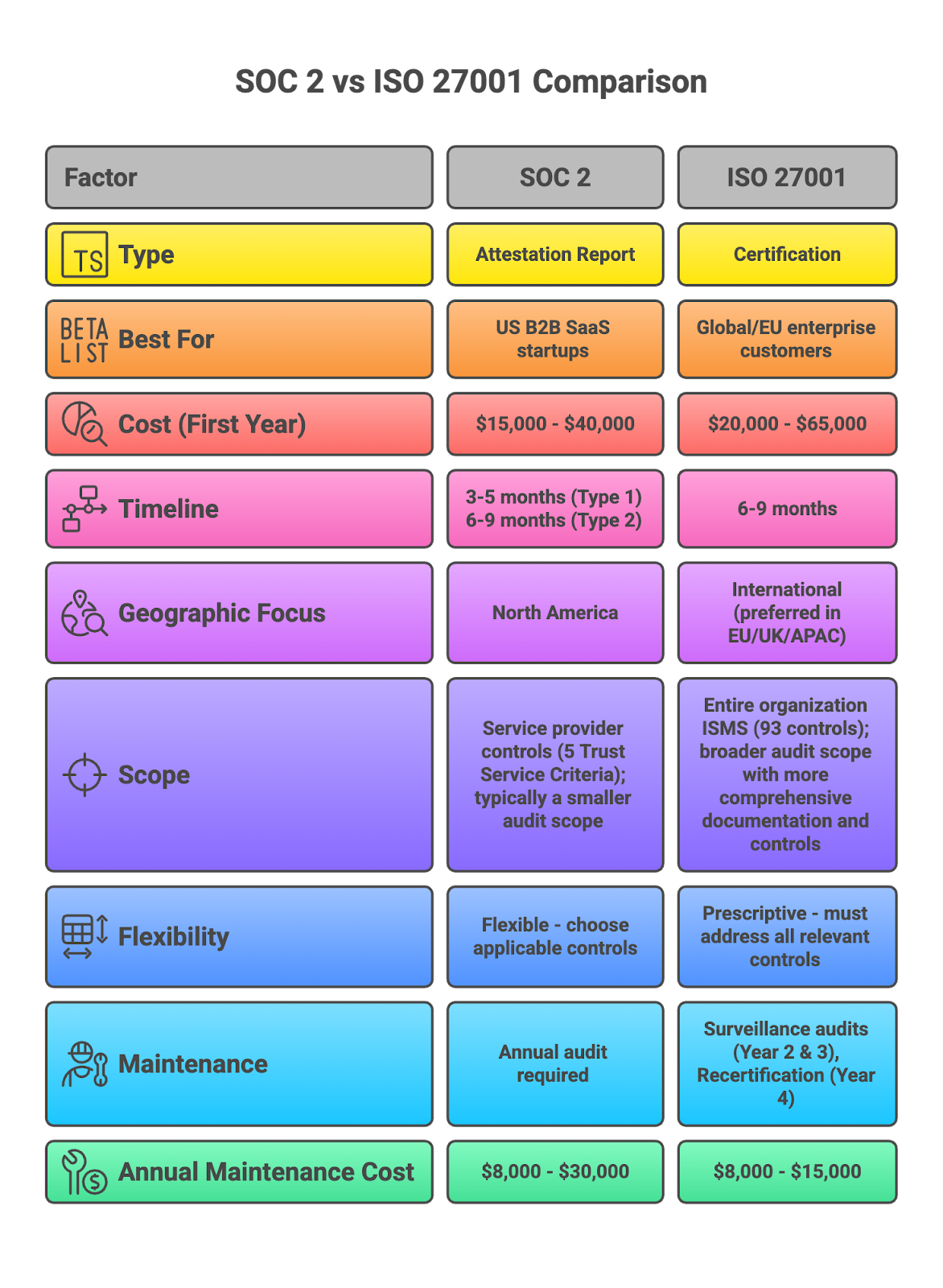
💡 Quick takeaway: If your customers are in the US, start with SOC 2. If international or EU-focused, start with ISO 27001. Note that ISO 27001 certification generally involves a higher cost and a broader audit scope due to its comprehensive requirements, starting with an initial certification audit to assess readiness.
Path A: SOC 2 First (Revenue-First for US SaaS)
What matters to sales: - A clean SOC 2 Type I gets you through early security reviews. - A Type II (6–12 months coverage) closes bigger, risk-averse buyers.
Indicative costs (2026 typical ranges):
-Tooling/automation: $7k–$20k/year depending on size and integrations.
- Pen test (app + infra): $5k–$20k.
- Audit (Type I): $5k–$10k; (Type II): $8k–$20k based on scope/period.
- vCISO/readiness help: $8k–$20k depending on lift.
Note: SOC 2 audits must be performed by a licensed CPA firm, and the resulting report is a service organization control (SOC) attestation that demonstrates your ongoing security and compliance practices.
💡Pro tip: If a whale is asking for SOC 2, negotiate the timeline for completion and make it a contractual commitment.
Path B: ISO 27001 First (Global, Enterprise, or EU/UK)
What matters to sales: - An accredited ISO 27001 certificate unblocks global procurement and partner marketplaces. ISO 27001 requires adherence to all 93 controls in Annex A unless justified for exclusion, while SOC 2 allows customization of controls based on business models.
Indicative costs:
- Tooling/automation: $7k–$20k/year .
- Pen test: $4k–$20k.
- Internal Audit: $2k–$7k.
- Certification body: $15k–$50k over 3 years (depends on headcount/scope)
- vCISO/implementation: $8k–$20k depending on maturity.
💡Pro tip: Schedule and execute formal Management Review Meetings at least annually (ideally quarterly). The agenda must explicitly cover all required inputs: Internal Audit Results, Non-conformities, Risk Status, Control Performance, and Continual Improvement Opportunities. Document the decisions made and actions assigned to prove the leadership is actively governing the ISMS. ISO 27001 requires a formal internal audit process at planned intervals to ensure ongoing compliance and support continuous improvement of the ISMS.
SOC 2 vs ISO 27001: Timeline Comparison
SOC 2 Type 1 Timeline: 3-4 Months
- Month 1-2: Gap assessment, policy documentation, control implementation. Organizations must design and implement internal controls and organizational controls to meet SOC 2 requirements during this phase.
- Month 3: Internal readiness review, evidence collection
- Month 4: External audit, report issuance
SOC 2 Type 2 Timeline: 6-9 Months
- Month 1-2: Gap assessment, policy creation, control design
- Month 3-5: Implement controls, evidence collection
- Month 6-8: Observation period (mandatory 3-6 months)
- Month 9: External audit, report issuance
ISO 27001 Timeline: 6-9 Months
- Month 1-2: Gap analysis, ISMS design, risk assessment
- Month 3-5: Control implementation, documentation, internal audit
- Month 6-8: Stage 1 audit (documentation review
- Month 9: Stage 2 audit (on-site assessment), certification
Audit Process: How SOC 2 and ISO 27001 Audits Actually Work
The audit process is where the rubber meets the road for both SOC 2 and ISO 27001, putting your information security management system and security controls under the microscope to ensure you’re truly protecting customer data. While both frameworks share the goal of safeguarding sensitive data and building customer confidence, the way they approach the audit—and what’s required to demonstrate compliance—differs in some important ways.
For SOC 2, the audit is conducted by independent certified public accountants (CPAs) who specialize in evaluating service organizations. The focus is on the design and operating effectiveness of your controls as they relate to the five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. The auditor will review your policies, procedures, and evidence to determine whether your controls are not only well-designed but also operating as intended over time. The result is an attestation report, which provides an independent opinion on your organization’s security posture and is often a key requirement for closing deals with enterprise customers.
ISO 27001, on the other hand, involves a more comprehensive certification process led by an accredited certification body. The audit examines your entire information security management system (ISMS), assessing how well you identify, manage, and mitigate information security risks across your organization. The process starts with a risk assessment to pinpoint areas of focus, followed by a deep dive into your security controls, documentation, and ongoing management practices. If your ISMS meets the rigorous requirements of the ISO 27001 standard, you’ll earn a formal certification—recognized by international clients and regulators alike.
A key difference between SOC 2 and ISO 27001 audits is the scope and prescriptiveness. SOC 2 audits are typically more flexible, allowing you to tailor your controls to your unique environment as long as you meet the relevant trust services criteria. ISO 27001 audits, by contrast, require you to address a comprehensive set of requirements and demonstrate a systematic, risk-based approach to information security management.
Regardless of which path you choose, ongoing compliance is essential. Both SOC 2 and ISO 27001 require regular internal audits, risk assessments, and continuous monitoring to ensure your controls remain effective and your management system evolves with new threats. This is where compliance automation platforms like Drata, Vanta, or Secureframe can make a real difference—streamlining evidence collection, automating control monitoring, and simplifying the entire compliance journey.
Ultimately, understanding the audit process for both SOC 2 and ISO 27001 helps you prepare for compliance audits, avoid security breaches, and demonstrate to customers and regulators that you take data protection seriously. By investing in a robust management system and leveraging the right tools, your organization can confidently manage information security risks, protect customer data, and maintain a strong security posture in any market.
SOC 2 vs ISO 27001: Mistakes I See (And How to Avoid Them)
1) Buying the audit before you’re ready
Symptom: Auditor calendar booked, your controls aren’t live, and you’re backfilling evidence. -
Fix: Do a readiness check first. Close the top 10 gaps. Book the audit for when you can pass the first time.
2) Scoping everything into your ISMS/system
Symptom: Your entire corporate IT, every microservice, and three legacy tools are “in scope.” -
Fix: Scope to what processes customer data and what materially impacts it. Keep nice-to-have systems out. Defining a clear audit scope is critical to ensure all relevant systems and controls are properly evaluated during both SOC 2 and ISO 27001 audits.
3) Copy-paste policies you don’t live by
Symptom: Beautiful policy PDF; no one follows it. Auditors find the drift instantly.
Fix: Write policies that match reality. Improve reality, then update policy. Not the other way around.
4) Treating SOC 2 Type II as a finish line
Symptom: Evidence fire drill every 11 months; nothing operational in between.
Fix: Build an evidence calendar and automate the feed. Treat compliance as part of engineering hygiene.
5) Ignoring the risk assessment
Symptom: Generic risks (“malware!”) unconnected to your architecture.
Fix: Tie risks to your stack: multitenancy boundaries, LLM feature threats, third-party auth, data residency. Choose controls that address those risks. Effective risk management is essential to prevent data breaches and ensure ongoing compliance.
SOC 2 vs ISO 27001:Frequent Asked Questions
Is SOC 2 the same as ISO 27001?
No, SOC 2 and ISO 27001 are not the same, though they share about 80% of the same security controls. SOC 2 is a US-focused attestation report for service organizations, whereas ISO 27001 is an international certification for an information security management system.
How much does SOC 2 cost vs ISO 27001?
SOC 2 Type 2: $15,000-$50,000
ISO 27001: $20,000-$75,000
Costs vary based on company size, system complexity, current security maturity, and the scope of the certification. Both SOC 2 and ISO 27001 require a significant commitment in terms of time, money, and effort to achieve compliance.
Which is faster: SOC 2 or ISO 27001?
SOC 2 Type 1 takes 3-4 months. SOC 2 Type 2 takes 6-9 months due to the mandatory 3-6 month observation period.
ISO 27001 initial certification takes 4-8 months. The actual speed depends on your starting point; well-prepared startups can achieve either in 4-6 months.
Do I need SOC 2 if I have ISO 27001?
For most B2B SaaS buyers, having either SOC 2 or ISO 27001 is sufficient. However, for government contracts or sales into highly regulated industries, ISO 27001 is often a firm requirement.
Is SOC 2 recognized internationally?
SOC 2 is recognized globally but is most prevalent in North America. Customers in Europe, the UK, and APAC often prefer ISO 27001 because it’s an international standard (ISO/IEC), is more familiar in their markets, and aligns with regulations like GDPR.
Can ISO 27001 replace SOC 2?
Not always. While ISO 27001 is more comprehensive, SOC 2 is specifically designed for service providers and includes Trust Services Criteria that US customers expect. If your customer contract explicitly requires SOC 2, ISO 27001 will not be an acceptable substitute.
What’s the difference between SOC 2 Type 1 and Type 2?
A Type 1 report assesses the design of your security controls at a single point in time (taking 3-4 months to achieve). A Type 2 report assesses the operating effectiveness of your controls over a period of time, typically requiring a 3-6 month observation period. Most customers require a Type 2 report.
How long does SOC 2 last?
SOC 2 reports are considered valid for 12 months from the audit date. You must complete annual audits to maintain compliance, with re-audits typically costing between $8K-$30K annually.
How long does ISO 27001 certification last?
ISO 27001 certification is valid for 3 years but requires annual surveillance audits in Year 2 and Year 3 to maintain it. A full recertification audit is required in Year 4. Annual maintenance costs typically range from $8K-$30K.
What industries require SOC 2?
SOC 2 is most common for B2B SaaS platforms, cloud service providers, data centers, financial services technology, HR and payroll platforms, and healthcare IT systems.
Does ISO 27001 help with GDPR compliance?
Yes, partially. ISO 27001’s framework aligns with many GDPR requirements for data protection and security. However, it does not cover all aspects of GDPR, so you will still need specific GDPR processes like privacy impact assessments and procedures for handling data subject rights.
Can a small startup get SOC 2?
Yes. Even pre-revenue startups with as few as 2-5 employees can achieve SOC 2. The key requirements are having defined security policies, implementing necessary controls (like access management and encryption), and being able to demonstrate that those controls have been operating for 3-6 months for a Type 2 report.
What happens if you fail a SOC 2 audit?
Technically, you don’t ‘fail’ a SOC 2 audit, as it’s an attestation, not a pass/fail exam. Instead, an auditor can issue a qualified opinion (some controls don’t meet criteria), an adverse opinion (significant issues), or a disclaimer (unable to audit). Most companies will address the findings and get re-audited rather than accept a negative opinion.
Which is harder: SOC 2 or ISO 27001?
ISO 27001 is generally considered more prescriptive, requiring a formal Information Security Management System (ISMS), a comprehensive risk assessment, and adherence to over 93 controls from Annex A. SOC 2 is more flexible, as you select controls based on the relevant Trust Services Criteria. However, the mandatory observation period for SOC 2 Type 2 can make its timeline longer.
Do VCs care about SOC 2 or ISO 27001?
Yes, increasingly. For Series A and later funding rounds, VCs often see SOC 2 or ISO 27001 certification as proof of security maturity, a way to reduce customer acquisition friction, and a sign of lower liability risk. It’s becoming a standard due diligence item, especially for B2B SaaS companies.
What’s the ROI of SOC 2 vs ISO 27001 for startups?
The return on investment is typically measured by a 20-40% increase in enterprise deal closure rates, a 2-4 week reduction in sales cycle length, and access to enterprise customers who require compliance. It also significantly reduces the time spent on security questionnaires. The payback period can be as short as 3-6 months if compliance was blocking major deals.
How much do SOC 2 and ISO 27001 controls overlap?
There is approximately an 80% overlap between the criteria of SOC 2 and ISO 27001, with shared focus areas in data security, availability, confidentiality, and privacy. This means many controls can be mapped between the two frameworks, streamlining compliance efforts.
What are the audit requirements for SOC 2 and ISO 27001?
Both SOC 2 and ISO 27001 require an independent audit by a certified third party to validate that your controls are operating effectively and meet the required standards.
What documentation is required for SOC 2 and ISO 27001?
Both frameworks require documentation to demonstrate that controls are designed appropriately and effectively implemented. This documentation is essential for auditors to assess your compliance.
What is the role of security controls in SOC 2 and ISO 27001?
Security controls are central to both frameworks, ensuring that your organization’s information assets are protected. The importance of security practices, security standards, and the control environment is emphasized in both SOC 2 and ISO 27001, as they provide the foundation for effective risk management and compliance.
How do SOC 2 and ISO 27001 address cloud and network security?
ISO 27001:2022 includes updated controls for cloud security and network security, addressing modern security challenges in cloud environments and ensuring robust protection of information systems.
How do SOC 2 and ISO 27001 help with managing information security?
Both frameworks help organizations in managing information security and protecting sensitive information, thereby improving the organization's security posture. Implementing these standards demonstrates a commitment to safeguarding data and building customer trust.
Strategic Takeaway: This Is a Go-To-Market Decision
Selecting SOC 2 or ISO 27001 isn’t a theology debate but it’s a revenue strategy.
The choice between SOC 2 and ISO 27001 should be informed by your organization's risk management strategy, security compliance requirements, and the desired security posture you want to demonstrate to customers and partners.
If your pipeline is mostly US mid-market and prospects say “send your SOC 2,” do SOC 2 Type I in 90–120 days, then Type II. Keep an eye on ISO mapping as you build.
If you’re selling to EU/UK or global enterprises, or marketplaces/partners require a certificate, do ISO 27001 first with a tight scope. It ages well and travels globally.






